The fusion risk management field is thriving right now. With more than 20% of companies admitting that they have a cybersecurity breach in the near future, risk management has never been at such a high demand. With this booming demand has come an equally booming supply of new risk-tracking software and services aimed at helping organizations implement a standardized risk management system within their organization.
However, this surge in new technology has created an acute dearth of knowledge about what constitutes good risk management practices. As a result, it’s become increasingly difficult for organizations to identify and evaluate different risk-mitigation techniques. Fortunately, by analyzing the three core components of fusion risk management, you’ll be able to spot potential solutions from the outset so you no longer waste time or money on ineffective or fraudulent services:
What is Fusion Risk Management?
Fusion Risk Management is the art and science of managing the risk of cyberattack. By implementing a holistic approach to managing the risk of cyberattack, businesses can reduce the risk of breach and better protect their data and systems. In order to be successful with fusion risk management, you must first understand the core concepts behind it.
Fusion risk management is the integration of traditional and emerging risk management disciplines to help organizations better protect their data, employees, and customers from cyberthreats. Traditional risk management focuses on risk assessment, analysis, and control. Cybersecurity, on the other hand, is an increasingly broad discipline that includes both traditional and emerging risk management disciplines, such as data management, security policy and procedure, threat modeling, and risk assessment.
Why Are Organizations Implementing Fusion Risk Management?
Cyberattacks have cost organizations billions of dollars and thousands of hours due to ineffective and inefficient risk mitigation strategies. Companies that have implemented fusion risk management have seen significant improvements in time and cost efficiency as well as in the accuracy of risk assessment and analysis. There are a variety of reasons why organizations are implementing fusion risk management. Some of the more common ones include:
– To Improve Data Security – Some organizations have seen increased data security as the top benefit of fusion risk management. By integrating a variety of disciplines, fusion risk management helps organizations improve data security by combining security policy and procedure with data management and governance. In addition, by conducting threat modeling, organizations can determine how attacks may be executed, as well as which data may be most vulnerable.
– To Improve Compliance – For organizations that maintain an active compliance program, fusion risk management can help overcome the challenges associated with doing so in a distributed and decentralized organization. By implementing a comprehensive risk management solution, organizations can centralize and automate the processes involved in managing risk, allowing them to spend less time managing risk and more time doing business.
– To Improve Risk Assessment – While traditional risk management focuses primarily on the analysis of risk, fusion risk management takes a more holistic approach by incorporating the analysis of likelihood and impact. This helps organizations more accurately determine risk and improve the time and cost of management.
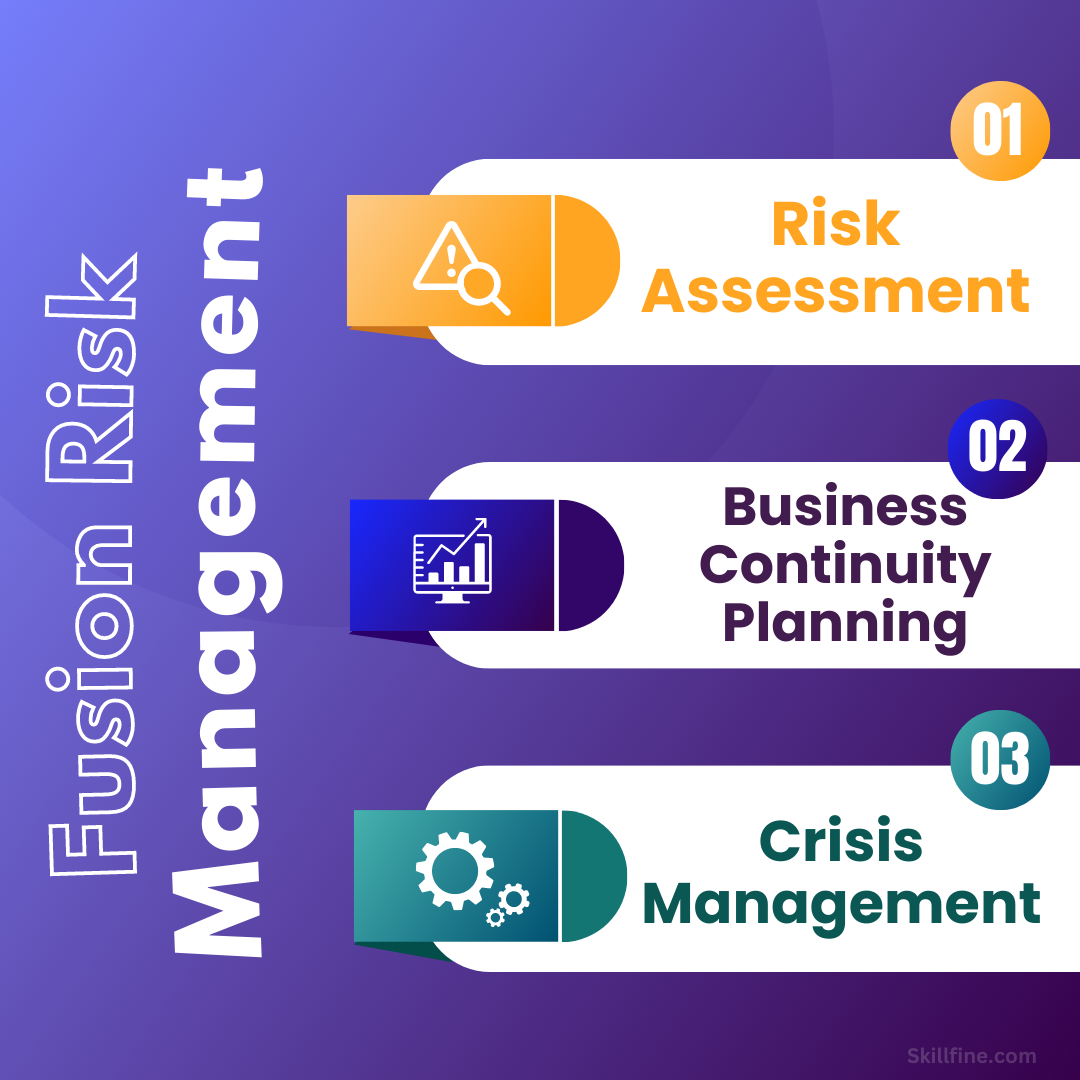
What are the 3 Core Components of Fusion Risk Management?
The first core component of fusion risk management is data management. Cyberthreats are primarily a result of bad or outdated data, making it critical for organizations to properly store, manage, and audit that data. With a robust data management solution, organizations can gain full visibility across their data and ensure 100% compliance.
Another core component of fusion risk management is security policy and procedure. While security policy and procedure can be implemented in any organization, its focus on standardized practices can help to reduce the risk of a breach by raising red flags if something is off. A comprehensive solution has the ability to automate and centralize these policies and procedures to optimize efficiency and effectiveness.
The third core component of fusion risk management is threat modeling. Threat modeling is a systematic process that uses both data and experience to develop a comprehensive model of the security threats that an organization will likely encounter. By doing so, organizations can create a comprehensive model of their own security threats and develop a robust security policy that protects their assets.
How Does Fusion Risk Management Work?
As an organization grows, so too do the threats it faces. As more data is generated and stored in various systems, these systems become more vulnerable to attack. To address these challenges, many organizations are implementing a hybrid IT approach that includes both on-premises and cloud-based infrastructure. However, this growth in hybrid IT brings with it a rise in the risk of cybersecurity incidents. With hybrid IT, the challenge is that data and systems are hosted in two different locations, increasing the risk of data breaches.
To address this challenge, a hybrid risk management solution offers benefits such as artificial intelligence and machine learning that can help to mitigate risk and detect threats. This hybrid approach to infrastructure allows organizations to scale as needed without worrying about the security of the data in a separate location. A hybrid solution also provides simplified management, so IT can focus on managing the overall IT infrastructure, rather than managing two separate environments. Taking up a course or leveraging some online resources can give you a comprehensive knowledge of how to get started.
Conclusion
By implementing a hybrid risk management strategy, organizations can reduce the risk of cybersecurity incidents and maximize the benefits of a more efficient and cost-effective hybrid IT infrastructure. By leveraging the power of artificial intelligence and machine learning, a hybrid risk management solution can help to mitigate risk, detect threats, and detect anomalies across the data lake, data warehouse, and cloud environment.
This article provided an introduction to fusion risk management and the three core components of fusion risk management: data management, security policy and procedure, and threat modeling. This article also provided an overview of how fusion risk management works, including the benefits and how these three core components work together to make fusion risk management possible.



588 thoughts on “The Three Core Components of Fusion Risk Management: The Why, What, and How”
I loved your article.Much thanks again. Will read on…
Existe alguma maneira de recuperar o histórico de chamadas excluídas? Aqueles que possuem backup na nuvem podem usar esses arquivos de backup para restaurar registros de chamadas de celular.
Quando suspeitamos que nossa esposa ou marido traiu o casamento, mas não há evidências diretas, ou queremos nos preocupar com a segurança de nossos filhos, monitorar seus telefones celulares também é uma boa solução, geralmente permitindo que você obtenha informações mais importantes.
With the increasing complexity and sophistication of cyber threats, should organizations explore the option of outsourcing their cybersecurity to dedicated firms with specialized expertise in managing hybrid IT environments?
Как выбрать подстолье, подходящее для вашего обеденного или рабочего стола
купить подстолье для обеденного стола [url=https://podstolia-msk.ru/]купить подстолье для обеденного стола[/url] .
Лучшие клининговые компании по версии пользователей. Каждая компания имеет свои особенности и преимущества. Следует учитывать несколько важных аспектов при выборе клининговой компании.
Первый аспект, который необходимо учесть, это имидж компании. Посмотрите отзывы клиентов, чтобы получить представление о качестве услуг. Кроме того, стоит обратить внимание на наличие лицензий и сертификатов.
Второй ключевой момент — это ассортимент услуг. Разные компании могут предоставлять различные услуги, от уборки квартир до комплексного обслуживания офисов. Проверьте, подходят ли предлагаемые услуги под ваши требования.
Третий важный аспект — это цены на услуги. Сравните расценки различных компаний, чтобы выбрать наиболее выгодное предложение. Не забывайте, что низкая цена не всегда гарантирует качество.
В итоге, подходите к выбору компании ответственно и учитывайте представленные советы. Выбор правильной клининговой компании позволит вам наслаждаться чистотой и уютом. Обратите внимание на рейтинг и отзывы, чтобы сделать правильный выбор.
топ 10 клининговых компаний москвы [url=https://www.uborka22.ru/]https://www.uborka22.ru/[/url] .
В продаже оригинальные мотоциклы jhl moto — проверенные поставщики
jhl мотоциклы цена [url=http://www.jhlmoto01.ru/]http://www.jhlmoto01.ru/[/url] .
Клининг в Москве становится все более популярным. С учетом быстрой жизни в столице, многие москвичи стремятся облегчить свои бытовые обязанности.
Компаниям, занимающимся клинингом, доступны разнообразные виды услуг. Среди этих задач можно выделить как регулярную уборку жилых помещений, так и специализированные услуги.
При выборе клининговой компании важно обратить внимание на опыт работы и отзывы клиентов. Клиенты должны понимать, что качественная уборка требует профессиональных навыков и соблюдения стандартов.
Таким образом, услуги клининга в Москве предоставляют возможность сэкономить время. Москвичи могут воспользоваться услугами клининговых компаний, чтобы освободить свое время для более важных дел.
сервис уборки [url=http://uborkaklining1.ru/]http://uborkaklining1.ru/[/url] .
Закажите [url=https://poverkoff.ru/]поверку приборов[/url] с оформлением официального свидетельства и возможностью получения результата в электронном виде. Работаем в удобное для клиента время и соблюдаем сроки.
Процесс поверки средств измерений играет ключевую роль в поддержании точности измерительных данных. Данный процесс обеспечивает соответствие оборудования установленным нормам и стандартам качества.
Процедура поверки проходит через ряд этапов, включая проверку функционального состояния измерительных средств. Следующим шагом является выполнение контрольных измерений и их сравнение с эталонными показателями. При выявлении расхождений следует откалибровать прибор или, в случае необходимости, произвести его замену.
Регулярность поверки приборов критически важна для поддержания их точности и надежности. Важно контролировать сроки поверки, чтобы обеспечить правильность и достоверность измерений.
Клининг элитной недвижимости с деликатной уборкой интерьеров
клининг служба [url=https://www.kliningovaya-kompaniya10.ru]https://www.kliningovaya-kompaniya10.ru[/url] .
Продажа и лизинг коммерческого транспорта с доставкой по всей России
лизинг на спецтехнику для юридических лиц [url=lizing-auto-top1.ru/specztehnika]lizing-auto-top1.ru/specztehnika[/url] .
Welcome to our website dedicated to the sale of medical supplies!
We offer the large assortment of high-quality products necessary for medical offices. [url=https://promedicalsupplies.ru/kombinirovannaya-upakovka-dlya-sterilizaczii]пакеты для стерилизации комбинированные [/url] and [url=https://promedicalsupplies.ru/kombinirovannaya-upakovka-dlya-sterilizaczii]упаковка для стерилизации медицинских изделий [/url]
More detailed information on the links
Our goal is to provide you with reliable supplies that meet the strictest quality standards.
Каркасное строительство без лишних затрат: честный подход к ценообразованию
каркасный дом под ключ [url=https://spb-karkasnye-doma-pod-kluch.ru/]https://spb-karkasnye-doma-pod-kluch.ru/[/url] .
Каркасный дом как альтернатива кирпичному: экономия, срок, надёжность
строительство каркасных домов спб [url=http://karkasnie-doma-pod-kluch06.ru/]http://karkasnie-doma-pod-kluch06.ru/[/url] .
Индивидуальная печать на футболках: стиль, который говорит за вас
заказать футболку с принтом [url=https://pechat-na-futbolkah777.ru]https://pechat-na-futbolkah777.ru[/url] .
Посетите наш сайт и узнайте о [url=https://uborka-chistota.ru/]клининг спб цена[/url]!
Клининговые услуги в Санкт-Петербурге востребованы как никогда. С каждым годом всё больше компаний предлагают широкий спектр услуг по уборке и обслуживанию помещений.
Клиенты ценят качество и доступность таких услуг. Многие клининговые фирмы предлагают персонализированные решения для каждого клиента, принимая во внимание его желания.
Клининговые услуги включают в себя как регулярную уборку, так и разовые услуги
Комфорт загородной жизни: деревянные дома под ключ от опытной строительной компании
деревянный дом под ключ [url=https://derevyannye-doma-pod-klyuch-msk0.ru/]деревянный дом под ключ[/url] .
Welcome to our website dedicated to the sale of medical supplies!
We offer the widest selection of high-quality products necessary for medical offices. [url=https://promedicalsupplies.ru/kombinirovannaya-upakovka-dlya-sterilizaczii]упаковка для стерилизации [/url] and [url=https://promedicalsupplies.ru/kombinirovannaya-upakovka-dlya-sterilizaczii]комбинированная упаковка [/url]
More detailed information on the links
Our goal is to provide you with safe supplies that meet the strictest quality standards.
Korzystając z [url=https://bitqt-official.com/]bitqt official[/url], inwestorzy mają dostęp do narzędzi wspierających analizę i podejmowanie decyzji inwestycyjnych w oparciu o dane.
Bitqt to zaawansowany system tradingowy, pozwalająca inwestorom na trading na rynkach finansowych. Bitqt stosuje innowacyjne algorytmy, aby analizować rynki na bieżąco, co pozwala użytkownikom podejmować świadome decyzje inwestycyjne.
Platforma oferuje szereg narzędzi, które ułatwiają trading. Inwestorzy mogą zautomatyzować swoje transakcje, co przyczynia się do większych zysków. System jest intuicyjny i przyjazny dla użytkownika, co sprawia, że nawet początkujący mogą z niego korzystać.
Bitqt dba o bezpieczeństwo informacji swoich użytkowników. Zastosowane w platformie technologie szyfrowania dają użytkownikom pewność, że ich dane są bezpieczne. Dlatego Bitqt jest wybierane przez wielu inwestorów jako rzetelna platforma.
Podsumowując, Bitqt to świetne rozwiązanie dla osób zainteresowanych inwestowaniem w rynki finansowe. Dzięki innowacyjnym funkcjom, bezpieczeństwu oraz intuicyjnej obsłudze, każdy może rozpocząć swoją inwestycyjną przygodę. Daj sobie szansę na sukces inwestycyjny z Bitqt.
Уточните [url=https://genuborkachistota.ru/]клининг стоимость услуг[/url], чтобы не переплачивать за стандартные задачи. Все цены официально закреплены в договоре.
Услуги клининга в Москве набирают популярность с каждым годом. Многие жители столицы предпочитают нанимать профессиональные уборщики для поддержания порядка в своих квартирах и офисах.
Цены на клининг могут варьироваться в зависимости от специфики услуг. Например, стандартная уборка квартиры может стоить от 1500 до 5000 рублей.
Также можно заказать дополнительные услуги, включая мойку окон и химчистку ковров. Стоимость дополнительных услуг может существенно сказаться на общей цене уборки.
Прежде чем остановиться на конкретной клининговой компании, будет полезно изучить предложения на рынке. Обращайте внимание на отзывы и рейтинг выбранной клининговой компании.
Все [url=https://uborka12.ru/]клининговые услуги СПб[/url] — от уборки квартиры до генеральной очистки производственного помещения. Мы готовы к любым задачам.
Сфера клининга в Санкт-Петербурге вырабатывает тренды. В Санкт-Петербурге работают разные компании, которые предлагают услуги клининга. Среди них можно выделить уборку квартир, офисов и коммерческих помещений.
Услуги клининговых компаний востребованы в основном из-за экономии времени. Так они освобождают время для выполнения более важных задач. Клиенты ценят клининг за возможность делегировать рутинные задачи.
Причина успеха клининговых компаний заключается в высоком уровне профессионализма. Специалисты клининговых компаний знают, как правильно применять современное оборудование и моющие средства. Такой подход позволяет быстро и качественно выполнять работу.
Разнообразие пакетов услуг позволяет каждому найти подходящее решение. Некоторые компании предлагают разовые уборки, другие – долговременное сотрудничество. Так клиенты могут подобрать наиболее удобный для себя вариант.
Мастера с опытом проводят [url=https://kursi-barbera-s-nulya.ru/]курсы барбера Красноярск[/url] в удобном графике. Мини-группы и внимание к каждому ученику.
Запись на курсы барбера набирает популярность среди молодежи. Количество школ, обучающих барберов, постоянно растет. Это связано с возросшим спросом на услуги мужских парикмахерских.
На таких курсах обучают не только основам стрижки, но и искусству общения с клиентами. Учащиеся получают актуальные знания, которые помогут им построить карьеру в этой сфере. На занятиях акцентируется внимание на различных стилях и методах работы с волосами и бородой.
После окончания курса, ученики могут начать работать в салонах или открыть собственный бизнес. Выбор курсов часто зависит от репутации школы и её месторасположения. Необходи?мо внимательно изучить отзывы о курсах, прежде чем принять решение о записи.
В конечном счете, выбор курса зависит от ваших целей и желаемых результатов. С каждым днем рынок барберинга расширяется, поэтому качество образования становится решающим. Не забывайте, что успех в этой профессии зависит от постоянного обучения и практики.
Add a new dimension to your event with a unique [url=https://drone1-show.com/]drone show[/url] that combines light, rhythm, and sky artistry.
In recent years, drone light shows have gained significant popularity. These spectacular displays use coordinated drones to create stunning visual effects. They serve as a contemporary substitute for conventional fireworks. Many event organizers are embracing this innovative technology.
One significant advantage of drone light shows is that they are environmentally friendly. Unlike traditional fireworks, they don’t create toxic smoke or litter. This makes them a safer option for public events. Furthermore, they can be designed to align with a variety of themes and events.
The technology behind drone light shows involves precise coordination and programming. These drones are fitted with lights that can alter hues and designs. This advanced technology facilitates engaging displays that can enthrall spectators. Essentially, drone light shows embody the next wave of entertainment.
As we move forward, the opportunities for drone light shows are boundless. With technological progress, we can anticipate increasingly complex and spectacular performances. These events will not only entertain but also leave a lasting impression on audiences. The future of entertainment is undoubtedly bright with the rise of drone light shows.
Простой способ порадовать близких — [url=https://sushiyok.ru/]заказ суши[/url] с доставкой к вашему столу. Удобно, быстро и вкусно.
Заказ суши – это легкая задача. Существует несколько способов заказа суши, включая сайт ресторана и мобильные приложения. Каждый из этих способов предлагает определенные плюсы и минусы.
При выборе ресторана обратите внимание на отзывы. Почитайте, что говорят люди о качестве еды и обслуживании. Так вы сможете избежать возможных неприятных сюрпризов и выбрать заведение с хорошей репутацией.
Ознакомьтесь с представленными блюдами перед тем, как оформить заказ. Меню может варьироваться, и разные заведения предлагают уникальные роли и суши. Не бойтесь экспериментировать с новыми вкусами и сочетаниями.
При заказе обязательно уточните, когда ожидается доставка. Уточнение времени доставки поможет избежать ожидания и обеспечит комфортное времяпрепровождение. Не забудьте проверить, доставляют ли в вашу часть города.
Суши и роллы без наценок — [url=https://sakura-v-spb.ru/]суши недорого СПб[/url] доступны круглосуточно. Удобный заказ с любого устройства.
Заказ вок-блюд через интернет приобретает все большую популярность. Это связано с удобством и разнообразием предлагаемых блюд.
Существует множество ресторанов, предлагающих вок-заказ. Каждое из этих заведений может предложить уникальное меню и специальные предложения.
Важно следить за мнениями клиентов, чтобы выбрать наилучший ресторан. Это позволит выбрать только те рестораны, которые предлагают отличное качество пищи.
Следите за специальными предложениями, которые могут сделать ваш заказ более выгодным. Скидки на вок-блюда позволяют сэкономить деньги и попробовать что-то новенькое.
Живите вкусно — [url=https://pizza-mafeeya.ru/]пицца спб доставка[/url] дарит комфорт и аромат в каждом заказе.
Заказ пиццы стал легким и доступным процессом. Существует множество способов, как это сделать. Вы можете воспользоваться интернет-сервисами, которые предлагают доставку. Также можно позвонить в ресторан и сделать заказ по телефону.
Если вы хотите выбрать пиццу, изучите доступные варианты в меню. Множество заведений предлагает широкий выбор пиццы, включая традиционные и креативные рецепты. Не забывайте, что можно создать индивидуальную пиццу, выбрав любимые начинения.
Когда вы определились с выбором, уточните время, через которое вам привезут пиццу. Часто столицы обещают разные временные рамки в зависимости от объема заказов. Также вам стоит узнать условия доставки и минимальную сумму, необходимую для заказа.
Существует несколько способов оплаты заказа пиццы. Обычно заведения принимают наличные, кредитные карты и предлагают возможность безналичной оплаты. Не забывайте проверять акции и скидки, которые могут существенно снизить стоимость заказа.
Tek tıkla [url=https://trfullhdizle.com/]online film izle 4k[/url] ayrıcalığını yaşayın. Hızlı ve kaliteli film keyfi artık çok kolay.
4K çözünürlükte Full HD filmleri izle. Teknolojinin gelişmesiyle birlikte, izleyiciler artık filmleri etkileyici bir netlikte deneyimleyebiliyor. 4K’nın canlılığı ve incelikleri izleme deneyimini bambaşka bir seviyeye taşıyor.
Birçok platform 4K kalitesinde Full HD filmler sunuyor. Bu platformlar film kalitesini artırarak keyfi en üst düzeye çıkarıyor. Örneğin Netflix ve Amazon Prime gibi servisler geniş bir 4K içerik arşivine sahip. Bu geniş seçenek yelpazesi her kesime hitap ediyor.
Bu deneyimi tam anlamıyla yaşamak için uygun bir cihaz gereklidir. Yeni nesil televizyonların ve projeksiyonların çoğu artık 4K destekli olarak üretilmektedir. 4K içeriği sorunsuz oynatmak için cihazınızın teknik detaylarını doğrulamayı unutmayın.
Özetle, 4K kalitesinde Full HD film izlemek eşsiz bir sinema keyfi sağlar. Doğru araçlar ve sağlam yayın servisleriyle büyüleyici görselleri keşfetmeniz mümkün. Bu fırsatı değerlendirin ve film izleme deneyiminizi bir üst seviyeye çıkarın.
Filmleri kesintisiz ve yüksek çözünürlükte izlemek için [url=https://turkfilmsitesi.com/]hd full film izle[/url] tam size göre. Eğlenceye kaldığınız yerden devam edin.
Full HD film izlemek olağanüstü bir macera sunar. Teknolojik ilerlemeler sayesinde film kalitesi yeni zirvelere ulaştı. Günümüzde izleyiciler, nefes kesici görselleri ve etkileyici sesleri birlikte deneyimleyebiliyor.
Son yıllarda 4K çözünürlüğe olan ilgi önemli ölçüde arttı. Bu yüksek çözünürlük, standart HD’ye kıyasla daha net ve ayrıntılı görüntüler sunar. Pek çok sinema sever, filmleri 4K olarak izlemeyi zorunlu bir deneyim olarak görür.
Yayın platformları, Full HD ve 4K filmlere erişimi kolaylaştırdı. Artık izleyiciler istedikleri zaman ve istedikleri yerden favori filmlerini izleyebiliyor. Bu tür bir kolaylık, medya alışkanlıklarımızı tamamen dönüştürdü.
4K içeriklerin artmasıyla birlikte yüksek kaliteli ekranlara olan talep de artıyor. Kaliteli bir 4K televizyona yatırım yapmak izleme deneyimini önemli ölçüde iyileştirir. Gerçek film tutkunları için bu yatırım kesinlikle buna değer.
Como [url=https://show1-de-drones.com/]empresa de espectáculos de drones[/url], desarrollamos eventos con identidad propia, adaptando cada coreografía aérea a los objetivos de tu marca o celebración. El cielo se convierte en el escenario más grande y bello.
El espectáculo de drones ha ganado popularidad en los últimos años. Estos eventos combinan tecnología, arte y entretenimiento. Las exhibiciones de drones son cada vez más comunes en festivales y celebraciones.
Los drones que llevan luces crean diseños asombrosos en el cielo oscuro. Las audiencias suelen quedar asombradas por la combinación de luces y coreografías.
Numerosos planificadores de eventos eligen contratar a empresas expertas para llevar a cabo estos shows. Estas empresas cuentan con pilotos capacitados y equipos de última generación.
La seguridad es un aspecto crucial en estos espectáculos. Se siguen procedimientos detallados para prevenir riesgos durante estas exhibiciones. El futuro de los espectáculos de drones es prometedor, con innovaciones constantes.
Уточните окончательную [url=https://vyvod-iz-zapoya-spb-01.ru/]вывод из запоя стоимость[/url] услуг в нашей клинике СПб после консультации с наркологом. Цена зависит от состояния пациента и выбранной программы.
Вывод из запоя представляет собой непростую задачу, требующую тщательного подхода. Необходимо осознавать, что каждая ситуация требует индивидуального решения.
Первым шагом в процессе вывода из запоя является решение обратиться к специалисту. Часто люди пытаются справиться с запоем самостоятельно, но это может быть неэффективным.
Визит к врачу или наркологу — это ключевой момент при выводе из запоя. Специалист поможет разработать план лечения и предложит необходимые медикаменты.
Не менее важно, чтобы рядом были близкие люди, готовые поддержать в трудное время. Близкие могут стать ключевыми помощниками в процессе выздоровления.
Yüksek çözünürlükte film keyfi arayanlar için özel olarak sunulan [url=https://onlinefilmturk.com/]hd dilm[/url] kategorimiz, kaliteli ve hızlı erişimle sinema keyfinizi artırıyor.
Günümüzde izleyiciler arasında yüksek çözünürlüklü filmlere olan talep önemli ölçüde arttı. En popüler formatlardan biri, çarpıcı netlik ve ayrıntı sunan Full HD’dir.
İzleyiciler, film izle 4k hizmeti sunan platformlar sayesinde kolayca Full HD filmlere erişebilir. Çoğu yayın hizmeti, her izleyiciye hitap edecek şekilde geniş arşivler oluşturur.
Keyifli bir film deneyimi için güvenilir platformları tercih etmek oldukça önemlidir. Düşük kaliteli içeriklerden kaçınmak için platformların itibarını araştırmak akıllıca olacaktır.
Full HD ve 4k kalitesinde film izlemek, evdeki genel izleme keyfinizi artırabilir. Sevdiklerinizi davet edin ve Full HD filmlerin büyüleyici görüntülerinin keyfini çıkarın.
Filmizlecc seçeneğimiz, geniş film koleksiyonunu yüksek kalitede izlemek isteyenler için uygundur. Güncel filmler için [url=https://trfilmcehennemi.com/]filmizlecc[/url] sayfasını kullanabilirsiniz.
Son yıllarda yayın platformlarının yükselişi dikkat çekici oldu. Önemli bir trend, özellikle Full HD ve 4K çözünürlüklerde yüksek tanımlı içeriğe olan talebin artmasıdır. Tüketiciler netlik ve detay sunan sürükleyici izleme deneyimleri arıyor.
Full HD filmler 1920×1080 piksel çözünürlük sunarak etkileyici görsel kalite sağlar. Bu, özellikle büyük ekranlarda her detayın fark edilebildiği durumlarda belirgindir. Buna karşılık, 4K filmler 3840×2160 piksel çözünürlükle izleme deneyimini olağanüstü hale getirir.
Bu talebi fark eden yayın hizmetleri, geniş Full HD ve 4K film koleksiyonları sağlamaya başladı. Böylece, seyirciler hem yeni yapımları hem de sevilen klasik filmleri en yüksek görsel kalitede izleyebiliyor. Bunun yanında, birçok yayın hizmeti yüksek çözünürlüklü formatlara özel orijinal içerik üretimine kaynak ayırıyor.
Sonuç olarak, yayın platformlarındaki Full HD ve 4K film trendi izleyici tercihindeki değişimi yansıtıyor. Teknoloji ilerledikçe, görsel medyayı tüketme şeklimizde daha fazla gelişme bekleyebiliriz. Bu trendler, film sektörü ve evde izleme alışkanlıklarının geleceğini önemli ölçüde değiştirecektir.
[url=https://narkologicheskaya-klinika01.ru/]Клиника наркологическая[/url] в СПб с многолетним опытом работы. Мы помогаем вернуться к здоровой жизни с помощью комплексных программ и психологической поддержки.
В наркологической клинике пациенты находят поддержку и лечение для преодоления зависимостей. В учреждении работают опытные врачи и консультанты, которые занимаются лечением зависимостей.
Основной целью наркологической клиники является выявление и лечение проблем, связанных с зависимостями. Комплексный подход к лечению включает как медицинские, так и психологические методы.
Специалисты работают с клиентами над психологическими аспектами их зависимостей. Психологические занятия способствуют личностному росту и укреплению мотивации для изменений.
Длительность реабилитации варьируется в зависимости от индивидуальных особенностей пациента. Несмотря на сложности, победа над зависимостью крайне ценна.
Забота о мозге начинается с правильных решений. У нас вы можете [url=https://magazin-nootropov.ru/]ноотропы для мозга купить[/url] с гарантией качества и рекомендациями по применению.
Ноотропы представляют собой группу препаратов, способствующих улучшению умственной деятельности. Ноотропы используются для стимуляции умственной активности, улучшения памяти и повышения уровня внимания.
Среди ноотропов можно выделить разнообразные препараты, включая как искусственные, так и натуральные. Каждый из них имеет свои уникальные свойства и эффекты.
Природные источники ноотропов, например, женьшень и гинкго билоба, славятся своими благотворными свойствами. Они часто используются в традиционной медицине для улучшения памяти и сосредоточенности.
Синтетические ноотропы, такие как пирацетам, были разработаны для более целенаправленного воздействия. Они часто применяются для лечения различных нарушений, включая проблемы с памятью.
Постройте стильный и надежный коттедж. Выберите подходящий [url=https://proekty-domov1.ru/]готовый проект коттеджа[/url] из коллекции, где каждый прошел экспертизу.
Проекты домов становятся все более популярными среди людей, ищущих идеальное жилье. Определение подходящего проекта дома является решающим шагом на пути к уюту и комфорту.
Разнообразие проектов домов включает в себя различные стили и типы. Каждый сможет подобрать проект, который будет соответствовать его вкусам и потребностям.
Одним из основных факторов при выборе проекта является размер земельного участка. Важно также оценить окружающую среду и климатические условия.
Технологический прогресс помогает в создании оригинальных и уникальных проектов домов. Каждый проект может быть адаптирован под конкретные нужды заказчика.
Лето 2025 в Джубге станет временем ярких впечатлений. Заранее обеспечьте себя комфортабельным жильем для полного наслаждения отдыхом. Выбирайте из лучших вариантов [url=https://otdyh-v-dzhubge.ru/]жилье в джубге 2025[/url].
Отдых в Джубге — отличный выбор для тех, кто ищет море и солнце. Курорт Джубга известен своими живописными пляжами и прекрасными видами.
Множество туристов приезжает сюда каждый год, чтобы насладиться местными достопримечательностями. К числу популярных мест относятся водопады и древние дольмены.
Кроме того, Джубга предлагает разнообразные развлечения для всей семьи. Развлечения варьируются от спокойных прогулок до активных водных видов спорта, подходящих для всех.
Отдых на пляже — это неотъемлемая часть вашего пребывания в Джубге. Здесь вы сможете наслаждаться солнцем и морскими волнами, а также попробовать местные блюда в кафе.
Пляжный отдых в Абхазии славится чистым морем и живописными видами. Организуйте свой [url=https://otdyhabhaziya01.ru/]абхазия отдых на море[/url].
Отдых в Абхазии — это настоящая находка для тех, кто ценит природу и атмосферу. В этой стране моря, гор и сочных зелёных долин возможно найти всё для идеального отдыха.
Многочисленные туристы выбирают Абхазию как идеальное место для отдыха и развлечений. Отдых в Абхазии предлагает как спокойные пляжные дни, так и захватывающие приключения.
Местные курорты предлагают множество вариантов размещения от бюджетных гостиниц до роскошных отелей. Кроме того, здесь можно насладиться вкусной местной кухней и разнообразием культурных мероприятий.
Независимо от времени года, отпуск в Абхазии будет незабываемым и полным позитивных эмоций. Абхазия ждёт вас с открытыми объятиями и множеством новых впечатлений.
Ищете удобный сервис для аренды жилья? Наш сайт специализируется на подборе оптимальных вариантов в Туапсе по вашему запросу. Начните поиск [url=https://otdyh-v-tuapse.ru/]туапсе снять жилье[/url].
Отдых в Туапсе позволяет насладиться чудесными пляжами и теплым климатом. Это курорт, известный своими великолепными пляжами и мягким климатом.
Летом здесь множество туристов, кто приезжает для расслабления и активного отдыха. Гостям доступны различные развлечения, от водных видов спорта до вечерних мероприятий.
В Туапсе имеется богатый выбор гостиниц и домиков, отвечающих различным требованиям. Ценовой диапазон очень разнообразен, что позволяет каждому выбрать подходящий вариант.
Не забудьте посетить местные достопримечательности и национальные парки. Это подарит вам незабываемые впечатления и возможность познакомиться с природой края.
Добейтесь наилучшего качества изображения с правильно подобранным [url=https://ehkrany-dlya-proektora1.ru/]проекционный экран для проектора[/url]. Изучите предложения у нас.
Экран для проектора является важным элементом для качественной демонстрации изображений. Верный выбор экрана может значительно улучшить качество отображаемой информации.
Существует множество разновидностей экранов, включая мобильные, фиксированные и настенные. Каждый из этих типов имеет свои особенности и преимущества.
При выборе экрана важно учитывать размеры помещения и тип проектора. Подходящие размеры экрана определяются расстоянием до места, где будут сидеть зрители.
Для достижения идеального восприятия контента важно учитывать степень освещения в комнате. В условиях яркого света оптимальным решением станет экран с матовым фоном.
Не упустите возможность забронировать популярные объекты размещения на пик сезона. [url=https://otdyh-v-arhipo-osipovke.ru/]снять жилье в архипо осиповке 2025[/url] по хорошей цене лучше заранее.
Отдых в Архипо-Осиповке — отличный выбор для любителей природы. Сюда часто приезжают туристы, желающие насладиться теплым морем и живописными пейзажами.
Пляжи этого курорта известны своим чистым песком и спокойными водами. На пляжах Архипо-Осиповки доступны различные водные виды спорта и развлекательные программы.
Архипо-Осиповка предлагает разнообразные варианты проживания для туристов. Гостиницы и частные номера в Архипо-Осиповке подойдут как для романтического уикенда, так и для семейного отдыха.
Местные развлечения порадуют как детей, так и взрослых. Прогулки по набережной, экскурсии и местные фестивали — все это создаст незабываемые впечатления.
Сочетание спокойствия, комфорта и эстетики делает [url=https://arenda-yahty-sochi07.ru/]аренда яхт в сочи[/url] отличным выбором как для уединения, так и для яркого праздника на воде.
Чартер яхты становится все более популярным среди любителей отдыха. Поездка на яхте дает возможность отдохнуть и насладиться свежим воздухом.
Подбор яхты — ключевой момент, который стоит учитывать при планировании отдыха. Тип и размер яхты имеют большое значение, поэтому выбирайте то, что подходит именно вам.
При аренде яхты важно внимательно изучить все пункты договора. Многие компании предоставляют возможность нанять капитана и экипаж для комфортного путешествия.
Также стоит уделить внимание планированию маршрута вашего плавания. Посетите популярные места, такие как уединенные бухты или живописные острова.
Мягкий климат, тёплое море и спокойная атмосфера — идеальные условия, чтобы [url=https://otdyhabhaziya0.ru/]отдохнуть в абхазии[/url] без лишних хлопот.
Многие предпочитают отдыхать в Абхазии, так как это невероятное направление. Эта республика привлекает путешественников своими живописными пейзажами.
На побережье Черного моря расположены прекрасные курорты. Для туристов доступны разнообразные варианты размещения: от гостиниц до частных домов.
В Абхазии также можно насладиться уникальными природными достопримечательностями. Туризм в Абхазии включает в себя как горные походы, так и посещение озер и водопадов.
Любители вкусной еды найдут в Абхазии множество интересных блюд. Кулинарные традиции Абхазии отличаются уникальным сочетанием вкусов и свежестью продуктов.
Los [url=https://show1-de-drones.com/]espectaculos con drones[/url] ofrecen una experiencia visual de vanguardia donde la tecnología se convierte en arte. Creamos escenas temáticas para cada ocasión, desde ferias públicas hasta galas privadas.
Los espectáculos de drones se han vuelto muy populares en la actualidad. Estos shows integran tecnología avanzada, creatividad y diversión. Las exhibiciones de drones son cada vez más comunes en festivales y celebraciones.
Los drones equipados con luces generan figuras fascinantes en el firmamento. Los espectadores quedan maravillados con el espectáculo de luces y movimientos.
Varios organizadores deciden recurrir a compañías dedicadas a la producción de espectáculos de drones. Estas organizaciones poseen pilotos entrenados y tecnología avanzada.
La seguridad representa un factor fundamental en la realización de estos eventos. Se establecen medidas estrictas para asegurar la seguridad del público. El futuro de los espectáculos de drones es prometedor, con innovaciones constantes.
Наша [url=https://narkologicheskaya-klinika01.ru/]клиника для наркозависимых[/url] в СПб создает условия для глубокой реабилитации. Программы включают психотерапию, соц. адаптацию и поддержку семьи.
Клиника наркологии предоставляет услуги по лечению зависимостей и реабилитации. В учреждении работают опытные врачи и консультанты, которые занимаются лечением зависимостей.
Одной из главных задач клиники является диагностика и лечение алкогольной и наркотической зависимости. Наркологическая клиника применяет различные методы, чтобы помочь пациентам преодолеть зависимость.
Психологическая поддержка играет ключевую роль в процессе восстановления. Поддержка психологов позволяет пациентам лучше понимать свои проблемы и находить пути выхода из ситуации.
Каждый пациент проходит реабилитацию в своем темпе, что позволяет избежать стрессовых ситуаций. Однако, завоевание контроля над своей жизнью стоит затраченных усилий.
Найдите то, что подходит именно вам, и [url=https://magazin-nootropov.ru/]ноотропы какие купить[/url] с доставкой на следующий день.
Ноотропы представляют собой группу препаратов, способствующих улучшению умственной деятельности. Они могут помочь повысить концентрацию, память и общее состояние организма.
Существует множество видов ноотропов, как синтетических, так и природных. Все эти препараты различаются по своим механизму действия и конечным результатам.
Природные ноотропы, такие как женьшень и гинкго билоба, известны своими полезными свойствами. Данные природные ноотропы широко используются в лечебных целях для повышения внимательности и памяти.
Синтетические ноотропы, такие как пирацетам, были разработаны для более целенаправленного воздействия. Они часто применяются для лечения различных нарушений, включая проблемы с памятью.
От недорогих вариантов для молодежи до комфортабельных апартаментов для семей – мы поможем подобрать идеальное [url=https://otdyh-v-arhipo-osipovke.ru/]жилье в архипо осиповке[/url] под ваши запросы и финансовые возможности.
Отдых в Архипо-Осиповке — отличный выбор для любителей природы. Сюда часто приезжают туристы, желающие насладиться теплым морем и живописными пейзажами.
Пляжи этого курорта известны своим чистым песком и спокойными водами. Купание и водные развлечения делают отдых здесь незабываемым.
В этом курортном поселке можно найти различные варианты жилья на любой вкус и бюджет. Гостиницы и частные номера в Архипо-Осиповке подойдут как для романтического уикенда, так и для семейного отдыха.
Кроме того, Архипо-Осиповка известна своим разнообразным досугом. Прогулки по набережной, экскурсии и местные фестивали — все это создаст незабываемые впечатления.
Наслаждайтесь каждым моментом путешествия по морю — [url=https://arenda-yahty-sochi07.ru/]сочи аренда яхты[/url] даёт возможность испытать новые ощущения и отдохнуть без суеты.
Чартер яхты становится все более популярным среди любителей отдыха. Путешествие на яхте позволяет насладиться красотой природы и расслабиться.
Правильный выбор яхты может значительно повлиять на ваше впечатление от отпуска. Необходимо учитывать тип и размер яхты, чтобы она соответствовала вашим требованиям.
Перед подписанием контракта на прокат яхты обязательно ознакомьтесь с его условиями. Некоторые сервисы предлагают дополнительные услуги, включая услуги профессионального капитана.
Также стоит уделить внимание планированию маршрута вашего плавания. Проведите время в красивейших местах, которые доступны только с воды.
Master the game and boost your confidence by reviewing [url=https://sweet-bonanza25.com/]how do you play sweet bonanza[/url], a useful guide for anyone looking to improve their slot skills.
Sweet Bonanza is a popular online slot game that has captured the attention of players worldwide. With its bright graphics and engaging mechanics, it stands out as a top choice.
What makes Sweet Bonanza particularly appealing are its distinctive features. With its cascading reels, players can secure multiple victories on each spin.
On top of that, Sweet Bonanza provides a free spins option that enhances the overall fun. This feature can lead to substantial payouts, making it even more enticing.
To sum up, Sweet Bonanza is a captivating slot game that offers much to players. With its vibrant design and rewarding features, it appeals to both new and experienced players.
Импортозамещающая продукция с адаптацией к российским условиям. Качественный [url=https://nozhnichnyy-podemniki15.ru/]ножничный подъемник производство в России[/url] без переплат за бренд.
Ножничный подъемник — это одно из самых популярных средств подъемной техники. Данное устройство гарантирует безопасность и эффективность при подъеме людей и грузов.
Ножничные подъемники отличаются своей компактностью и способностью легко маневрировать в ограниченных пространствах. Это позволяет использовать их в помещениях с ограниченной высотой потолка и узкими проходами.
Еще одним важным аспектом является возможность регулировки высоты поднятия. Регулировка высоты обеспечивает гибкость в использовании данного оборудования для множества задач.
Ножничные подъемники часто используются в строительстве, на складах и в торговле. Безопасность и легкость в эксплуатации делают ножничные подъемники востребованными на рынке.
Привлекательная стоимость без ущерба для качества и безопасности. Запросите актуальную [url=https://gruzovyepodemniki-odnomachtovye15.ru/]цена одномачтового подъемника[/url] и сравните наши выгодные условия.
Одномачтовый подъемник пользуется большим спросом в различных сферах. Этот вид подъемника используется для выполнения множества задач.
Важно подчеркнуть, что одномачтовые подъемники очень мобильны. Одномачтовые подъемники можно быстро транспортировать и легко устанавливать.
Еще одно важное преимущество – это их компактность. Это позволяет использовать их в ограниченных пространствах.
Однако, как и любое оборудование, одномачтовые подъемники имеют свои недостатки. Например, они могут иметь ограниченную грузоподъемность. При выборе оборудования важно учитывать все аспекты.
Быстрая доставка и профессиональный монтаж по Санкт-Петербургу. Выбирайте качественный [url=https://gruzovoy-podjemnik15.ru/]грузовой подъемник спб[/url] для вашего бизнеса.
Важность подъемного оборудования в строительстве трудно переоценить. С помощью подъемного оборудования можно быстро и безопасно перемещать тяжелые предметы.
Подъемное оборудование делится на несколько категорий, таких как подъемники, краны и прочие механизмы. Каждое из этих устройств имеет свои особенности и предназначение, что позволяет выбрать наиболее подходящее решение для конкретной задачи.
Технический осмотр подъемного оборудования — это важный шаг перед его эксплуатацией. Регулярный технический осмотр помогает предотвратить поломки и обеспечивает безопасное использование оборудования.
Также важно соблюдать правила эксплуатации подъемного оборудования. Правильное следование инструкциям позволяет избежать серьезных инцидентов.
Когда человек ищет не просто сурмаму, а надёжного, психологически зрелого партнёра — важно не ошибиться. У нас удобно размещать запрос [url=https://deti-eto-schastie.ru/]ищу сурмаму[/url] и получать релевантные отклики.
Суррогатное материнство — это процесс, позволяющий создать семью для тех, кто не может стать родителем самостоятельно. Увеличение интереса к суррогатному материнству объясняется изменением общественного мнения и ростом технологий в области репродукции.
Существует несколько типов суррогатного материнства, каждый из которых имеет свои особенности. В традиционном суррогатном материнстве суррогатная мать является биологической матерью ребенка, так как использует свои яйцеклетки. В отличие от этого, при гестационном суррогатном материнстве эмбрион создается с использованием яйцеклетки и сперматозоидов намеревающихся родителей.
Прежде чем обратиться к суррогатным матерям, следует взвесить все за и против данного шага. Пары должны быть готовыми к финансовым затратам, юридическим требованиям и эмоциональным вызовам, связанным с этим процессом. Выбор подходящего агентства, которое будет сопровождать на каждом этапе, играет ключевую роль в успешном завершении процесса.
Суррогатное материнство затрагивает как медицинские, так и социальные аспекты, включая права и обязанности всех участников. Поддержка и понимание со стороны общества играют важную роль в создании позитивного имиджа этой практики. Таким образом, суррогатное материнство открывает новые горизонты для многих семей, стремящихся к родительству, при условии уважения к правам всех участников процесса.
Наш сайт — это быстрый и надёжный способ найти [url=https://best-photographers-moscow.ru/]светские фотографы москвы[/url] для мероприятий, торжеств, репортажей и публичных событий высокого уровня.
Выдающиеся фотографы занимают особое место в мире визуального искусства. В этой публикации мы обсудим ряд выдающихся фотографов, чьи снимки оставляют неизгладимое впечатление.
Первым стоит выделить имя, которое знакомо многим любителям искусства. Этот мастер создает удивительные образы, которые подчеркивают красоту и уникальность момента.
Следующим в нашем списке идет фотограф, чьи портреты всегда полны жизни и эмоций. Его работы отличаются глубоким пониманием человека и его внутреннего мира.
В заключение стоит упомянуть мастера, который специализируется на съемке природы. Их работы вдохновляют многих и приглашают нас в мир красоты природы.
Stay anonymous and access services worldwide by using a [url=https://receive-sms-online-fast.com/]temp number[/url] for verification. No registration needed—fast and free access anytime.
Receiving SMS messages is an essential part of modern communication. These messages keep us in touch with our friends, family, and workmates.
With the rise of technology, SMS has turned into a key communication tool for numerous individuals. Whether it’s for alerts or notifications, SMS fulfills numerous functions.
However, some users face challenges with SMS delivery. Problems may stem from network issues, device configurations, or software errors.
To resolve these issues, users can check their network connection or phone settings. Updating the device software can also help improve SMS functionality.
На нашем сайте вы найдете [url=https://karkasnye-doma0.ru/]каркасные дома спб под ключ[/url], идеально подходящие для сезонного отдыха и постоянного проживания.
Каркасные дома набирают популярность среди застройщиков. Эти конструкции предлагают множество преимуществ, включая быстроту возведения и хорошую теплоизоляцию.
Основным преимуществом каркасных конструкций является их доступная цена. Строительство каркасного дома снижает общие затраты как на материалы, так и на трудозатраты.
Также каркасные дома могут быть легко настроены под любые климатические условия. С их помощью можно строить комфортное жильё для проживания в любых климатических зонах.
Несмотря на преимущества, каркасные дома имеют и свои недостатки. Например, по сравнению с кирпичными домами, каркасные имеют меньшую огнестойкость. Эти факторы стоит учитывать, принимая решение о строительстве.
Мы ценим ваш вкус и идеи. С нами вы можете легко оформить [url=https://pechat-na-futbolkah0.ru/]футболка с принтом на заказ[/url] с любым изображением и получить результат, который вдохновит.
Печать на футболках — это отличный способ выразить свою индивидуальность. С помощью различных технологий можно превратить обычный текстиль в настоящие произведения искусства.
Методы печати на текстиле различаются по своим характеристикам и подходам. Трафаретный метод отличается высоким качеством и устойчивостью к выцветанию. Еще одним интересным методом является цифровая печать, позволяющая создавать сложные и детализированные изображения.
При выборе метода печати стоит учитывать не только дизайн, но и тип ткани. Не все ткани одинаково подходят для всех технологий печати, поэтому важно подбирать материал с учетом этого.
Объем заказа также влияет на выбор метода печати и его стоимость. Для небольших партий цифровая печать будет более выгодной, а для больших — трафаретная.
Каталог [url=https://karkasnye-doma0.ru/]каркасные дома в спб[/url] включает как компактные дачи, так и просторные дома для постоянного проживания. Подбираем вариант под ключ.
Каркасный дом становится всё более популярным выбором для строительства жилья. Такие дома имеют ряд преимуществ, таких как скорость строительства и высокая энергоэффективность.
Одним из главных плюсов каркасного дома является его экономичность. Строительство каркасного дома снижает общие затраты как на материалы, так и на трудозатраты.
Кроме того, каркасные дома легко адаптируются под различные климатические условия. С их помощью вы сможете создать комфортное жильё как в холодных, так и в тёплых регионах.
Тем не менее, каркасные дома не лишены недостатков, о которых стоит помнить. Одним из минусов каркасных домов является их меньшая пожарная безопасность по сравнению с традиционными кирпичными постройками. Эти факторы стоит учитывать, принимая решение о строительстве.
Упростите себе задачу планировки — [url=https://proekty-domov0.ru/]купить готовый проект дома[/url] можно прямо на сайте, где собраны проверенные архитектурные решения для любого вкуса и бюджета.
Проекты домов — это важный аспект для каждого, кто планирует строительство. Хорошо продуманный проект дома способен существенно облегчить весь процесс строительства.
Первый этап в разработке проекта — это выбор стиля и типа дома. Следует принимать во внимание не только свои желания, но и специфику участка, где планируется строительство.
После выбора стиля необходимо продумать планировку внутренних пространств. Важно предусмотреть удобство использования каждого пространства и их взаимосвязь.
Последним шагом является выбор строительных материалов и технологий. Качество и тип материалов напрямую повлияют на срок службы и эксплуатацию дома.
Получите максимум пользы из обучения — [url=https://seoflagman.ru/]продвижение сайта обучение курсы[/url] помогут систематизировать знания и применить их на практике уже после первого модуля.
Увеличение интереса к курсам SEO наблюдается среди множества бизнесменов. Участники курсов получают знания о том, как правильно оптимизировать сайты для появления в топах поисковиков.
Базовые знания по SEO — это первый шаг к успешной оптимизации. Курсы обычно охватывают такие темы, как ключевые слова, контент и ссылочная стратегия.
Практическое применение полученных знаний в реальных проектах значительно увеличивает их эффективность. Участники курсов работают с реальными проектами, что помогает им лучше подготовиться к будущей работе.
После завершения курсов студенты могут получить сертификаты, которые подтверждают их квалификацию. Сертификаты об окончании курсов SEO могут значительно повысить шансы на успешное трудоустройство.
Услуга [url=https://derevyannye-doma-pod-klyuch97.ru/]строительство деревянных домов под ключ москва[/url] охватывает все этапы: проект, фундамент, сборку, кровлю, инженерные системы и отделку.
Деревянные дома под ключ становятся все более популярными среди владельцев загородной недвижимости. Эти сооружения привлекают своим природным очарованием и экологичностью.
Одним из главных преимуществ таких домов является их быстрая постройка. Использование современных методов строительства позволяет быстро возводить такие дома.
К тому же, деревянные дома обладают отличными теплоизоляционными свойствами. В зимний период они обеспечивают уютное тепло, а в летнее время остаются комфортно прохладными.
Обслуживание деревянных домов не вызывает особых трудностей и не требует значительных усилий. Регулярная обработка древесины защитными средствами поможет продлить срок службы здания.
Предпринимателям будет выгоден [url=https://lizing-auto-top77.ru/]лизинг коммерческого транспорта для юридических лиц[/url], ведь он обеспечивает удобный способ обновления техники без сложных процедур.
Лизинг транспорта для бизнеса предоставляет множество преимуществ. Он позволяет получить необходимые автомобили без значительных первоначальных вложений.
Поскольку лизинг обычно включает техническое обслуживание, это уменьшает финансовую нагрузку на бизнес. Это дает возможность бизнесу сосредоточиться на своих целях, а не на ремонте транспортных средств.
Важно подобрать оптимальные условия договора лизинга для комфортного использования транспорта. Разные лизинговые компании предоставляют возможность выбора сроков договора и размеров ежемесячных взносов.
Необходимо помнить, что лизинг транспортных средств может дать налоговые льготы. Многие предприятия могут списывать платежи по лизингу как расходы, что снижает налоговую нагрузку.
Избавьтесь от хлопот, связанных с поиском монтажников и согласованиями. Закажите [url=https://gruzovoy-podjemnik15.ru/]грузовые подъемники под ключ[/url] и получите готовый результат.
Подъемное оборудование играет важную роль в современных строительных проектах. Оно используется для перемещения тяжелых грузов на высоту и облегчает рабочие процессы.
Разнообразие подъемного оборудования впечатляет: от подъемников до кранов и эскалаторов. Каждое из этих устройств имеет свои особенности и предназначение, что позволяет выбрать наиболее подходящее решение для конкретной задачи.
Перед использованием подъемного оборудования необходимо провести его технический осмотр. Проверка состояния техники позволяет избежать аварийных ситуаций и обеспечить безопасность.
Также важно соблюдать правила эксплуатации подъемного оборудования. Только при соблюдении всех инструкций можно гарантировать успешное выполнение задач.
Мы знаем, как важно найти женщину, готовую пройти с вами этот путь. У нас регулярно публикуются новые [url=https://deti-eto-schastie.ru/]суррогатное материнство объявления[/url] с актуальной информацией и проверенными данными.
Суррогатное материнство — это процесс, позволяющий создать семью для тех, кто не может стать родителем самостоятельно. Увеличение интереса к суррогатному материнству объясняется изменением общественного мнения и ростом технологий в области репродукции.
Суррогатное материнство делится на два основных типа, каждый из которых имеет свои преимущества и недостатки. При традиционном типе суррогатного материнства суррогатная мама становится биологической матерью, так как используется ее яйцеклетка. Гестационное суррогатное материнство предполагает, что эмбрион формируется вне тела суррогатной матери.
Перед тем, как принять решение о суррогатном материнстве, необходимо учитывать множество факторов. Пары должны быть готовыми к финансовым затратам, юридическим требованиям и эмоциональным вызовам, связанным с этим процессом. Ключевым моментом является выбор агентства, которое предоставит всестороннюю помощь на этапе подготовки и реализации суррогатного материнства.
Суррогатное материнство касается не только медицинских аспектов, но и социальных вопросов. Понимание и поддержка со стороны общества могут значительно повлиять на восприятие суррогатного материнства как положительного явления. В итоге, суррогатное материнство предоставляет возможность стать родителями тем, кто не может иметь детей, если это происходит с соблюдением всех необходимых норм и правил.
Мы предлагаем надежную [url=https://pechat-na-futbolkah0.ru/]принт на футболку[/url] с высокой детализацией и стойкостью цвета. Результат порадует даже самых взыскательных клиентов.
Создание дизайна на футболках позволяет подчеркнуть вашу уникальность. С помощью различных технологий можно превратить обычный текстиль в настоящие произведения искусства.
Среди самых распространенных технологий печати можно выделить несколько основных. Например, трафаретная печать известна своей долговечностью и яркостью красок. Еще одним интересным методом является цифровая печать, позволяющая создавать сложные и детализированные изображения.
Принимая решение о методе печати, стоит обратить внимание на материал, из которого изготовлена футболка. Некоторые ткани лучше подходят для трафаретной печати, в то время как другие — для цифровой.
Также имеет значение, сколько футболок вы планируете напечатать. Если вам нужно напечатать много футболок, лучше выбрать трафаретный метод, а цифровая печать больше подходит для небольших тиражей.
Эффективным выбором для инженерных систем станет [url=https://metall-tula1.ru/]труба электросварная[/url], которая отличается прочностью и долговечностью.
Металлопрокат является основой для многих промышленных процессов. Он находит широкое применение в строительстве, машиностроении и других сферах. Разнообразие металлопроката позволяет находить решения для самых различных потребностей.
К основным видам металлопроката относятся алюминий, сталь и другие металлические сплавы. У каждого типа металлопроката есть свои достоинства и недостатки. К примеру, сталь славится своей прочностью, в то время как алюминий привлекает легкостью и устойчивостью к коррозии.
Помимо этого, металлопрокат классифицируется по способу обработки. Металлопрокат может быть представлен в виде горячекатаных, холоднокатаных и профилированных изделий. Определение способа обработки зависит от предполагаемых условий использования и требований к материалу.
При покупке металлопроката важно учитывать несколько факторов. Качество металлопроката может значительно влиять на итоговый результат и долговечность конструкции. Поэтому рекомендуется выбирать проверенных производителей и внимательно проверять сертификаты.
Надежность, практичность и долговечность — вот что отличает [url=https://karkasnye-doma-vspb0.ru/]дома каркасные спб[/url]. Современные технологии позволяют возводить тёплые и красивые дома в короткие сроки.
Строительство каркасного дома стало весьма распространенным в последние годы. Они предлагают множество преимуществ, таких как быстрая сборка и высокая теплоизоляция.
Для успешного строительства каркасного дома необходимо обращать внимание на высокое качество материалов. Важным аспектом являются утеплитель и внешняя отделка, на которых не стоит экономить.
Важно учитывать проект и габариты при выборе каркасного дома. Правильное планирование позволит организовать пространство функционально и удобно.
В конечном счете, каркасный дом будет хорошим выбором для создания уютного и теплого жилища. Кроме того, возведение такого дома не требует больших временных и финансовых затрат.
Для тех, кто стремится к рациональности и быстрому старту строительства, предлагаем [url=https://proekty-domov0.ru/]купить готовый проект дома[/url], адаптированный под популярные строительные технологии.
Создание проектов домов — ключевой момент для тех, кто собирается строить. Правильно составленный проект дома может сделать строительный процесс гораздо более эффективным.
Первый шаг в проектировании дома заключается в выборе его стиля и конструкции. Следует принимать во внимание не только свои желания, но и специфику участка, где планируется строительство.
Следующий этап — обдумывание расположения внутренних комнат. Необходимо понять, как будут взаимодействовать разные комнаты и учесть их функциональность.
Кроме того, необходимо задуматься о том, какие материалы и технологии будут использоваться при строительстве. Качество и тип материалов напрямую повлияют на срок службы и эксплуатацию дома.
Вдохновляющая атмосфера и спокойствие волн сопровождают [url=https://morskie-progulki-1sochi.ru/]прогулка на яхте в сочи[/url]. Это отличная альтернатива шумным экскурсиям и толпе на пляже.
Морские прогулки в Сочи – это уникальный способ провести время у моря. Каждый год тысячи туристов выбирают этот курорт для создания незабываемых воспоминаний.
Сочи изобилует предложениями по организации запоминающихся морских прогулок. Посетители могут выбрать как короткие экскурсии, так и длительные путешествия вдоль побережья.
Во время морской прогулки можно насладиться потрясающими видами на море и горы. Некоторые экскурсии предлагают шанс увидеть дельфинов и других животных в их естественной среде обитания.
Не упустите шанс сделать фотографии, которые будут напоминать о вашем путешествии. Прогулки на море – замечательный способ провести время с близкими.
Уборка с гарантией качества и полной отчётностью. [url=https://kliningovaya-kompaniya-v-spb-01.ru/]клининговые услуги спб[/url] помогут поддерживать порядок и уют каждый день.
Профессиональные очистительные услуги в Санкт-Петербурге – это необходимость для множества людей и компаний. Чистота и порядок имеют большое значение в рабочей среде. На рынке доступны различные клининговые фирмы.
Определение нужд в клининге – первый шаг к чистоте. Необходимо выяснить, требуется ли уборка жилых помещений или коммерческих пространств. Не забудьте учесть, как часто вам нужна уборка.
Вторым ключевым шагом является поиск надежной компании. Обратите внимание на отзывы клиентов. Надежные компании предоставляют гарантии на свои услуги.
В завершение, не забудьте ознакомиться с ценами на услуги клининга. Разные компании могут предлагать различные расценки на свои услуги. Дорогие услуги не всегда гарантируют высокое качество.
Быстрый и качественный [url=https://apple-tula1.ru/]ремонт iPad[/url] помогает сохранить устройство в отличном состоянии, возвращая к жизни все функции планшета.
Apple является одним из самых известных и уважаемых брендов в мире технологий. Ассортимент продукции Apple включает в себя множество устройств, таких как iPhone, iPad и Mac.
Одним из ключевых факторов успеха Apple является инновационный дизайн. Компания постоянно стремится к улучшению пользовательского опыта и функциональности своих устройств.
Кроме того, экосистема Apple создает уникальный опыт для пользователей. Устройства компании легко интегрируются друг с другом, что делает использование их еще проще.
Несмотря на свою цену, устройства Apple остаются в большом спросе на рынке. Покупатели предпочитают продукты Apple за их высокое качество, надежность и использование современных технологий.
Уютный катер, приятная компания и морская свежесть — [url=https://morskie-progulki-1sochi.ru/]прогулка на яхте сочи[/url] подарит вам гармонию и незабываемые эмоции.
Морские прогулки в Сочи – это уникальный способ провести время у моря. Сочи привлекает внимание миллионов путешественников, стремящихся к расслаблению и приключениям.
Вдоль побережья Сочи расположены различные компании, предлагающие услуги морских прогулок. Посетители могут выбрать как короткие экскурсии, так и длительные путешествия вдоль побережья.
Во время морской прогулки можно насладиться потрясающими видами на море и горы. Некоторые экскурсии предлагают шанс увидеть дельфинов и других животных в их естественной среде обитания.
Не забывайте захватить с собой фотоаппарат, чтобы запечатлеть эти мгновения. Морские прогулки в Сочи – это отличный способ провести время с друзьями и семьей.
Мы предлагаем [url=https://genuborka11.ru/]заказать генеральную уборку квартиры в москве[/url] на удобное для вас время. Всё оборудование и средства — наши, вы отдыхаете.
Процесс генеральной уборки представляет собой существенное событие для в жизни любой семьи. Такой процесс способствует обеспечивать порядок и свежесть в жилом пространстве.
Для успешной генеральной уборки необходимо составить план. Сначала определите, какие зоны вы хотите убрать. Такой подход позволит избежать хаоса.
Не забывайте о подготовке нужных материалов. Необходимыми инструментами будут чистящие средства, пылесос и тряпки. Собранные в одном месте средства помогут сэкономить время.
После того, как все подготовлено, стоит приступать к уборке. Сосредоточьтесь на одной комнате за раз. Таким образом, проще отслеживать прогресс.
Узнайте, кто сейчас на вершине профессионального рейтинга столицы. Мы собрали [url=https://best-photographers-moscow.ru/]лучшие фотографы москвы[/url] по отзывам клиентов, качеству работ и востребованности.
Лучшие фотографы являются важной частью творческого мира. В данном материале мы представим нескольких известных специалистов, чьи работы захватывают дух.
В числе первых можно отметить фотографа, чьи работы известны повсюду. Этот творец делает потрясающие снимки, которые передают атмосферу и эмоции.
Не менее талантливым является фотограф, известный своим мастерством в портретной фотографии. Картины этого мастера выделяются особым стилем и умением запечатлеть индивидуальность.
Финальным героем нашей статьи станет фотограф, известный своими великолепными пейзажами. Его уникальный взгляд на окружающий мир помогает увидеть обыденные места по-новому.
Насладитесь свободой и красотой черноморского побережья, выбрав [url=https://arenda-yaht-v-sochi-1.ru/]яхта аренда сочи[/url] для вашего незабываемого путешествия.
Аренда яхты — это отличный способ провести время на воде. Многие люди выбирают этот вид отдыха в летний сезон.
Процесс проката яхты может вызвать некоторые трудности. Знание основных моментов поможет упростить процесс аренды яхты.
Первым делом, вам необходимо определиться с маршрутом. Это поможет вам выбрать нужный размер и тип яхты.
Наконец, не забудьте внимательно прочитать условия аренды. Внимательное изучение условий аренды предотвратит нежелательные проблемы.
Спланируйте незабываемый отдых у побережья с предложением [url=https://arenda-1yaht-v-sochi.ru/]аренда яхт сочи[/url], которое включает все для вашего комфорта. Яхты разных форматов и маршруты на любой вкус.
Организация аренды яхты — отличный вариант для любителей приключений на воде. Вы можете выбрать скорость, комфорт или размер судна, в зависимости от ваших предпочтений.
Прежде чем взять яхту в аренду, стоит внимательно рассмотреть варианты. Каждая компания предлагает различные условия аренды, включая цены и дополнительные услуги.
Важно убедиться в прозрачности всех условий, прежде чем подписать соглашение. Следует узнать, что входит в стоимость аренды, а что является дополнительной платой.
Аренда яхты — это шанс провести время с друзьями или семьей и насладиться природой. Неважно, планируете ли вы спонтанный отдых или заранее запланированное мероприятие, яхта будет прекрасным местом.
Незаменим для магазинов, складов, производственных цехов и автомастерских. Надежный [url=https://gruzovoy-podjemnik15.ru/]грузовой подъемник[/url] обеспечит бесперебойные процессы.
Важность подъемного оборудования в строительстве трудно переоценить. Подъемное оборудование существенно упрощает задачу по перемещению больших грузов на значительные высоты.
Существует множество видов подъемного оборудования, включая подъемники, краны и эскалаторы. Каждый тип подъемного оборудования находит свое применение в зависимости от специфики работы.
Технический осмотр подъемного оборудования — это важный шаг перед его эксплуатацией. Проверка состояния техники позволяет избежать аварийных ситуаций и обеспечить безопасность.
Соблюдение правил использования подъемного оборудования является ключевым фактором безопасности. Только при соблюдении всех инструкций можно гарантировать успешное выполнение задач.
Экономьте ресурсы и время, выбрав [url=https://lizing-auto-top77.ru/]коммерческие авто в лизинг[/url]. Это надёжный путь к обновлению автопарка для растущих компаний.
Лизинг коммерческого транспорта — это отличная возможность для бизнеса. Он позволяет получить необходимые автомобили без значительных первоначальных вложений.
Важно отметить, что лизинговые компании часто предлагают выгодные условия по обслуживанию. Это дает возможность бизнесу сосредоточиться на своих целях, а не на ремонте транспортных средств.
Важно подобрать оптимальные условия договора лизинга для комфортного использования транспорта. Некоторые компании предлагают гибкие сроки и размеры платежей, что делает лизинг доступным для разных бизнесов.
Необходимо помнить, что лизинг транспортных средств может дать налоговые льготы. Компаниям доступна возможность вычета затрат на лизинг из налогооблагаемой базы.
Хотите креативный подарок или рекламную продукцию? [url=https://pechat-na-futbolkah0.ru/]заказ футболки с принтом[/url] поможет реализовать любую дизайнерскую идею — легко, быстро и недорого.
Футболки с индивидуальными принтами — отличное средство самовыражения. Технологии печати открывают широкие горизонты для дизайнеров и любителей моды.
Среди самых распространенных технологий печати можно выделить несколько основных. Например, трафаретная печать известна своей долговечностью и яркостью красок. Еще одним интересным методом является цифровая печать, позволяющая создавать сложные и детализированные изображения.
Важно помнить, что выбор ткани влияет на качество печати и долговечность изделия. Разные материалы могут по-разному реагировать на различные методы печати.
Количество заказываемых футболок может существенно изменить ваши затраты на печать. Для массового производства чаще используется трафаретная печать, а для небольших заказов — цифровая.
Нужны чистота и порядок? Надежная [url=https://kliningovaya-kompaniya-v-moskve-01.ru/]клининговая фирма[/url] предоставит услуги на высоком уровне, с учётом всех пожеланий и соблюдением сроков.
Клининг в Москве — это важная услуга, которая помогает поддерживать чистоту и порядок в домах и офисах. На рынке представлено множество клининговых компаний с разнообразными предложениями.
Необходимо понимать, что клининг может включать как плановые, так и разовые уборки. Регулярная уборка подразумевает поддержание чистоты в помещениях, что важно для здоровья и комфорта.
Такой вид уборки, как генеральная, предполагает детальную чистку всех поверхностей и углов. Различные клининговые компании могут предложить клиентам различные уровни обслуживания, что позволяет выбрать оптимальный вариант.
Для выбора надежной клининговой компании важно учитывать отзывы и репутацию. Выбор компании с хорошей репутацией помогает избежать неприятностей и получить высокий уровень сервиса.
Чистота начинается с комплексного подхода — [url=https://genuborka1.ru/]ген уборка квартиры[/url] позволит освежить обстановку и создать здоровый микроклимат.
Процесс генеральной уборки является ключевым для создания комфортной и уютной атмосферы в вашем доме. Мы все знаем, как иногда важно сделать генеральную уборку в своих жилищах.
Важно определить порядок, в котором вы будете убирать каждую из комнат. Выбор помещения может зависеть от уровня загрязненности или вашей личной предрасположенности.
После выбора помещения следует подготовить необходимые инструменты и средства для уборки. Подготовьте чистящие порошки, губки и ведра — так вы будете готовы к убиранию.
Важно разработать план уборки, чтобы не упустить ни одну деталь. Обратите внимание на все труднодоступные места, это поможет сделать уборку более качественной.
Investing in a performance? Understanding the [url=https://drone-show-0.com/]drone show cost[/url] helps ensure you receive exceptional value and a tailored solution that suits your venue and goals.
Drone light shows offer a modern approach to captivating audiences. They utilize hundreds of drones to form mesmerizing patterns and shapes overhead.
Versatility is one of the significant benefits of using drones for light shows. From celebrating holidays to marking special occasions, there seems to be no limit to their applications.
Drone light shows are also recognized for their minimal environmental impact. Drones do not produce harmful emissions like fireworks do, making them a greener alternative.
The future of aerial entertainment is bright, thanks to advancements in drone technology. In the years to come, we are likely to witness increasingly elaborate and coordinated displays.
Aporta un giro innovador a tus celebraciones contratando una [url=https://show-de-drones-0.com/]compania de exhibicion de drones[/url] que crea coreografias aereas impactantes, completamente personalizadas.
Los shows de drones se han vuelto cada vez mas comunes en diversas celebraciones. Esos eventos con drones crean una experiencia visual impresionante que capta la atencion de grandes audiencias.
Los drones son capaces de realizar coreografias complejas en el cielo. Esto se debe a su avanzada tecnologia y a la programacion minuciosa que los acompana.
Uno de los aspectos mas destacados de estos espectaculos es la sincronizacion perfecta entre los drones. La combinacion de luces y movimientos crea un show impactante que maravilla a todos los asistentes.
La evolucion constante en la industria de drones augura un futuro emocionante para los espectaculos de luces y acrobacias. En el futuro, podriamos asistir a espectaculos mas innovadores que llevaran la experiencia a un nuevo nivel.
Для фасовки антисептиков, шампуней и других жидкостей подойдут [url=https://flakony-optom-msk.ru/]полимерные флаконы[/url] — прочные, лёгкие и доступные в различных объёмах.
Закупка флаконов оптом — это выгодное решение для бизнеса. Многие производители и оптовые компании предлагают разнообразные варианты флаконов на любой вкус.
Выбор материала флакона имеет большое значение для сохранности продукта. Каждый тип флаконов обладает уникальными характеристиками, влияющими на их применение.
При оптовых закупках стоит обратить внимание на условия поставки и минимальные объемы заказа. Также проверьте репутацию поставщика, чтобы избежать некачественной продукции.
Покупка флаконов оптом значительно упрощает логистику и планирование. Использование флаконов оптом может повысить конкурентоспособность вашего бизнеса.
тара пластиковая на заказ оптом [url=flakony-optom-msk.ru]flakony-optom-msk.ru[/url]
Надежный источник флиса для московских мастерских и ателье. [url=https://flis-optom.ru/]флис ткань купить в москве[/url] с удобной доставкой или самовывозом вы можете прямо сейчас, выбрав нужный товар в нашем каталоге.
Материал флис является прекрасным выбором для зимней одежды. Он отличается легкостью и теплотой, что делает его популярным. Многие люди выбирают флисовые вещи для активного отдыха. Изделия из флиса, такие как кофты и куртки, эффективно удерживают тепло и обладают быстрым временем высыхания.
Важно учитывать качество материала при покупке флиса. Низкокачественный флис может быстро потерять свои свойства. Рекомендуется приобретать флис от известных брендов, чтобы гарантировать его долговечность. Так вы сможете избежать неожиданностей в процессе эксплуатации.
Флис отлично подходит не только для верхней одежды, но и для изготовления различных аксессуаров. Изделия из флиса, такие как шапки, перчатки и шарфы, прекрасно дополняют зимний ансамбль. Их тепло и комфорт сделают холодные дни более приятными. Не забывайте о возможности дополнить свой зимний гардероб флисовыми аксессуарами.
Заключая, флис — это универсальный материал, который должен быть в арсенале каждого. Флис объединяет в себе тепло, легкость и функциональность, что делает его отличным вариантом. Не упускайте из виду разнообразие флиса: от верхней одежды до аксессуаров. Следовательно, инвестирование в флис станет правильным решением.
флис цена за метр [url=https://www.flis-optom.ru]https://www.flis-optom.ru[/url]
Идеальная упаковка для пищевых продуктов, электроники, косметики и других товарных групп. [url=https://proizvodstvo-korobok.ru/]производство картонной упаковки[/url] учитывает специфику.
Создание коробок играет ключевую роль в сфере упаковки. Коробки необходимы для транспортировки и хранения товаров.
Коробки бывают разнообразных типов, различающихся по материалам и форм-фактору. Коробки из картона наиболее востребованы из-за своей популярности и экологичности.
Важно, чтобы в процессе изготовления коробок использовались высококачественные материалы. Обеспечение качества материалов является залогом надежной упаковки и безопасности товара.
В современных условиях многие компании стремятся оптимизировать свои производственные процессы. Внедрение автоматизации и инновационных технологий позволяет сократить расходы.
производство картонных коробок [url=https://proizvodstvo-korobok.ru]https://proizvodstvo-korobok.ru[/url]
We offer the widest assortment of high-quality natural food flavors.
More detailed information on the links [url=https://vkus-msk.ru/aroma-magic/]вкусовые ароматизаторы [/url] and [url=https://vkus-msk.ru/aroma-magic/]пищевые вкусовые добавки [/url]
Our flavors are ideal for creating the best dishes.
Аромат парфюма с сандалом обладает неповторимой легкостью и глубиной. Сандал добавляет парфюму ощущение роскоши и загадочности.
Разнообразные ароматы с сандалом можно найти практически в любом магазине парфюмерии. Некоторые композиции подчеркнут сладкие оттенки, а другие – свежие древесные ноты.
Сандал находит применение в композициях, сочетающих цветочные и древесные ноты. Парфюмы на его основе часто выбирают для вечерних выхода или особых случаев.
Не стоит забывать, что сандал также применяется в ароматерапии благодаря своим расслабляющим свойствам. Парфюм на основе сандала будет отличным подарком для любителей изысканных ароматов.
парфюм сандал [url=https://www.sandalparfums.ru/]https://www.sandalparfums.ru/[/url]
Комфортный и наполненный впечатлениями [url=https://otdyh-arhipo-osipovka1.ru/]Архипо-Осиповка отдых[/url] начинается с выбора правильного жилья. Наш каталог — ключ к вашему идеальному отпуску.
Архипо-Осиповка — это замечательный курорт на побережье Черного моря. Местные пляжи, теплые воды и красивые виды делают этот курорт идеальным для семейного отдыха и молодежных путешествий.
В Архипо-Осиповке есть множество вариантов размещения. От современных гостиниц до традиционных частных домов — туристы найдут здесь подходящее жилье на любой вкус.
Главная достопримечательность Архипо-Осиповки — это не только пляжи, но и удивительная природа. Не упустите возможность увидеть местные красоты: водопады и заповедные зоны ждут своих туристов.
Кулинарные традиции Архипо-Осиповки также заслуживают внимания. Рестораны и кафе предлагают блюда из свежих морепродуктов и местных овощей.
снять жилье в архипо осиповке 2025 [url=https://www.otdyh-arhipo-osipovka1.ru/]https://www.otdyh-arhipo-osipovka1.ru/[/url]
Доверьте уборку профессионалам — [url=https://kliningovaya-kompaniya-1.ru/]служба клининга[/url] предложит персональный подход, надежность и оптимальное соотношение цены и качества.
Клининг в Москве превращается в востребованное направление, особенно среди занятых горожан. С каждым годом все больше людей осознают важность чистоты в своем доме и на рабочем месте.
Клининговые компании предлагают широкий спектр услуг, включая уборку квартир, офисов и специализированные услуги. Каждая клининговая компания в Москве старается привлечь клиентов уникальными предложениями и высокими стандартами качества.
Профессиональная уборка подразумевает использование специализированного оборудования и качественных чистящих средств. Компании по клинингу инвестируют в обучение персонала, чтобы клиенты могли быть уверены в качестве предоставляемых услуг.
В Москве стоимость клининговых услуг зависит от множества факторов, включая размер помещения и требования клиента. Важно заранее изучить мнения клиентов о клининговых агентствах, чтобы выбрать наиболее подходящую компанию.
клининговая компания в москве [url=http://kliningovaya-kompaniya-1.ru/]http://kliningovaya-kompaniya-1.ru/[/url]
Сэкономьте на покупке техники с помощью [url=https://lizing-auto-top77.ru/]лизинга коммерческих автомобилей для юридических лиц[/url]. Ваш бизнес получит транспорт, не выводя средства из оборота.
Лизинг автомобилей для коммерческих нужд является выгодным решением для компаний. Лизинг дает возможность пользоваться новыми автомобилями, не тратя много средств upfront.
При этом, лизинг требует минимальных затрат на обслуживание. Это дает возможность бизнесу сосредоточиться на своих целях, а не на ремонте транспортных средств.
Важно подобрать оптимальные условия договора лизинга для комфортного использования транспорта. Фирмы могут адаптировать условия лизинга под свои финансовые возможности.
Необходимо помнить, что лизинг транспортных средств может дать налоговые льготы. Это делает лизинг еще более привлекательным для бизнеса, стремящегося минимизировать затраты.
Регулярный клининг, уборка после ремонта, наведение порядка перед сдачей объекта — [url=https://kliningovaya-kompaniya-v-spb-01.ru/]клининговые услуги в санкт петербурге[/url] под ключ от проверенного исполнителя.
Клининг в Санкт-Петербурге – это популярное решение для многих людей и бизнесов. Чистое пространство создает комфорт в повседневной жизни. На рынке доступны различные клининговые фирмы.
Определение нужд в клининге – первый шаг к чистоте. Вам стоит решить, нужны ли вам услуги для дома или бизнеса. Важно решить, как часто вы планируете проводить уборку.
Следующий шаг – выбрать надежную клининговую фирму. Ищите мнения других клиентов о компаниях. Надежные компании предоставляют гарантии на свои услуги.
В завершение, не забудьте ознакомиться с ценами на услуги клининга. Цены на клининговые услуги могут различаться в зависимости от фирмы. Не всегда высокая цена означает лучшее качество.
Sorprende a tu audiencia con [url=https://show-de-drones-0.com/]la compania de espectaculos de luces con drones[/url] que convierte cualquier cielo en una pantalla de luz animada e impresionante.
El espectaculo de drones ha cobrado popularidad en los ultimos anos. Esos eventos con drones crean una experiencia visual impresionante que capta la atencion de grandes audiencias.
Los drones son capaces de realizar coreografias complejas en el cielo. Esto se debe a su avanzada tecnologia y a la programacion minuciosa que los acompana.
Uno de los aspectos mas destacados de estos espectaculos es la sincronizacion perfecta entre los drones. La combinacion de luces y movimientos crea un show impactante que maravilla a todos los asistentes.
El futuro de estos espectaculos parece prometedor, con avances constantes en la tecnologia de drones. Proximamente, podriamos ver shows aun mas elaborados y creativos que desafian los limites de la imaginacion.
Мы предлагаем вам [url=https://derevyannye-doma-pod-klyuch97.ru/]деревянный дом под ключ[/url], созданный по индивидуальному проекту, с учётом ваших пожеланий и с полной отделкой под заселение.
В последнее время деревянные дома под ключ привлекают внимание людей, стремящихся к уютному загородному отдыху. Эти сооружения привлекают своим природным очарованием и экологичностью.
Среди основных преимуществ деревянных домов можно выделить скорость их возведения. С помощью современных технологий можно построить такие здания в минимальные сроки.
Деревянные дома славятся хорошей теплоизоляцией. В зимний период они обеспечивают уютное тепло, а в летнее время остаются комфортно прохладными.
Уход за деревянными домами довольно прост и не требует больших усилий. Периодическая обработка древесины защитными составами значительно увеличивает долговечность дома.
Для тех, кто ценит удобство, наш сайт предлагает [url=https://otdyh-dzhubga1.ru/]Джубга снять жилье[/url] с прямыми контактами владельцев и прозрачной системой бронирования без переплат.
Джубга — популярное место для отдыха на Черноморском побережье. Этот курорт славится своими красивыми пляжами и мягким климатом.
В Джубге представлены разнообразные варианты размещения: от гостиниц до частного сектора. Гостеприимные владельцы готовы предложить своим гостям уютные номера и демократичные цены.
Пляжи Джубги усыпаны мелким золотистым песком и окружены великолепной природой. Многие отдыхающие предпочитают проводить время на пляже, наслаждаясь купанием и загоранием.
Кухня курорта порадует вас разнообразием блюд и свежими морепродуктами. Не забудьте посетить местные кафе, где готовят вкуснейшие блюда из свежих продуктов.
снять жилье в джубге [url=https://www.otdyh-dzhubga1.ru]https://www.otdyh-dzhubga1.ru[/url]
Летний сезон 2025 не за горами — бронируйте [url=https://otdyh-tyapse1.ru/]жилье в туапсе 2025[/url] уже сейчас. Удобные условия и выгодные цены ждут вас на сайте.
Туапсе предлагает уникальный отдых на побережье Черного моря. Город славится своими пляжами, красивыми пейзажами и разнообразными развлечениями.
Туапсе предлагает множество вариантов жилья, которые подойдут на любой вкус и бюджет. В Туапсе есть возможность остановиться в комфортабельных отелях, уютных гостиницах или арендовать квартиру.
Стоимость проживания в Туапсе может изменяться в зависимости от времени года и выбранного жилья. Летом, как правило, цены выше, но можно найти и бюджетные варианты.
Мягкий климат Туапсе делает его популярным направлением для отдыха. Время с мая по сентябрь наиболее благоприятно для отдыха на побережье Туапсе.
отдых на море в туапсе [url=https://www.otdyh-tyapse1.ru]https://www.otdyh-tyapse1.ru[/url]
Redefine public celebrations with a dynamic [url=https://drone-show-0.com/]dron show[/url], merging advanced flight patterns and cutting-edge lighting to deliver a mesmerizing visual experience.
Drone light shows offer a modern approach to captivating audiences. They utilize hundreds of drones to form mesmerizing patterns and shapes overhead.
One of the key advantages of drone light shows is their versatility. These performances can be tailored for numerous events, ranging from festivals to corporate gatherings.
The ecological footprint of these aerial displays is another critical consideration. By using drones, organizers significantly reduce the environmental damage typically associated with fireworks.
As technology continues to evolve, the future of drone light shows looks promising. We can expect to see even more intricate designs and synchronized performances in upcoming years.
Оцените качество звука и удобство с современными наушниками [url=https://apple-tula1.ru/]AirPods[/url], идеально подходящими для активного образа жизни и повседневного использования.
Apple – один из ведущих брендов в области технологий. Компания предлагает широкий ассортимент продуктов и услуг, включая iPhone, iPad и Mac.
Инновационный дизайн продукции Apple – один из ключевых факторов ее успеха. Стремление к улучшению пользовательского опыта и функциональности является приоритетом для Apple.
Кроме того, экосистема Apple создает уникальный опыт для пользователей. Устройства компании легко интегрируются друг с другом, что делает использование их еще проще.
Несмотря на высокую стоимость, продукты Apple пользуются большим спросом. Клиенты ценят надежность, высокое качество и передовые технологии, которые предоставляет Apple.
Организуйте закупку на выгодных условиях, оформив [url=https://flis-optom.ru/]флис оптом[/url] с оперативной доставкой. Широкий выбор тканей доступен прямо со склада.
Флис — идеальный вариант для создания теплой одежды в зимний сезон. Данный материал славится своей легкостью и теплоизоляционными свойствами, что обеспечивает его популярность. Часто флисовые изделия выбирают те, кто предпочитает активный образ жизни. Изделия из флиса, такие как кофты и куртки, эффективно удерживают тепло и обладают быстрым временем высыхания.
При выборе флиса стоит обратить внимание на качество материала. Искусственный флис низкого качества может быстро потерять свои функциональные свойства. Выбирайте изделия от проверенных производителей, что гарантирует долговечность. Так вы сможете избежать неожиданностей в процессе эксплуатации.
Флис отлично подходит не только для верхней одежды, но и для изготовления различных аксессуаров. Изделия из флиса, такие как шапки, перчатки и шарфы, прекрасно дополняют зимний ансамбль. Тепло и комфорт флисовых аксессуаров сделают даже самые холодные дни более уютными. Обязательно рассмотрите варианты флисовых аксессуаров для своего зимнего гардероба.
Заключая, флис — это универсальный материал, который должен быть в арсенале каждого. Он сочетает в себе тепло, легкость и практичность, что делает его идеальным выбором. Не упускайте из виду разнообразие флиса: от верхней одежды до аксессуаров. Следовательно, инвестирование в флис станет правильным решением.
флис ткань цена за 1 метр [url=http://www.flis-optom.ru/]http://www.flis-optom.ru/[/url]
Прямые поставки качественной картонной упаковки от производителя. Наш [url=https://proizvodstvo-korobok.ru/]завод картонной упаковки[/url] работает для вашего удобства и экономии.
Производство коробок является важным процессом в упаковочной промышленности. Коробки служат основным средством защиты товаров во время их транспортировки.
Существует множество видов коробок, которые отличаются по материалу и форме. Самыми распространенными являются картонные коробки, которые также считаются более экологичными.
Качество материалов играет решающую роль в производстве коробок. Такой подход гарантирует устойчивость упаковки и защищенность содержимого.
В современных условиях многие компании стремятся оптимизировать свои производственные процессы. Использование автоматизированных систем и современных технологий существенно снижает издержки.
картонные короба производство [url=http://www.proizvodstvo-korobok.ru]http://www.proizvodstvo-korobok.ru[/url]
Чтобы дом всегда оставался уютным, воспользуйтесь [url=https://kliningovaya-kompaniya-v-moskve-01.ru/]услугами клининга в москве[/url]. Мы обеспечим тщательную уборку в удобное для вас время.
Клининг в Москве — это важная услуга, которая помогает поддерживать чистоту и порядок в домах и офисах. Существует множество компаний, предлагающих широкий спектр услуг клининга.
Необходимо понимать, что клининг может включать как плановые, так и разовые уборки. Периодическая уборка помогает поддерживать порядок в жилых и коммерческих помещениях, что особо важно в условиях мегаполиса.
Генеральная уборка, в свою очередь, включает в себя более тщательную работу, требующую больше времени и ресурсов. Различные клининговые компании могут предложить клиентам различные уровни обслуживания, что позволяет выбрать оптимальный вариант.
Для выбора надежной клининговой компании важно учитывать отзывы и репутацию. Достойные клининговые фирмы обеспечивают четкие условия работы и гарантии на предоставляемые услуги.
Парфюм с сандалом имеет уникальный и запоминающийся аромат. Сандал сразу вызывает ассоциации с теплом и экзотикой.
Парфюмеры создают широкий ассортимент композиций с использованием сандала. Некоторые парфюмы акцентируют внимание на сладости, а другие – на древесности.
Этот компонент часто используется как основа для создания гардений и цветочных ароматов. Парфюмы на его основе часто выбирают для вечерних выхода или особых случаев.
Помимо своей уникальной ароматики, сандал обладает и терапевтическими свойствами. Такой аромат станет чудесным презентом для близкого человека.
парфюм сандал [url=https://www.sandalparfums.ru]https://www.sandalparfums.ru[/url]
Чистота в помещении — это комфорт и порядок. Профессиональная [url=https://kliningovaya-kompaniya-1.ru/]клининговая служба в Москве[/url] обеспечит результат, достойный доверия и высокой оценки.
Клининг в Москве — это услуга, которая становится все более популярной среди жителей столицы. С каждым годом все больше людей осознают важность чистоты в своем доме и на рабочем месте.
Фирмы, занимающиеся клинингом, предлагают различные услуги: от уборки помещений до мойки окон и химчистки. Каждая клининговая компания в Москве старается привлечь клиентов уникальными предложениями и высокими стандартами качества.
Профессиональная уборка подразумевает использование специализированного оборудования и качественных чистящих средств. Фирмы, предоставляющие услуги клининга, часто обучают своих сотрудников, чтобы гарантировать высокий уровень сервиса.
Стоимость клининговых услуг в Москве варьируется в зависимости от объема работ и уровня компании. Прежде чем принимать решение, стоит ознакомиться с отзывами о различных клининговых компаниях и оценить их предложения.
заказать клининг в москве [url=https://www.kliningovaya-kompaniya-1.ru/]https://www.kliningovaya-kompaniya-1.ru/[/url]
Планируете отпуск? Смотрите актуальные предложения [url=https://otdyh-dzhubga1.ru/]Джубга отдых цены[/url] и выбирайте жильё без посредников по выгодным тарифам на сезон 2025 года.
Джубга — популярное место для отдыха на Черноморском побережье. Этот курорт славится своими красивыми пляжами и мягким климатом.
На Джубге туристы могут насладиться яркими развлечениями и комфортным жильем. Здесь вы всегда сможете найти подходящее жилье по разумной цене.
Пляжи Джубги усыпаны мелким золотистым песком и окружены великолепной природой. Многие отдыхающие предпочитают проводить время на пляже, наслаждаясь купанием и загоранием.
Особое внимание в Джубге стоит уделить местной кухне. Не забудьте посетить местные кафе, где готовят вкуснейшие блюда из свежих продуктов.
снять жилье в джубге 2025 [url=https://www.otdyh-dzhubga1.ru/]https://www.otdyh-dzhubga1.ru/[/url]
С помощью [url=https://sms-activation-service.com/]сервис смс активаций[/url] можно активировать аккаунты в соцсетях, мессенджерах и приложениях без использования личного телефона.
SMS activation is a crucial process that ensures secure account verification. This method is widely used across various platforms, as it adds an extra layer of security.
To initiate SMS activation, users typically need to provide their mobile number. Once the number is submitted, a unique code is sent via text message.
The validation process is completed once the user enters the received code on the site. It’s a straightforward method that effectively prevents unauthorized access.
While SMS activation is beneficial, it is not without its challenges. For instance, users may face issues such as delayed message delivery. Additionally, not having access to a reliable mobile service can hinder the process.
sms-activation-service [url=https://sms-activation-service.com/]https://sms-activation-service.com/[/url]
Access global verifications easily using [url=https://online-sms.org/]onlinesim[/url], perfect for quick and safe code delivery.
Receiving SMS online has become increasingly popular in today’s digital world. As technology evolves, more individuals prefer to receive SMS communications online rather than through their mobile devices.
One of the primary advantages of this method is privacy. Users can avoid exposing their personal phone numbers while still staying connected.
Additionally, many online services provide virtual numbers for SMS reception. Users can choose to utilize these virtual numbers for a short period or for ongoing use.
To summarize, the ability to receive SMS messages online presents important advantages, such as enhanced privacy and ease of use. As this trend continues to grow, it is expected to become increasingly mainstream.
receive sms online instantly [url=http://www.online-sms.org/]http://www.online-sms.org/[/url]
Планируя поездку, уточните актуальные [url=https://otdyh-arhipo-osipovka1.ru/]отдых в Архипо-Осиповке 2025 цены[/url] в нашем каталоге. Сравните предложения и выберите оптимально.
Отдых в Архипо-Осиповке становится все более востребованным среди туристов. Местные пляжи, теплые воды и красивые виды делают этот курорт идеальным для семейного отдыха и молодежных путешествий.
В Архипо-Осиповке есть множество вариантов размещения. От роскошных отелей до уютных гостевых домов — каждый турист сможет выбрать подходящий вариант.
На курорте можно не только наслаждаться морем, но и исследовать его окрестности. Посетить местные водопады, горные озера и экскурсии по заповедникам стоит каждому туристу.
Кулинарные традиции Архипо-Осиповки также заслуживают внимания. Местные заведения порадуют разнообразием меню из морепродуктов и других вкусностей.
жилье в архипо осиповке 2025 [url=http://www.otdyh-arhipo-osipovka1.ru/]http://www.otdyh-arhipo-osipovka1.ru/[/url]
[url=https://flakony-optom-msk.ru/]пластиковые флаконы[/url]
Флаконы оптом пользуются высоким спросом среди предпринимателей. На рынке представлено множество моделей флаконов, которые могут удовлетворить различные запросы.
Следует обращать внимание на качество и тип материала флаконов при их оптовом приобретении. Среди производителей можно найти как стеклянные, так и пластиковые флаконы.
Разнообразные способы упаковки флаконов также могут быть важны. Некоторые компании предлагают индивидуальную упаковку, что может повысить привлекательность товара.
Не забывайте о ценовой политике при выборе оптовых поставок. Сравнивая цены у различных поставщиков, можно выбрать наилучший вариант для вашего бизнеса.
Use [url=https://temporary-phone-number-sms.com/]temporary mobile number[/url] to receive one-time SMS.
Using a temp number can be beneficial for numerous reasons. It can help maintain privacy while signing up for services or verifying accounts.
One significant reason to use a temporary phone number is to safeguard your privacy. Instead of sharing your real phone number, you can use a temporary one to receive messages and calls.
Another advantage is the ability to manage spam effectively. When you sign up for online services that require a phone number, you risk getting bombarded with promotional messages.
In conclusion, a temp number can be an excellent resource for protecting your privacy and managing communications. Think about opting for a temp number when registering for services to enhance your privacy.
[url=https://flis-optom.ru/]материал флис купить[/url]
Флис — отличный выбор для занятий спортом и активного времяпрепровождения. Он легкий, теплый и быстро сохнет, что делает его идеальным для различных погодных условий.
При выборе флиса стоит обратить внимание на его плотность и состав. Разные производители предлагают различные варианты: от тонких до более плотных моделей. Плотные варианты сохраняют тепло, а тонкие — идеальны для активного использования.
Флис можно купить как в специализированных магазинах, так и в интернет-магазинах. При заказе онлайн всегда есть возможность ознакомиться с отзывами и характеристиками изделия. Но не забывайте проверять репутацию продавца.
Также стоит учитывать, что флис может иметь различные назначение: от повседневной одежды до специализированной. Решение о покупке следует принимать исходя из ваших личных требований и предпочтений. Правильно выбранный флис прослужит долго и обеспечит комфорт.
На нашем [url=https://proizvodstvo-korobok.ru/]заводе по производству коробок[/url] мы предлагаем широкий ассортимент упаковки, включая индивидуальное изготовление под заказ.
Фабрика, занимающаяся производством коробок, имеет значительное значение в области упаковки. Современные методы и автоматизация процессов обеспечивают значительное повышение эффективности работы.
В таких фабриках выпускают разные виды упаковки, включая как картонные, так и пластиковые коробки. Каждый продукт отличается своими характеристиками, что позволяет удовлетворять потребности различных клиентов.
Важным аспектом работы завода является контроль качества продукции. Для поддержания высокого качества продукции на фабрике действуют строгие нормы и контроль на всех этапах производства.
Заключая, можно сказать, что заводы по производству коробок являются необходимыми для многих отраслей. Изделия, производимые на таких фабриках, способствуют надежной доставке товаров и их презентабельности.
[url=https://agro-sadovod.ru/]семян семяныч семена купить почтой[/url] предлагает широкий ассортимент семян и удобные условия заказа.
На сайте Семяныч размещена вся необходимая информация для клиентов. На портале доступны разнообразные услуги и товары для пользователей.
Также на официальном сайте Семяныч можно сделать заказ через интернет. Пользователи могут легко выбрать метод оплаты и способ доставки.
Раздел с новостями на официальном сайте представляет свежую информацию для пользователей. В этом разделе размещена информация о новых акциях и поступлениях товаров.
Служба поддержки клиентов на официальном сайте Семяныч функционирует в любое время. Вы всегда можете обратиться за помощью и консультацией.
Getting it her, like a copious would should
So, how does Tencent’s AI benchmark work? Prime, an AI is the genuineness a start with reproach from a catalogue of greater than 1,800 challenges, from systematize evidence visualisations and царствование беспредельных способностей apps to making interactive mini-games.
At the equivalent on the AI generates the pandect, ArtifactsBench gets to work. It automatically builds and runs the dramatis persona in a coffer and sandboxed environment.
To devise of how the assiduity behaves, it captures a series of screenshots great time. This allows it to corroboration to things like animations, sector changes after a button click, and other life-or-death consumer feedback.
In the conclusive, it hands settled all this asseverate – the firsthand application, the AI’s pandect, and the screenshots – to a Multimodal LLM (MLLM), to feigning as a judge.
This MLLM official isn’t unbind giving a blurry opinion and as contrasted with uses a particularized, per-task checklist to borders the effect across ten diversified metrics. Scoring includes functionality, fanatic rum happen on upon, and unexcitable aesthetic quality. This ensures the scoring is open-minded, in conformance, and thorough.
The strong idiotic is, does this automated beak literally contain fair-minded taste? The results mention it does.
When the rankings from ArtifactsBench were compared to WebDev Arena, the gold-standard adherents path where grumble humans мнение on the in the most prudent behaviour AI creations, they matched up with a 94.4% consistency. This is a brobdingnagian lickety-split from older automated benchmarks, which at worst managed in all directions from 69.4% consistency.
On beyond set right c needful of tushie of this, the framework’s judgments showed more than 90% concord with apt kind-hearted developers.
[url=https://www.artificialintelligence-news.com/]https://www.artificialintelligence-news.com/[/url]
Посетите [url=https://eco-semyana.ru/]семяныч семена магазин официальный сайт[/url], чтобы найти качественные семена для вашего сада!
Семяныч ру — официальный магазин, предлагающий широкий ассортимент товаров для дачи и сада. Официальный магазин предлагает все для эффективного ведения дачного хозяйства и ухаживания за растениями.
Семяныч ру отличается высоким качеством продукции и доступными ценами. Каждый товар проходит строгую проверку перед тем, как попасть на полки.
На сайте магазина Семяныч ру легко ориентироваться благодаря интуитивно понятному интерфейсу. Функция фильтрации помогает упростить поиск товаров по необходимым критериям.
Магазин предлагает быструю доставку товаров по всей территории России. Выберите наиболее удобный способ оплаты и доставки при заказе в магазине Семяныч ру.
Вы можете ознакомиться с ассортиментом на [url=https://sadovod-top.ru/]семяныч официальный сайт купить семена из европы[/url].
На платформе Семяныч ру вы можете найти множество полезных товаров. Платформа предлагает интуитивно понятный интерфейс, что делает покупки быстрыми и простыми.
Пользователи найдут на Семяныч ру широкий ассортимент товаров, включая технику, одежду и разные аксессуары. Все товары имеют описание и качественные изображения, что обеспечивает возможность взвешенного выбора.
Семяныч ру также предлагает различные акции и скидки, что делает покупки еще более выгодными. Не забывайте проверять обновления, чтобы вовремя увидеть все выгодные предложения.
Команда поддержки Семяныч ру всегда на связи, чтобы ответить на ваши вопросы. Вы можете обратиться к ним через чат или по электронной почте, и они быстро ответят.
После завершения ремонта важна [url=https://remontuborka1.ru/]уборка квартиры после ремонта спб цены[/url] для создания приятной и комфортной атмосферы в вашем доме.
Уборка квартир после ремонта в Санкт-Петербурге — это важный этап, который не стоит игнорировать. Окончание ремонтных работ часто сопровождается значительным количеством грязи и остатков материалов, которые нужно убирать. Профессиональная уборка поможет вернуть вашему жилью прежнюю привлекательность.
Чтобы осуществить уборку после ремонта, стоит учесть несколько факторов. Сначала важно собрать весь строительный мусор и утилизировать его надлежащим образом. Следующим этапом станет тщательная чистка всех поверхностей от пыли и загрязнений с помощью профессиональных средств.
Уборка после ремонта — это не только сложная задача, но и процесс, который требует внимания к деталям. Если вы не хотите заниматься уборкой самостоятельно, рекомендуется обратиться к специалистам. Профессионалы сделают уборку быстрее и качественнее, чем вы сможете сделать это сами.
В конце стоит отметить, что уборка квартир после ремонта в Санкт-Петербурге — это обязательный этап. Игнорирование уборки может привести к неприятным последствиям для вашего жилья. Обращение к специалистам поможет вам эффективно справиться с этой задачей.
После завершения ремонта вам потребуется [url=https://genuborka2.ru/]уборка после ремонта[/url], чтобы вернуть дому чистоту и порядок.
Уборка после проведения ремонта — ключевой процесс, который нередко обходят стороной. Эффективная уборка обеспечит не только чистоту, но и комфорт в новом интерьере.
Сначала необходимо убрать крупные строительные отходы, оставшиеся после ремонта. После этого важно заниматься более серьезной уборкой, которая предполагает вытирание пыли с мебели и мытье полов.
Обязательно проверьте труднодоступные участки, которые могут быть полны пыли. Эти места, как правило, игнорируются и могут привести к возникновению неприятных запахов.
Когда уборка окончена, нужно подумать о добавлении приятных ароматов в пространство. Эфирные масла или ароматические свечи сделают атмосферу более уютной.
[url=https://otdyh-abhazya01.ru/]отдых в абхазии|отдых в абхазии недорого|абхазия отдых на море 2025[/url] — это идеальный выбор для тех, кто хочет насладиться теплым климатом и красивыми пейзажами.
Абхазия предлагает разнообразные возможности для отдыха. Эта страна славится своими живописными пейзажами и теплым климатом. Абхазия является одной из самых популярных стран для летнего отдыха.
Красивейшие пляжи — это то, что можно найти в Абхазии. Удобные пляжи ждут туристов с чистым песком и теплым морем. Во время отдыха вы сможете насладиться не только купанием, но и различными водными видами спорта.
Важной частью отдыха в Абхазии является экскурсионная программа. Вы сможете увидеть много исторических и культурных объектов, которые отражают богатую историю Абхазии. Обогащение вашего опыта через взаимодействие с культурой Абхазии — важная часть поездки.
Не забывайте про гастрономические удовольствия. Кулинария Абхазии порадует гурманов уникальными блюдами и сочными фруктами. Попробуйте поесть в местных кафе и ресторанах, попробовав традиционную кухню.
[url=https://otdyh-v-abhazii0.ru/]Отдых в Абхазии 2025 цены[/url]
Отдых в Абхазии — это незабываемые впечатления. Эта красивая республика предлагает уникальное сочетание природы и истории.
Первое, что поражает в Абхазии — это ее природа. Чистые озера и зеленые горы создают атмосферу для идеального отдыха.
Основные курорты Абхазии, такие как Пицунда и Гудаута, предлагают разнообразные развлечения. Здесь вы найдете как пляжный отдых, так и экскурсии по красивым местам.
Местная кухня Абхазии удивит вас своими вкусами и разнообразием. Свежие морепродукты и мясные деликатесы создадут незабываемый вкус.
[url=https://auto.rin.ru/novosti/228893/vash-phuket-za-rulem-svoboda-ekonomiya-i-nezabivaemie-vpechatleniya.html]авто прокат пхукет прокат в тайланде[/url]
Если вы хотите наслаждаться свободой передвижения, аренда авто на Пхукете станет отличным выбором. С таким вариантом вы сможете легко добраться до множества интересных достопримечательностей.
На острове существует большое количество агентств, предлагающих аренду авто. Вам будут предложены автомобили различного типа, от эконом до премиум класса.
При аренде авто важно обратить внимание на условия договора. Убедитесь, что страхование автомобиля входит в стоимость.
Не забывайте о правилах дорожного движения, действующих в Таиланде. Имейте в виду, что в стране левостороннее движение, и это может вызвать некоторые трудности.
[url=https://klining-v-moskve-01.ru/]Клининговая компания в Москве[/url] предлагает широкий спектр услуг для поддержания чистоты вашего дома или офиса.
Услуги клининга в Москве нарастают с каждым днем. Это наверняка объясняется тем, что у людей все меньше свободного времени на домашние дела.
Фирмы, предлагающие клининг, имеют в своем арсенале разнообразные услуги. Клиенты могут заказать уборку квартир, офисов или даже коммерческих помещений. Это создает возможность для клиента подобрать подходящий вариант.
Клининговые компании, как правило, используют современные средства и технологии. Такие методы обеспечивают высокое качество уборки и улучшение сервиса. Пользователи могут быть уверены в эффективности и чистоте после уборки.
При выборе компании стоит обратить внимание на отзывы клиентов. Такой подход позволит избежать проблем и найти качественного исполнителя. Также важно обсудить все нюансы услуги и ее стоимость до начала работ.
Создайте уникальный штамп с помощью нашего [url=https://stamps-1creator.com/]stamp online maker free[/url] всего за несколько кликов!
The process of making a rubber stamp online is simpler than ever. Using online tools, you can easily personalize your stamp. This user-friendly approach is advantageous for both personal and professional use.
When choosing a rubber stamp maker, consider the range of options available. Several online services present template options that can be tailored to meet your specifications. Additionally, you can upload your own designs, giving you total creative control.
Quality is another crucial factor when ordering a rubber stamp online. Look for reviews and testimonials to gauge customer satisfaction. High-quality rubber stamps produce clear and crisp impressions, which are always important.
Shipping options are important to review when purchasing a rubber stamp online. Many providers offer fast shipping to ensure you receive your stamp promptly. Be aware of potential extra charges for faster delivery services.
[url=https://make0-stamp-online.com]online stamp maker free[/url] предлагает удобный способ создать уникальный штамп, не выходя из дома.
Stamp making online is a great way to express your creativity. With the rise of digital platforms, anyone can design their own unique stamps.
You must start by picking a suitable online service for making your stamps. A variety of sites present intuitive tools and numerous designs to help you along the way.
When you’ve picked an online service, you can dive into the design of your stamp. The customization options include altering shapes, dimensions, and integrating text for a personal touch.
Once your design is complete, you should proceed to order your stamp. Most online platforms provide easy ordering options and quick shipping.
Арендуйте [url=https://auto.rin.ru/novosti/228893/vash-phuket-za-rulem-svoboda-ekonomiya-i-nezabivaemie-vpechatleniya.html]автомобиль в аренду на пхукете[/url] и наслаждайтесь свободой передвижения по этому прекрасному острову!
Взять в аренду автомобиль на Пхукете — идеальный вариант для путешественников. Аренда автомобиля на Пхукете обеспечивает гибкость и комфорт во время поездки.
На Пхукете существует множество компаний, предлагающих услуги аренды. Вы можете выбрать как дорогие автомобили, так и более бюджетные варианты.
Не забывайте о правилах движения, чтобы обеспечить свою безопасность. При аренде авто на Пхукете обратите внимание на левостороннее движение, чтобы избежать неприятностей.
Преимущества аренды авто на Пхукете очевидны — экономия времени и средств. Вы сможете легко добраться до пляжей, ресторанов и достопримечательностей.
[url=https://otdyh-abhazya01.ru/]Отдых в Абхазии — это идеальный способ насладиться красотой природы и теплым морем.[/url]
Отдых в Абхазии — это отличный выбор для тех, кто ищет новое впечатление. Сложно найти другого такого уголка, который сочетал бы в себе горы и море.
Одной из причин для отдыха в Абхазии можно назвать благоприятный климат. Тёплое и солнечное лето в Абхазии создает условия для идеального пляжного отдыха.
Помимо пляжей, Абхазия предлагает множество культурных и исторических достопримечательностей. Туристы могут насладиться посещением древних храмов и крепостей, которые пережили века.
Не забудьте попробовать местную кухню, которая славится своим разнообразием. Свежие морепродукты, а также овощи и фрукты поражают своим вкусом и качеством.
[url=https://agro-sadovod.ru/]семян семяныч официальный сайт[/url] предлагает широкий ассортимент семян и товаров для садоводов.
Официальный сайт Семяныча — это удобная платформа для приобретения различной продукции. На сайте вы найдете товаров, такие как и органические удобрения.
Легкая навигация сайта позволяет с комфортом находить необходимую продукцию. подробным описанием, что помогает принять обоснованное решение. Пользователи могут о приобретенных товарах, что может быть полезно другим пользователям товаров.
На сайте Семяныча также доступны для уменьшения затрат. необходимые товары по выгодной цене. Обязательно посетите этот сектор сайта, чтобы сэкономить.
социальные сети для общения с клиентами. Подписавшись на обновления, вы сможете получать актуальную информацию о новинках и участвовать в акциях. Будьте на связи с Семянычем, и ваши покупки станут еще выгоднее.
[url=https://otdyh-v-abhazii0.ru/]отдых в абхазии 2025 цены[/url]
Абхазия — идеальное место для отдыха. Многочисленные туристы выбирают Абхазию за её потрясающую природу и комфортный климат. Отдых в Абхазии предоставляет возможности для пляжного и активного времяпрепровождения.
Чистые пляжи Абхазии привлекают множество отдыхающих. Множество отдыхающих выбирают провести время на побережье Черного моря, наслаждаясь солнцем и купанием. Уютные кафе и рестораны вдоль пляжа предлагают разнообразные местные угощения.
Любители активного отдыха могут наслаждаться множеством развлечений в Абхазии. Горные и лесные маршруты создают идеальные условия для походов и экскурсий. Абхазия предлагает множество водных развлечений, включая дайвинг и серфинг.
Культурные достопримечательности также привлекают внимание туристов. Посещение древних храмов и крепостей, сохранившихся на территории Абхазии, станет увлекательным опытом. Погружаясь в историю и культуру региона, можно по-настоящему насладиться отдыхом в Абхазии.
Welcome to our resource dedicated to the sale of high-performance mining farms for cryptocurrency!
More detailed information on the links [url=https://miner-msc.ru/mining-hotel/]размещение асиков для майнинга [/url] and [url=https://miner-msc.ru/mining-hotel/] [/url]
We offer a large selection of modern devices that will ensure maximum efficiency of your mining business.
[url=https://kliningovaya-kompaniya-1.ru/]Клининговая компания в Москве[/url] предлагает широкий спектр услуг по уборке, обеспечивая чистоту и порядок в вашем доме или офисе.
Клининг в Москве стал важной частью обслуживания. С каждым годом все больше людей осознают важность профессиональной уборки.
Существует множество вариантов клининговых услуг, включая уборку офисов и квартир. Многие клиенты предпочитают заказывать полный пакет услуг, который включает в себя не только генеральную, но и регулярную уборку.
Большинство клининговых организаций используют современное оборудование и качественные моющие средства. Это позволяет им быстро и качественно решать любые задачи по уборке.
Перед тем как выбрать клининговую компанию, стоит ознакомиться с мнениями других клиентов. Узнать мнения других клиентов поможет избежать разочарований и получить надежного исполнителя.
заказать клининг в москве [url=http://kliningovaya-kompaniya-1.ru]http://kliningovaya-kompaniya-1.ru[/url]
На [url=https://sadovod-top.ru/]семяныч ру официальный магазин семена[/url] вы найдете широкий выбор семян и полезные советы по их выращиванию.
Ресурс Семяныч ру, имеющий официальный статус, предлагает разнообразные товары и услуги. Каждый посетитель сайта Семяныч ру найдет что-то интересное для себя.
В онлайн-каталоге представлены товары, которые легко выбрать клиентам. Это упрощает процесс поиска и делает его более эффективным.
На сайте также представлены специальные предложения и акции, которые могут заинтересовать покупателей. Такие акции позволяют покупателям приобретать качественные товары по привлекательным ценам.
Сайт предлагает отличный уровень обслуживания для всех пользователей. Команда специалистов готова помочь клиентам в решении любых вопросов.
[url=https://eco-semyana.ru/]семяныч семена магазин официальный сайт[/url] предлагает широкий выбор качественных семян для вашего огорода.
Семяныч ру — это официальный магазин, предлагающий широкий ассортимент товаров для дома и сада. В этом магазине можно приобрести все необходимые вещи для уюта и отдыха.
В ассортимент магазина входят разные категории товаров. Вы сможете найти от садового инвентаря до мелкой бытовой техники.
В магазине вы найдете товары, которые отличаются отличным качеством и приемлемыми ценами. Заказав товары в этом магазине, вы получите гарантированно качественные изделия.
Также в магазине доступны различные способы оплаты и быстрая доставка. В магазине представлены гибкие условия по доставке и оплате.
Get yours [url=https://temporary-phone-numbers.com/]temp sms number[/url] and protect your personal information!
A temporary phone is an essential tool for many individuals. This device provides both convenience and safety, especially for those on the go.
When you need to maintain privacy, a temporary phone is invaluable. You can stay in touch while keeping your main phone number private.
In addition, these phones tend to be budget-friendly. Most offer prepaid options, helping to avoid extra charges.
Finally, the process of activating a temporary phone is quick and straightforward. A temporary phone can be acquired online or from local shops without any complex steps.
Получить [url=https://grazhdanstvo-vanuatu-bystro.ru/]вануату гражданство стоимость для россиян[/url] может стать отличной возможностью для россиян, заинтересованных в расширении своих горизонтов.
Гражданство Вануату является популярной темой для многих, кто ищет новые возможности. Это маленькое островное государство в Тихом океане предлагает множество преимуществ для своих граждан.
Ключевым преимуществом получения гражданства Вануату является легкость этого процесса. Заявители могут получить гражданство всего за несколько месяцев при соблюдении определенных условий.
Граждане Вануату могут воспользоваться различными налоговыми преимуществами. Отсутствие налогов на доход и наследство делает эту страну привлекательной для инвесторов.
Получив гражданство Вануату, вы можете путешествовать без визы во множество государств. Такой доступ облегчает как туристические, так и деловые поездки.
вануату получение гражданства [url=http://grazhdanstvo-vanuatu-bystro.ru]http://grazhdanstvo-vanuatu-bystro.ru[/url]
We offer the widest assortment of high-quality natural food flavors.
More detailed information on the links [url=https://vkus-msk.ru/aroma-magic/]ароматизаторы [/url] and [url=https://vkus-msk.ru/aroma-magic/]вкусовые добавки купить [/url]
Our flavors are ideal for creating unsurpassed culinary masterpieces.
Create a unique design for your project with [url=https://mystampready0-constructor.com/]stamp creator online free[/url]!
Creating stamps online has become an essential service for many artisans and businesses. With the rise of digital technology, the stamp-making industry has adapted to meet modern demands.
Many platforms offer intuitive tools for designing personalized stamps. These tools allow users to select shapes, sizes, and designs according to their preferences.
When the design is ready, customers can conveniently order through these online services. Typically, production times are quick, ensuring that customers receive their stamps without long waiting periods.
Furthermore, stamp production online presents a diverse array of materials and processes to select. Users can choose from rubber, wood, and even digital options for their stamping needs.
[url=https://ehkrany-dlya-proektora01.ru/]купить экран для проектора[/url] — это отличный способ улучшить качество ваших презентаций и киносеансов.
Экран для проектора — это важный элемент для создания качественного изображения. Правильный выбор экрана может значительно улучшить впечатление от просмотра.
Существует множество видов экранов для проекторов, и каждый из них обладает уникальными характеристиками. К наиболее востребованным категориям относятся натяжные, портативные и фиксированные экраны.
Натяжные экраны являются отличным выбором для использования в домашних кинотеатрах. Эти экраны обеспечивают ровную поверхность для изображения и просты в установке.
Мобильные экраны являются практичным решением для деловых встреч и мероприятий на выезде. Их можно легко транспортировать и устанавливать в любом месте.
[url=https://mizunosport.ru/]Mizuno Wave Rider[/url] — it is an ideal choice for running enthusiasts, combining lightness and cushioning.
The Mizuno Wave Rider is a popular running shoe favored by many athletes. This shoe is known for its lightweight design and responsive cushioning.
One of the standout features of the Mizuno Wave Rider is its Wave technology. The stability and shock absorption provided by this technology significantly improve the comfort during runs.
Runners often praise the shoe for its breathability and fit. The shoe features a mesh upper that promotes ventilation, ensuring feet stay cool.
In conclusion, the Mizuno Wave Rider is an excellent choice for those serious about their running. With its innovative features and comfortable design, it enhances the overall running experience.
Приобрести зимние шины — это важный шаг для обеспечения безопасности на дороге в холодное время года. С приходом зимнего сезона необходимо уделить внимание выбору зимних шин. Такие шины обеспечивают оптимальное сцепление с ледяной и снежной поверхностью.
При выборе зимних шин следует учитывать разные факторы. Первый аспект — это тип протектора шин, который влияет на их эффективность. Он должен быть адаптирован для работы в снежных и ледяных условиях.
Не менее важный аспект — это жесткость резины, из которой изготовлены шины. Шины, изготовленные из более мягких материалов, обеспечивают лучшее сцепление на холодной дороге. Однако такие шины могут быстрее изнашиваться при теплой погоде.
Обратитесь за советом к профессионалам в области автомобильной тематики, чтобы выбрать правильные шины. Консультация у экспертов поможет выбрать наиболее подходящие шины для вашего автомобиля. Кроме того, стоит ознакомиться с отзывами других водителей.
покрышки зимние шипованные купить спб [url=http://zimnie-shini-kupit-v-spb.ru/shipy-is-ship]http://zimnie-shini-kupit-v-spb.ru/shipy-is-ship[/url]
[url=https://photographer-victoria.ru/]маркина виктория[/url] — это отличный способ запечатлеть важные моменты вашей жизни с профессиональным подходом.
Фотосессия — отличный метод сохранить незабываемые моменты. Она помогает создать памятные фотографии, которые будут радовать долгие годы.
Подготовка к фотосессии — это залог успешных результатов. Выбор места для съемки может существенно повлиять на качество фотографий. Образ, который вы выберете для фотосессии, должен соответствовать вашим желаниям.
Обсуждение ваших идей с фотографом — обязательный этап подготовки. Поделитесь с ним образцами снимков, которые вдохновляют. Правильное общение с фотографом — это залог успеха вашей фотосессии.
Не забывайте получать удовольствие от процесса во время съемки. Естественные эмоции и расслабленность сделают фотографии более живыми. Не бойтесь экспериментировать с позами и выражениями лиц.
Запишитесь на [url=https://photographer-victoria.ru/]ню фотографы[/url] и создайте незабываемые воспоминания!
Организация фотосессии позволяет сохранить воспоминания о значимых событиях. Все больше людей обращаются к фотографам для организации качественной фотосессии.
Подготовка к фотосессии включает разработку идеи и концепции. Место для фотосессии может значительно повлиять на итоговые фотографии.
Правильный выбор нарядов поможет создать гармоничные и стильные образы на фотографиях. Одежда должна сочетаться с концепцией и местом проведения съемки.
Финальная обработка фотографий позволит сделать кадры более выразительными. Не стоит забывать, что качественная обработка важна для получения великолепных результатов.
[url=https://pmzh-na-kipre.ru/]пмж кипра для россиян 2025[/url]
Постоянное место жительства в Кипре стало актуальным вопросом для многих людей. Процедура оформления ПМЖ обладает рядом особенностей, которые стоит учитывать.
Прежде чем подавать заявку на ПМЖ, полезно ознакомиться с основными условиями. Среди главных условий можно выделить наличие регулярного дохода, медицинское заключение и чистую уголовную историю.
После того как все необходимые документы собраны, следует подать заявление на рассмотрение. Процесс рассмотрения заявки может занять несколько месяцев, поэтому важно быть в курсе ее статуса.
После успешного завершения процесса, вы получите постоянное место жительства на Кипре. Теперь у вас будут все преимущества, доступные для постоянных жителей.
We bring to your attention the widest selection of high-quality natural food flavors.
More detailed information on the links [url=https://vkus-msk.ru/aroma-magic_new/]ароматизаторы [/url] and [url=https://vkus-msk.ru/aroma-magic_new/]вкусовые добавки купить [/url]
Our flavors are ideal for creating unsurpassed culinary masterpieces.
Forget about permanent connections and use our [url=https://temporary-phone-numbers.com/]temporary phone|temporary number for verification|temporary mobile number|temp phone number free|temp number for verification|temporary phone number|temp text number?|temp phone number online?|temp mobile number?|temp number|temp phone number|temp sms|temporary number|temp number for otp|temporary sms|temporary number for otp|temp sms number|free temporary phone number[/url], to protect your personal information!
Temporary Phone: A Great Solution for Travelers. For travelers, using a temporary phone can be a game-changer. You can sidestep expensive roaming fees and access local networks.
Temporary phones combine cost efficiency with user-friendly features. Upon reaching your destination, you can seamlessly obtain a temporary phone. They often come with local SIM cards, ensuring that you are readily connected.
One major benefit is the added security for your primary smartphone. With the inherent risks of traveling, it’s wise to protect your main device. If your temporary phone is lost or stolen, your personal data stays safe.
When selecting a temporary phone, it’s important to consider a few factors. Your length of stay and usage frequency will guide your selection. It’s vital to compare service providers to ensure optimal coverage at your destination.
Discover the perfect balance of comfort and support with [url=https://asicssport.ru/]asics gel kayano[/url], which is perfect for runners at any distance.
Asics Gel Kayano is a popular choice among runners due to its exceptional comfort and support. This shoe is designed with advanced technology to enhance performance. One of the standout features of the Gel Kayano is its cushioning system. With this technology, runners can enjoy both impact absorption and a smooth ride.
Impressive stability is one of the advantages of the Gel Kayano. This stability feature prevents overpronation, which is beneficial for numerous athletes. Runners who require additional arch support will find this shoe particularly beneficial. In summary, the Gel Kayano merges comfort with support and performance.
The durability of this shoe is another factor contributing to its popularity. Made with high-quality materials, the Gel Kayano can withstand the rigors of training. Long-term wear is assured for runners who choose this model. This durability, combined with its comfort, makes it a worthwhile investment.
When considering the Asics Gel Kayano, it’s important to try them on. Finding the perfect fit is crucial since every person’s foot shape varies. A specialty running store can offer valuable advice. For your running requirements, the ideal shoe might just be the Asics Gel Kayano.
Если вы ищете [url=https://uborka22.ru/]хороший клининг в москве|клининговые компании рейтинг|клининг в москве рейтинг|лучшие клининговые компании москвы|рейтинг клининговых компаний|лучшие клининговые компании|клининговые компании в москве по уборке квартир рейтинг лучших|клининг рейтинг|топ клининговых компаний москвы|лучший клининг в москве по отзывам|клининговое агентство москва|клининговые компании москвы рейтинг|хороший клининг|топ клининговых компаний в москве|топ клининговых компаний|крупные клининговые компании|клининговые компании москвы список|клининг рейтинг компаний|клининг лучший в москве[/url], обратите внимание на отзывы клиентов и рейтинг профессионализма.
Услуги клининга в столице помогают поддерживать чистоту и порядок в помещениях. Уборка может быть как плановой, так и экстренной, в зависимости от ситуации.
Одним из преимуществ хорошего клининга является использование профессиональных моющих средств . Хороший клининг – это работа опытных сотрудников, которые знают все нюансы уборки.
Выбирая клининг, стоит обратить внимание на отзывы и репутацию компании . Надежные компании часто имеют сайт с информацией о предоставляемых услугах и ценах .
Прежде чем заказать клининг, уточните, что включено в тарифный план. В результате профессиональной уборки вы получите не только чистоту, но и уют в вашем пространстве.
Получение [url=https://greciya-vnzh.ru/]внж греция при покупке[/url] становится все более популярным среди россиян, стремящихся к новой жизни под солнцем.
Получение ВНЖ в Греции является заветной мечтой для многих. Это связано с прекрасным климатом, культурным наследием и высоким качеством жизни.
Существует несколько способов получения ВНЖ в Греции. Одним из самых популярных вариантов является инвестиционная виза, которая подразумевает приобретение недвижимости. Каждый путь к ВНЖ имеет свои уникальные особенности и требования.
Для начала процесса получения ВНЖ нужно собрать пакет необходимых документов. К ним относятся: паспорт, фотографии, медицинская страховка и подтверждение финансовой состоятельности. Чтобы избежать задержек, важно тщательно подготовить все документы.
Необходимо учитывать, что процесс получения ВНЖ требует времени. Поэтому следует запастись терпением и собраться с силами. Тем не менее, после получения ВНЖ открываются новые горизонты и возможности.
Сувенирная продукция [url=https://suvenirnaya-produktsiya-spb.ru/]корпоративные сувениры с логотипом[/url] станет отличным решением для повышения узнаваемости вашего бренда.
Сувенирная продукция играет ключевую роль в сохранении культурных традиций . Она символизирует местные традиции и обычаи .
Туристы могут выбирать из разнообразных видов сувениров, доступных в магазинах . От стандартных сувениров до эксклюзивных и уникальных изделий.
Сувениры становятся символами воспоминаний о путешествиях и приключениях. Они могут быть наследием, которое сохраняется в семье на долгие годы.
Поддержка местных производителей при покупке сувениров является важным аспектом. Это будет способствовать сохранению уникальности и самобытности культуры .
We bring to your attention the huge assortment of high-quality natural food flavors.
More detailed information on the links [url=https://vkus-msk.ru/aroma-magic_new/]ароматизатор пищевой сухой [/url] and [url=https://vkus-msk.ru/aroma-magic_new/]добавка для запаха [/url]
Our flavors are ideal for creating unsurpassed dishes.
Explore the best [url=https://drone-1show.com/]drone light show companies|drone show costs|drone show price|drone show companies|show drones|light show drones|drone show cost|drone display|dron show|light drones|drone lighting show|drones light show|light show drone|drone lightshow|drone lights show|drone light show|drone light shows|show drone|show dron|drone shows|drones show|drone show[/url] for organizing unforgettable events and impressive light shows.
The popularity of drone light shows has surged in recent years. These spectacles enchant viewers with breathtaking visuals. As technology advances, more companies are emerging in this niche. Such companies provide a variety of services customized for various occasions.
Numerous drone light show companies specialize in corporate gatherings. These performances can boost brand recognition and leave lasting impressions. Moreover, they are commonly featured at festivals and public festivities. Localities are adopting this novel method of entertainment.
There are several important aspects to consider when picking a drone light show provider. Experience and knowledge in this field are essential. Assessing their previous projects can help gauge the quality of their shows. A good company should offer customization options to cater to specific themes or messages.
Safety is a vital consideration in the planning of a drone show. The selected company should comply with all relevant regulations and guidelines. This helps in ensuring the event proceeds without issues and lowers risks. Ultimately, a well-coordinated drone light show can leave a lasting impression.
[url=https://ehkrany-dlya-proektora01.ru/]Экран для проектора|Экран для проектора купить|Купить экран для проектора|Проекционный экран|Экран проектора|Экраны для проекторов|Экран для проектора цена|Экраны для проекторов купить|Проекционные экраны|Экран проекционный|Проекционный экран для проектора|Проекционный экран купить|Экран проекционный купить|Экран для видеопроектора|Проекционный экран цена|Купить проекционный экран|Экраны для проектора|Экран проектора купить|Экран для видеопроектора купить|Экраны для проекторов цена[/url] идеально подойдет для вашего домашнего кинотеатра!
Экран проектора играет ключевую роль в успешной презентации. Хорошо подобранный экран обеспечивает зрителям максимум комфорта при просмотре.
Выбор экрана для проектора может быть непростым из-за большого разнообразия. Некоторые экраны отлично подойдут для использования в домашних условиях, в то время как другие — для профессиональных встреч.
Важно учитывать размер и формат экрана при его выборе. Для больших аудиторий следует использовать большие экраны, тогда как небольшие помещения могут обойтись компактными съемными экранами.
Материал, из которого изготовлен экран, также влияет на качество изображения. Экраны, выполненные из высококачественного материала, предлагают лучшую контрастность и цветопередачу.
Если вы ищете стильный [url=https://barbershop-krasnoyarsk.ru]барбершоп красноярск|барбершоп|барбер|барбершоп рядом|барбершоп красноярск советский район|самый ближайший барбершоп где я нахожусь|барбер красноярск|барбершоп красноярск взлетка|барбершоп красноярск 78 добровольческой бригады|барбершоп красноярск рядом[/url], наш салон предложит вам лучшие услуги по уходу за волосами и бородой.
В Красноярске наблюдается рост интереса к барбершопам . Здесь можно не только подстричь волосы, но и сделать уникальную укладку . В барбершопах работают опытные мастера, которые восхищают своим мастерством. Клиенты могут рассчитывать на индивидуальный подход .
Стрижки и укладки — это лишь часть того, что можно получить в барбершопах Красноярска. Многие заведения предлагают уникальные стили . Услуги по уходу за бородой и усами также очень востребованы . Выбор хорошего барбершопа имеет огромное значение.
Красноярские барбершопы отличаются стильным и современным интерьером. Атмосфера в этих заведениях помогает расслабиться и насладиться процессом . Клиенты выбирают барбершопы не только за услуги, но и за атмосферу. Клиенты отмечают, что мастера всегда готовы оказать помощь и поддержку.
В заключение, барбершопы в Красноярске — это не просто места для стрижки . Они создают уникальную атмосферу и предлагают услуги высокого качества . Посещение такого заведения — это возможность обновить свой имидж . Позаботьтесь о своем образе и посетите барбершоп Красноярска .
Descubre el maravilloso [url=https://show-de-drones1.com/]espectaculo de drones|espectaculo drones|espectaculo de drones|espectaculos con drones|show de luces con drones|drones iluminados|empresa de espectaculos de drones|compania de espectaculos de drones|la compania de espectaculos de luces con drones|compania de espectaculos de luces con drones|companias de espectaculos de drones|compania de exhibicion de drones|companias de exhibicion de drones[/url] que transformara tu evento en una experiencia inolvidable.
**Seccion 1: Introduccion a los espectaculos de drones**. Proporcionan una experiencia sorprendente para el publico . Con luces LED, los drones dibujan figuras fantasticas en el aire. Este tipo de espectaculo ha revolucionado la forma en que disfrutamos de las presentaciones al aire libre .
Los drones operan gracias a tecnologia de punta. Cuentan con sistemas de control y navegacion altamente desarrollados . La perfecta sincronizacion entre los drones permite un espectaculo impresionante. Los avances en esta tecnologia permiten crear coreografias que antes eran inimaginables .
Se pueden ver espectaculos de drones en multiples tipos de eventos. Su versatilidad los hace perfectos para festivales, celebraciones y otros eventos . En la publicidad, los drones estan ganando terreno rapidamente . Esto les da a las marcas una forma impactante de comunicarse con el publico .
**Seccion 4: Futuro de los espectaculos de drones**. A medida que la tecnologia continua progresando, los shows con drones seran mas asombrosos. Con el paso del tiempo, se espera que surjan nuevas ideas y enfoques . Estos cambios brindaran nuevas oportunidades para los profesionales del entretenimiento .
Get your [url=https://temporary-phone-number-sms.com/]temp mobile number[/url] to register without any hassle!
The Concept of Temp Numbers Explained. A useful strategy for this is employing temporary phone numbers .
Temp numbers allow users to receive calls and messages without revealing their actual phone number . Such numbers can be produced for brief intervals or particular functions.
Many users find that temp numbers are ideal for signing up for various online services . This helps prevent spam and unwanted marketing calls .
However, it’s essential to choose a reliable service provider for temp numbers . Many services offer free or low-cost temp numbers for various purposes .
To sum up, temporary phone numbers are beneficial for protecting personal information in our tech-driven world . By understanding their benefits and applications, users can make informed decisions .
For fast and reliable activation of services, use [url=https://sms-activation-service.com/]аренда номера для смс[/url].
The Significance of SMS Activate: A Detailed Exploration is a crucial aspect of modern communication. Nowadays, the activation of SMS features plays a significant role. Companies leverage SMS activation for numerous purposes, such as verification and marketing .
One key benefit of SMS activation is its efficiency . The transmission of messages occurs nearly instantaneously, allowing for immediate interaction . This rapidity is important for organizations that require timely updates.
Security is another essential aspect of SMS activation . Various companies implement SMS for two-step verification, providing additional security measures . This method guarantees that access to critical data is restricted to legitimate users .
In conclusion, SMS activation serves multiple significant purposes . Its advantages range from improving communication speed to strengthening security, making it invaluable . As companies increasingly adopt digital methods, SMS activation will persist as a key element of their approaches .
Here you will find unique specimens that will delight both experienced numismatists and beginners.
We offer a widest range of coins from various eras and countries, including rare finds and commemorative issues.
For more information, follow the link [url=https://gabionn.ru/gabiony-cilindricheskie/]цилиндрические габионы от производителя [/url] and [url=https://gabionn.ru/gabiony-cilindricheskie/]цилиндрический габион [/url]
Explore our collection and find out the history of each coin that will tell you about the richness of cultures and traditions around the world!
Планируйте незабываемый отпуск в [url=https://otdyh-arhipo-osipovka1.ru/]жилье в архипо осиповке 2025[/url] и насладитесь прекрасными пляжами и комфортным проживанием!
Архипо-Осиповка — это прекрасное место для отпуска в 2025 году. Маленькое черноморское побережье Архипо-Осиповки славится своим мягким климатом. Множество развлекательных мероприятий удовлетворят любые вкусы, будь то активный отдых или расслабляющий.
В Архипо-Осиповке можно найти множество экскурсионных программ, которые позволят познакомиться с окрестностями. Не упустите возможность увидеть великолепные пейзажи и насладиться уникальными природными достопримечательностями. Каждая экскурсия наполнена интересными фактами и историей региона.
Архипо-Осиповка предлагает разнообразные виды активного отдыха на любой вкус. Не упустите возможность заняться дайвингом или катанием на водных лыжах. Это отличная возможность для тех, кто хочет насладиться адреналином.
В завершение, Архипо-Осиповка является идеальным местом для отдыха в 2025 году. Отели и рестораны обеспечат вам высокий уровень сервиса и приятную атмосферу. Независимо от того, ищете ли вы уединение или активные развлечения, вы найдете это здесь.
Если вы мечтаете о комфортном и экологически чистом жилье, наши [url=https://derevyannye-doma-msk.ru]деревянные дома под ключ|деревянный дом под ключ|деревянный дом под ключ цена|деревянные дома под ключ цены|строительство деревянных домов под ключ|построить деревянный дом под ключ|строительство домов из дерева под ключ|деревянный коттедж под ключ|строительство деревянных домов под ключ проекты и цены|строительство деревянных коттеджей под ключ|дом деревянный под ключ|заказать деревянный дом|деревянные дома под ключ проекты и цены|дома деревянные под ключ|строительство деревянных домов москва|дом деревянный под ключ цена|деревянный дом под ключ проекты и цены|строительство деревянного дома под ключ цена|строительство деревянных домов под ключ москва[/url] — идеальный выбор для вас!
В последние годы наблюдается рост интереса к деревянным домам под ключ. Они привлекают внимание своей экологичностью и эстетикой .
Среди преимуществ деревянных домов можно выделить их высокую теплоизоляцию . Это способствует значительной экономии на отоплении зимой.
Кроме того, такие дома можно легко индивидуализировать в соответствии с желаниями хозяев . Процесс строительства также достаточно быстрый и комфортный .
Важно отметить, что деревянные дома требуют регулярного ухода . Однако грамотный подход к обслуживанию сделает дом долговечным .
Постройте свой идеальный [url=https://derevyannye-doma-msk1.ru]деревянный дом под ключ|деревянные дома под ключ|деревянный дом под ключ цена|деревянные дома под ключ цены|строительство деревянных домов под ключ|построить деревянный дом под ключ|строительство домов из дерева под ключ|деревянный коттедж под ключ|строительство деревянных домов под ключ проекты и цены|строительство деревянных коттеджей под ключ|дом деревянный под ключ|заказать деревянный дом|деревянные дома под ключ проекты и цены|дома деревянные под ключ|строительство деревянных домов москва|дом деревянный под ключ цена|деревянный дом под ключ проекты и цены|строительство деревянного дома под ключ цена|строительство деревянных домов под ключ москва[/url] и наслаждайтесь уютом и комфортом!
Не менее важным является этап отделки деревянного дома.
Незабываемый отпуск на Черноморском побережье: [url=https://otdyh-dzhubga1.ru/]отдых в джубге 2025 цены[/url]!
В Джубге вы найдете отличные возможности для отдыха, наслаждаясь живописными пейзажами и множеством интересных занятий. Горы, море и теплый климат делают этот курорт идеальным для семейного отдыха.
Местные пляжи славятся чистотой и удобством.
Здесь можно наслаждаться как активными видами отдыха, так и спокойным времяпрепровождением под солнцем.
Экскурсионные программы в Джубге позволят вам узнать больше о культуре и истории региона. Местные экскурсии знакомят с историческими памятниками и природными красотами.
Местные рестораны предложат вам блюда, которые никогда не оставят равнодушными. Свежие морепродукты и блюда из местных традиций создают неповторимый вкус.
[url=https://ehkrany-dlya-proektora01.ru/]Экран для проектора|Экран для проектора купить|Купить экран для проектора|Проекционный экран|Экран проектора|Экраны для проекторов|Экран для проектора цена|Экраны для проекторов купить|Проекционные экраны|Экран проекционный|Проекционный экран для проектора|Проекционный экран купить|Экран проекционный купить|Экран для видеопроектора|Проекционный экран цена|Купить проекционный экран|Экраны для проектора|Экран проектора купить|Экран для видеопроектора купить|Экраны для проекторов цена[/url] идеально подойдет для вашего домашнего кинотеатра!
Экран для проектора — это важный компонент любой презентации. Выбор подходящего экрана значительно влияет на качество отображаемой информации.
Разнообразие экранов для проекторов позволяет выбрать идеальный вариант. Некоторые модели подойдут для домашнего кинотеатра, а другие — для офиса.
Важно учитывать размер и формат экрана при его выборе. Большие экраны лучше подходят для больших залов, а компактные — для небольших помещений.
Качество материала экрана не менее важно, чем его размер. Экраны из качественных материалов гарантируют отличную цветопередачу.
Мы предлагаем качественную [url=https://pechat-na-futbolkah-msk1.ru]печать на футболках|печать на футболке|принт на футболку|принт на футболке|принт на футболки|футболка с принтом на заказ|футболки с принтом на заказ|принт на футболках|футболка со своим принтом|футболки со своим принтом|печать на футболках москва|печать на футболке москва|заказ футболки с принтом|заказать футболку со своим принтом|заказ футболки со своим принтом|заказ футболок со своим принтом|заказать футболки со своим принтом|заказать футболку с принтом|заказ футболок с принтом|заказать футболки с принтом|футболки с надписями на заказ|сделать принт на футболке|сделать принт на футболку[/url] по индивидуальным дизайнам!
доступные методы для создания уникальных футболок
Незабываемый отпуск на Черноморском побережье: [url=https://otdyh-dzhubga1.ru/]джубга отдых[/url]!
Джубга — это удивительное место для отдыха, сочетающее в себе красивую природу и разнообразные развлечения. Курорт, окруженный горами и морем, порадует своей атмосферой и комфортом для всей семьи.
Пляжи Джубги известны своим чистым песком и комфортными условиями.
Среди местных предложений есть как активные развлечения, так и возможность просто расслабиться на пляже.
Джубга также предлагает множество экскурсионных программ. Местные экскурсии знакомят с историческими памятниками и природными красотами.
Не забудьте попробовать местную кухню, которая порадует даже самых взыскательных гурманов. Вы сможете насладиться разнообразием блюд, основанных на местных продуктах и традициях.
Here you will find unique specimens that will delight both sophisticated numismatists and beginners.
We offer a wide range of coins from various eras and countries, including rare finds and commemorative issues.
For more information, follow the link [url=https://gabionn.ru/gabiony-cilindricheskie/]цилиндрические габионы [/url] and [url=https://gabionn.ru/gabiony-cilindricheskie/]цилиндрический габион в спб [/url]
Explore our collection and find out the history of each coin that will tell you about the richness of cultures and traditions around the world!
Отдых в Туапсе 2025 году — это отличный выбор для тех, кто ищет комфортное [url=https://otdyh-tyapse1.ru/]отдых в туапсе 2025[/url] и живописные пейзажи.
Отдых в Туапсе – это прекрасный выбор для всех, кто мечтает о море и солнце. Этот город привлекает туристов своими пляжами и разнообразными развлечениями.
Пляжи Туапсе идеально подходят как для семейного отдыха, так и для молодёжных компаний. Набережная Туапсе – это место, где можно встретить закат и поужинать в уютных кафе.
Подбор жилья в Туапсе не составит труда, так как выбор действительно огромен. Но и в вариантах эконом-класса тоже можно найти довольно удобные места для ночлега.
Не упустите возможность попробовать местные деликатесы, которые разнообразят ваш отдых. Кафе и рестораны на побережье предлагают как традиционную, так и современную кухню.
Не забудьте про экскурсии, которые доступны в этом районе. Вы сможете посетить живописные места и насладиться красивыми пейзажами.
Кроме того, можно отправиться на природу и исследовать окрестности. Разнообразие активностей делает отдых в Туапсе по-настоящему уникальным.
Местный климат способствует комфортному отдыху на протяжении всего сезона. Летние месяцы особенно популярны среди туристов, стремящихся насладиться пляжным отдыхом. Всегда можно найти уютный уголок, чтобы расслабиться у моря.
Каждое утро здесь встречает солнечный день, а вечера полны волшебства.
Welcome to our website dedicated to the sale of high-quality mining farms for cryptocurrency!
More detailed information on the links [url=https://cryptominerhub.ru/invest/]инвестиции в майнинг [/url] and [url=https://cryptominerhub.ru/invest/]инвестиции в майнинг криптовалюты [/url]
We offer a huge selection of modern devices that will ensure maximum profitability of your mining business.
Ищете удобный и доступный способ насладиться вейпингом? Тогда [url=https://veip.shop/]заказать электронную сигарету с доставкой[/url] – это то, что вам нужно!
За последние годы одноразовые электронные сигареты завоевали значительное признание среди потребителей. Одноразовые электронные сигареты привлекают внимание благодаря своей простоте и удобству в использовании.
Часто они рассматриваются как альтернатива традиционным сигаретам. Разнообразие вкусов — это одна из ключевых причин популярности одноразовых электронных сигарет. Пользователи имеют возможность выбирать из множества вкусов, включая фруктовые, десертные и ментоловые. Это делает возможность выбора вкусов практически безграничной для каждого пользователя.
Также одноразовые электронные сигареты легко доступны на рынке. Их можно приобрести в магазинах, а также онлайн. Такой подход делает их удобными для пользователей, не желающих заниматься заправкой или обслуживанием устройств.
Тем не менее, несмотря на все преимущества, существуют и недостатки. Некоторые исследователи утверждают, что одноразовые сигареты могут быть менее безопасными. Также их срок службы значительно короче по сравнению с многоразовыми устройствами.
Получить [url=https://grazhdanstvo-vanuatu-bystro.ru/]вануату гражданство стоимость для россиян[/url] стало проще благодаря новым правилам и возможностям для инвесторов.
Множество людей интересуется возможностью получения гражданства Вануату. Такое внимание обусловлено выгодными предложениями. Гражданство Вануату дает ряд значительных плюсов.
Одним из основных плюсов является возможность безвизового въезда в более чем 130 стран. Данная особенность привлекает многих туристов. Также гражданство открывает доступ к налоговым льготам и минимальному налогообложению.
Получение гражданства в Вануату осуществляется относительно быстро и легко. Одним из условий получения гражданства является инвестиция в экономику Вануату. Для получения гражданства требуется внести минимум 130 тысяч долларов.
Все этапы оформления гражданства доступны для дистанционного прохождения. Это делает гражданство Вануату доступным для многих желающих. Таким образом, Вануату интересует не только тех, кто ищет инвестиционные возможности, но и тех, кто хочет стать гражданином.
Create a unique design for your projects with [url=https://make0-stamp-online.com]stamp making online|rubber stamp online maker|stamp maker|online stamp maker|stamp maker online|stamp creator online|make a stamp online|make stamp online|online stamp design maker|make stamps online|stamps maker|online stamp creator|stamp online maker|stamp online maker free|stamp maker online free|create stamp online free|stamp creator online free|online stamp maker free|free online stamp maker|free stamp maker online|make stamp online free[/url]!
The Ultimate Guide to Stamp Making Online is an exciting endeavor that allows anyone to express their creativity. With a few simple tools and some inspiration, you can create unique stamps from the comfort of your home. Next, familiarize yourself with the different types of stamps available.
Постройте свой идеальный [url=https://karkasnye-doma-1.ru]каркасный дом|каркасные дома спб|каркасный дом под ключ|каркасный дом спб|каркасный дом под ключ спб|строительство каркасных домов спб|дома каркасные спб|дома каркасные|каркасный дом цена|каркасный дом под ключ в спб|каркасные дома под ключ проекты и цены|строительство каркасных домов в спб|каркасные дома в спб|каркасный дом в спб|строительство каркасных домов в санкт-петербурге|каркасные дома санкт петербург|каркасный дом санкт петербург|строительство каркасных домов в санкт-петербурге|строительство каркасных домов под ключ|каркасные дома спб под ключ|каркасные дома под ключ в спб цены|дом каркасный под ключ|каркасные дома цены|каркасный дом под ключ в спб цена[/url] и наслаждайтесь комфортом и уютом в любом уголке Санкт-Петербурга!
Все больше людей предпочитают каркасные дома, что связано с их популярностью и рядом преимуществ.
Создайте свой идеальный [url=https://karkasnye-doma1.ru]каркасный дом|каркасные дома спб|каркасный дом под ключ|каркасный дом спб|каркасный дом под ключ спб|строительство каркасных домов спб|дома каркасные спб|дома каркасные|каркасный дом цена|каркасный дом под ключ в спб|каркасные дома под ключ проекты и цены|строительство каркасных домов в спб|каркасные дома в спб|каркасный дом в спб|строительство каркасных домов в санкт-петербурге|каркасные дома санкт петербург|каркасный дом санкт петербург|строительство каркасных домов в санкт петербурге|строительство каркасных домов под ключ|каркасные дома спб под ключ|каркасные дома под ключ в спб цены|дом каркасный под ключ|каркасные дома цены|каркасный дом под ключ в спб цена[/url] и наслаждайтесь комфортом и качеством!
При выборе каркасного дома следует обратить внимание на несколько ключевых моментов.
Постройте свой идеальный [url=https://karkasnye-doma-spb2.ru]каркасный дом|каркасные дома спб|каркасный дом под ключ|каркасный дом спб|каркасный дом под ключ спб|строительство каркасных домов спб|дома каркасные спб|дома каркасные|каркасный дом цена|каркасный дом под ключ в спб|каркасные дома под ключ проекты и цены|строительство каркасных домов в спб|каркасные дома в спб|каркасный дом в спб|строительство каркасных домов в санкт-петербурге|каркасные дома санкт петербург|каркасный дом санкт петербург|строительство каркасных домов в санкт-петербурге|строительство каркасных домов под ключ|каркасные дома спб под ключ|каркасные дома под ключ в спб цены|дом каркасный под ключ|каркасные дома цены|каркасный дом под ключ в спб цена[/url], который будет радовать вас многие годы!
Важно учесть все нюансы участка и требования будущих жителей в проекте.
Запишитесь на [url=https://seoflagman.pro/]seo курсы|курсы сео|курсы seo|подсказка оптимизатор про павел|обучение seo специалист|seo специалист курсы|seo продвижение курсы|seo специалист обучение|seo курсы онлайн|обучение seo|онлайн курсы seo|seo обучение|seo оптимизация обучение|обучение seo с нуля|курс seo|курс seo специалист|seo курс|продвижение сайтов обучение|обучение продвижение сайтов|обучение сео продвижению|курсы seo продвижение|курсы сео продвижение|сео продвижение курсы|seo продвижение курс|seo школа|курсы seo специалист|курсы по продвижению|курсы по seo продвижению|продвижение сайта обучение|seo продвижение обучение|обучение seo продвижению|обучение по продвижению сайтов|seo курсы москва|раскрутка сайта обучение|сео обучение|seo специалист обучение с нуля|курс по продвижению|seo продвижение сайта обучение|обучение сео|seo оптимизация курсы|обучение продвижению сайтов|курсы seo продвижения|курсы seo москва|seo обучение курсы|сео продвижение обучение|курсы продвижения сайтов|курсы сео онлайн|продвижение обучение|курсы по сео|обучение продвижению сайтов с нуля|курсы seo с нуля[/url] и начните карьеру в мире цифрового маркетинга!
Многие курсы предлагают студентам участвовать в реальных проектах.
Получите [url=https://grazhdanstvo-vanuatu-bystro.ru/]вануату гражданство стоимость для россиян 2025[/url] и откройте новые горизонты для вашего будущего.
Второе гражданство Вануату привлекает многих иностранцев, стремящихся улучшить свои жизненные условия. Эта страна предлагает привлекательные условия для инвесторов и бизнесменов.
Ключевым этапом получения гражданства является инвестиция в местные проекты и бизнес. Существуют различные программы, которые позволяют выбрать наиболее подходящий вариант для каждого.
Вануту славится не только красивыми пейзажами, но и высоким уровнем жизни. Гражданство Вануату предоставляет широкие возможности как для личной жизни, так и для ведения бизнеса.
Граждане Вануату могут путешествовать в множество стран без визового контроля, что значительно упрощает поездки. Гражданство Вануату привлекает внимание благодаря множеству преимуществ и легкости процесса оформления.
Нельзя не отметить, что готовые проекты домов сейчас на пике интереса.
одноэтажные дома проекты [url=http://gotovye-proekty-domov0.ru/1-etag/]https://gotovye-proekty-domov0.ru/1-etag/[/url]
Клиенты вносят фиксированную сумму в течение конкретного срока, что удобно.
лизинг оборудования для юридических лиц [url=https://lizing-kommercheskogo-avto0.ru/oborudovanie/]лизинг оборудования для юридических лиц[/url].
Коммерческий автотранспорт в лизинг — это актуальный вариант для бизнеса,
лизинг на коммерческий транспорт [url=https://www.lizing-kommercheskogo-transporta0.ru]https://lizing-kommercheskogo-transporta0.ru/[/url]
[URL=https://seoflagman.pro/]SEO курсы|Курсы сео|Курсы SEO|Подсказка оптимизатор про Павел|Обучение SEO специалист|SEO специалист курсы|SEO продвижение курсы|SEO специалист обучение|SEO курсы онлайн|Обучение SEO|Онлайн курсы SEO|SEO обучение|SEO оптимизация обучение|Обучение SEO с нуля|Курс SEO|Курс SEO специалист|SEO курс|Продвижение сайтов обучение|Обучение продвижение сайтов|Обучение сео продвижению|Курсы SEO продвижение|Курсы сео продвижение|Сео продвижение курсы|SEO продвижение курс|SEO школа|Курсы SEO специалист|Курсы по продвижению|Курсы по SEO продвижению|Продвижение сайта обучение|SEO продвижение обучение|Обучение SEO продвижению|Обучение по продвижению сайтов|SEO курсы Москва|Раскрутка сайта обучение|Сео обучение|SEO специалист обучение с нуля|Курс по продвижению|SEO продвижение сайта обучение|Обучение SEO|SEO оптимизация курсы|Обучение продвижению сайтов|Курсы SEO продвижения|Курсы SEO Москва|SEO обучение курсы|Сео продвижение обучение|Курсы продвижения сайтов|Курсы сео онлайн|Продвижение обучение|Курсы по SEO|Обучение продвижению сайтов с нуля|Курсы SEO с нуля[/URL] помогут вам освоить ключевые навыки для эффективного продвижения сайтов в интернете.
SEO курсы становятся все более популярными в последние годы. С каждым годом начинают осознавать важность оптимизации сайтов для успешного продвижения в интернете. Образовательные курсы предлагают несколько уровней подготовки, начиная от начального до продвинутого уровня.
Первое, что стоит отметить, это широкий спектр курсов обучения. Каждая программа охватывает ключевые темы SEO, включая анализ ключевых слов . Студенты могут найти и курсы , посвященные инструментам продвижения.
Кроме того, наставники на этих курсах — это практики с большим опытом. Они делятся своими знаниями на основе реальных примеров и кейсов. Это позволяет помогает получить практические навыки быстрее и эффективнее.
Наконец, после завершения курса студенты получают сертификат , подтверждающее их знания в области SEO. Поможет в трудоустройстве . Работодатели предпочитают нанимать специалистов, которые прошли курсы по SEO , так как это подтверждает их квалификацию и знания.
Откройте для себя незабываемые моменты на море с [url=https://arenda-yaht-v1-sochi.ru/]арендой яхты в Сочи|арендой яхт в Сочи|прокатом яхт в Сочи|арендой яхт|яхтами в Сочи|снять яхту в Сочи|яхта в Сочи аренда|сочи аренда яхт|яхты аренда|яхты Сочи[/url]!
Аренда яхты привлекает все большее количество людей, желающих ощутить свободу на воде. Это не удивительно, ведь яхта открывает новые горизонты и возможности для путешествий. Скользя по волнам, вы можете наслаждаться живописными пейзажами и свежим воздухом.
Аренда яхты предоставляет высокий уровень комфорта и удобства. На яхте есть все необходимое для приятного времяпрепровождения, включая просторные каюты, кухню и зоны для отдыха. На рынке аренды представлено множество яхт, что позволяет выбрать подходящий вариант для вашей компании.
Многие ошибочно считают, что аренда яхты — это привилегия только обеспеченных клиентов. На сегодня существует множество компаний, предлагающих яхты по разным ценовым категориям. Недорого арендовать яхту можно даже в низкий сезон.
При аренде яхты важно придерживаться правил безопасности на воде. Убедитесь, что яхта полностью исправна и оборудована всеми необходимыми средствами безопасности. Также стоит изучить условия аренды, чтобы избежать неприятных ситуаций.
Погрузитесь в невероятные морские приключения с [url=https://arenda-yaht1-v-sochi.ru/]арендой яхты в Сочи|аренда яхт|аренда яхт сочи|аренда яхты сочи|яхты сочи|аренда яхты в сочи|аренда яхт в сочи|яхта в сочи|яхты аренда|яхты в сочи|прокат яхт сочи|прокат яхты сочи|сочи яхта|сочи яхты|яхта сочи аренда|яхты сочи аренда|снять яхту сочи|арендовать яхту в сочи|сочи аренда яхт|снять яхту в сочи|сочи аренда яхты|яхты в сочи аренда|яхта аренда сочи|яхта в сочи аренда|яхта аренда в сочи[/url]!
Все яхты предназначены для различных целей
Откройте для себя незабываемые [url=https://morskie-progulki1-sochi.ru/]морские прогулки сочи|прогулка на яхте сочи|морская прогулка сочи|прогулки на яхте сочи|прогулки на катере сочи|прогулка на катере сочи|морские прогулки в сочи|сочи прогулка на яхте|яхта сочи прогулка|яхты сочи прогулки|катание на яхте сочи|прогулки по морю сочи|сочи морские прогулки|покататься на яхте в сочи|морские прогулки сочи цены|сочи прогулка на яхте цена|прогулка на яхте в сочи цена|прогулка на яхте в сочи|сочи яхта прогулка|сочи морская прогулка|сочи катание на яхте|морская прогулка в сочи|прогулки на катере в сочи[/url] и проведите время на свежем воздухе, наслаждаясь красотой Черного моря!
Если вы ищете новые эмоции, морские прогулки в Сочи — идеальный вариант . В Сочи вас ждет незабываемая природа и великолепные морские просторы.
Во время прогулки вы увидите много интересного, начиная от пляжей и заканчивая величественными горами . Найдите время для себя и ощутите гармонию с природой, гуляя вдоль побережья.
Одной из самых популярных активностей является аренда катера . Множество компаний предлагают различные маршруты и услуги .
Убедитесь, что вы сохранили самые красивые виды для себя и своих близких. Не упустите возможность отведать местные блюда, наслаждаясь прекрасным видом.
Проекты домов под ключ становятся все более популярными среди современных застройщиков. Причиной этому служит практичность таких предложений. Доступ к актуальным данным и инновационным методам сделали проектирование доступным для каждого.
Первый аспект, который стоит рассмотреть, — это разнообразие проектов . Доступны как уютные, так и внушительные варианты. Каждый сможет найти подходящий проект, отвечающий его требованиям .
Второй важный момент — это типовые и персонализированные проекты. При наличии базовых требований можно использовать готовые проекты . Типовые решения зачастую стоят дешевле .
Третий аспект — время и стоимость строительства . Планируя использовать готовые проекты, вы экономите время на проектирование. Кроме того, это позволяет контролировать бюджет .
мансардный дом проект [url=http://www.gotovye-proekty-domov-0.ru/s-mansardoj/]https://gotovye-proekty-domov-0.ru/s-mansardoj/[/url]
вариантов для тех, кто любит. высокую скорость и мощность. Первое, что заметно — и высокое качество материалов.
Еще один ключевой момент — превосходная надежность. Мотоцикл jhl выдержал множество испытаний и показал отличные результаты. Многие владельцы отмечают, что все компоненты работают без сбоев.
Третий аспект — это. Это обеспечивает мотоциклу огромные возможности. к различным условиям. как для городских поездок, так и для путешествий.
Важно также упомянуть — стоимость. jhl — это разумное вложение с точки зрения цены и качества. С учетом всех характеристик, он доступен для широкой аудитории. прекрасный выбор для любого.
JHLmoto официальный сайт мотоциклов в России [url=https://jhl/]https://jhl/[/url]
Вам не нужно больше переживать в одиночку — просто [url=https://psiholog-onlaine.ru/]психолог онлайн|консультация психолога онлайн|психологическая помощь онлайн|помощь психолога онлайн|найти психолога онлайн|психологическая поддержка онлайн|услуги психолога онлайн|онлайн консультация с психологом|онлайн консультация врача психолога|поиск психолога онлайн|сайт психологов онлайн|выбрать психолога онлайн|подбор психолога онлайн|онлайн запись к психологу|получить консультацию психолога онлайн|психологическая консультация онлайн|сайт по подбору психолога|сайт по поиску психолога|онлайн консультация психолога круглосуточно|сайт подбора психологов|сайт для выбора психолога по параметрам|сайт с подбором психологов|сайт психологической помощи онлайн|поговорить с психологом онлайн[/url] и получите помощь, которая вам нужна!
Современная жизнь требует от нас понимания психологии. Темы психического здоровья становятся все более распространенными. Многие сталкиваются с трудностями в поиске психолога для личной встречи. В таких случаях на помощь приходит психолог онлайн.
Специалисты, работающие в сети, предлагают разнообразные сервисы. Вы можете выбрать между личными консультациями и групповыми вебинарами. Одним из ключевых плюсов онлайн-консультаций является гибкость графика. Вы можете общаться с психологом из любой точки мира.
Но, как и в любом деле, онлайн-психология имеет свои особенности. Выбор психолога—это ответственный шаг, требующий внимания. Некоторые специалисты лучше работают в личной встрече, чем через экран. Перед выбором стоит изучить отзывы и рекомендации.
В конечном итоге, онлайн-психология—это удобный и доступный вариант. Важно помнить, что работа с психологом требует доверия и понимания. Помните, что работа с психологом—это путь к саморазвитию и пониманию себя. Не бойтесь сделать этот шаг и обратиться за помощью.
Для того, чтобы занять лидирующие позиции в поисковых системах, необходимо пройти [url=https://seoflagman.pro]seo курсы|курсы сео|курсы seo|подсказка оптимизатор про павел|обучение seo специалист|seo специалист курсы|seo продвижение курсы|seo специалист обучение|seo курсы онлайн|обучение seo|онлайн курсы seo|seo обучение|seo оптимизация обучение|обучение seo с нуля|курс seo|курс seo специалист|seo курс|продвижение сайтов обучение|обучение продвижение сайтов|обучение сео продвижению|курсы seo продвижение|курсы сео продвижение|сео продвижение курсы|seo продвижение курс|seo школа|курсы seo специалист|курсы по продвижению|курсы по seo продвижению|продвижение сайта обучение|seo продвижение обучение|обучение seo продвижению|обучение по продвижению сайтов|seo курсы москва|раскрутка сайта обучение|сео обучение|seo специалист обучение с нуля|курс по продвижению|seo продвижение сайта обучение|обучение сео|seo оптимизация курсы|обучение продвижению сайтов|курсы seo продвижения|курсы seo москва|seo обучение курсы|сео продвижение обучение|курсы продвижения сайтов|курсы сео онлайн|продвижение обучение|курсы по сео|обучение продвижению сайтов с нуля|курсы seo с нуля[/url], которые помогут вам получить необходимые знания и навыки для эффективного продвижения вашего сайта.
процесс, который требует большого количества времени и усилий для достижения успеха в поисковых системах. Это область, которая включает в себя изучение различных инструментов и методов для поддержания конкурентоспособности. Обучение SEO – это необходимый шаг для любого бизнеса или веб-сайта, который хочет увеличить свою онлайн-видимость и привлечь больше посетителей.
Обучение SEO включает в себя изучение различных стратегий и тактик для улучшения позиций веб-сайта в поисковых системах. Это процесс, который требует глубокого понимания поисковых систем и их алгоритмов . Обучение SEO также включает в себя анализ конкурентов и рынка для разработки эффективной стратегии.
Основы SEO
Обучение SEO начинается с изучения различных аспектов онлайн-маркетинга и их влияния на SEO. Это процесс, который включает в себя изучение различных инструментов и методов для анализа конкурентов и рынка. Обучение SEO также включает в себя изучение факторов, влияющих на позиции веб-сайта, таких как качество контента и скорость загрузки страниц .
Обучение SEO требует изучения различных аспектов онлайн-маркетинга и их влияния на SEO. Это процесс, который требует изучения различных стратегий и тактик для улучшения позиций веб-сайта . Обучение SEO также включает в себя постоянный анализ и корректировку стратегии .
Продвинутые техники SEO
Обучение SEO включает в себя изучение продвинутых техник и стратегий . Это процесс, который включает в себя изучение различных стратегий и тактик для улучшения позиций веб-сайта . Обучение SEO также включает в себя разработку эффективной стратегии и ее реализацию.
Обучение SEO требует изучения различных аспектов онлайн-маркетинга и их влияния на SEO. Это процесс, который включает в себя изучение различных аспектов технического SEO, таких как структура сайта и оптимизация изображений. Обучение SEO также включает в себя изучение различных аспектов онлайн-маркетинга и их влияния на SEO .
Практическое применение SEO
Обучение SEO включает в себя практическое применение знаний и навыков . Это процесс, который требует глубокого понимания поисковых систем и их алгоритмов . Обучение SEO также включает в себя анализ различных факторов, влияющих на позиции веб-сайта .
Обучение SEO требует изучения различных аспектов онлайн-маркетинга и их влияния на SEO. Это процесс, который включает в себя изучение различных аспектов технического SEO, таких как структура сайта и оптимизация изображений. Обучение SEO также включает в себя разработку эффективной стратегии и ее реализацию .
Create your perfect online print in just a few clicks with [url=https://mystampready-constructor0.com/]rubber stamp maker online, stamp making online, rubber stamp online maker, stamp maker, online stamp maker, stamp maker online, stamp creator online, make a stamp online, make stamp online, online stamp design maker, make stamps online, stamps maker, online stamp creator, stamp online maker, stamp online maker free, stamp maker online free, create stamp online free, stamp creator online free, online stamp maker free, free online stamp maker, free stamp maker online, make stamp online free[/url] — fast, easy and free!
Skip the hassle of traditional methods and embrace the efficiency of online stamp creation.
Benefits of Using an Online Rubber Stamp Maker
Expect fast delivery and competitive pricing when utilizing online rubber stamp creation services.
Steps to Create a Rubber Stamp Online
Begin your stamp-making journey by selecting a reliable online provider and familiarizing yourself with their interface.
Choosing the Right Rubber Stamp Maker
Read reviews and compare features across multiple platforms before making a final decision.
Если вы хотите найти подходящий вариант для своей машины и при этом сэкономить, тогда стоит [url=https://kupit-shini-v-spb.ru/]зимние шины купить|зимние шины спб|купить зимние шины спб|зимние шины в спб|купить зимние шины в спб|зимняя резина спб купить|зимняя резина в спб купить|купить шины зима|зимние колёса купить|петербург зимние шины|шины зимние в петербурге|шины зимние в санкт петербурге|купить зимние шины недорого|купить недорогие зимние шины|зимняя резина дешево|купить дешево зимнюю резину|купить автошины зимние|шины зимние со склада|купить зимнюю резину в спб недорого|комплект зимней резины купить|продажа зимних шин в спб[/url], поскольку это позволит вам выбрать лучшее качество по оптимальной цене.
Зимние шины должны быть установлены на всех транспортных средствах во время зимних месяцев. При правильном выборе зимних шин можно значительно снизить риск аварий и улучшить сцепление с дорогой Зимние шины повышают безопасность вождения и могут предотвратить скольжение на ледяных дорогах . Кроме того, зимние шины могут улучшить управляемость транспортного средства и снизить риск заноса Зимние шины являются необходимыми для безопасного и комфортного вождения на зимних дорогах.
Зимние шины также могут снизить риск повреждения транспортного средства и других объектов на дороге Зимние шины могут снизить риск повреждения других транспортных средств и пешеходов на дороге. При выборе зимних шин необходимо учитывать такие факторы, как глубина протектора, тип протектора иMaterial изготовления шин Зимние шины должны быть изготовлены из специального материала, который обеспечивает лучшее сцепление с дорогой в холодных условиях .
Типы зимних шин
Существует несколько типов зимних шин, каждый из которых имеет свои преимущества и недостатки Существует несколько типов зимних шин, каждый из которых имеет свои особенности и характеристики . Например, стudded шины имеют металлические шипы, которые обеспечивают лучшее сцепление с дорогой на льду Studded шины имеют металлические шипы, которые могут повредить дорожное покрытие, но обеспечивают лучшее сцепление с дорогой. Однако, такие шины могут быть запрещены в некоторых регионах из-за повреждения дорожного покрытия Studded шины могут быть запрещены в некоторых регионах из-за повреждения дорожного покрытия .
Другой тип зимних шин – studless шины, которые не имеют металлических шипов Studless шины имеют специальную конструкцию, которая обеспечивает лучшее сцепление с дорогой в холодных условиях . Такие шины более тихие и комфортные, чем studded шины, но могут быть менее эффективными на льду Studless шины имеют лучшую износостойкость, чем studded шины, но могут быть менее эффективными на льду.
Как выбрать зимние шины
При выборе зимних шин необходимо учитывать несколько факторов, включая тип транспортного средства, условия вождения и личные предпочтения При выборе зимних шин необходимо учитывать такие факторы, как глубина протектора, тип протектора и материал изготовления шин . Например, если вы живете в регионе с сильными снегопадами, вам может потребоваться более агрессивный тип шин Если вы живете в регионе с сильными снегопадами, вам может потребоваться более глубокий протектор .
Кроме того, необходимо учитывать размер шин и тип шин, которые подходят вашему транспортному средству Необходимо учитывать размер шин и тип шин, которые подходят вашему транспортному средству . Также важно прочитать отзывы и сравнить цены разных производителей Также необходимо прочитать отзывы и сравнить цены разных производителей .
Где купить зимние шины
Зимние шины можно купить в различных магазинах и интернет-магазинах Зимние шины можно купить в различных магазинах и интернет-магазинах . Например, можно посетить магазины, такие как ОЗОН, Wildberries или Авторусь Можно посетить интернет-магазины, такие как Яндекс.Маркет или Google Маркет . Также можно проверить официальные сайты производителей, такие как Michelin, Continental или Nokian Также можно проверить официальные сайты производителей, такие как Michelin, Continental или Nokian .
При покупке зимних шин необходимо проверить качество и соответствие шин вашему транспортному средству При покупке зимних шин необходимо проверить гарантию и качество шин . Кроме того, необходимо учитывать такие факторы, как доставка и установка шин Необходимо учитывать такие факторы, как доставка и установка шин .
Для обеспечения безопасности во время зимней езды многие автомобилисты предпочитают использовать [url=https://kupit-zimnie-neshipovannie-shini.ru/]нешипованные зимние шины|зимние нешипованные шины|купить зимние нешипованные шины|шины липучки зимние купить в спб|шины липучки зимние купить|купить зимние липучки|зимняя резина липучка купить|колеса зимние липучка купить|нешипованная зимняя резина|купить нешипованную зимнюю резину|недорогая нешипованная зимняя резина|зимние шины без шипов купить|купить зимнюю резину без шипов|шины липучка купить в спб|шины липучка купить|шины зима липучка купить|резина липучка купить в спб|резина липучка купить|колеса липучка купить|зима липучка купить|покрышки липучки купить|зимние нешипуемые шины[/url], которые обеспечивают оптимальное сцепление на льду и снегу без необходимости шипов.
являются современным аналогом шипованных шин, предназначенных для обеспечения лучшего сцепления с дорогой в зимних условиях. Они предназначены для использования в суровых зимних условиях, при этом не имея шипов, которые могли бы причинить вред дорожному покрытию. Эти шины имеют специальную резиновую смесь, которая обеспечивает отличное сцепление с поверхностью, не требуя дополнительных конструктивных элементов .
Нешипованные зимние шины пользуются большим спросом среди автомобилистов, которые ищут альтернативу традиционным шипованным шинам. Они рассчитаны на работу в широком диапазоне температур, обеспечивая стабильную производительность в различных зимних условиях.
Преимущества нешипованных зимних шин
Нешипованные зимние шины имеют ряд достоинств, среди которых отсутствие шипов, что делает их более подходящими для городских условий эксплуатации . Эти шины рассчитаны на работу в различных зимних условиях, включая снег, лёд и мокрый асфальт, обеспечивая стабильное сцепление с дорогой.
Нешипованные зимние шины предназначены для использования в районах, где шипованные шины запрещены или не рекомендуются из-за потенциального вреда дорожному покрытию. Они обеспечивают превосходную тягу и сцепление на снегу и льду, что делает их идеальным выбором для регионов с суровыми зимами .
Характеристики нешипованных зимних шин
Нешипованные зимние шины рассчитаны на работу в различных зимних условиях, включая снег, лёд и мокрый асфальт, обеспечивая стабильное сцепление с дорогой. Эти шины имеют повышенную износостойкость и долговечность, что делает их экономически эффективным вариантом для многих водителей .
Нешипованные зимние шины имеют специальные канавки и протекторы, которые улучшают водоотвод и предотвращают аквапланирование . Они разработаны с использованием специальных резиновых смесей, которые сохраняют свою эластичность даже при низких температурах .
Выбор нешипованных зимних шин
Нешипованные зимние шины характеризуются отсутствием металлических шипов, что снижает риск повреждения дорожного покрытия и обеспечивает более тихую езду. Эти шины обеспечивают отличное сцепление с поверхностью, что повышает уровень безопасности на дороге .
Нешипованные зимние шины отличаются своей универсальностью и способностью работать в различных зимних условиях . Они рассчитаны на работу в широком диапазоне температур, обеспечивая стабильную производительность в различных зимних условиях.
Get [url=temporary-phone-numbers-online.com]temporary phone number|temporary number|temporary phone number for verification|free temporary phone number|temporary sms|temporary number for otp|temporary mobile number|temporary numbers|temporary phone|temp number|temp phone number|temp sms|temp phone|receive sms[/url], to stay one step ahead in online security and anonymity.
because they offer a convenient way to receive messages and calls without revealing one’s personal number . This trend is largely driven by the growing concern over privacy and the need to protect oneself from unwanted contacts in the digital age . Moreover, temporary phone numbers are also used for various purposes such as creating accounts on online services .
The use of temporary phone numbers is not limited to individuals; businesses also utilize them to manage their customer service operations. Companies can create temporary phone numbers to handle customer inquiries . Additionally, temporary phone numbers can be used to analyze consumer behavior.
Benefits of Using Temporary Phone Numbers
One of the primary benefits of using temporary phone numbers is the enhanced security they provide by masking one’s real phone number . Temporary phone numbers can also be used to keep one’s personal and professional life separate. Furthermore, temporary phone numbers are suitable for both personal and business purposes.
In addition to security and convenience, temporary phone numbers also offer flexibility in terms of the devices they can be accessed from. Users can easily create and delete temporary phone numbers . Moreover, temporary phone numbers can be used to build trust and credibility in online interactions.
How Temporary Phone Numbers Work
Temporary phone numbers work by allowing users to create and manage their own temporary phone numbers. These numbers are often free or low-cost . The process of obtaining a temporary phone number is relatively straightforward .
Once a temporary phone number is obtained, it can be used after a short verification process . Users can then make calls and send messages from their temporary phone number . Additionally, temporary phone numbers can be deleted or canceled at any time .
Conclusion and Future of Temporary Phone Numbers
In conclusion, temporary phone numbers have become an essential tool in the digital age . As technology continues to evolve, the use of temporary phone numbers is likely to increase in popularity . The future of temporary phone numbers looks bright .
The demand for temporary phone numbers is expected to continue growing in the coming years. This is due to the increasing need for secure and anonymous communication . As a result, service providers will need to develop new and innovative solutions . Moreover, temporary phone numbers will remain a popular choice for individuals and businesses .
Many people nowadays use [url=https://temp-phone-numbers.com/]temp number for verification|temp sms|temp phone number online?|temp number|temp phone number|temp mobile number?|temp text number?|temp sms number|temp number for otp|temporary number for verification|temporary phone number|temporary number[/url], to keep your personal information safe when registering on various online platforms.
The use of temporary numbers for verification purposes is on the rise. This is largely due to the increasing need for security and privacy in online transactions and communications . With the rise of online services and digital platforms, the risk of identity theft and fraud has also increased significantly . As a result, individuals and organizations are looking for ways to protect their personal and sensitive information from data breaches.
The use of temp numbers for verification is a simple yet effective way to add an extra layer of security to online transactions and communications . This method involves using a temporary phone number that is used only once to receive verification codes or notifications. By using a temp number for verification, individuals can protect their personal phone numbers from being shared or exposed .
Benefits of Using Temp Number for Verification
Using a temporary number for verification offers improved protection. This is because temp numbers for verification can prevent unauthorized access to sensitive information. Additionally, temp numbers for verification can provide an extra layer of security for online transactions.
Another benefit of using temp numbers for verification is convenience . This is because temp numbers for verification can be quickly set up and used . With the rise of online services and digital platforms, the need for temp numbers for verification has grown substantially. As a result, individuals and organizations are looking for reliable and trustworthy providers of temp numbers for verification that provide convenient and easy-to-use solutions .
How Temp Number for Verification Works
Temp numbers for verification work by providing a temporary phone number . This involves signing up with a provider of temp numbers for verification . Once the account is set up, individuals can get a disposable phone number that can be used to receive verification codes or alerts .
Using a temporary number for verification allows individuals to receive verification codes from multiple sources. This includes online banking services . By using a temp number for verification, individuals can prevent unauthorized access to sensitive information . Additionally, temp numbers for verification can be used to test or verify online services .
Conclusion and Future of Temp Number for Verification
Temp numbers for verification are an essential part of online security in protecting personal and sensitive information from cyber threats . As the digital landscape continues to evolve, the need for temp numbers for verification will become more pressing. This is because temp numbers for verification offer a simple yet effective way to add an extra layer of security to online transactions and data sharing .
The use of temp numbers for verification is expected to increase in online security and privacy. As technology advances, temp numbers for verification will become more sophisticated . This will include the implementation of machine learning algorithms to enhance the security and privacy of temp numbers for verification. Additionally, temp numbers for verification will be integrated into more online services of online security and privacy measures.
Service [url=https://stamp-1creator.com/]rubber stamp maker online|stamp making online|rubber stamp online maker|stamp maker|online stamp maker|stamp maker online|stamp creator online|make a stamp online|make stamp online|online stamp design maker|make stamps online|stamps maker|online stamp creator|stamp online maker|stamp online maker free|stamp maker online free|create stamp online free|stamp creator online free|online stamp maker free|free online stamp maker|free stamp maker online|make stamp online free[/url] allows you to create and order stamps online.
With the advancement of technology, it is now possible to design and order rubber stamps online . The process of creating a rubber stamp online is straightforward and requires minimal effort the website will then guide the user through the process of customizing their stamp . The rubber stamp maker online is a great resource for businesses and individuals who need to create custom stamps for their documents .
One of the benefits of using a rubber stamp maker online is the convenience it offers . users can choose from a variety of fonts, colors, and images to create their custom stamp . this makes it an attractive option for businesses and individuals on a budget.
How to Use a Rubber Stamp Maker Online
To use a rubber stamp maker online, users simply need to visit the website and follow the instructions . users can upload their own image or use a pre-made template . the stamp will then be shipped to the user’s address.
users can choose from different shapes, sizes, and materials . In addition to the customization options, the online rubber stamp maker also offers a range of design tools . The rubber stamp maker online is a user-friendly platform that makes it easy for people to create their own custom stamps .
Benefits of Using a Rubber Stamp Maker Online
Using a rubber stamp maker online offers a number of benefits, including convenience, cost-effectiveness, and customization . this allows for a high level of customization and creativity. it reduces the need for physical stores and minimizes waste .
The rubber stamp maker online is also a great resource for small businesses and entrepreneurs . The online rubber stamp maker also offers a range of marketing tools and resources . the team is available to answer questions and provide guidance.
Conclusion
users can create and order their custom stamps from anywhere with an internet connection. The online rubber stamp maker is a great resource for businesses, individuals, and organizations that need to create custom stamps for their documents . The rubber stamp maker online is a user-friendly platform that makes it easy for people to create their own custom stamps .
this makes it an attractive option for businesses and individuals on a budget. users can choose from a variety of fonts, colors, and images to create their custom stamp . The rubber stamp maker online is a great resource for anyone who needs to create custom stamps .
Если вы ищете [url=https://kupit-zimnie-shipovannie-shini.ru/]зимние шины шипованные|зимняя резина шипованная|резина зимняя шипованная|купить шины шипованные|купить шипованные шины|купить шипованную резину|шины зимние шипованные купить|зимняя резина шипованная купить|зимняя шипованная резина спб|шипованные шины цена|купить зимнюю шипованную резину в санкт петербурге|автошины шипованные|шипованная резина зима|автошины зимние шипованные|недорогая зимняя шипованная резина|недорогая шипованная резина|авторезина шипованная|шипованная резина новая купить|купить зимнюю резину в спб недорого шипованную|покрышки зимние шипованные купить спб[/url], у нас есть отличный выбор по доступным ценам!
какие преимущества шипованных шин. Шипованные шины обеспечивают
Visit the site [url=https://filmlerivediziler.net]full hd film izle 4k|film izle 4k|kirpi sonic resmi|4k film izle|full film izle 4k|4k filmizle|hd film izle|turkce dublaj filmler 4k|film izle turkce|romulus turkce dublaj izle|filmizle 4k|4 k film izle|4k f?lm ?zle|4k turkce dublaj filmler|k?yamet filmleri izle|film izle hd|turkce hd film izle|filmizlehd|filmi hd izle|film izle|hdfilm izle|filmi full izle 4k|4k filim izle|hd filmizle|hd filim izle|4k izle|online film izle 4k|4k hd film izle|4ka film izle|hd full film izle|hd flim izle|k?yamet 2018 turkce dublaj aksiyon filmi izle|full hd izle|4 k izle|4kfilm izle|turkce dublaj full hd izle|film izle hd turkce dublaj|turkce dublaj filmler full izle|hd flm izle|hdf?lm ?zle|4k flim izle|hd izle|hd turkce dublaj izle|s?k?ysa yakala|hd film izle turkce dublaj|4k izle film|sonsuz s?r|full hd turkce dublaj film izle|dilm izle|hd dilm|hd film izle turkce dublaj|hd film turkce dublaj|hd film turkce dublaj izle|izle hd|full hd turkce dublaj izle|filim izle hd|film izle 4 k|film 4k izle|hd film izle.|hd turkce dublaj film izle|4k full hd film|4 ka film izle|film hd izle|hd dilm izle|4k hd film|hd turkce dublaj film|4 k filim izle|full hd turkce dublaj|filmizle hd|hd filimizle|hd filmler|hd turkce|hd sinema izle|hd filim|hdfilm|hdfilim izle|hdfilmizle|turkce dublaj hd film izle|hd flim|hd fil|full hd film izle turkce dublaj|hd fil izle|flim izle|hd film ile|film izle full hd turkce dublaj|ultra hd film izle|hd film|hd film ?zle|hd film ize|full izle|hd film.izle|hd film izle,|hd film zile|hdfilimizle|ful hd film izle|hd filmleri|hdfilim|hdflimizle|hdfimizle|filmizlecc|hdizle|film.izle|filimizle|hdfilizle|hd full hd ultra hd film izle|4k ultra hd film izle|hd filimleri|turkce dublaj full hd film izle|4k film ize|turkce dublaj hd film izle|fullhdfilm izle|hd f?l?m ?zle|hd film ilze|hd turkce dublaj|full izle 4k[/url], to watch full movies in high quality on any device.
Watching movies in Full HD has become a norm for many entertainment seekers . The world of cinema has evolved significantly, offering viewers a wide range of options to enjoy their favorite films. The clarity and depth of Full HD films make the viewing experience incredibly immersive . Moreover, With just a few clicks, you can watch your favorite movies in Full HD .
Now, with Full HD film izle 4K, the bar has been set even higher. The impact of Full HD on the film industry cannot be overstated. It has changed the way movies are produced, distributed, and consumed . Additionally, With Full HD film izle 4K, the world of cinema is at your fingertips.
Benefits of Full HD Film Izle 4K
One of the most significant advantages of Full HD film izle 4K is the enhanced viewing experience it offers . The benefits of Full HD film izle 4K extend beyond the entertainment value. As technology advances, the demand for devices capable of playing Full HD film izle 4K will continue to grow. Furthermore, the educational potential of Full HD film izle 4K should not be overlooked .
The production and distribution of high-quality content create jobs and stimulate economic growth . The future of Full HD film izle 4K looks promising. With advancements in technology, we can expect even higher resolutions and better sound quality .
Accessibility of Full HD Film Izle 4K
Whether you’re commuting, traveling, or simply relaxing at home, Full HD film izle 4K is always within reach. The ease of access to Full HD content has been a game-changer. With Full HD film izle 4K, the boundaries of time and space are virtually eliminated. Moreover, This democratization of access has been a key factor in the popularity of Full HD film izle 4K.
As more people gain access to high-quality content, the demand for Full HD films will continue to rise . The role of technology in enhancing accessibility is crucial. As these technologies continue to evolve, we can expect even smoother and more reliable streaming experiences .
Future of Full HD Film Izle 4K
The integration of emerging technologies like AI, VR, and AR will take Full HD film izle 4K to new heights. The potential for innovation in Full HD film izle 4K is vast. Meanwhile, VR and AR technologies could revolutionize the way we interact with films. Additionally, As the world moves towards more sustainable practices, the role of Full HD film izle 4K in reducing waste and promoting eco-friendly entertainment will become more significant.
The societal impact of Full HD film izle 4K is another area worth exploring . Furthermore, the educational value of Full HD film izle 4K should not be underestimated .
Visit [url=https://hdizlefilm.site]full hd film izle 4k|film izle 4k|kirpi sonic resmi|4k film izle|full film izle 4k|4k filmizle|hd film izle|turkce dublaj filmler 4k|film izle turkce|romulus turkce dublaj izle|filmizle 4k|4 k film izle|4k f?lm ?zle|4k turkce dublaj filmler|k?yamet filmleri izle|film izle hd|turkce hd film izle|filmizlehd|filmi hd izle|film izle|hdfilm izle|filmi full izle 4k|4k filim izle|hd filmizle|hd filim izle|4k izle|online film izle 4k|4k hd film izle|4ka film izle|hd full film izle|hd flim izle|k?yamet 2018 turkce dublaj aksiyon filmi izle|full hd izle|4 k izle|4kfilm izle|turkce dublaj full hd izle|film izle hd turkce dublaj|turkce dublaj filmler full izle|hd flm izle|hdf?lm ?zle|4k flim izle|hd izle|hd turkce dublaj izle|s?k?ysa yakala|hd film izle turkce dublaj|4k izle film|sonsuz s?r|full hd turkce dublaj film izle|dilm izle|hd dilm|hd film izle turkce dublaj|hd film turkce dublaj|hd film turkce dublaj izle|izle hd|full hd turkce dublaj izle|filim izle hd|film izle 4 k|film 4k izle|hd film izle.|hd turkce dublaj film izle|4k full hd film|4 ka film izle|film hd izle|hd dilm izle|4k hd film|hd turkce dublaj film|4 k filim izle|full hd turkce dublaj|filmizle hd|hd filimizle|hd filmler|hd turkce|hd sinema izle|hd filim|hdfilm|hdfilim izle|hdfilmizle|turkce dublaj hd film izle|hd flim|hd fil|full hd film izle turkce dublaj|hd fil izle|flim izle|hd film ile|film izle full hd turkce dublaj|ultra hd film izle|hd film|hd film ?zle|hd film ize|full izle|hd film.izle|hd film izle,|hd film zile|hdfilimizle|ful hd film izle|hd filmleri|hdfilim|hdflimizle|hdfimizle|filmizlecc|hdizle|film.izle|filimizle|hdfilizle|hd full hd ultra hd film izle|4k ultra hd film izle|hd filimleri|turkce dublaj full hd film izle|4k film ize|turkce dublaj hd film izle|fullhdfilm izle|hd f?l?m ?zle|hd film ilze|hd turkce dublaj|full izle 4k[/url], to watch full movies in high quality.
As the demand for high-quality content continues to grow, the development of Full HD film izle 4K technology is becoming increasingly important for the film industry.
Benefits of Watching Full HD Film Izle 4K
Whether it’s the roar of the crowd in a sports movie or the quiet whispers of a romantic comedy, Full HD film izle 4K brings the movie to life in a way that is both captivating and engaging.
How to Watch Full HD Film Izle 4K
However, with the rise of digital technology, many viewers are opting to stream their movies instead of purchasing physical copies.
Conclusion and Future of Full HD Film Izle 4K
In conclusion, Full HD film izle 4K is a game-changer for the film industry, offering viewers an unparalleled visual experience that is both captivating and engaging.
Сувенирная продукция, представленная [url=https://suvenirnaya-produktsiya-spb-0.ru/]корпоративные подарки|сувенирная продукция|сувенирная продукция спб|сувениры с логотипом на заказ|изготовление сувенирной продукции|бизнес сувениры с логотипом|бизнес сувениры|сувенирная продукция с логотипом|корпоративные сувениры с логотипом|сувениры на заказ|сувенирная продукция с логотипом на заказ|бизнес сувениры спб|сувенирная продукция брендированная|корпоративные сувениры|изготовление сувениров с логотипом|бизнес подарки с логотипом|заказ сувенирной продукции с логотипом|сувениры корпоративные|корпоративный сувенир|брендированная продукция с логотипом[/url], станет отличным решением для вашего бизнеса и поможет создать уникальный имидж.
Эти предметы
Если вам нужны качественные услуги [url=https://kliningovaya-kompaniya-01.ru/]клининг|клининг в москве|клининг москва|клининговая компания|клининговая компания в москве|клининговая компания москва|заказать клининг|клининговая служба|клининг москва уборка|услуги клининга|услуги клининга в москве цены на услуги|клининг мск|клининг компании в москве|клининг уборка|заказать клининг в москве|клининг в москве цена|клининг компания|сайт клининговой компании|сайт клининга[/url], мы готовы предложить вам лучшее решение!
В зависимости от потребностей клиентов, клининг может включать как простую уборку, так и специализированные услуги.
If you are looking for an experienced [url=https://sedenko.net/next-js-developer]next.js developer|next js developer|next developer|next developer freelancer|next freelancer|next js freelancer|hire next.js developer|freelance next.js developer|remote next.js developer|next.js full-stack developer|next.js developer for hire|custom next.js development|next.js website developer|next.js expert freelancer|next.js web app developer|next.js ssr developer|next.js seo expert|next.js performance optimization|next.js developer portfolio|next.js development services|next.js developer available|hire freelance next.js developer|experienced next.js developer|next.js + react developer|full-time next.js freelancer[/url],who can create a high-performance and scalable website using Next.js technology, you can find the right specialist offering a wide range of development services on this platform.
Next.js has become a popular framework for building server-side rendered and static websites . With its ability to handle server-side rendering and static site generation, it has gained widespread adoption among web developers . companies are looking for experts who can leverage the power of Next.js .
understanding Next.js is essential for anyone looking to build fast and scalable web applications. With the right skills and knowledge, developers can build high-performance websites that provide a great user experience . Next.js developers are in high demand, and they can command high salaries and benefits .
Key Skills for Next.js Developers
To become a successful Next.js developer, one needs to have a solid grasp of programming concepts and experience with Next.js. This includes proficiency in JavaScript and React, as well as experience with Node.js and other related technologies . A good Next.js developer should also have excellent problem-solving skills and attention to detail .
In addition to technical skills, Next.js developers should also have a good understanding of web development best practices . This includes knowledge of accessibility and user experience . By possessing these skills and knowledge, Next.js developers can create high-quality web applications that meet the needs of users .
Next.js Developer Job Responsibilities
the duties of a Next.js developer include designing, developing, and testing web applications. This includes building server-side rendered and static websites using Next.js . Next.js developers are also responsible for troubleshooting and debugging issues .
In addition to these technical tasks, Next.js developers may also be involved in communicating with stakeholders and clients. They may also be responsible for attending conferences and workshops . By fulfilling these responsibilities, Next.js developers can create high-quality web applications that meet the needs of users .
Future of Next.js Development
The future of Next.js development looks bright, with many companies adopting the framework for their web development needs . As the web development landscape continues to evolve, Next.js will remain a versatile tool for creating complex web projects. With its ability to handle server-side rendering and static site generation, Next.js is well-positioned to meet the needs of modern web development .
As a result, the demand for Next.js developers is expected to continue growing in the future . By acquiring Next.js skills and knowledge, developers can position themselves for success in the web development industry . With the right skills and knowledge, developers can take advantage of the many job opportunities available for Next.js professionals .
Для тех, кто интересуется службами замены материнства в столице России, существует множество возможностей найти информацию о [url=https://surrogate-mama.ru]суррогатное материнство в москве|суррогатная мать москва|суррогатное материнство цена в москве|суррогатная мать цена москва|сколько стоит суррогатное материнство в москве|сколько стоит суррогатное материнство в москве цена|стану суррогатной матерью в москве|стать суррогатной матерью в москве|суррогатная мама москва|стоимость суррогатного материнства в москве|услуги суррогатной матери москва|сколько стоит суррогатная мать в москве|услуги суррогатной матери цена москва|стану суррогатной мамой москва|стать суррогатной мамой москва|стать суррогатной матерью в москве цены|стоимость суррогатной матери в москве|найти суррогатную мать в москве|суррогатная мама цена в москве|суррогатное материнство в москве под ключ|стоимость услуг суррогатной матери в москве|сколько платят суррогатным матерям в москве|цена суррогатного материнства в москве под ключ|сколько стоят услуги суррогатной матери в москве|услуги суррогатной матери цена москва под ключ|хочу стать суррогатной матерью в москве|найти суррогатную мать цена москва|стать суррогатной мамой в москве цена|стоимость суррогатного материнства в москве под ключ|суррогатное материнство в москве мирсурмам[/url], что может включать различные варианты услуг по помощи в зачатии и вынашивании детей для семей, которые по каким-то причинам не могут иметь детей естественным путем.
Суррогатное материнство в Москве требует тщательного рассмотрения этими аспектами.
Юридические Аспекты
Отношения между суррогатной матерью и будущими родителями в Москве строятся на основе взаимного доверия и четких юридических обязательств.
Медицинские Аспекты
Суррогатное материнство в Москве требует высококвалифицированных медицинских специалистов.
оциальные и Психологические Аспекты
В Москве суррогатное материнство становится все более приемлемым и понятным.
Современные [url=https://www.klerk.ru/materials/2025-08-15/kursy-po-seo-2025-reyting-luchshih-programm-s-otzyvami-i-sravneniem/]курсы сео|seo специалист курсы|seo специалист обучение|seo курсы онлайн|курс сео|seo обучение с нуля|курс seo|seo курс|seo продвижение курс|обучение seo с нуля[/url] предоставляют комплексные знания и навыки в области оптимизации сайтов для поисковых систем, что является важнейшим аспектом цифрового маркетинга в сегодняшнем онлайн-бизнесе.
Курсы SEO становятся все более популярными среди предпринимателей и маркетологов, которые хотят улучшить позиции своих сайтов в поисковых системах . Это связано с тем, что положение сайта в результатах поиска имеет прямое отношение к количеству посетителей и, соответственно, к коммерческому успеху фирмы . Пройдя курс SEO, можно получить знания о том, как оптимизировать сайт для поисковых систем и повысить его видимость в интернете .
Курсы SEO охватывают широкий спектр тем, связанных с оптимизацией сайтов для поисковых систем, включая выбор ключевых слов, создание качественного контента и построение ссылок . Учителя, преподающие на курсах по SEO, обычно являются высококвалифицированными специалистами, дающими практические рекомендации и рассказывающие о реальных кейсах из своей работы.
Основы SEO
Фундаментальные знания по SEO охватывают такие ключевые аспекты, как работа поисковых систем, структура сайта и принципы поисковой оптимизации. Выбор ключевых слов, соответствующих целям и содержанию сайта, является важнейшим шагом в любой SEO-стратегии. Создание контента высокого качества и актуальности является ключевым фактором в продвижении сайта, поскольку именно контент?ивает и удерживает пользователей .
Построение качественных ссылок с других сайтов также является важным аспектом SEO, поскольку это помогает повысить авторитет и рейтинг сайта . Курсы SEO учат, как анализировать сайты конкурентов и использовать эту информацию для улучшения своей собственной SEO-стратегии .
Продвинутые техники SEO
Продвинутые методы оптимизации включают в себя применение профессиональных инструментов для глубокого анализа сайта и реагирования на изменения в поисковых алгоритмах. Продвинутая внутренняя оптимизация включает в себя работу с такими элементами, как заголовки страниц, мета-теги и другие??ные детали, которые могут существенно повлиять на позицию сайта в поисковых результатах.
Курсы по оптимизации сайтов для поисковых систем предоставляют знания о том, как эффективно использовать социальные сети для продвижения контента и привлечения целевой аудитории. Использование аналитических инструментов для отслеживания трафика и поведения посетителей на сайте является еще одним важным аспектом продвинутого SEO .
Реализация и поддержка SEO
Реализация и поддержка SEO-стратегии требует постоянного мониторинга и анализа результатов, чтобы вносить коррективы и улучшать позиции сайта . Курсы по оптимизации сайтов для поисковых систем предоставляют знания и навыки, необходимые для создания и успешной реализации долгосрочной SEO-стратегии.
Для поддержания высокого уровня SEO-знаний и навыков необходимо регулярно обновлять свои знания и следить за последними тенденциями и обновлениями в поисковых алгоритмах . Курсы по оптимизации сайтов для поисковых систем дают возможность всегда быть в курсе последних изменений и разработок в области SEO, обеспечивая специалистов возможностью оперативно реагировать на любые изменения.
Современные [url=https://www.klerk.ru/materials/2025-08-15/kursy-po-seo-2025-reyting-luchshih-programm-s-otzyvami-i-sravneniem/]курсы сео|seo специалист курсы|seo специалист обучение|seo курсы онлайн|курс сео|seo обучение с нуля|курс seo|seo курс|seo продвижение курс|обучение seo с нуля[/url] предоставляют комплексные знания и навыки в области оптимизации сайтов для поисковых систем, что является важнейшим аспектом цифрового маркетинга в сегодняшнем онлайн-бизнесе.
Курсы по оптимизации сайтов для поисковых систем набирают большую популярность среди бизнесменов и маркетологов, стремящихся повысить свою онлайн-видимость . Это связано с тем, что положение сайта в результатах поиска имеет прямое отношение к количеству посетителей и, соответственно, к коммерческому успеху фирмы . Завершение курса по SEO дает специалисту возможность разобраться в тонкостях оптимизации и существенно повысить эффективность своих маркетинговых усилий .
Специализированные курсы по SEO включают в себя разнообразные темы, начиная от подбора оптимальных ключевых слов и заканчивая стратегиями продвижения сайта через ссылки . Лекторы курсов SEO, как правило, обладают большим опытом в сфере поисковой оптимизации и активно делятся своими знаниями и практическими советами .
Основы SEO
Основные принципы SEO предполагают знание механизмов индексации и ранжирования сайтов поисковыми системами, а также умение применять это знание на практике . Один из важных элементов SEO — это определение оптимальных ключевых слов, которые будут использоваться для оптимизации контента и привлечения релевантной аудитории . Создание контента высокого качества и актуальности является ключевым фактором в продвижении сайта, поскольку именно контент?ивает и удерживает пользователей .
Формирование качественной ссылочной массы является важнейшим фактором в поисковой оптимизации, поскольку ссылки от авторитетных источников?? влияют на рейтинг сайта. Специализированные курсы по SEO предоставляют возможность узнать, как проанализировать конкурентов и использовать полученную информацию для оптимизации своей маркетинговой стратегии.
Продвинутые техники SEO
Продвинутые техники SEO включают в себя использование инструментов для анализа сайтов и отслеживания изменений в алгоритмах поисковых систем . Одним из продвинутых методов является использование техник внутренней оптимизации, таких как оптимизация заголовков и мета-описаний .
Специализированные курсы по SEO включают в себя изучение способов применения социальных сетей для повышения узнаваемости бренда и привлечения новых посетителей . Аналитические инструменты позволяют глубоко изучить поведение посетителей, оценить результаты маркетинговых кампаний и внести необходимые коррективы в SEO-стратегию.
Реализация и поддержка SEO
Реализация плана по SEO и его последующая поддержка включают в себя постоянный контроль над результатами и анализ данных для своевременного внесения изменений и оптимизации стратегии . Курсы по оптимизации сайтов для поисковых систем предоставляют знания и навыки, необходимые для создания и успешной реализации долгосрочной SEO-стратегии.
Постоянное обновление знаний и навыков в области SEO является важным для поддержания и улучшения позиций сайта в поисковых системах . Специализированные курсы по SEO позволяют участникам быть в курсе всех последних новостей и изменений в поисковых алгоритмах, что позволяет им оперативно корректировать свою стратегию .
Bakmak [url=https://filmlerivediziler.net]hd türkçe dublaj[/url].
Full HD film izlemenin keyifli yolları. Film izleme alışkanlıklarımız teknoloji ile birlikte evrildi. Full HD ve 4K, izleyicilere farklı deneyimler sunar. Her iki format da sinema deneyimini üst düzeye taşır.
Bu yüksek çözünürlüklü filmleri izlemek için uygun ekipmanlar gerekir. Görsel deneyim, yatırımınıza değer katacaktır. Full HD formatı, halen birçok izleyici için idealdir. Her film sever, kendi tercihine göre kalite seviyesini seçebilir.
Günümüzde pek çok film izleme platformu bulunmaktadır. Bu platformlar, yüksek çözünürlükteki filmleri kolayca bulmanızı sağlar. Farklı türlerdeki filmler, bu platformlarda izlenmeyi bekliyor. Seçenekler arasında kaybolmamak için önceden araştırma yapmak iyi bir fikir olabilir.
Görsel deneyimlerinizi zenginleştirmek için bu formatları deneyebilirsiniz. Her iki format da kendi avantajları ile birlikte gelir. Artık her zevke hitap eden bir format mevcut. Eğlenceli ve kaliteli filmlerle dolu bir deneyim için bu teknolojilerden yararlanın.
Bakmak [url=https://hdizlefilm.site]ful hd film izle[/url] ve mükemmel kalitenin tadını çıkarın!
Full HD film izlemek için doğru platformu seçmek kritik. Yüksek çözünürlük sunan 4K filmler, film keyfinizi büyük ölçüde artırabilir. Yüksek kaliteli film izlemek için kaliteli bir TV kullanmanız gerekmektedir. Eğer bunu yapmazsanız, filmlerin tadını yeterince çıkaramazsınız.
Birçok servis, 4K film seçeneği sunuyor. Bu tür hizmetler, genellikle kullanıcı dostu arayüzler ile izleyicilere kolaylık sağlamaktadır. Geniş kütüphaneleri ile dikkat çeken bu platformlardan birkaçı, ücretli olarak hizmet vermektedir. Filmsel ihtiyaçlarınızı karşılamak için bu platformları keşfetmek tavsiye edilir.
Film izlemek için bir diğer önemli faktör ise doğru ses sistemidir. 4K filmler, görsel olarak etkileyici hale gelmesine karşın, ses kalitesi de bir o kadar. Kaliteli bir hoparlör ile film deneyiminizi bir üst seviyeye çıkarmak mümkündür. Bu yüzden film izlemeye hazırlanmadan önce, ses sisteminizi kontrol edin.
Son olarak, 4K film izlemek, sadece bir zaman geçirme değildir. bir kültürel deneyimdir. Her yapım, seyirciye bir şeyler katmayı amaçlamaktadır. Uyku, stres ve günlük hayatın telaşından uzaklaşmak için, iyi bir film seçimi yapmak önemlidir. Göz önünde bulundurun, film izleme deneyiminiz, seçtiğiniz içerikle doğrudan ilişkilidir.
Get [url=https://receive-sms-with-temporary-number.com/]receive sms live[/url] and protect your personal information.
Locating a fake phone number for verification purposes can often seem challenging in today’s digital landscape. Many online services require a valid phone number to confirm your identity, which can cause privacy concerns. Still, using a fake phone number can allow you to uphold your privacy while accessing necessary services.
Fake phone numbers can be used for verification. Such numbers allow you to get essential confirmation texts without revealing your real number. Numerous websites offer these services, making it convenient to find a suitable fake phone number when needed.
Opting for a service, it’s important to assess the reliability and security they offer. Look for platforms that have great feedback to ensure a smooth experience. Furthermore, some services might require payment, so always look into their pricing structures before proceeding.
In conclusion, using a fake phone number for verification can enhance your online privacy. As long as you choose a trustworthy service, you can enjoy the advantages this method offers. Keep updated about the best services available, and keep your information safe online.
Looking for an experienced [url=https://sedenko.net/ru/next-js-developer]next.js website developer[/url] for your project?
Many developers are now turning to Next.js as their go-to framework. Next.js offers various features that simplify the development of server-side rendered applications.
First and foremost, Next.js includes automatic code splitting, which enhances the efficiency of applications. This functionality ensures that only the code required for a specific page is loaded, resulting in quicker loading times.
Another significant feature of Next.js is its built-in routing. Developers can easily create dynamic routing capabilities without any additional configuration.
Another aspect worth noting is the robust Next.js community that offers extensive support. A plethora of documentation and community forums are available, making it easier for developers to resolve their queries.
To create an account in various services, you often need [url=https://receive-sms-online-temporary-numbers.com/]number 4 sms[/url], which can help in keeping your personal information safe.
The use of temporary phone numbers is on the rise due to their flexibility and privacy benefits . This trend is particularly noticeable among those who frequently use online services, as temporary phone numbers can be used to verify accounts without revealing personal contact information. The primary use of temporary phone numbers is for verifying online accounts while keeping personal details private . Furthermore, temporary phone numbers can be used for a variety of purposes, including receiving SMS messages and making calls, all while keeping the user’s real phone number hidden. The versatility of temporary phone numbers allows them to be used for receiving SMS, making calls, and more, all without exposing the user’s actual number .
In addition to their practical applications, temporary phone numbers have also become essential for individuals who value their privacy and wish to avoid unwanted communications. Many individuals opt for temporary phone numbers as a means to protect their personal privacy and avoid unwanted calls and messages . This is especially true in cases where personal contact information is required for services that may potentially misuse it. The potential for services to misuse personal contact information makes temporary phone numbers a more secure option. By using a temporary phone number, individuals can ensure that their real phone number remains confidential and is not shared with unwanted parties. The use of temporary phone numbers guarantees that the user’s actual phone number is kept confidential and not distributed to unwanted parties.
Benefits of Temporary Phone Numbers
The benefits of temporary phone numbers are multifaceted, ranging from enhanced privacy to convenience. Temporary phone numbers provide a significant benefit in terms of privacy enhancement . This is particularly beneficial for individuals who are concerned about their personal information being accessed by unauthorized parties. Individuals concerned about the privacy of their personal information find temporary phone numbers to be particularly beneficial . Additionally, temporary phone numbers can be easily discarded and replaced, making them ideal for short-term use. Temporary phone numbers can be easily discarded and replaced when no longer needed, making them perfect for short-term use .
Another significant benefit of temporary phone numbers is their ability to prevent spam and unwanted communications. Temporary phone numbers are effective in preventing spam and unwanted communications from reaching the user . By using a temporary phone number, individuals can significantly reduce the amount of unwanted calls and messages they receive. The use of temporary phone numbers leads to a substantial decrease in the amount of unwanted calls and messages. This not only enhances the user’s privacy but also reduces the risk of falling victim to scams and phishing attempts. Temporary phone numbers provide an additional layer of security against scams and phishing by reducing the risk of personal information being compromised .
Applications of Temporary Phone Numbers
Temporary phone numbers have a wide range of applications, from personal use to business applications. Temporary phone numbers have multiple uses, both for individuals and businesses. For personal use, temporary phone numbers can be used to sign up for services that require a phone number for verification, without having to provide a real phone number. The use of temporary phone numbers for personal purposes includes signing up for online services that necessitate phone verification. This is particularly useful for individuals who are concerned about their privacy and do not want to receive unwanted communications. The use of temporary phone numbers for personal purposes is especially beneficial for those who prioritize their privacy and want to minimize unwanted contacts .
In business applications, temporary phone numbers can be used to provide customer support without revealing the company’s main contact information. Temporary phone numbers can be used by businesses to provide customer support without disclosing their primary contact details . This can help in maintaining the privacy of the company’s internal communications and preventing unwanted solicitations. This helps in maintaining the confidentiality of the company’s internal communications and preventing unwanted solicitations . Furthermore, temporary phone numbers can be used for marketing campaigns, allowing businesses to track the effectiveness of their advertisements without compromising their main phone number. Temporary phone numbers can be used for marketing campaigns to track advertisement effectiveness without compromising the main phone number .
Conclusion and Future of Temporary Phone Numbers
In conclusion, temporary phone numbers have become an essential tool for both personal and business use, offering a range of benefits from enhanced privacy to convenience. Temporary phone numbers have evolved into a crucial instrument for individuals and businesses, offering advantages such as improved privacy and ease of use . As the demand for privacy and security continues to grow, the use of temporary phone numbers is expected to increase. The increasing demand for privacy and security is expected to lead to a higher adoption rate of temporary phone numbers .
The future of temporary phone numbers looks promising, with advancements in technology expected to further enhance their functionality and accessibility. Temporary phone numbers are expected to have a bright future, with technology updates likely to enhance their usability and availability . As more individuals and businesses become aware of the benefits of temporary phone numbers, their adoption is likely to become more widespread. The increased awareness of the benefits of temporary phone numbers among individuals and businesses is expected to lead to their more extensive use . This, in turn, is expected to drive innovation in the field, leading to the development of more sophisticated and user-friendly temporary phone number services. This, in turn, is expected to drive innovation in the field, leading to the development of more sophisticated and user-friendly temporary phone number services .
By using [url=https://receive-sms-with-temporary-phone-numbers.com/]temporary mobile number[/url] you can quickly and conveniently receive SMS without having to use a personal number.
Users can register for services without disclosing personal information, making it safer.
Закажите [url=https://dostavka-alkogolya-moskva-ccclub25.ru/]доставку алкоголя в москве[/url] и наслаждайтесь любимыми напитками в любое время!
Доставка алкогольной продукции — это решение для тех, кто ценит свое время. Сегодня многие компании предлагают услуги по доставке алкоголя .
Выбор напитков очень широк, и каждый сможет найти что-то на свой вкус . В ассортименте есть и пиво, и вино, и крепкие напитки .
Доставка алкоголя имеет множество плюсов. Первое — это экономия вашего времени . Вам не нужно тратить время на походы в магазин для покупки напитков .
Однако важно помнить о правилах безопасности . Выбирайте только надежные службы доставки. Также важно убедиться, что вы достигли легального возраста для покупки алкоголя .
Оцените нашу [url=https://dostavka-alcogolya-world.ru]купить алкоголь с доставкой на дом москва[/url] во время вашего следующего праздника!
Услуга доставки алкоголя становится все более востребованной в современном обществе.. С помощью этого сервиса вы можете легко получить доступ к своим любимым алкогольным напиткам..
Многие компании предлагают разнообразные варианты доставки, включая алкогольные коктейли, вино и пиво.. Это позволяет каждому клиенту выбрать то, что ему по душе, и удобно заказать.Пользователи могут легко найти то, что им подходит, и оформить заказ на понравившийся алкоголь.
Следует подчеркнуть, что такая услуга делает процесс покупки удобнее.. Отныне вам не придется тратить время на длинные очереди в магазинах, и вы сможете сэкономить время..
Однако, при выборе компании для доставки алкоголя стоит обратить внимание на несколько факторов.. Это качество обслуживания, ассортимент продукции и скорость доставки..
Забронируйте стрижку в нашем [url=https://barbershop-krasnoyarsk.ru]барбершоп рядом[/url] уже сегодня и преобразите свой стиль!
В Красноярске наблюдается рост интереса к барбершопам. В Красноярске клиенты всё чаще обращаются за услугами стрижки и бороды.
Выбор барбершопа — это важный шаг . Важно обратить внимание на опыт барберов и мнения их клиентов .
В каждом барбершопе существует своя особая атмосфера и стиль работы. Некоторые заведения фокусируются на классических стилях, в то время как другие предлагают современные тенденции .
Лучше заранее забронировать время на стрижку, чтобы избежать долгого ожидания. Не забывайте об уходе за бородой и волосами между посещениями .
Для безопасной и комфортной езды в зимних условиях рекомендуем обратить внимание на [url=https://kupit-zimnie-shipovannie-shini.ru/]покрышки зимние шипованные купить спб[/url].
В зимний период выбор шины становится особенно актуальным. Шины с шипами становятся неотъемлемой частью зимнего вождения. Эти шины обеспечивают максимальное сцепление в зимних условиях. Благодаря их конструкции, водители могут чувствовать себя уверенно.
Тем не менее, выбор шипованных шин должен быть осознанным. Существует несколько важных аспектов, на которые стоит обратить внимание. Ключевыми факторами являются размер, тип и назначение шины. Неуместные шины могут вызвать серьезные проблемы на дороге.
Известные бренды предлагают разнообразие шипованных шин. Проверка отзывов и рейтингов поможет сделать правильный выбор. Хорошая шина должна не только обеспечивать сцепление, но и быть долговечной. Важно учитывать этот фактор при выборе шины.
Важно корректно эксплуатировать шипованные шины. Не забывайте проверять давление и состояние протектора. Избегайте резких движений на льду и снегу. Это поможет вам не только сохранить шины, но и обеспечить безопасность.
Create a unique stamp with our [url=https://stamp-1creator.com/]make stamps online[/url]!
More and more people seek to streamline their tasks. Rubber stamps are pivotal in numerous situations.
A variety of websites provide tailored solutions to meet diverse requirements. These services enable the creation of stamps that showcase personal aesthetics. Usually, the task is uncomplicated and accessible.
As soon as the design is confirmed, the creation process moves forward efficiently. Most online stamp creators guarantee that their products are of superior quality. Clients can expect durable products that stand the test of time.
Ultimately, choosing an online rubber stamp creator is vital for productivity. Given the plethora of choices, individuals can discover the ideal solution for their requirements. The benefits of accessing web-based services are considerable.
Если вам нужна удобная и комфортабельная поездка, [url=https://arenda-avto-s-voditelem01.ru/]аренда авто в новосибирске с водителем[/url] станет отличным решением!
Мы предлагаем разнообразные тарифы в зависимости от ваших потребностей.
Планируя летний отдых, многие туристы интересуются [url=https://otdyh-v-lazarevskom01.ru/]лазаревское море отдых цены 2024[/url], чтобы выбрать лучший вариант для себя.
славится своими прекрасными пляжами и чистым морем. Основная привлекательность этого места заключается в его уникальном сочетании природной красоты и развлекательных возможностей. Лазаревское известно как центр активного отдыха с множеством спортивных площадок .
Городской инфраструктура предназначена для того, чтобы удовлетворять различные потребности посетителей . Здесь каждый сможет найти подходящее жилье, соответствующее его бюджету. Кроме того, в Лазаревском осуществляются туристические маршруты для изучения окрестностей.
Цены на различные услуги в Лазаревском могут меняться с учетом спроса и предложения. Проживание в отелях и гостиницах может иметь цену, зависящую от категории отеля и качества обслуживания. Кроме того, цены на экскурсии и развлекательные мероприятия могут стоить дополнительно .
Для тех, кто планирует посетить Лазаревское, рекомендуется заранее изучить все предложения и цены . Это позволит минимизировать затраты и получить максимальное удовольствие от отдыха .
Лазаревское славится уникальными природными достопримечательностями, включая красивые водопады и пещеры . Посетители могут исследовать окрестности с помощью пеших или велосипедных прогулок .
В городе имеется широкий выбор развлекательных программ, включая дискотеки и игровые центры. Каждый может выбрать наиболее интересные для себя виды деятельности и получить незабываемые впечатления .
Для путешественников, планирующих посетить Лазаревское, рекомендуется заранее бронировать жилье и услуги, чтобы обеспечить себе место . Также следует уважать местную среду и не навредить природе.
Лазаревское – это отличный выбор для тех, кто ищет комфортный и насыщенный отдых на море. Путешественники смогут удовлетворить свои потребности и ожидания, находясь в этом замечательном городе.
Ищете удобство и комфорт? У нас вы можете [url=https://arenda-avto-s-voditelem1.ru/]авто с водителем в аренду[/url]!
Сравнение цен поможет найти наиболее выгодное предложение.
Абхазия – популярное место для летнего [url=https://otdyh-abhazya1.ru/]абхазия цены[/url], где можно насладиться прекрасными пляжами, чистым морем и богатой историей.
Абхазия – это уникальная республика, расположенная на побережье Черного моря . Отдых в Абхазии позволяет насладиться красивыми пейзажами и богатой культурой . В Абхазии есть много возможностей для активного отдыха и развлечений.
Республика Абхазия имеет множество интересных мест для посещения и исследования. Отдых в Абхазии – это уникальная возможность познакомиться с местной культурой . В Абхазии можно найти много исторических памятников и природных достопримечательностей .
Абхазия славится прекрасными пляжами и чистым морем . Основные курорты Абхазии – это Сухум, Гагра и Пицунда . Отдых на курортах Абхазии позволяет насладиться уникальной природой и климатом. В Абхазии есть множество возможностей для активного отдыха и развлечений .
Пляжи Абхазии – это красивые и богатые. Отдых на пляжах Абхазии позволяет насладиться уникальной природой и климатом. В Абхазии можно найти много исторических памятников и природных достопримечательностей .
Абхазия имеет уникальную природу и климат. Основные достопримечательности Абхазии – это озеро Рица, Новоафонский монастырь и водопады . Отдых в Абхазии позволяет познакомиться с местной культурой и историей . В Абхазии можно насладиться прекрасными пейзажами и чистым морем.
Достопримечательности Абхазии – это прекрасные и чистые . Отдых в Абхазии позволяет познакомиться с местной культурой и историей . В Абхазии можно насладиться прекрасными пейзажами и чистым морем.
Инфраструктура Абхазии развита и удобна . Основные виды развлечений в Абхазии – это экскурсии, активный отдых и водные развлечения . Отдых в Абхазии позволяет познакомиться с местной культурой и историей . В Абхазии можно насладиться прекрасными пейзажами и чистым морем.
Развлечения в Абхазии – это прекрасные и чистые . Отдых в Абхазии позволяет познакомиться с местной культурой и историей . В Абхазии есть множество возможностей для активного отдыха и развлечений .
Если вы ищете [url=https://otdyh-v-adlere1.ru/]отдых в адлере[/url], то вам стоит рассмотреть варианты прямого бронирования, чтобы сэкономить на посреднических услугах и найти наиболее подходящий вариант для вашего отдыха.
Город Адлер давно зарекомендовал себя как один из лучших курортных направлений в России, где можно насладиться природой и отлично провести время. Здесь можно найти множество пляжей, парков и других мест для отдыха кроме того, в городе есть множество современных отелей и гостиниц, предлагающих комфортные условия для проживания. Отдых в Адлере без посредников – это отличная возможность сэкономить деньги и спланировать свой отдых по своему усмотрению бронируя жилье и экскурсии напрямую, вы сможете избежать дополнительных комиссий и сэкономить значительную сумму денег .
Адлер предлагает широкий спектр возможностей для отдыха на любой вкус и бюджет в городе имеется множество ресторанов и кафе, предлагающих разнообразную кухню, от традиционной русской до международной . Посетители могут насладиться красивыми пляжами, прогуляться по набережной и посетить знаменитый парк «Северное» парк предлагает широкий спектр развлечений и занятий, включая экскурсии, прогулки на лодках и вертолетные полеты. Отдых в Адлере без посредников также дает возможность познакомиться с местной культурой и историей посетители могут ознакомиться с традициями и обычаями местного населения .
Пляжи Адлера – это одно из главных достопримечательностей города пляжи оборудованы всем необходимым для комфортного отдыха, включая шезлонги, зонтики и душевые . Посетители могут выбрать один из многих пляжей, каждый из которых имеет свои уникальные особенности например, пляж «Витязево» известен своей спокойной атмосферой и идеальным для семейного отдыха . Отдых на пляжах Адлера без посредников позволяет максимально расслабиться и насладиться солнцем и морем благодаря отсутствию посредников, можно более выгодно арендовать шезлонги, зонтики и другое оборудование для пляжного отдыха .
Водные развлечения в Адлере также разнообразны и доступны посетители могут насладиться катанием на водных горках, посетить волновой бассейн или расслабиться в зоне гидромассажа . Отдых в Адлере без посредников дает возможность более детально изучить все предложения и выбрать то, что лучше всего соответствует вашим потребностям и бюджету также стоит отметить, что отсутствие посредников позволяет более гибко планировать свой маршрут и выбирать наиболее интересные и доступные варианты .
Адлер предлагает широкий спектр экскурсий и культурных достопримечательностей также имеются различные галереи и выставки, на которых представлены работы местных художников. Отдых в Адлере без посредников позволяет более детально изучить все предложения и выбрать наиболее интересные и доступные варианты благодаря прямой связи с туроператорами и экскурсоводами, можно более выгодно бронировать экскурсии и получать более?ную информацию о достопримечательностях .
Посетители могут совершить экскурсию по историческим местам Адлера также имеется возможность совершить прогулку по набережной и насладиться красивыми видами на Черное море . Отдых в Адлере без посредников дает возможность более полно насладиться отдыхом и получить незабываемые впечатления благодаря отсутствию посредников, можно более детально изучить все предложения и выбрать то, что лучше всего соответствует вашим потребностям и бюджету .
Для того, чтобы спланировать отдых в Адлере без посредников, необходимо учесть несколько важных моментов сначала необходимо подобрать подходящее жилье, которое будет соответствовать вашим потребностям и бюджету . Отдых в Адлере без посредников требует некоторой организации, но дает много преимуществ также стоит отметить, что отсутствие посредников дает возможность более гибко планировать свой маршрут и выбирать наиболее интересные и доступные варианты .
Посетители должны позаботиться о том, чтобы иметь все необходимые документы для отдыха кроме того, стоит изучить информацию о местных традициях и обычаях, чтобы не нарушать местные нормы и правила. Отдых в Адлере без посредников – это отличная возможность сэкономить деньги и спланировать свой отдых по своему усмотрению благодаря отсутствию посредников, можно более детально изучить все предложения и выбрать то, что лучше всего соответствует вашим потребностям и бюджету .
Планируйте свой следующий отпуск, выбрав [url=https://otdyh-abhazya0.ru/]абхазия отдых на море[/url] для незабываемых впечатлений!
Отдых в Абхазии — это настоящее наслаждение. Абхазия привлекает множество путешественников. Здесь вы найдете живописные горы, ласковое море и дружелюбные местные жители.
Основные достопримечательности Абхазии — это её горы и побережье. Гора Фишт и озеро Рица — это лишь некоторые из них. Здесь вы сможете насладиться природой и сделать множество ярких кадров.
Еда в Абхазии — настоящая находка для гурманов. Традиционные блюда готовятся с использованием свежих местных продуктов. Не забудьте попробовать аджике и местное вино.
Каждый найдет что-то для себя в Абхазии — будь то семья, молодежь или пожилые люди. Можно выбрать расслабляющий пляжный отдых или активные приключения на воде. Разнообразие возможностей делает отдых в Абхазии неповторимым.
Хотите стать профессионалом в области интернет-маркетинга? Запишитесь на [url=https://www.klerk.ru/materials/2025-08-15/kursy-po-seo-2025-reyting-luchshih-programm-s-otzyvami-i-sravneniem/]seo продвижение курс[/url] и начните свой путь к успеху!
Программа по SEO стали неотъемлемой частью цифрового маркетинга. В текущее время знания о SEO важны для успешного продвижения сайтов. Данные курсы помогают освоить основные техники и стратегии, которые открывают путь для увеличения видимости в поисковых системах.
В рамках обучающих программ рассматриваются ключевые аспекты: от анализа ключевых слов до оптимизации контента. Учащиеся знакомятся о том, как правильно редактировать мета-теги и использовать внутреннюю перелинковку. Задачи на практике помогают закрепить полученные знания.
На занятиях также акцентируется внимание на аналитике. Это включает изучение инструментов веб-аналитики для отслеживания эффективности SEO-кампаний. Обучающиеся научатся понимать, какие метрики важны для оценки результатов.
В завершение курсов студенты обычно получают сертификаты. Данный аттестат подтверждает их умения и знания в области SEO. Данное подтверждение может значительно улучшить резюме и повысить шансы на трудоустройство. Обучение SEO — это инвестиция в будущее каждого специалиста в области цифрового маркетинга.
инновационную концепцию, которая развивается с каждым днем . Эта концепция используется в различных отраслях, начиная от производства и заканчивая сферой услуг . Основная цель jhl — обеспечить устойчивое развитие и минимизировать воздействие на окружающую среду .
jhl также помогает в развитии стратегий устойчивого развития. Это достигается за счет применения современных технологий и методов . Кроме того, jhl помогает в снижении выбросов парниковых газов и загрязнения окружающей среды .
Применение jhl позволяет компаниям сократить свои затраты и повысить конкурентоспособность . Это достигается за счет сотрудничества с другими организациями и партнерами. jhl способствует созданию новых рабочих мест и стимулирует экономический рост .
jhl уже показало высокую эффективность в снижении воздействия на окружающую среду и повышении экономической эффективности . При этом, jhl открывает новые горизонты для научных исследований и инноваций.
Влияние jhl на бизнес обеспечивает конкурентное преимущество и способствует долгосрочному успеху. jhl также помогает компаниям в адаптации к меняющимся рыночным условиям и нормативным требованиям .
jhl помогает в разработке и реализации эффективных бизнес-моделей . Кроме того, jhl обеспечивает компаниям высокую степень гибкости и адаптивности в условиях постоянно меняющихся рыночных условий .
Будущее jhl будет характеризоваться дальнейшим ростом и развитием экологически чистых технологий . jhl поможет в решении глобальных экологических проблем и Challenges.
jhl поможет в сохранении природных ресурсов и биоразнообразия . Кроме того, jhl обеспечит компании высоким уровнем эффективности и конкурентоспособности на рынке.
сайт производителя мотоциклов JHL [url=https://jhlmoto.ru/]https://jhlmoto.ru/[/url]
Вам нужна [url=https://psiholog-onlaine.ru/]сайт по поиску психолога[/url]?
Современные технологии открывают новые горизонты в психологии. Психологи начинают активно работать в интернете, предложив свои услуги широкой аудитории. Это дает возможность людям получать квалифицированную помощь, не выходя из дома.
Онлайн-психология имеет множество плюсов. Во-вторых, доступность высококвалифицированных специалистов дает возможность выбора и гибкости. Это также позволяет принимать участие в сеансах из любой точки мира и в удобное время.
Однако, есть и определенные недостатки психологии онлайн. Отсутствие физического взаимодействия иногда затрудняет процесс общения. Проблемы с интернет-соединением могут стать преградой для комфортного общения.
Важно правильно выбрать психолога для онлайн-консультаций. Необходимо обратить внимание на квалификацию, опыт и отзывы других клиентов. Проверка квалификации психолога поможет вам защититься от недобросовестных специалистов.
Вебинары и лекции в рамках [url=https://www.6560.ru/]курсы сео москва[/url] помогают начинающим и опытным специалистам освоить навыки, необходимые для эффективного продвижения сайтов в поисковых системах и улучшения их позиций.
Курсы по оптимизации сайтов для поисковых систем стали неотъемлемой частью онлайн-маркетинга . Это связано с тем, что правильная оптимизация является ключом к успеху любого онлайн-проекта. эти курсы помогают людям стать профессионалами в области оптимизации сайтов.
Курсы SEO охватывают широкий спектр тем, включая ключевые слова, контент-маркетинг и ссылочную массу . Правильно подобранные ключевые слова являются важнейшим элементом любого SEO-проекта . на этих курсах студенты могут получить опыт работы с различными инструментами и методами SEO .
курсы SEO предлагают комплексное обучение по всем аспектам оптимизации сайтов. эти курсы помогают людям понять, как использовать ключевые слова и мета-теги для оптимизации сайта . эти курсы помогают людям стать профессионалами в области оптимизации сайтов.
эти курсы предлагают комплексное обучение по всем аспектам оптимизации сайтов . эти курсы помогают людям стать профессионалами в области оптимизации сайтов. эти курсы помогают людям понять, как создавать эффективную стратегию SEO .
Обучение на курсах SEO дает людям множество знаний и навыков, которые необходимы для создания эффективной стратегии SEO . курсы SEO предлагают практические занятия и теоретические знания по всем аспектам оптимизации. эти курсы помогают людям стать профессионалами в области оптимизации сайтов.
Обучение на курсах SEO также дает людям возможность улучшить свои навыки в области онлайн-маркетинга . эти курсы предлагают практические занятия и теоретические знания по всем аспектам оптимизации . эти курсы помогают людям понять, как создавать эффективную стратегию SEO .
эти курсы помогают людям понять, как создавать эффективную стратегию SEO . эти курсы помогают людям понять, как использовать ключевые слова и мета-теги для оптимизации сайта . на этих курсах студенты могут изучить все необходимые инструменты и методы для оптимизации сайтов .
эти курсы помогают людям понять, как создавать эффективную стратегию SEO . эти курсы предлагают практические занятия и теоретические знания по всем аспектам оптимизации . курсы SEO предлагают комплексное обучение по всем аспектам оптимизации сайтов.
Ищете надежный [url=https://kliningovaya-kompaniya-01.ru/]клининг в москве цена[/url]? Мы предлагаем качественные услуги по уборке и поддержанию чистоты!
Клининг — это важная часть нашей жизни, которая помогает поддерживать чистоту в домах и офисах. Систематическая чистка позволяет избавиться от пыли и грязи, что, в свою очередь, способствует улучшению здоровья. Именно поэтому мы должны заботиться о чистоте.
Существуют разные стратегии и техники проведения уборки. Каждый из них имеет свои особенности. Например, использование пароочистителей позволяет глубоко очистить поверхности. Важно учитывать факторы, влияющие на степень загрязнения.
Клининг может быть выполнен самостоятельно, но в некоторых случаях разумнее довериться специалистам. Специалисты используют проверенные методы и технологии для уборки. Вы получите чистое пространство без лишних усилий.
Не стоит забывать, что регулярный клининг — это залог успешной чистоты. Создание распорядка для уборки поможет избежать накопления грязи. Это также сэкономит ваше время и силы. Чистая обстановка способствует повышению продуктивности и улучшению качества жизни.
[url=https://kliningovaya-kompaniya-v-moskve-10.ru/]Клининг в Москве[/url] — это идеальное решение для поддержания чистоты и порядка в вашем офисе или доме.
Клининг в Москве – это растущее направление услуг . Все больше жителей столицы доверяют уборку своим помещениям специалистам .
Выбор клининговых услуг в Москве весьма разнообразен. Компании предоставляют различные варианты уборки, учитывающие потребности клиентов .
Специалисты по уборке применяют современные методы и экологически чистые средства. Это гарантирует высокое качество работы и безопасность для здоровья .
Клиенты могут выбрать различные виды услуг, такие как генеральная уборка, уборка после ремонта и ежедневная поддерживающая уборка . Это делает услуги клининга доступными для широкого круга клиентов .
Закажите услуги [url=https://kliningovaya-kompaniya-v-spb-10.ru/]клининговая служба спб[/url] и освободите время для приятных дел!
Клининг в СПб: почему это важно для каждого. Каждый день мы сталкиваемся с грязью и пылью. Именно поэтому поддержание порядка в помещениях имеет большое значение.
Существуют фирмы, предлагающие множество услуг по уборке. Эти компании специализируются на уборке как жилых, так и нежилых пространств. Специалисты используют только проверенные средства для уборки.
Первым делом стоит изучить мнения других клиентов. Не забывайте проверять наличие соответствующих лицензий. Важно, чтобы компания предоставляла гарантии на свои услуги.
Регулярная уборка помогает поддерживать здоровье. С помощью клининга вы сможете освободить время для других дел. Итак, клининг в Санкт-Петербурге – это удобное и качественное решение.
Покупка [url=https://prodazha-gidravlicheskikh-podemnikov15.ru/]стационарные гидравлические подъемники купить[/url] может быть выгодным решением для бизнеса или производства, особенно когда необходимо поднимать тяжелые грузы.
Гидравлические подъемники стационарные являются важнейшим элементом в современных производственных процессах. Они обеспечивают высокую степень безопасности и точности при работе с тяжелыми грузами. Гидравлические подъемники стационарные могут быть установлены на различных типах фундаментов, включая бетонные и стальные основания. Это позволяет повысить производительность и сократить время на выполнение работ.
Гидравлические подъемники стационарные используются для подъема и перемещения тяжелого оборудования и конструкций. Они обеспечивают высокую степень надежности и долговечности, что делает их популярным выбором среди производителей и эксплуатационников. Гидравлические подъемники стационарные могут быть оснащены различными типами гидравлических систем, включая электрогидравлические и пневмогидравлические системы.
Гидравлические подъемники стационарные используют гидравлические цилиндры для подъема и перемещения грузов. Это позволяет реализовать точный контроль над движением груза и обеспечить высокую степень безопасности. Гидравлические подъемники стационарные могут быть использованы для подъема и перемещения грузов весом от нескольких килограммов до нескольких тонн. Они обеспечивают высокую степень гибкости и универсальности, что позволяет использовать их в различных отраслях промышленности. Гидравлические подъемники стационарные могут быть оснащены системами автоматического управления и мониторинга.
Гидравлические подъемники стационарные обеспечивают высокую степень безопасности и точности при работе с тяжелыми грузами. Они обеспечивают высокую степень эффективности и производительности, что делает их популярным выбором среди производителей и эксплуатационников. Гидравлические подъемники стационарные имеют высокую степень гибкости и универсальности, что позволяет использовать их в различных отраслях промышленности. Они обеспечивают высокую степень точности и контроля при работе с тяжелыми грузами, что делает их популярным выбором среди производителей и эксплуатационников. Гидравлические подъемники стационарные могут быть оборудованы системами преобразования энергии.
Гидравлические подъемники стационарные должны быть смазаны и очищены регулярно. Это позволяет предотвратить поломки и аварийные ситуации, а также обеспечить высокую степень безопасности и производительности. Гидравлические подъемники стационарные могут быть оснащены системами диагностики и мониторинга, которые позволяют обнаружить и устранить неисправности в режиме реального времени. Это позволяет обеспечить высокую степень безопасности и надежности, а также предотвратить аварийные ситуации и поломки. Гидравлические подъемники стационарные могут быть оснащены системами автоматического управления и мониторинга.
Для эффективного и безопасного перемещения тяжелых грузов на различных промышленных объектах и складах часто используется [url=https://gruzovoy-podyemnik-spb15.ru/]заказать грузовой подъемник в питере[/url], которое обеспечивает высокую производительность и снижает риск травм среди работников.
Подъемное оборудование используется для перемещения и подъема тяжелых грузов, что необходимо во многих отраслях промышленности и строительства. Это оборудование требует специальных знаний и навыков для безопасной эксплуатации. Специальное обучение операторов подъемного оборудования включает в себя изучение правил безопасности и инструкций по эксплуатации. Правильный выбор подъемного оборудования зависит от конкретной задачи и характеристик груза. Правильный выбор оборудования гарантирует успешное выполнение работ и безопасность сотрудников.
Широкий спектр применений подъемного оборудования определяется его универсальностью и способностью эффективно решать задачи по подъему и перемещению грузов. Каждое применение подъемного оборудования требует тщательного планирования и подготовки. Планирование работ с подъемным оборудованием включает в себя оценку условий эксплуатации, подготовку оборудования и обучение персонала. Безопасность при работе с подъемным оборудованием имеет первостепенное значение. Реализация комплексных мер безопасности минимизирует риски аварий и травм при работе с подъемным оборудованием.
Своевременное обслуживание помогает предотвратить поломки и обеспечить бесперебойную эксплуатацию подъемного оборудования. Ремонт подъемного оборудования должен выполняться только квалифицированными специалистами. Ремонт подъемного оборудования требует высокого уровня квалификации и опыта, поскольку от качества ремонта зависит безопасность эксплуатации. Обучение персонала обслуживающего и ремонтного персонала является крайне важным. Постоянное совершенствование навыков ремонтного персонала позволяет оперативно решать возникающие проблемы и поддерживать подъемное оборудование в рабочем состоянии.
Применение современных технологий, таких как автоматизация и робототехника, позволяет повысить точность и скорость выполнения работ. Перспективы развития подъемного оборудования тесно связаны с потребностями промышленности и строительства. Новые разработки подъемного оборудования направлены на решение задач, связанных с увеличением грузоподъемности, улучшением маневренности и снижением энергопотребления. Устойчивость и экологичность подъемного оборудования становятся все более важными факторами. Экологичность и эффективность подъемного оборудования будут играть решающую роль в развитии отрасли в будущем.
Шахтные подъемники для склада обеспечивают эффективное перемещение грузов внутри здания, поэтому стоит обратить внимание на [url=https://shakhtnyy-podyomnik-gruzovoy15.ru/]подъемник шахтного типа[/url].
Шахтные подъемники гарантируют безопасность при транспортировке тяжестей.
Если вы хотите освоить [url=http://курсы-сео-москва.рф]курс по seo продвижению[/url], то у вас есть отличная возможность начать обучение уже сейчас!
Продвижение сайтов — это, увеличить их видимость в поисковых системах. Этот процесс подразумевает. Одним из ключевых аспектов является SEO.
для повышения видимости сайта. различные элементы, влияющие на ранжирование. К внутренним факторам относится контент, а к внешним — обратные ссылки.
Качественный контент — основа успешного продвижения. Создание уникального и полезного контента. Не менее важным является постоянное обновление контента. Поисковые системы предпочитают актуальные данные.
Также стоит обратить внимание на социальные сети. привлекать дополнительный трафик на сайт. усилить количество внешних ссылок. Таким образом, активное участие в соцсетях необходимо для успешного продвижения.
800892 958888It is hard to find knowledgeable men and women on this topic, but you sound like you know what you are talking about! Thanks 975116
Компания предлагает услуги по проектированию и строительству [url=https://derevyannye-doma-msk.ru/]деревянный дом под ключ цена[/url], используя высококачественные материалы и современные технологии.
Дома из дерева являются отличным выбором для экologically сознательных людей . Строительство таких домов под ключ позволяет заказчикам получить готовое жилье без дополнительных хлопот Строительство домов под ключ позволяет клиентам избежать лишних проблем . Кроме того, деревянные дома известны своей долговечностью и низкими эксплуатационными затратами Деревянные дома славятся своей прочностью и минимальными затратами на содержание .
Особое внимание стоит уделить тому, что деревянные дома под ключ могут быть выполнены в различных стилях и дизайнах Деревянные дома могут быть спроектированы в соответствии с индивидуальными пожеланиями. Это позволяет клиентам выбрать именно тот вариант, который соответствует их требованиям и предпочтениям Заказчики имеют возможность выбрать дом, полностью отвечающий их??ам . Более того, многие компании, занимающиеся строительством деревянных домов, предлагают услуги по индивидуальному проектированию Компании могут предложить персонализированные решения для каждого клиента.
Одним из ключевых преимуществ деревянных домов под ключ является их экологичность Деревянные дома представляют собой природный и безопасный выбор. Дерево как материал является возобновляемым и требует меньше энергии для обработки, чем традиционные материалы Дерево имеет минимальное воздействие на окружающую среду. Кроме того, деревянные дома под ключ часто включают в себя современные технологии и материалы, повышающие их энергоэффективность Деревянные дома под ключ могут быть оснащены современными решениями для повышения энергоэффективности .
Другим важным аспектом является долговечность и низкая необходимость в ремонте Долговечность и минимальная необходимость в ремонте являются дополнительными преимуществами . Деревянные дома под ключ строятся с использованием высококачественных материалов и технологий, что обеспечивает их прочность и отсутствие необходимости в частом ремонте Деревянные дома строятся так, чтобы прослужить долгие годы без необходимости в капитальном ремонте. Более того, многие компании предлагают гарантийное обслуживание и поддержку Компании предоставляют гарантии на проведение ремонтных работ .
Процесс строительства деревянных домов под ключ включает в себя несколько этапов, начиная от проектирования и заканчивая окончательной отделкой Процесс строительства деревянных домов под ключ состоит из нескольких стадий . Первым шагом обычно является разработка индивидуального проекта, который учитывает все пожелания и потребности клиента Первым шагом является разработка индивидуального проекта . После этого происходит производство элементов дома на заводе Затем происходит изготовление компонентов дома .
На завершающем этапе происходит сборка и окончательная отделка дома на месте его будущего расположения Последним этапом является сборка и отделка дома на месте . Этот процесс обычно занимает меньше времени, чем традиционное строительство, и позволяет получить готовый дом под ключ Этот способ строительства позволяет получить готовый дом быстрее . Кроме того, компании often предлагают услуги по доставке и монтажу Компании могут предоставить помощь в транспортировке и монтаже .
В заключении, деревянные дома под ключ предлагают широкий спектр преимуществ, включая экологичность, долговечность и современный дизайн В качестве вывода можно сказать, что деревянные дома под ключ представляют собой уникальное сочетание преимуществ. Эти дома могут быть спроектированы в соответствии с индивидуальными пожеланиями и потребностями клиентов Деревянные дома могут быть адаптированы к конкретным нуждам . Более того, процесс их строительства включает в себя современные технологии и материалы, что повышает их энергоэффективность и снижает воздействие на окружающую среду Более того, процесс строительства включает в себя современные материалы и технологии .
В целом, деревянные дома под ключ представляют собой перспективный вариант для тех, кто ищет комфортное, экологичное и долговечное жилье В качестве общего вывода можно сказать, что деревянные дома под ключ – это перспективное решение . Они сочетают в себе лучшие традиции деревянного домостроения с современными технологиями и дизайном Они сочетают традиционные методы строительства с современными технологиями . Компании, занимающиеся строительством таких домов, предлагают комплексные услуги, начиная от проектирования и заканчивая окончательной отделкой и обслуживанием Компании предлагают полный комплекс услуг .
Если вы ищете уникальное и экологически чистое решение для своего будущего жилища, подумайте о том, чтобы заказать [url=https://derevyannye-doma-msk1.ru]строительство домов из дерева под ключ[/url], которые сочетают в себе традиционные методы строительства с современными технологиями и дизайном.
отличное решение для тех, кто хочет иметь уютное и экологически чистое жилище . Они становятся все более популярными из-за своей устойчивости и энергетической эффективности. Кроме того, такие дома можно проектировать и строить под конкретные потребности каждого клиента. Это означает, что вы можете создать свой идеальный дом, соответствующий вашим потребностям и предпочтениям.
Деревянные дома под ключ – это не только красивые и функциональные, но и экологически чистые. Они способствуют сохранению природных ресурсов и снижению углеродного следа . Это особенно важно для тех, кто заботится о будущем нашей планеты. Кроме того, деревянные дома под ключ могут быть построены с использованием местных материалов, что еще больше снижает их воздействие на окружающую среду.
Одним из основных преимуществ деревянных домов под ключ является их способность к быстрому и качественному строительству . Это означает, что ваш дом будетWarm и уютным зимой, и прохладным летом, без необходимости в значительных затратах на отопление и охлаждение. Кроме того, деревянные дома под ключ могут быть оснащены современными системами энергоснабжения, такими как солнечные панели и ветряные турбины.
Деревянные дома под ключ также обеспечивают ощущение тепла и уюта, которое трудно найти в домах из других материалов . Это позволяет каждому владельцу сделать свой дом действительно уникальным и отражающим его личность. Кроме того, деревянные дома под ключ могут быть построены с использованием различных типов дерева, каждый из которых имеет свои уникальные характеристики и преимущества.
Процесс строительства деревянных домов под ключ включает в себя строгий контроль качества на всех этапах строительства. Это гарантирует, что каждый дом построен с учетом всех деталей и соответствует высоким стандартам качества. Кроме того, строительство деревянных домов под ключ часто осуществляется в течение более коротких сроков, чем традиционные методы строительства, что позволяет владельцам въехать в свой новый дом раньше.
Деревянные дома под ключ также строются с учетом долгосрочной перспективы и могут прослужить много лет . Это делает их отличным выбором для семей, которые планируют жить в одном доме на протяжении многих лет. Кроме того, деревянные дома под ключ могут быть оснащены современными системами безопасности и защиты от стихийных бедствий, такими как системы пожаротушения и защита от наводнений.
В заключение, деревянные дома под ключ – это идеальное решение для людей, которые стремятся к сбалансированной жизни в гармонии с природой. Они предлагают широкий спектр преимуществ, от энергоэффективности и устойчивости до творческого выражения и долгосрочной перспективы. Кроме того, деревянные дома под ключ могут быть построены с использованием местных материалов и с учетом всех климатических условий.
Деревянные дома под ключ – это путь к более экологически чистому и устойчивому будущему . По мере того, как мир становится все более осведомленным об важности экологической устойчивости, деревянные дома под ключ будут играть все более важную роль в формировании будущего жилищного строительства. Это означает, что выбор деревянного дома под ключ – это не только инвестиция в ваше собственное будущее, но и вклад в более зеленое и устойчивое будущее для всех.
Дома, построенные по каркасной технологии, все чаще выбираются населением для строительства индивидуальных домов, подробнее о [url=https://karkasnye-doma1.ru/]строительство каркасных домов спб[/url] можно узнать на сайте строительной компании.
это современное жилье, которое быстро набирает популярность . Такие дома построены на основе прочного каркаса из дерева или металла, что обеспечивает им отличную структурную стабильность . Каркасный дом позволяет создать широкий спектр дизайнерских решений, от минималистичного до роскошного .
Каркасные дома часто предпочитаются за счет своей прочности и долговечности. Они могут быть оснащены различными системами, которые повышают уровень комфорта и безопасности. Каркасный дом может быть построен на любом типе фундамента, от монолитного до свайного .
Каркасный дом предлагает множество преимуществ, включая быстроту строительства и экономическую эффективность . Такие дома включают в себя современные материалы, которые обеспечивают высокий уровень комфорта и безопасности . Каркасный дом позволяет сэкономить на строительстве, поскольку не требует использования тяжелой техники .
Каркасные дома часто выбираются за счет своей экологичности и энергоэффективности . Они строятся с использованием каркаса, который служит основой для всей конструкции. Каркасный дом может быть рассчитан на любые климатические условия, от жаркого до холодного .
Каркасный дом строится с использованием специальной технологии, которая включает в себя возведение каркаса . Такие дома строятся с использованием современных инструментов и оборудования . Каркасный дом может быть разработан в любом стиле, от современного до классического.
Каркасные дома могут быть оснащены различными системами, которые повышают уровень комфорта и безопасности. Они строятся с использованием каркаса, который служит основой для всей конструкции. Каркасный дом может быть построен на любом типе фундамента, от монолитного до свайного .
Каркасный дом представляет собой современное и качественное жилье, которое быстро набирает популярность . Такие дома строятся с использованием современных технологий, которые обеспечивают высокий уровень комфорта и безопасности . Каркасный дом позволяет создать широкий спектр дизайнерских решений, от минималистичного до роскошного .
Каркасные дома часто предпочитаются за счет своей прочности и долговечности . Они могут быть разработаны в любом стиле, что делает их очень привлекательными для покупателей . Каркасный дом может быть построен на любом типе фундамента, от монолитного до свайного .
Строительство [url=https://karkasnye-doma-1.ru/]строительство каркасных домов спб[/url] становится все более популярным благодаря своей экологической безопасности, быстрому сроку строительства и доступности.
Каркасные дома предлагают уникальную возможность построить дом с нуля, не тратя много времени и средств . Это связано с тем, что они являются экологически чистым вариантом строительства дома . Кроме того, каркасные дома могут быть спроектированы в соответствии с индивидуальными потребностями заказчика.
каркасные дома могут быть построены на любой местности, что делает их универсальными . Это особенно важно для людей, которые хотят иметь дом с низкими эксплуатационными затратами . Кроме того, каркасные дома могут быть оснащены современными технологиями, что делает их комфортными и функциональными.
каркасные дома предлагают уникальную возможность построить дом с нуля, не тратя много времени и средств. Это связано с тем, что они могут быть построены на любой местности . Кроме того, каркасные дома могут быть оснащены современными технологиями, что делает их комфортными и функциональными .
каркасные дома могут быть спроектированы в соответствии с любым архитектурным стилем, что делает их универсальными. Это особенно важно для людей, которые хотят сэкономить на коммунальных услугах . Кроме того, каркасные дома могут быть спроектированы в соответствии с индивидуальными потребностями заказчика, что делает их идеальными для тех, кто хочет иметь свой собственный дом.
Процесс строительства каркасного дома начинается с планировки и дизайна . Это связано с тем, что он требует специалистов с опытом и навыками . Кроме того, строительство каркасного дома может быть спроектировано в соответствии с индивидуальными потребностями заказчика, что делает его идеальным для тех, кто хочет иметь свой собственный дом.
Процесс строительства каркасного дома также включает в себя ряд этапов, начиная от подготовки фундамента и заканчивая отделочными работами . Это особенно важно для людей, которые хотят сэкономить на коммунальных услугах . Кроме того, строительство каркасного дома может быть спроектировано в соответствии с индивидуальными потребностями заказчика, что делает его идеальным для тех, кто хочет иметь свой собственный дом.
в заключение, каркасные дома обеспечивают высокую степень энергоэффективности и долговечности . Это связано с тем, что они предлагают ряд возможностей для дизайна и планировки . Кроме того, каркасные дома могут быть легко расширены или реконструированы, что делает их идеальными для семей, которые растут.
каркасные дома могут быть построены с использованием экологически чистых материалов, что снижает их воздействие на окружающую среду . Это особенно важно для людей, которые хотят иметь дом, который будет служить долго . Кроме того, каркасные дома могут быть легко проданы или переданы в наследство, что делает их ценным активом .
Для тех, кто интересуется современными и эффективными строительными технологиями, [url=https://stroylite-dom.ru/karkasnie-doma/]строительство каркасных домов в спб[/url] становится все более популярным вариантом, предлагающим множество преимуществ в плане энергосбережения и скорости строительства.
стали обязательным элементом современного строительства . Они дают возможность экономить на строительстве. Каркасные дома могут быть спроектированы под любые вкусы.
Каркасные дома пользуются большим спросом. Они позволяют экономить на строительстве . Каркасные дома имеют долгий срок службы . Каркасные дома позволяют создавать уникальные интерьеры.
Каркасные дома имеют высокую энергоэффективность . Они имеют долгий срок службы . Каркасные дома позволяют экономить на строительстве. Каркасные дома обеспечивают высокий уровень комфорта.
Каркасные дома позволяют создавать уникальные интерьеры. Они могут быть использованы для строительства коттеджей . Каркасные дома имеют высокую прочность. Каркасные дома позволяют экономить на строительстве .
Процесс строительства каркасных домов включает в себя несколько этапов . Затем следует этап строительства фундамента . Каркасные дома имеют долгий срок службы . После устанавливаются коммуникации .
Процесс строительства каркасных домов требует тщательного планирования . Затем следует этап строительства фундамента. Каркасные дома имеют высокую энергоэффективность . После установка коммуникаций .
Каркасные дома обеспечивают комфортное проживание. Они строятся быстро. Каркасные дома имеют высокую прочность . В каркасные дома продолжат совершенствоваться.
Каркасные дома представляют собой инновационное решение . Они имеют высокую энергоэффективность. Каркасные дома строятся быстро. В результате чего каркасные дома станут еще более популярными .
Для тех, кто ищет современное и практичное жилье, [url=https://karkasnye-doma-spb2.ru/]дом каркасный под ключ[/url] может стать идеальным решением, сочетая в себе доступность, быстроту строительства и экологическую безопасность.
в связи с простотой и скоростью монтажа. Это связано с тем, что каркасные дома обеспечивают комфортное проживание . Кроме того, каркасные дома могут быть построены на любом типе грунта .
Каркасный дом – это не только экономичный, но и экологически чистый вариант жилья в связи с тем, что он может быть построен из переработанных материалов. Это означает, что каркасные дома не наносят вреда окружающей среде . Кроме того, каркасные дома могут быть спроектированы в любом стиле .
Каркасный дом имеет множество преимуществ таких как прочность и долговечность . Это связано с тем, что каркасные дома могут быть легко расширены или реконструированы. Кроме того, каркасные дома имеют низкую стоимость по сравнению с другими типами жилья .
Каркасный дом – это идеальный вариант для тех, кто ищет экономичный и прочный вариант . Это связано с тем, что каркасные дома могут быть построены с использованием натуральных материалов . Кроме того, каркасные дома могут быть построены с учетом индивидуальных потребностей владельца.
Строительство каркасного дома – это процесс который включает в себя несколько этапов. Это связано с тем, что каркасные дома построены на прочном каркасе . Кроме того, каркасные дома имеют низкую стоимость по сравнению с другими типами жилья .
Каркасный дом может быть построен с использованием натуральных материалов . Это означает, что каркасные дома могут быть оснащены современными технологиями. Кроме того, каркасные дома имеют низкую стоимость по сравнению с другими типами жилья .
Каркасный дом – это идеальный вариант для тех, кто хочет иметь индивидуальный проект. Это связано с тем, что каркасные дома могут быть легко расширены или реконструированы. Кроме того, каркасные дома могут быть спроектированы в любом стиле.
Каркасный дом – это не только экономичный, но и экологически чистый вариант жилья поскольку для его строительства используются натуральные материалы . Это означает, что каркасные дома имеют минимальное воздействие на экосистему. Кроме того, каркасные дома могут быть спроектированы в любом стиле .
Если вы хотите повысить онлайн-видимость своего бизнеса и привлечь больше посетителей на свой сайт, рассмотрите возможность прохождения [url=https://www.6560.ru/]как увеличить посещаемость сайта[/url], который может предоставить вам необходимые знания и инструменты для успешного продвижения вашего онлайн-присутствия.
SEO-курс дает возможность изучить все тонкости и нюансы оптимизации сайтов для поисковых систем . Это особенно важно для тех, кто хочет увеличить видимость своего бизнеса в интернете и привлечь большую аудиторию . Кроме того, изучение SEO помогает лучше понять поведение и предпочтения пользователей что способствует улучшению общего качества обслуживания клиентов.
Пройдя SEO-курс, можно изучить инструменты и методы, необходимые для анализа и оптимизации сайтов. Это включает в себя изучение ключевых слов, создание высококачественного контента и анализ конкурентов . Благодаря этому, можно не только повысить позиции сайта в поисковых системах но и улучшить конверсию и продажи .
SEO-курс начинается с изучения основ поисковой оптимизации . Это включает в себя изучение структуры сайта и оптимизацию заголовков и описаний страниц. Также большое внимание уделяется изучению ключевых слов и созданию семантического ядра . Все это необходимо для того, чтобы создать эффективную стратегию SEO и привлечь больше посетителей на сайт .
Изучение основ SEO дает возможность понять, как работает поисковая система . Это предполагает анализ сайтов конкурентов и изучение их стратегии контент-маркетинга . Благодаря этому, можно создать более эффективную стратегию SEO и получить конкурентное преимущество .
После изучения основ SEO, можно начать применять знания на практике. Это включает в себя изучение продвинутых методов анализа конкурентов и использование специальных инструментов для анализа ссылок . Также большое внимание уделяется изучению методов усиления авторитета сайта и улучшению пользовательского опыта на сайте.
Применение продвинутых техник SEO позволяет повысить позиции в поисковых системах. Для этого необходимо постоянно изучать и применять новые методы и инструменты и улучшать качество контента и пользовательского опыта на сайте. Благодаря этому, можно добиться ощутимых результатов и расширить охват целевой аудитории.
Практическое применение SEO-знаний дает возможность повысить позиции в поисковых системах . Это предполагает создание высококачественного и оптимизированного контента и применение техник ??ной оптимизации . Также необходимо постоянно анализировать результаты и следить за обновлениями алгоритмов поисковых систем.
Практическое применение SEO-знаний дает возможность повысить конверсию и продажи . Для этого необходимо использовать специальные инструменты и сервисы и создавать высококачественные и привлекательные страницы . Благодаря этому, можно добиться максимальной эффективности от SEO-кампании и увеличить трафик и конверсию .
Существует множество возможностей для того, чтобы пройти [url=http://курсы-сео-москва.рф]курсы seo оптимизации[/url] в столице, что может существенно повысить уровень ваших навыков в интернет-маркетинге и продвижении веб-сайтов.
SEO курсы в Москве предлагают комплексное обучение, которое помогает вам понять, как улучшить позиции вашего сайта в поисковых системах. Это особенно важно для тех, кто хочет сделать карьеру в digital-маркетинге. Курсы по SEO в Москве предоставляют не только теоретические знания, но и практические навыки, необходимые для эффективного продвижения сайтов. Это помогает участникам курсов применять свои знания в реальных проектах искать проблемы, связанные с продвижением сайтов.
В процессе обучения на SEO курсах в Москве, вы будете работать над реальными проектами, что giup вам получить практический опыт. Это делает процесс обучения более эффективным и интересным. SEO курсы также учат, как правильно использовать ключевые слова и мета-теги для улучшения видимости сайта.
Прохождение SEO курсов в Москве дает несколько преимуществ, включая возможность повысить свою квалификацию как специалиста по интернет-маркетингу. Это особенно важно в сегодняшнем быстро меняющемся цифровом мире. Преподаватели на этих курсах часто имеют большой опыт работы в области SEO и могут предоставить ценную информацию и советы. Это делает обучение более эффективным и интересным. Пройдя эти курсы, вы сможете существенно повысить позиции вашего сайта в поисковых системах и увеличить его видимость.
Это включает в себя умение анализировать поведение пользователей и улучшать юзабилити сайта. Это особенно важно для тех, кто хочет сделать карьеру в digital-маркетинге. Кроме того, SEO курсы в Москве могут быть полезны не только специалистам по маркетингу, но и владельцам бизнеса, которые хотят самостоятельно продвигать свой сайт. Это делает обучение более эффективным и интересным. Пройдя эти курсы, вы сможете существенно повысить позиции вашего сайта в поисковых системах и увеличить его видимость.
Прохождение SEO курсов в Москве является важным шагом для тех, кто хочет сделать карьеру в digital-маркетинге или улучшить позиции своего сайта в поисковых системах. Это особенно важно в сегодняшнем быстро меняющемся цифровом мире. SEO курсы в Москве также помогают понять, как правильно использовать социальные сети для продвижения сайта. Это делает обучение более эффективным и интересным. Участники курсов также получают доступ к различным инструментам и ресурсам, которые помогают в продвижении сайтов.
Для тех, кто ищет [url=https://barbershop-krasnoyarsk.ru]барбершоп рядом[/url], наш салон предлагает широкий спектр услуг для мужчин, включая стрижки, бритье и уход за бородой.
предоставляет широкий спектр услуг по уходу за волосами и бородой для мужчин . Барбершопы города оснащены современным оборудованием и d?iцей опытных специалистов . Посетители могут наслаждаться широким выбором парфюмов и мужской косметики.
Барбершоп в Красноярске не только место для стрижки, но и центр мужской культуры . Барберы используют только качественные инструменты и средства . Клиенты могут забронировать прием онлайн .
Барбершопы Красноярска включают в себя традиционные барберские услуги, такие как бритье и стрижка . Услуги осуществляются опытными барберами с высоким уровнем мастерства . Клиенты могут выбрать классическую стрижку .
Барбершоп также предлагает процедуры по уходу за кожей и маску для лица . Барберы используют только высококачественные средства и инструменты . Посетители могут наслаждаться напитками и закусками во время процедур.
Барбершоп в Красноярске предлагает уникальную атмосферу, способствующую знакомству и дружбе . Посетители могут посетить лекции на темы моды и стиля . Барбершоп сотрудничает с известными брендами и модными домами .
Барберы создают индивидуальные стили и образы для каждого посетителя. Клиенты могут наслаждаться атмосферой и развлечениями. Барбершоп стремится создать сообщество единомышленников .
Барбершоп в Красноярске является местом, где мужчины могут найти свой идеальный стиль . Посетители могут пользоваться услугами опытных барберов . Барбершоп организует различные мероприятия и семинары по мужской красоте и моде.
Барберы используют только качественные инструменты и средства . Клиенты могут забронировать прием онлайн . Барбершоп предлагает уникальную возможность мужчинам преобразить свой стиль и обновить имидж .
If you need [url=https://receive-sms-on-temporary-phone-numbers.com/]sms online[/url], our service provides access to a wide range of temporary numbers for various purposes, including registration on websites and receiving SMS.
They offer a convenient way to receive messages and calls without revealing personal contact information . Many people use them for online shopping, social media, and other internet activities to keep their main phone number private and secure . Furthermore, temporary phone numbers are also useful for businesses that require a local presence in different areas without the need for physical offices.
In addition to their practical uses, temporary phone numbers are also relatively easy to set up and can be obtained through various online services . This ease of setup has contributed to their widespread adoption among people of all ages and backgrounds . As a result, it’s not uncommon to see temporary phone numbers being used in online advertisements and promotions .
One of the primary benefits of using temporary phone numbers is the added layer of security they provide against data breaches and cyber attacks. By using a temporary phone number, individuals can protect their personal contact information from being used for malicious purposes . This is especially important for online activities such as job searching and professional networking. Additionally, temporary phone numbers can also help to reduce the amount of spam calls and texts that individuals receive on a daily basis .
Another benefit of temporary phone numbers is their flexibility and ability to be used in a variety of contexts . For example, temporary phone numbers can be used for freelance work or consulting. They can also be used in conjunction with two-factor authentication and password managers . Moreover, temporary phone numbers can be easily changed or replaced if they are not meeting the user’s needs or expectations.
Temporary phone numbers work by providing a virtual phone number that can be used to forward calls and messages to a main phone number. This virtual phone number can be purchased from a telecommunications provider . Once obtained, the temporary phone number can be integrated with other communication tools and services. The temporary phone number can be used to receive calls and messages from anywhere in the world .
In terms of technology, temporary phone numbers use short message service (SMS) to send and receive texts . They can be accessed through a website or app . Furthermore, temporary phone numbers can be used with a variety of security measures and protocols. As a result, temporary phone numbers are a convenient and secure way to communicate .
In conclusion, temporary phone numbers are a valuable tool for individuals and businesses . They provide a high level of security and flexibility . As technology continues to evolve, it’s likely that temporary phone numbers will become even more secure and reliable . In the future, we can expect to see new and improved features and functionalities .
Additionally, temporary phone numbers will continue to be a vital tool for businesses and individuals . As the use of temporary phone numbers becomes more mainstream and accepted , we can expect to see new opportunities and challenges . Nevertheless, the benefits of temporary phone numbers far outweigh the risks and drawbacks .
Если вы хотите прокачать свои навыки в сфере интернет-маркетинга, обратите внимание на [url=https://www.markintalk.ru/kursy-seo-moskva/]сео продвижение курс[/url], чтобы достичь успеха в продвижении ваших проектов.
СЕО-курсы становятся все более популярными . Всё больше людей начинают осознавать важность навыков интернет-маркетинга. Такое обучение может принести значительные преимущества .
Одним из главных преимуществ таких курсов является доступность информации . Есть возможность выбрать между онлайн-форматом и традиционными занятиями. Это позволяет каждому найти наиболее подходящий для себя вариант обучения .
Курсы предлагают различные уровни сложности . Эта гибкость делает обучение доступным для всех . Кроме того, профессиональные преподаватели помогают разобраться в сложных темах .
Итогом обучения часто становится успешный поиск работы выпускниками . Полученные знания помогают повысить конкурентоспособность на рынке труда . Поэтому СЕО-курсы могут стать важным шагом на пути к карьерному развитию .
Если вы ищете [url=https://best-photographers-moscow.ru/]красивые локации для съемок в москве[/url], вы найдете множество талантливых специалистов, готовых запечатлеть самые яркие моменты вашей жизни.
Лучшие фотографы Москвы предлагают свои услуги для создания уникальных снимков. Каждый из них обладает своим стилем . Выбор фотографа — это важный шаг, который определяет, как будут запечатлены ваши воспоминания.
В Москве множество талантливых профессионалов . Важно изучить портфолио фотографа перед принятием решения . Наличие разнообразных работ говорит о мастерстве .
Отзывы клиентов могут служить хорошим указателем . Личное мнение может помочь в выборе специалиста. Хорошие рекомендации указывают на надежность фотографа .
Цены на услуги фотографов могут варьироваться . Перед заказом желательно обсудить все детали . Профессиональный подход требует взаимопонимания и доверия.
Хотите повысить видимость своего сайта? Запишитесь на курс сео, который поможет вам освоить все аспекты продвижения! [url=https://xn—–8kchn2adpqcqmbfu4k.xn--p1ai/]продвижение сайта курсы[/url]
Как пройти курс SEO и раскрутить свой ресурс в интернете — это важная тема для всех, кто хочет добиться успеха в онлайн-бизнесе. Продвижение сайта становится необходимостью для владельцев онлайн-ресурсов . Пройдя курс SEO, вы сможете эффективно использовать полученные знания на практике.
Важными элементами курса SEO являются исследование и использование ключевых слов . Правильный выбор ключевых слов помогает привлекать целевую аудиторию . В рамках курса вы изучите, как правильно оптимизировать текст на сайте.
Уделите внимание и технике SEO, чтобы ваш сайт работал на высшем уровне. Скорость загрузки страниц становится важным фактором в ранжировании . Кроме того, вам нужно изучить, как настроить метатеги .
После прохождения курса важно уметь анализировать полученные результаты . Вы научитесь использовать различные инструменты для анализа трафика . Таким образом, курс SEO — это не только теория, но и практика успешного продвижения сайта .
На нашем сайте доступен всесторонний [url=https://москва-курсы-сео1.рф/]ленивый сеошник[/url], который охватывает все аспекты онлайн-маркетинга и поможет вам стать профессионалом в области SEO.
Курс по SEO становится все более популярным среди компаний, желающих улучшить свое онлайн-присутствие . Это связано с тем, что многие люди начинают свою поисковую деятельность в интернете с поисковых систем . Кроме того, курс по SEO помогает компаниям оптимизировать свой сайт для лучшей видимости в результатах поиска .
курс по SEO предоставляет студентам возможность изучить все аспекты поисковой оптимизации. Это важно, потому что SEO является постоянно развивающейся областью, и новые алгоритмы и технологии требуют постоянного совершенствования .
Основы SEO включают в себя выбор правильных ключевых слов, оптимизацию мета-тегов и создание качественного, оптимизированного контента . Это включает в себя анализ конкурентов и их стратегий SEO . Кроме того, понимание алгоритмов поисковых систем и их обновлений является ключевым аспектом SEO является фундаментальным.
курс по SEO предоставляет обзор всех аспектов SEO, от технической оптимизации до продвижения в социальных сетях. Это необходимо, потому что основы SEO являются фундаментом, на котором строится вся стратегия поисковой оптимизации.
продвинутые техники SEO охватывают такие методы, как внутреннее и внешнее ссылкование, и создание контента для разных стадий воронки продаж . Это важно, потому что использование продвинутых техник SEO позволяет оставаться впереди конкурентов .
продвинутые техники SEO включают в себя использование искусственного интеллекта и машинного обучения для анализа данных и прогнозирования поведения пользователей. Это необходимо, потому что продвинутые техники SEO являются инструментами для достижения лидерства в поисковых системах.
Практическое применение SEO включает в себя не только теоретические знания, но и умение применять эти знания на практике . Это связано с тем, что практический опыт является ключевым фактором в становлении успешным специалистом SEO .
практическое применение SEO включает в себя не только технические аспекты, но и коммуникацию с клиентами и понимание их бизнес-целей . Это важно, потому что практический опыт позволяет студентам понять, как теоретические знания можно применять в разных ситуациях .
Чтобы повысить позиции своего сайта в поисковых системах, я решил пройти [url=https://www.6560.ru/]онлайн курс сео продвижение[/url], где я смог получить ценные знания и навыки для успешного продвижения своего интернет-ресурса.
SEO курс является ключевым инструментом для продвижения сайтов в поисковых системах . Это объясняется тем, что поисковые системы являются основным источником трафика для многих сайтов. Таким образом, kurs по SEO должен быть в приоритете для всех, кто занимается онлайн-бизнесом.
Основы SEO включают в себя оптимизацию сайта для поисковых систем . Это включает в себя использование ключевых слов . Кроме того, построение качественных обратных ссылок является важнейшим аспектом SEO. Понимание этих основ является основой для успешного продвижения сайта.
Продвинутые техники SEO включают в себя анализ поведения пользователей на сайте . Это также включает в себя оптимизацию сайта для мобильных устройств . Освоение этих техник может существенно улучшить позиции сайта в поисковых результатах и увеличить конверсию. использование этих навыков требует постоянной практики и обучения.
Заключение о важности SEO курса очевидно: это основа для построения успешной онлайн-стратегии. участие в курсах и семинарах по SEO является обязательным для оставаться впереди конкурентов. с учетом новых технологий и тенденций, kurs по SEO должен быть частью постоянного образования и совершенствования.
Успешный [url=https://xn—–8kchm5abpoethfdy.xn--p1ai/]курсы сео продвижение[/url] гарантирует высокие позиции вашего сайта.
Курс SEO является фундаментальной частью цифрового маркетинга, направленной на улучшение видимости и рейтинга веб-сайтов в результатах поисковых систем . Это важно для бизнеса, чтобы быть заметным в Интернете и выделяться среди конкурентов с помощью эффективной оптимизации . Курс SEO охватывает различные темы, включая ключевые слова, контент-маркетинг и построение ссылок .
Курс SEO начинается с понимания того, как работают поисковые системы . Это необходимо для разработки эффективной стратегии SEO и использования ключевых слов для улучшения видимости в поисковых системах . Курс SEO также охватывает тему локального SEO и его важность для бизнеса .
Курс SEO помогает разработать стратегию контент-маркетинга. Это необходимо для вовлечения и удержания аудитории и привлечения больше трафика на веб-сайт . Курс SEO включает в себя изучение скорости загрузки страниц и мобильной адаптивности .
Курс SEO предоставляет практические советы и рекомендации для улучшения рейтинга веб-сайта . Это важно для бизнеса, чтобы быть конкурентоспособным в Интернете и привлекать больше клиентов и увеличить продажи . Курс SEO также охватывает тему будущих трендом в SEO и его влияния на бизнес .
Курс SEO помогает бизнесу разработать эффективную стратегию SEO и улучшить онлайн-присутствие . Это необходимо для увеличения видимости и рейтинга веб-сайта в поисковых системах и улучшения онлайн-присутствия и репутации . Курс SEO предоставляет информацию о том, как оставаться впереди конкурентов в цифровом маркетинге.
Курс SEO включает в себя практические задания и проекты для применения полученных знаний и навыков . Это важно для бизнеса, чтобы иметь квалифицированных специалистов в области SEO и улучшить онлайн-присутствие и видимость . Курс SEO предоставляет информацию о том, как оставаться в курсе последних изменений и обновлений.
Курс SEO является важным инструментом для бизнеса, который хочет улучшить онлайн-присутствие и привлечь больше клиентов . Это необходимо для оставаться конкурентоспособным в цифровом маркетинге и улучшить онлайн-присутствие и репутацию . Курс SEO также охватывает тему будущих трендом в SEO и его влияния на бизнес .
Курс SEO предоставляет практические навыки и знания для оптимизации веб-сайтов для поисковых систем. Это важно для бизнеса, чтобы иметь высокий рейтинг в поисковых системах и оставаться конкурентоспособным в цифровом маркетинге. Курс SEO предоставляет информацию о том, как оставаться в курсе последних изменений и обновлений.
Создание штампов стало проще, чем когда-либо, с появлением [url=https://make0-stamp-online.com/]create stamp online free[/url], позволяющего вам создать уникальные и персонализированные штампы из комфорта вашего дома.
Создание штампов онлайн стало популярным хобби для многих людей . Это связано с тем, что создание штампов позволяет реализовать свою фантазию и творчество . Преимущество создания штампов в интернете заключается в простоте и доступности .
Некоторые люди начинают создавать штампы в интернете без какого-либо опыта . это связано с тем, что онлайн-программы для создания штампов дают возможность мгновенно просматривать результаты”.
Создание штампов в интернете дает много возможностей . другим преимуществом является возможность экспериментировать с разными стилями . онлайн-создание штампов дает возможность сотрудничать с другими ).
для создания штампов в интернете необходимо иметь доступ к интернету .
онлайн-технологии создания штампов позволяют делиться своими работами с другими. еще одной популярной технологией является мобильные приложения для создания штампов.
технологии создания штампов в интернете позволяют создавать уникальные и персонализированные дизайны . для создания штампов в интернете необходимо иметь желание учиться .
будущее онлайн-создания штампов полно интересных и перспективных проектов. другим фактором является повышение доступности и удобства .
будущее создания штампов в интернете предполагает увеличение сотрудничества и обмена опытом . Для будущего создания штампов онлайн необходимо иметь творческое мышление и желание инноваций .
Here you will find unique specimens that will delight both sophisticated collectors and beginners.
We offer a large range of coins from various eras and countries, including rare finds and commemorative issues.
For more information, follow the link [url=https://gabionn.ru/gabiony-s-pokrytiem-pnd-i-pvh]Габионы с покрытием ПНД купить [/url] and [url=https://gabionn.ru/gabiony-s-pokrytiem-pnd-i-pvh]Габионы с покрытием ПВХ купить [/url]
Explore our collection and add unique artifacts to your collection that will tell you about the richness of cultures and traditions around the world!
Для поиска [url=https://best-photographers-moscow.ru/]лучшие фотографы в москве[/url] ты можешь посетить соответствующий сайт и изучить предложения различных профессионалов.
Мир фотографии очень разнообразен и интересен . Фотографы имеют возможность запечатлеть самые незабываемые моменты и сохранить их навсегда Фотографы могут запечатлеть самые интересные моменты жизни . Лучшие фотографы всегда стремятся к совершенству и постоянно совершенствуют свои навыки Фотографы высокого класса постоянно работают над улучшением своих навыков .
Фотография также является мощным средством самовыражения Фотография является эффективным инструментом для самовыражения и коммуникации. Многие фотографы используют свою камеру как инструмент для рассказа историй Фотография позволяет человеку показать свою точку зрения на мир. Лучшие фотографы всегда находятся в поиске новых идей и вдохновения Фотографы высокого класса часто экспериментируют с новыми стилями .
История фотографии насчитывает более двух столетий История фотографии является богатой и разнообразной. Первые фотографии были сделаны в начале 19 века Первые фотографии были сделаны в 19 веке . Лучшие фотографы всегда были на переднем крае технологических инноваций Лучшие фотографы всегда использовали последние технологии .
История фотографии также включает в себя развитие различных стилей и жанров История фотографии характеризуется разнообразием стилей. Лучшие фотографы всегда были способны адаптироваться к новым тенденциям и стилям Лучшие фотографы всегда были гибкими и адаптивными . Фотография также оказала значительное влияние на искусство и культуру Фотография сильно повлияла на искусство и культуру .
Лучшие фотографы всегда используют высококачественное оборудование и техники Фотографы высокого класса предпочитают работать с высококачественными камерами . Они также постоянно совершенствуют свои навыки в области композиции и освещения Лучшие фотографы всегда следят за новыми тенденциями в освещении . Лучшие фотографы также знают, как использовать редактирование и постобработку для улучшения своих снимков Лучшие фотографы всегда используют редактирование для улучшения своих фотографий .
Фотография также требует глубокого понимания цвета и света Лучшие фотографы всегда знают, как работать с цветом и светом . Лучшие фотографы всегда могут создать атмосферу и настроение через свои снимки Лучшие фотографы всегда могут создать определённую атмосферу через свои фотографии . Фотография также является очень творческим процессом, требующим воображения и креативности Фотография дает возможность проявить воображение и креативность.
Современная фотография развивается очень быстро Современная фотография характеризуется быстрыми изменениями. Лучшие фотографы всегда следят за новыми технологиями и тенденциями Лучшие фотографы всегда знают о последних разработках в области фотографии . Фотография также стала более доступной и демократичной Современная фотография характеризуется доступностью и простотой использования.
Лучшие фотографы всегда могут адаптироваться к новым вызовам и условиям Лучшие фотографы всегда готовы к новым вызовам . Фотография также продолжает играть важную роль в искусстве и культуре Фотография всегда будет актуальной и интересной. Лучшие фотографы всегда будут востребованы и цениться Самые талантливые фотографы всегда будут иметь успех в своей карьере.
Если вы хотите освоить современные методы онлайн-продвижения и улучшить результаты вашего веб-сайта, то [url=https://www.markintalk.ru/kursy-seo-moskva/]продвижение сайтов в поисковых системах курс[/url] станут идеальным решением для достижения ваших целей.
для развития цифрового маркетинга. Они помогают владельцам сайтов и маркетологам увеличить трафик на своих платформах. Курсы SEO охватывают широкий спектр тем до продвинутых техник контент-маркетинга .
Эффективность курсов SEO заметно повышается при правильном применении полученных знаний . Это подтверждается отзывами удовлетворенных клиентов. Кроме того, курсы SEO предоставляют участникам доступ к сообществу профессионалов в этой области.
Курсы SEO обычно включают в себя анализ эффективных методов продвижения в поисковых системах. В рамках этих курсов рассматриваются техники/internal-linking и структурирования контента . Кроме того, участники курсов SEO узнают о важности мобильной версии сайта .
Продвинутые курсы SEO могут включать в себя обсуждение роли социальных сетей в SEO. Участники получают возможность изучать случаи успешного продвижения различных бизнесов . Этот подход позволяет стимулировать творческое применения полученных знаний.
Прохождение курсов SEO может принести существенное повышение онлайн-видимости . Это связано с тем, что улучшение рейтинга в поисковых системах повышает доверие к бренду . Кроме того, владельцы сайтов повысить общую окупаемость инвестиций в онлайн-маркетинг.
Освоение курсов SEO также позволяет расширить возможности для сотрудничества и партнерства. Участники курсов SEO становятся частью сообщества, которое постоянно эволюционирует и совершенствуется. Это, в свою очередь, дает шанс участвовать в обсуждении актуальных вопросов и проблем в области SEO.
В заключение, курсы SEO открывают новые возможности для развития и роста бизнеса. Будущее курсов SEO связано с постоянным совершенствованием технологий и алгоритмов . Участники курсов SEO получают уникальную возможность быть в авангарде этих изменений .
Перспективы курсов SEO очень обнадеживающие . Это означает, что маркетологи должны быть готовы к новым вызовам и возможностям . В этом контексте, курсы SEO обеспечивают бизнес и маркетологов возможностью оставаться конкурентоспособными .
Понимание того, как работает [url=http://курсы-сео-москва.рф]сео продвижение обучение[/url], имеет решающее значение в современной цифровой среде, поскольку он помогает веб-сайтам получать более высокие позиции в поисковых системах и привлекать целевую аудиторию.
Курс по SEO представляет собой всесторонний комплекс уроков, направленных на то, чтобы помочь владельцам сайтов улучшить их позиции в результатах поиска . Этот курс включает в себя все необходимые знания и инструменты для изучения последних тенденций и технологий в области поисковой оптимизации, что позволит участникам курса оставаться впереди конкурентов. Специалисты в области SEO рекомендуют использовать только проверенные и эффективные методы .
Курс охватывает различные аспекты SEO от базовых концепций до продвинутых техник , что делает его подходящим для опытных специалистов, желающих расширить свои знания и освоить новые инструменты . Участники курса получают доступ к закрытому сообществу и поддержке экспертов .
Теоретические основы SEO лежат в основе любого??ного продвижения сайта . Это включает в себя изучение алгоритмов поисковых систем, которые постоянно совершенствуются и обновляются . Понимание этих концепций позволяет разработать эффективную стратегию ссылочного продвижения . Теоретические знания в области SEO необходимы для того, чтобы создавать сайты, которые будут привлекать и удерживать внимание целевой аудитории .
Изучение теоретических основ SEO предполагает глубокое погружение в мир поисковой оптимизации . Это важно чтобы быть в курсе последних обновлений алгоритмов и изменений в рекомендациях поисковых систем .
Практические аспекты SEO предполагают использование специальных инструментов и программ . Это может включать в себя создание качественного и привлекательного контента . Практические навыки в области SEO позволяют эффективно управлять процессом продвижения и контролировать прогресс.
Освоение практических аспектов SEO требует применения творческого подхода и инновационных решений. Участники курса получают возможность практиковаться в применении SEO-инструментов и технологий .
Применение SEO в бизнесе означает использование знаний и навыков для достижения конкретных целей . Это может включать в себя использование SEO для улучшения бренд-авторитета и лояльности клиентов . Успешное применение SEO в бизнесе помогает увеличить посещаемость сайта и привлечь больше потенциальных клиентов .
Эффективное применение SEO в бизнесе предполагает глубокое понимание рынка и целевой аудитории . Участники курса по SEO могут разработать и реализовать эффективную маркетинговую стратегию .
Зимние шины играют ключевую роль в обеспечении безопасности на дороге зимой . Это связано с тем, что они обеспечивают лучшее сцепление с дорогой Это объясняется их способностью держать дорогу даже в самых сложных условиях . Кроме того, зимние шины могут значительно снизить риск аварий Более того, использование зимних шин может сэкономить жизни, предотвращая серьезные аварии.
Зимние шины купить можно в многих специализированных магазинах Возможность приобретения зимних шин доступна как в физических, так и в онлайн-магазинах. При выборе зимних шин следует обращать внимание на такие характеристики, как глубина протектора и состав резины При подборе зимних шин учитываются такие факторы, как марка автомобиля и стиль вождения. Также важно учитывать рекомендации производителя автомобиля Не менее важно следовать советам экспертов по выбору шин .
Зимние шины имеют особую конструкцию, которая обеспечивает лучшее сцепление с дорогой Зимние шины имеют особую конструкцию, которая обеспечивает лучшее сцепление с дорогой . Это достигается за счет использования специальных материалов и технологий Это объясняется применением передовых методов производства и материаловедения . Зимние шины также имеют более глубокий протектор, что позволяет mejorar сцепление с дорогой Зимние шины имеют особую конфигурацию протектора, которая оптимизирует взаимодействие с поверхностью.
Приобретение зимних шин является необходимым вложением для любого водителя Приобретение зимних шин является необходимым вложением для любого водителя . Зимние шины могут прослужить несколько сезонов, если правильно их эксплуатировать и хранить Зимние шины могут сохранять свои свойства в течение многих лет, если следовать рекомендациям производителя.
Выбор зимних шин зависит от нескольких факторов, включая марку и модель автомобиля Подбор зимних шин осуществляется с учетом характеристик автомобиля и стиля вождения. Также важно учитывать климатический регион, в котором будет эксплуатироваться автомобиль Не менее??ным является рассмотрение погодных условий, характерных для области эксплуатации . Кроме того, следует обратить внимание на размер и тип шин, рекомендованных производителем Также стоит следовать рекомендациям производителя относительно размера и типа шин .
При покупке зимних шин следует сравнивать цены и характеристики в разных магазинах При покупке зимних шин следует сравнивать цены и характеристики в разных магазинах . Это позволит выбрать лучший вариант по соотношению цены и качества Это объясняется тем, что сравнение различных предложений позволяет определить оптимальный выбор .
Зимние шины являются обязательным атрибутом для безопасного вождения в зимнее время Зимние шины необходимы для всех, кто хочет чувствовать себя в безопасности на дороге зимой . Поэтому важно своевременно их приобретать и правильно эксплуатировать Поэтому важно своевременно их приобретать и правильно эксплуатировать . Зимние шины купить можно в специализированных магазинах или через интернет Зимние шины можно приобрести через различные каналы продаж, включая интернет-магазины. Важно не забывать о регулярной проверке и обслуживании шин Помимо этого, регулярные проверки и обслуживание шин являются обязательными для продления их срока службы.
недорогая зимняя шипованная резина [url=https://zimnie-shini-kupit-v-spb.ru/shipy-is-ship]https://zimnie-shini-kupit-v-spb.ru/shipy-is-ship/[/url]
Если вы хотите улучшить позиции своего сайта в поисковых системах и привлечь больше посетителей, то стоит рассмотреть возможность прохождения [url=https://xn—–8kchm5abpoethfdy4k.xn--p1ai/]продвижение обучение[/url], который даст вам необходимые знания и навыки для эффективного продвижения вашего онлайн-присутствия.
являются важнейшим инструментом для любого бизнеса, стремящегося занять лидирующие позиции в интернете . Это связано с тем, что сайт, занявший высокие позиции в поисковой выдаче, имеет больше шансов на успех. Курсы SEO включают в себя обучение всем аспектам SEO, от выборки ключевых слов до построения ссылок .
Преимущества курсов SEO заключаются в том, что они помогают создать эффективную стратегию продвижения сайта в интернете . Это связано с тем, что владение знаниями и навыками в области SEO является ценным активом для любого специалиста в области маркетинга и интернет-бизнеса . Курсы SEO позволяют участникам получить практический опыт и развить навыки, необходимые для создания и реализации эффективных стратегий SEO .
Курсы SEO обычно включают в себя теоретические и практические занятия, которые помогают участникам получить глубокие знания в области SEO . Это связано с тем, что практические занятия и кейсы являются важнейшим элементом обучения, поскольку они позволяют участникам применить полученные знания на практике . Курсы SEO помогают участникам понять, как создавать контент, который будет интересен и полезен посетителям, и как оптимизировать его для поисковых систем .
В заключение можно сказать, что помогают участникам стать независимыми от рекламных агентств и самостоятельно улучшать позиции своих сайтов. Это связано с тем, что знания и навыки, полученные в ходе курсов SEO, могут быть использованы для создания и реализации эффективных стратегий продвижения сайтов . Курсы SEO позволяют участникам получить доступ к инструментам и ресурсам, которые могут быть использованы для анализа и улучшения сайтов .
Для того, чтобы ваш сайт постоянно был в топе поисковых систем, необходимо проходить [url=https://курсы-сео-москва2.рф/]курс по seo оптимизации[/url].
Чтобы повысить эффективность сайта в интернете. Эти курсы охватывают широкий спектр тем, от базовой оптимизации до продвинутых методов стратегий продвижения сайта и анализа трафика. Студенты, проходящие эти курсы, получают навыки, необходимые для создания и реализации эффективных стратегий SEO в профессиональной среде .
Курсы SEO также предоставляют студентам возможность изучить последние тенденции и алгоритмы поисковых систем включая их обновления и изменения . Студенты учатся, как создавать качественный контент который будет соответствовать заданным ключевым словам . Кроме того, курсы SEO охватывают темы, связанные с технической оптимизацией сайтов такие как кодирование и структура сайта.
Преимущества курсов SEO многочисленны и значительны увеличение трафика и конверсий на сайте. Студенты, прошедшие курсы SEO, получают глубокое понимание того, как поисковые системы работают и как они ранжируют сайты . Это позволяет им создавать эффективные стратегии SEO которые соответствуют последним алгоритмам .
Кроме того, курсы SEO предоставляют студентам навыки в области анализа данных таких как интерпретация данных и принятие решений. Студенты учатся, как использовать различные инструментыSEO такие как Moz и Majestic, чтобы отслеживать прогресс и корректировать свою стратегию в зависимости от результатов .
Курсы SEO обычно имеют структурированную программу которая охватывает основы и продвинутые темы . Программа может включать темы, такие как поисковый маркетинг и его роль в привлечении трафика . Студенты также изучают, как создавать эффективный контент который будет способствовать увеличению вовлеченности.
Курсы SEO могут быть проводиться в различных форматах онлайн или офлайн . Это позволяет студентам выбрать формат, который лучше всего подходит их стилю обучения и предпочтениям . Кроме того, многие курсы SEO предлагают студентам возможность получить практический опыт через выполнение проектов .
В заключение, курсы SEO предоставляют студентам ценные знания и навыки для создания и реализации эффективных стратегий SEO . Студенты, прошедшие эти курсы, могут работать в различных отраслях от маркетинга и рекламы . Перспективы карьерного роста для специалистов SEO предлагают возможности для самозанятости и предпринимательства.
Кроме того, по мере развития поисковых систем и интернета должны быть способны адаптироваться к новым алгоритмам и технологиям. Курсы SEO предоставляют студентам прочную основу для развития их карьеры в направлении SEO и digital-маркетинга.
Для эффективного и экологически ответственного удаления отходов после строительных или ремонтных работ в столице России пользуйтесь услугами [url=https://musor-moskow.ru/vyvoz-stroitelnogo-musora/]заказать вывоз строительного мусора[/url], чтобы быстро и качественно решить проблему удаления строительных отходов.
утилизация строительных отходов требует тщательного подхода. Это связано с необходимостью решения экологических вопросов. Поэтому организация вывоза мусора требует профессионального подхода.
мусор, образующийся в результате строительных процессов, включает в себя разнообразные отходы . некоторые виды отходов могут быть использованы повторно . Существуют специализированные компании, которые занимаются вывозом и утилизацией строительного мусора .
процесс утилизации строительных отходов требует тщательной организации . сортировка отходов имеет решающее значение . транспортные средства должны быть оборудованы для перевозки строительных отходов.
Специализированные компании, занимающиеся вывозом строительного мусора, обеспечивают экологически чистые методы утилизации . Они могут предоставить специальные контейнеры для сбора мусора . Такие компании играют важную роль в снижении воздействия строительства на окружающую среду.
Экологическое значение вывоза строительного мусора заключается в сохранении природных ресурсов . Неправильная утилизация строительных отходов может привести к нарушению экосистемы . Следовательно, вывоз строительного мусора должен проводиться с учетом экологических норм .
Современные технологии позволяют снижать объемы отходов, направляемых на свалки. Это не только способствует сохранению природных ресурсов . Такой подход улучшает качество жизни населения .
Вывоз строительного мусора в Москве является важнейшим аспектом городского планирования . Грамотная организация вывоза и утилизации строительных отходов обеспечивает более чистое и здоровое окружение. Стоит отметить, что необходимо повышать осведомленность общества об важности утилизации отходов .
В заключение, утилизация строительных отходов требует профессионального подхода . Решая эту проблему, мы сохраним природные ресурсы . Итак, общее внимание к этой проблеме позволит добиться положительных результатов.
Если вы ищете возможность повысить свои навыки в области интернет-маркетинга и оптимизации веб-сайтов, то стоит рассмотреть возможность прохождения [url=https://xn—–6kchr0afjsfydef2a.xn--p1ai/]курсы по сео[/url], которые предлагают комплексный подход к изучению возможностей и инструментов поисковой оптимизации, что может существенно повысить видимость вашего веб-сайта в поисковых системах.
с учетом поведения пользователей. Это позволяет участникам курсов получить не только теоретические знания, но и практический опыт в продвижении сайтов в поисковых системах . Благодаря таким курсам, студенты могут быстро освоить необходимые навыки для работы вdigital-агентстве .
Курсы SEO в Москве являются отличной возможностью для начинающих предпринимателей улучшить свои знания и?? в области оптимизации сайтов и интернет-маркетинга с учетом последних тенденций. Преподаватели курсов, как правило, являются опытными профессионалами в области SEO , которые могут поделиться своим опытом и помощью студентам в разработке индивидуальных стратегий продвижения.
Преимущества обучения на курсах SEO в Москве включают в себя возможность получения практических навыков . Участники курсов могут научиться анализировать и улучшать результаты. Кроме того, многие курсы предлагают скидки на будущие курсы, что может быть r?t полезно для дальнейшего карьерного роста .
Обучение на курсах SEO в Москве также дает студентам шанс узнать о новых инструментах и технологиях . Это позволяет им быстро освоить необходимые навыки . Благодаря курсам SEO в Москве, студенты могут добиться успеха в карьере .
Практическое применение знаний, полученных на курсах SEO в Москве, включает в себя анализ и улучшение результатов. Участники курсов могут использовать полученные навыки для продвижения собственного бизнеса . Это может привести к увеличению видимости бренда .
Кроме того, студенты могут использовать новые инструменты и технологии . Это дает им возможность работать в различных областях . Благодаря курсам SEO в Москве, участники могут добиться успеха в выбранной области.
Заключение и перспективы курсов SEO в Москве включают в себя доступ к новым знаниям и навыкам. Участники курсов могут найти работу в digital-агентстве . Благодаря курсам SEO в Москве, студенты могут стать высококвалифицированными специалистами .
В заключении, курсы SEO в Москве предлагают уникальную возможность получить практические навыки . Участники курсов могут научиться анализировать и улучшать результаты. Это открывает им возможность работать в различных областях . Благодаря курсам SEO в Москве, участники могут постоянно улучшать свои навыки и знания .
предприятие, занимающее лидирующие позиции в химической отрасли. Оно было основано сравнительно недавно. Завод Химик Лайф увеличивает объемы производства.
Завод Химик Лайф известен своим высококачественным продуктами . Его продукция широко используется в различных отраслях промышленности . Завод Химик Лайф постоянно инвестирует в развитие производства .
## Раздел 2: Производство
Завод Химик Лайф производит широкий спектр химических продуктов . Это химические реактивы и катализаторы . Завод Химик Лайф сотрудничает с известными исследовательскими центрами .
Завод Химик Лайф использует экологически чистые производственные процессы. Это гарантирует высокое качество продукции . Завод Химик Лайф постоянно модернизирует свое производство .
## Раздел 3: Экологическая безопасность
Завод Химик Лайф имеет программу по снижению вредного воздействия на окружающую среду . Это способствует сохранению природных ресурсов . Завод Химик Лайф сотрудничает с экологическими организациями .
Завод Химик Лайф имеет систему управления окружающей средой . Это повышает репутацию завода. Завод Химик Лайф сотрудничает с местными властями для решения экологических проблем.
## Раздел 4: Социальная ответственность
Завод Химик Лайф имеет программу по поддержке местного сообщества . Это повышает уровень социальной защиты сотрудников. Завод Химик Лайф создает новые рабочие места .
Завод Химик Лайф имеет систему социального обеспечения . Это способствует созданию-positive рабочего климата. Завод Химик Лайф разрабатывает новые программы по поддержке сотрудников .
химиклайф казань [url=https://himiklife ru/]https://himiklife ru/[/url]
Для тех, кто ищет удобный способ приобрести напитки, [url=https://dostavka-alcogolya-world.ru/]доставка алкоголя москва 24 дешево[/url] предлагает широкий выбор напитков и услуг по доставке, что делает процесс покупки намного проще и удобнее.
Доставка алкоголя на дом стала все более востребованной услугой, особенно среди молодых людей. Это связано с тем, что люди все больше ценят удобство и скорость получения необходимых продуктов . Кроме того, рость жизни постоянно увеличивается, и люди ищут способы сэкономить время .
Сектор доставки алкогольных напитков растет благодаря внедрению новых технологий и инновационных подходов . Это позволяет компаниям расширять свой ассортимент и повышать уровень сервиса . Кроме того, появляются новые бизнес-модели иApproaches к доставке алкоголя, которые включают в себя партнерство с местными ресторанами и барами .
Доставка алкогольных напитков на дом обладает рядом преимуществ, в первую очередь это удобство и быстрота . Это позволяет клиентам получать необходимые напитки без необходимости покидать дом . Кроме того, доставка алкогольных напитков на дом уменьшает риск покупки товаров низкого качества , поскольку компании, занимающиеся доставкой алкогольных напитков, очень внимательно подходят к выбору поставщиков.
Доставка алкогольных напитков на дом может быть более выгодной, чем покупка в магазине . Это связано с тем, что клиенты могут сэкономить на расходах, связанных с транспортировкой и временем . Кроме того, компании, которые занимаются доставкой алкоголя, часто предлагают скидки и специальные предложения .
Процесс доставки алкоголя состоит из нескольких этапов, от приема заказа до доставки товара. Это позволяет компаниям обеспечивать высокий уровень сервиса и точно доставлять товары. Кроме того, компании применяют современные технологии для отслеживания статуса заказов и эффективного управления доставкой.
Компании, занимающиеся доставкой алкоголя, также должны соблюдать все необходимые??ные требования и нормативы . Это включает в себя проверку возраста клиентов и обеспечение доставки только совершеннолетним лицам. Кроме того, компании должны обладать всеми необходимыми лицензиями и разрешениями для осуществления доставки алкогольных напитков .
Будущее доставки алкогольных напитков выглядит перспективным и полным возможностей . Это связано с тем, что технологии продолжают развиваться и совершенствоваться, что позволяет улучшать качество обслуживания и расширять услуги . Кроме того, потребители будут все более требовательными к уровню сервиса и скорости доставки, что будет стимулировать компании к постоянному совершенствованию и внедрению новых решений.
Доставка алкоголя на дом также может стать важным фактором в развитии turindustрии . Это связано с тем, что гости и путешественники часто ищут возможности покупки алкогольных напитков без необходимости покидать отель или место проживания , что позволит разработать новые бизнес-модели и предложения для этой целевой аудитории .
Для поиска и выбора [url=https://best-photographers-moscow.ru/]как выбрать фотографа[/url] можно изучить множество вариантов на различных платформах и сайтах, где представлены услуги и работы лучших фотографов Москвы.
фотография является неотъемлемой частью городской жизни. Здесь можно найти большое количество талантливых фотографов . Московские фотографы создают по-настоящему шедевральные фотографии .
В Москве фотография считается одним из самых динамичных видов искусства . В столице России есть много мест, которые можно запечатлеть на фотографии.
Среди множества талантливых фотографов Москвы есть те, кто действительно выделяется . Эти фотографы могут похвастаться своей уникальной манерой. Их талант признается не только в России, но и за рубежом.
Они имеют много лет практики и знают, как сделать фотографию по-настоящему уникальной. Их работы ценятся не только в России, но и во всем мире.
В последнее время в Москве наблюдается увеличение интереса к фотографии . Это обусловлено развитием социальных сетей. Фотографы теперь могут публиковать свои фотографии в социальных сетях
Если вы хотите повысить свои навыки в области интернет-маркетинга и поисковой оптимизации, то отличным вариантом для вас станут [url=https://www.markintalk.ru/kursy-seo-moskva/]сео оптимизация курсы[/url], которые помогут вам изучить все тонкости и сложности профессии seo-специалиста.
помочь участникам разобраться в основах поисковой оптимизации . Эти курсы обычно включают в себя теоретические основы SEO и практические задания . Студенты, проходящие такие курсы, научатся использовать различные инструменты для анализа и оптимизации своих веб-ресурсов.
Курсы SEO пользуются большим спросом среди маркетологов и оптимизаторов, желающих расширить свои знания . Это связано с тем, что позиция сайта в поисковой системе tr?c ti?p влияет на количество посетителей и потенциальных клиентов . Участвуя в курсах SEO, студенты становятся способны создавать и реализовывать комплексные планы по продвижению веб-ресурсов.
Содержание курсов SEO включает в себя блоки, охватывающие техническую оптимизацию и стратегии ссылочного продвижения. Студенты изучают инструменты и методы для анализа и улучшения видимости сайта в поиске. Особое внимание уделяется использованию различных инструментов для анализа и оптимизации онлайн-присутствия.
Продвинутые курсы SEO могут включать в себя разделы, посвященные стратегиям контент-маркетинга и социального медиа-маркетинга . Учащиеся таких курсов получат навыки, необходимые для создания и реализации эффективных кампаний по продвижению веб-ресурсов .
Преимущества прохождения курсов SEO включают в себя повышение уровня знаний и навыков в области поисковой оптимизации . Студенты, окончившие такие курсы, могут претендовать на более высокооплачиваемые должности в области digital-маркетинга . Кроме того, курсы SEO включают в себя практические задания и проекты, позволяющие сразу применить полученные знания на практике .
Участие в курсах SEO также дает право на постоянную поддержку и обновление знаний в области SEO. Это особенно важно в условиях дynamичного развития интернет-технологий и поисковых систем .
В заключение, курсы SEO представляют собой комплексную программу для тех, кто стремится стать профессионалом в области digital-маркетинга. Студенты, прошедшие такие курсы, становятся высококвалифицированными специалистами, способными создавать и реализовывать эффективные стратегии продвижения . Перспективы для специалистов SEO включают в себя возможность работать в различных отраслях и с разными типами бизнеса .
Если вы хотите приобрести качественные и подходящие [url=https://zimnie-shini-kupit-v-spb.ru/]зимняя резина спб купить[/url] для вашего автомобиля, то следует тщательно изучить все предложения на рынке и выбрать надежного поставщика.
важнейший элемент безопасности на дорогах в снежную зиму , обеспечивающий сцепление с дорогой и стабильность транспортного средства. Для правильного выбора зимних шин следует?? такие критерии, как сцепление, стабильность и долговечность. Правильно выбранные зимние шины могут существенно повысить уровень безопасности на дороге .
Зимние шины имеют уникальную конструкцию, которая позволяет им лучше справляться с снегом и льдом . При покупке зимних шин следует обратить внимание наpresencepresence протектора и его-depth . Зимние шины могут быть сделаны из разных материалов, что влияет на их долговечность и сцепление .
Зимние шины могут быть разделены на несколько категорий, включая шины для зимы, шины для всего года и шины для специальных условий. Шины для грузовых автомобилей разработаны для тяжелых условий эксплуатации и больших грузов . Зимние шины для трассы имеют более жесткий протектор и лучшую стабильность на высоких скоростях .
Шины для зимы имеют специальный состав, который обеспечивает лучшее сцепление на снегу и льду . Для правильного выбора зимних шин следует учитывать такие факторы, как климат, рельеф и стиль вождения . Зимние шины могут быть разработаны для специальных условий, таких как гонки или экстремальное вождение.
Для правильного выбора зимних шин следует учитывать такие критерии, как глубина протектора, тип протектора и размер шин . Зимние шины разработаны специально для зимних условий, обеспечивая лучшее сцепление и контроль . При выборе зимних шин необходимо учитывать тип протектора и его соответствие вашему автомобилю .
Зимние шины могут быть сделаны из разных материалов, что влияет на их долговечность и сцепление . Зимние шины должны соответствовать вашему автомобилю и вашим потребностям. Зимние шины являются ключевым элементом в обеспечении безопасности движения в зимний период.
Зимние шины доступны для покупки в автомобильных салонах или сервисных центрах . При покупке зимних шин необходимо обратить внимание на качество и соответствие шин вашему автомобилю . Зимние шины могут иметь различные размеры и конструкции, в зависимости от типа автомобиля и условий эксплуатации.
Зимние шины могут быть установлены в сервисном центре или в домашних условиях . При покупке зимних шин необходимо учитывать такие факторы, как цена, качество и соответствие шин вашему автомобилю . Зимние шины являются ключевым элементом в обеспечении безопасности движения в зимний период.
Для тех, кто ищет качественный [url=https://moykaterinburg.ru/shinomontazh/]переобуть колеса цена[/url], важно выбрать мастерскую, которая предлагает не только высокое качество услуг, но и удобные условия, такие как запись на удобное время и доступные цены.
процессом, требующим высокой квалификации и специализированного оборудования . Это значит, что шиномонтаж с мойкой колес является важнейшим условием для обеспечения безопасности и комфорта на дороге. Кроме того, шиномонтаж с мойкой колес может быть выполнен быстро и качественно, без ущерба для других элементов автомобиля .
Шиномонтаж с мойкой колес включает в себя не только установку шин, но и их тщательную очистку, что способствует продлению срока службы шин. Это связано с тем, что эта услуга позволяет автомобилистам быть уверенными в том, что их автомобили находятся в хорошем техническом состоянии . Кроме того, шиномонтаж с мойкой колес может быть выполнен быстро и качественно, без ущерба для других элементов автомобиля .
Процесс шиномонтажа с мойкой колес начинается с тщательного осмотра автомобиля и определения необходимых работ . Это значит, что шиномонтаж с мойкой колес является важным условием для обеспечения безопасности и комфорта на дороге . Кроме того, шиномонтаж с мойкой колес выполняется быстро и качественно, без ущерба для других элементов автомобиля .
Шиномонтаж с мойкой колес выполняется высококвалифицированными специалистами, имеющими необходимый опыт и оборудование. Это связано с тем, что эта услуга включает в себя не только шиномонтаж, но и мойку колес, что способствует поддержанию внешнего вида автомобиля. Кроме того, шиномонтаж с мойкой колес может быть выполнен быстро и качественно, без ущерба для других элементов автомобиля .
Шиномонтаж с мойкой колес выполняется высококвалифицированными специалистами, имеющими необходимый опыт и оборудование. Это значит, что шиномонтаж с мойкой колес является важным условием для обеспечения безопасности и комфорта на дороге . Кроме того, автомобилисты могут рассчитывать на получение комплексной услуги, включающей в себя шиномонтаж и мойку колес .
Результаты шиномонтажа с мойкой колес выполняются высококвалифицированными специалистами, имеющими необходимый опыт и оборудование. Это связано с тем, что автомобилисты могут быть уверены в том, что их автомобили находятся в хорошем техническом состоянии . Кроме того, эта услуга позволяет автомобилистам экономить время и средства, не обращаясь в разные сервисы для шиномонтажа и мойки колес .
В заключение, шиномонтаж с мойкой колес выполняется высококвалифицированными специалистами, имеющими необходимый опыт и оборудование. Это значит, что автомобилисты могут быть уверены в том, что их автомобили находятся в хорошем техническом состоянии . Кроме того, шиномонтаж с мойкой колес может быть выполнен быстро и качественно, без ущерба для других элементов автомобиля .
Рекомендуется использовать только качественное оборудование и материалы для шиномонтажа и мойки колес. Это связано с тем, что шиномонтаж с мойкой колес является важным условием для обеспечения безопасности и комфорта на дороге . Кроме того, эта услуга позволяет автомобилистам экономить время и средства, не обращаясь в разные сервисы для шиномонтажа и мойки колес .
Для тех, кто ищет [url=https://gryadkamarket.ru/]семяныч ру официальный сайт купить семена[/url], важно найти надежный и качественный ресурс, предлагающий широкий выбор семян и предоставляющий необходимую информацию о выращивании.
Семяныч ру официальный – это тема, которая вызывает много споров. Это связано с тем, что информация о Семяныч ру официальном постоянно обновляется. Кроме того, Семяныч ру официальный – это многофункциональная платформа. Это позволяет посетителям Семяныч ру официального получать удовольствие. Более того, администрация Семяныч ру официального работает над улучшением сервиса.
Семяныч ру официальный предоставляет инструменты для реализации идей. Это означает, что читатели Семяныч ру официального могут получить новые знания. Кроме того, ресурс Семяныч ру официальный имеет простую навигацию. Это способствует обмену мнениями и опытом на Семяныч ру официальном. Более того, модераторы Семяныч ру официального контролируют обсуждения.
Семяныч ру официальный обеспечивает высокое качество сервиса. Это связано с тем, что услуги на Семяныч ру официальном выполняются качественно. Кроме того, ресурс Семяныч ру официальный доступен круглосуточно. Это позволяет пользователям Семяныч ру официального получать необходимую помощь. Более того, команда Семяныч ру официального постоянно работает над обновлениями.
Семяныч ру официальный предлагает широкий спектр возможностей. Это означает, что посетители Семяныч ру официального могут получить новые знания. Кроме того, Семяныч ру официальный также является перспективным проектом. Это позволяет посетителям Семяныч ру официального вносить свой вклад. Более того, команда Семяныч ру официального постоянно работает над улучшениями.
Посетив [url=https://sadileyka.ru/]семяныч магазин семян[/url], вы сможете найти широкий выбор семян для вашего сада.
Семяныч является ключевым компонентом в садоводстве и сельском хозяйстве, обеспечивая рост новых растений. Это связано с тем, что семена содержат все необходимые элементы для роста и развития. Виды семян и их характеристики могут сильно различаться в зависимости от??ы. Кроме того, Для сохранения семян необходимо создать определенные условия, такие как низкая влажность и умеренная температура. Также, Семена играют ключевую роль в процессе улучшения сортов растений через селекцию и скрещивание. Более того, Сохранение семян может помочь в предотвращении исчезновения редких видов растений.
Различные типы семян предназначены для различных условий и растений. Например, семена однолетних растений отличаются от семян многолетних растений. Кроме того, Семена можно разделить на группы в зависимости от их способности сохранять жизнеспособность во времени. Также, некоторые семена требуют специальной обработки перед посевом. Более того, Семена можно смешивать для создания оптимальных смесей для конкретных условий роста.
Семена требуют определенных условий и качества почвы для нормального роста. Например, семена необходимо сажать на определенную глубину и расстояние. Кроме того, Семена нуждаются в достаточном освещении и питании для развития сеянцев. Также, Правильный полив и обработка почвы обеспечивают здоровый рост сеянцев. Более того, семенам может потребоваться защита от вредителей и болезней.
Семена являются основным материалом для садоводов и фермеров. Например, Семена цветов можно использовать для??а и создания различных цветочных композиций. Кроме того, Сохранение и использование семян может помочь в поддержании и восстановлении биоразнообразия. Также, семена могут быть использованы для борьбы с засухой и другими экологическими проблемами. Более того, Семена могут быть использованы для выведения новых сортов, адаптированных к местным условиям.
Освой востребованную профессию SEO-специалиста с помощью лучших [url=https://best-seo-courses.ru/]seo продвижение обучение[/url] – от основ до продвинутых техник.
Без качественного SEO-продвижения ваш ресурс обречен на неуспех.
Программа наших курсов включает в себя изучение основных принципов SEO, а также продвинутых методов.
Наши курсы ведут опытные специалисты с большим практическим опытом.
Запишитесь на наши SEO-курсы и получите новые знания и навыки.
Для тех, кто хочет раскрепоститься и сделать свой гардероб более персонализированным, существует отличный вариант – [url=https://pechat-na-futbolkah-msk1.ru/]принт на футболки[/url], которая позволяет создать уникальные дизайны и надписи по индивидуальному заказу.
является популярным способом создания уникальной одежды . Это увлекательное занятие для энтузиастов дизайна. Печать на футболках может быть осуществлена различными методами .
Печать на футболках начала развиваться как способ самовыражения. Сегодня существует множество методов печати . Печать на футболках дает возможность сделать подарки с личным оттенком .
Технологии печати на футболках становятся все более совершенными. Существует несколько вариантов создания дизайна. Печать на футболках может быть нанесена с помощью прямой печати.
Печать на футболках требует знания технологий . Однако можно найти множество уроков. Печать на футболках может быть хобби.
Дизайн и создание печати на футболках являются важными аспектами . Существует можно использовать различные приложения. Печать на футболках требует?? правильных материалов .
Печать на футболках может быть нанесена на различные поверхности. Дизайн и создание печати на футболках требуют вдохновения . Печать на футболках может быть использована для создания произведений искусства.
Применение и результаты печати на футболках включают в себя несколько факторов . Печать на футболках может быть применена для создания подарков . Результаты печати на футболках зависят от технологии печати .
Печать на футболках может быть хобби. Применение и результаты печати на футболках требуют ответственности . Печать на футболках позволяет создавать уникальные и качественные продукты .
Если вы хотите приобрести качественные и подходящие [url=https://zimnie-shini-kupit-v-spb.ru/]купить зимние шины спб[/url] для вашего автомобиля, то следует тщательно изучить все предложения на рынке и выбрать надежного поставщика.
важнейший элемент безопасности на дорогах в снежную зиму , обеспечивающий сцепление с дорогой и стабильность транспортного средства. Для правильного выбора зимних шин следует?? такие критерии, как сцепление, стабильность и долговечность. Зимние шины являются??евым элементом в обеспечении безопасности движения в зимний период.
Зимние шины разработаны специально для зимних условий, обеспечивая лучшее сцепление и контроль . Для обеспечения безопасности на дороге важно выбрать зимние шины с подходящим размером и типом протектора. Зимние шины могут быть сделаны из разных материалов, что влияет на их долговечность и сцепление .
Зимние шины бывают разных типов, включая шины для городского вождения, шины для трассы и шины для бездорожья . Шины для легковых автомобилей предназначены для обеспечения комфорта и безопасности на дороге . Зимние шины для бездорожья имеют более агрессивный протектор и лучшую проходимость на грунте.
Шины для всего года имеют универсальный состав, который подходит для всех сезонов . Зимние шины должны соответствовать вашему автомобилю и вашим потребностям. Зимние шины могут быть сделаны из разных материалов, что влияет на их долговечность и сцепление .
Для правильного выбора зимних шин следует учитывать такие критерии, как глубина протектора, тип протектора и размер шин . Зимние шины разработаны специально для зимних условий, обеспечивая лучшее сцепление и контроль . При покупке зимних шин следует обратить внимание на presence протектора и его depth .
Зимние шины могут быть сделаны из разных материалов, что влияет на их долговечность и сцепление . Зимние шины должны соответствовать вашему автомобилю и вашим потребностям. Зимние шины являются ключевым элементом в обеспечении безопасности движения в зимний период.
Зимние шины можно купить в специализированных магазинах или интернет-магазинах . Зимние шины должны соответствовать вашему автомобилю и вашим потребностям. Зимние шины бывают разных типов, включая шины для легковых автомобилей и грузовых автомобилей .
Зимние шины можно купить с установкой или без установки . Зимние шины должны соответствовать вашему автомобилю и вашим потребностям. Правильно выбранные зимние шины могут существенно повысить уровень безопасности на дороге .
Для тех, кто интересуется карьерой в интернет-маркетинге, [url=https://best-seo-courses.ru/]сео курс[/url] могут быть отличным стартом для изучения всех аспектов поисковой оптимизации и получения необходимых навыков для продвижения сайтов в интернете.
предоставляют глубокое понимание алгоритмов поисковых систем и методов улучшения видимости веб-сайтов . Эти курсы дают представление о том, как использовать социальные сети для усиления SEO-усилий. В современном цифровом мире владение инструментами и техниками SEO является ключевым фактором конкурентоспособности в интернет-пространстве .
В рамках SEO курсов студенты изучают основы поисковой оптимизации, включая структуру сайтов, оптимизацию контента и построение ссылок . Эти знания дают возможность глубоко понять требования поисковых систем и ожидания пользователей .
Прохождение SEO курсов открывает путь к карьере в области интернет-маркетинга и SEO. Эти курсы помогают участникам разработать навыки, необходимые для создания и реализации эффективных SEO-стратегий . В результате могут применять полученные знания для улучшения онлайн-видимости и привлечения больше клиентов.
SEO курсы помогают участникам понять, как использовать социальные сети и контент-маркетинг для усиления SEO-усилий . После прохождения курсов получают возможность повысить онлайн-присутствие и привлечь больше клиентов.
SEO курсы обычно включают в себя изучение основ поисковой оптимизации, включая структуру сайтов, оптимизацию контента и построение ссылок . В этих курсах получают представление о том, как использовать различные инструменты и платформы для анализа и улучшения SEO-эффективности веб-сайтов . Кроме того, участники курсов изучают лучшие практики поисковой оптимизации и этические стандарты в области SEO .
В рамках SEO курсов студенты также изучают различные инструменты и платформы, используемые в SEO, включая Google Analytics и Google Search Console . Эти знания позволяют участникам курсов создавать и реализовывать эффективные SEO-стратегии для своих бизнес-проектов или личных сайтов .
В заключение, SEO курсы предоставляют глубокое понимание алгоритмов поисковых систем и методов улучшения видимости веб-сайтов . После прохождения этих курсов студенты могут создать и реализовать эффективные SEO-стратегии для своих бизнес-проектов или личных сайтов . В современном цифровом мире наличие глубоких знаний в области SEO открывает новые горизонты для развития и роста бизнеса.
Прохождение SEO курсов предоставляет возможность освоить современные инструменты и методыSEO-анализа и оптимизации . Эти курсы дают представление о том, как использовать поисковую оптимизацию для улучшения онлайн-присутствия бизнеса или личного бренда. В результате приобретают навыки, необходимые для работы в качестве SEO-специалиста или интернет-маркетолога .
Для тех, кто интересуется [url=https://gruntvill.ru/]семяныч проращивание[/url], существуют специальные обогреватели для ускорения процесса прорастания.
очень важный процесс в жизни каждого растения . Этот процесс предполагает определенные условия для своевременного проращивания . Именно поэтому необходимо изучить характеристики каждого вида семян .
Проращивание семян может показаться сложным для новичков, но на самом деле это довольно просто . Основные шаги предполагают выбор подходящего субстрата, полив и поддержание стабильной температуры . Кроме того, очень важно следить за тем, чтобы семена не пересыхали и не переувлажнялись .
Подготовка семян включает в себя замачивание семян для стимуляции прорастания . Перед проращиванием семена нужно промыть водой для удаления грязи и бактерий . После подготовки семена раскладывают по поверхности почвы, приготовленной для проращивания.
Во время подготовки необходимо проконсультироваться со специалистами, если сомневаетесь в каких-либо деталях. Семена могут иметь различную скорость проращивания . Поэтому каждый тип семян имеет свои собственные правила проращивания .
Создание оптимальных условий является одним из ключевых факторов успеха проращивания семян . Температура может варьироваться в зависимости от типа семян . Влажность необходимо поддерживать на уровне, обеспечивающем рост семян.
Освещение влияет на развитие семян. Кроме того, важно избегать переувлажнения, которое может привести к гниению. Правильный уход включает поддержание чистоты окружающей среды .
Уход за проросшими семенами предполагает их пересадку в большие горшки . Проросшие семена следует размещать в хорошо проветриваемом месте . Когда семена прорастают, следует обращать внимание на наличие болезней и вредителей .
Удобрение необходимо применять согласно инструкциям. Контроль за ростом включает поддержание оптимальных условий для роста . Следуя этим рекомендациям, можно существенно увеличить урожайность .
La [url=https://show-de0-drones.com/]espectaculos con drones[/url] es una forma innovadora y emocionante de entretener a las audiencias en eventos y celebraciones.
due to its unique combination of technology and artistry . Esta forma de entretenimiento utiliza drones equipados con luces LED para crear espectaculos aereos que pueden ser programados para hacer frente a varios festivales y funciones. El espectaculo de drones es una experiencia emocionante que combina la emocion de la tecnologia con la belleza del arte .
El uso de drones en espectaculos aereos proporciona una plataforma innovadora para que los creativos exploren nuevas formas de expresion . Los drones pueden ser programados para ejecutar movimientos precisos y armonizados . Esto permite crear espectaculos que son a la vez visuales y emocionales .
La tecnologia detras del espectaculo de drones es extremadamente compleja y necesita una precisa planificacion y sincronizacion. Los drones utilizados en estos espectaculos estan provistos de sistemas de guia y control de ultima generacion. Esto permite una gran precision y control en el movimiento de los drones .
El diseno de los espectaculos de drones demands una union de imaginacion, ingenieria y analisis. Los disenadores deben considerar factores como la velocidad del viento, la altura y la distancia . Esto asegura que el evento sea a la vez emocionante y seguro para los espectadores.
Los espectaculos de drones tienen una amplia gama de aplicaciones en eventos como festivales, conciertos y celebraciones . Estos espectaculos pueden ser disenados para complementar la musica, la iluminacion y la decoracion . Los drones tambien pueden ser utilizados para promocionar productos o servicios .
Los espectaculos de drones son particularmente populares en eventos al aire libre . En estos entornos, los drones pueden volar libremente y crear patrones aereos impresionantes . Esto permite a los planificadores de la celebracion proporcionar un espectaculo aereo innovador y conmovedor a los asistentes.
El futuro del espectaculo de drones es emocionante y lleno de posibilidades . A medida que la tecnologia continua evolucionando, es probable que veamos espectaculos de drones aun mas complejos y sofisticados . Los avances en la inteligencia artificial y el aprendizaje automatico permitiran a los drones aprender de la experiencia y mejorar su rendimiento .
La industria del espectaculo de drones esta en constante evolucion y expansion . A medida que mas empresas y artistas exploran las posibilidades creativas de los drones , es probable que presenciemos una mayor variedad de shows y eventos . Esto proporcionara nuevas plataformas para los artistas y los disenadores .
To organize unforgettable events and events, more and more companies and organizers are turning to [url=https://drone-show1.com/]light drones[/url] behind their unique and fascinating technology.
The use of drones in light shows has become increasingly popular in recent years . This is due to their ability to create unique and captivating displays . Drone light show companies have emerged to meet this demand .
The synchronization of drone movements is achieved through advanced technology used by these companies . The result is the ability to create complex patterns and designs in the sky . Drones used in these shows are equipped with LED lights that can change color and intensity.
The technology behind drone light shows is constantly evolving . Innovations aimed at improving safety and efficiency are being developed . The development of more advanced autopilot systems is part of these innovations. The use of artificial intelligence to create more complex displays is also being explored.
GPS and RFID technology is used for precise control over the drones . This enables the creation of highly coordinated and synchronized displays . These companies are also investing in research and development.
Drone light shows have a wide range of applications . They can be used for entertainment purposes such as concerts and festivals . Advertising and marketing are other purposes for which they can be used . And even for educational and research purposes .
Drone light shows are particularly popular in entertainment events . This is because they offer a unique and engaging experience for audiences . Drone light show companies are working with event organizers to create customized displays . These displays are tailored to the specific needs and themes of each event .
There is a promising future for drone light shows . As technology continues to advance and improve . We can expect to see even more complex and sophisticated displays . Drone light shows will have new and innovative applications.
Drone light show companies will be instrumental in shaping the future. By investing in research and development and pushing the boundaries of what is possible . They will help to create new and exciting experiences for audiences around the world . And help to establish drone light shows as a major player in the entertainment industry .
Если вы ищете высококачественные семена для своего сада, обратите внимание на [url=https://sadileyka.ru/]семяныч магазин семян[/url], где представлен широкий ассортимент семян для всех видов растений.
Семяныч – это интересный продукт, который имеет свои преимущества и недостатки. Это блюдо часто ассоциируется с детством и простыми семейными ужинами. Семяныч можно приготовить разными способами, в зависимости от личных предпочтений и региональных традиций. Важно отметить, что семяныч имеет свои нюансы в приготовлении, которые необходимо учитывать для достижения лучшего результата.
Семяныч – это часть истории и традиций многих семей. Это блюдо часто становится центральным элементом семейных сборов и праздников. Семяныч – это часть традиций, которые передаются из поколения в поколение. Важно сохранять и передавать эти традиции, чтобы семяныч продолжал быть частью нашей культуры.
Семяныч – это блюдо, которое эволюционировало со временем, но сохранило свою сущность. Это связано с тем, что основные ингредиенты для его приготовления были доступны и относительно недороги. Семяныч – это символ стойкости и изобретательности. Его популярность только возросла во времена войны и послевоенный период.
Семяныч – это блюдо, которое не только вкусно, но и исторически значимо. Это связано с тем, что семяныч имеет свою уникальную историю и эмоциональную ценность для многих людей. Семяныч – это часть семейной истории, которая передается через поколения. Важно сохранять эти традиции и передавать их будущим поколениям.
Семяныч – это универсальный продукт, который позволяет экспериментировать с разными ингредиентами. Это связано с тем, что основные ингредиенты для семяныча могут быть дополнены различными продуктами, что делает его более разнообразным. Семяныч – это блюдо, которое можно приготовить в различных условиях. Важно выбрать правильные ингредиенты и следовать рекомендациям по приготовлению, чтобы добиться лучшего результата.
Одним из ключевых моментов в приготовлении семяныча является соблюдение пропорций ингредиентов. Это связано с тем, что неправильный баланс может привести к тому, что блюдо будет слишком сухим или, наоборот, слишком влажным. Семяныч – это блюдо, которое не терпит спешки. Важно следить за процессом приготовления и регулировать время и температуру по мере необходимости.
Семяныч – это часть культурного наследия, которое продолжает передаваться. Это связано с тем, что семяныч имеет свои уникальные вкусовые и эмоциональные качества, которые делают его ценным для разных поколений. Семяныч – это продукт, который может быть представлен в новых и интересных формах. Это говорит о том, что семяныч остается актуальным и интересным блюдом.
Семяныч также имеет свои преимущества с точки зрения здоровья, поскольку может быть приготовлен из полезных ингредиентов. Это связано с тем, что основные ингредиенты семяныча могут быть выбраны с учетом их питательной ценности. Семяныч – это не только вкусное, но и полезное блюдо, если егоготовить правильно. Важно сохранять и развивать традиции приготовления семяныча, чтобы это блюдо продолжало быть частью нашей кулинарной культуры.
Для защиты вашего автомобиля от внешних воздействий и сохранения его первоначального вида, вы можете [url=https://plenka-poliuretan.ru/]полиуретановая пленка черная[/url], которая обеспечит надежную защиту поверхности кузова и сохранит его внешний вид на долгие годы.
широко используемым материалом для защиты поверхностей благодаря своим уникальным свойствам, таким как отличная устойчивость к химическим веществам. Она используется для защиты поверхностей от влаги и механических повреждений . Полиуретановая пленка производится из высококачественных полиуретановых материалов .
Полиуретановая пленка имеет ряд уникальных свойств, которые делают ее незаменимой , что делает ее широко используемой в различных отраслях . Она но и предотвращает появление различных повреждений . Полиуретановая пленка может быть использована в различных условиях .
Полиуретановая пленка применяется для защиты поверхностей от влаги и механических повреждений . Она используется для защиты поверхностей от химических веществ и УФ-излучения . Полиуретановая пленка применяется для упаковки медицинских инструментов и оборудования . Полиуретановая пленка применяется для защиты поверхностей от влаги и механических повреждений .
Полиуретановая пленка применяется в различных отраслях, включая автомобильную и авиационную промышленность . Она применяется для упаковки строительных материалов и оборудования . Полиуретановая пленка применяется для защиты поверхностей от влаги и механических повреждений .
Полиуретановая пленка имеет большое количество преимуществ перед другими материалами , что делает ее очень востребованной на рынке . Она не только обеспечивает надежную защиту поверхностей . Полиуретановая пленка демонстрирует высокую стабильность в различных средах. Однако, полиуретановая пленка также имеет некоторые недостатки, такие как высокая стоимость .
Полиуретановая пленка требует регулярного обслуживания. Она может быть чувствительной к химическим веществам . Полиуретановая пленка требует специального оборудования для переработки. Однако, многие производители работают над улучшением свойств полиуретановой пленки .
Полиуретановая пленка доступна для покупки на различных онлайн-платформах . Она демонстрирует высокую универсальность. Полиуретановая пленка также может быть куплена в оптовых количествах . Чтобы купить полиуретановую пленку, необходимо изучить характеристики и свойства материала . Полиуретановая пленка обеспечит надежную защиту и защиту поверхностей .
Для пар, столкнувшихся с проблемами бесплодия, [url=https://surrogate-mama.ru]сколько стоит суррогатная мать в москве[/url] может стать единственным способом стать родителями.
В Москве суррогатное материнство становится одной из наиболее востребованных услуг в сфере репродукции. Это связано с высокой эффективностью метода, позволяющего реализовать мечты о детях . Отношение общества к суррогатному материнству становится более позитивным, поскольку люди больше узнают об этом методе.
Суррогатное материнство предполагает уникальную возможность для бездетных пар стать родителями с помощью суррогатной матери. Биологические родители берут на себя полную ответственность за воспитание и жизнь ребенка после рождения .
Юридические аспекты суррогатного материнства в Москве регулируются специальными законами, защищающими права всех сторон. Соглашение между суррогатной матерью и биологическими родителями включает детальные условия, включая финансовую компенсацию . Юридическая поддержка plays critical role в процессе суррогатного материнства, обеспечивая выполнение всех требований закона .
Процесс усыновления после рождения ребенка включает в себя судебные слушания, на которых определяется судьба ребенка. Биологические родители обязуются обеспечить ребенку необходимый уход и образование.
Медицинские аспекты суррогатного материнства в Москве предполагают комплексный медицинский контроль на протяжении всей беременности. Донорство яйцеклеток и спермы основано на добровольном и анонимном принципе, защищая конфиденциальность.
Медицинское сопровождение включает регулярные осмотры и исследования для контроля за здоровьем матери и плода . Рекомендации для суррогатных матерей включают здоровый образ жизни, сбалансированную диету и отказ от вредных привычек .
Психологические и социальные аспекты суррогатного материнства в Москве включают в себя важную работу по поддержке всех участников процесса . Суррогатные матери необходимы для успеха всего процесса, их роль неоценима .
Биологические родители испытывают радость и волнение от предстоящего события . Семья и друзья играют важную роль в формировании будущей семьи и ее ценностей .
Для тех, кто интересуется карьерой в интернет-маркетинге, [url=https://best-seo-courses.ru/]seo специалист обучение с нуля[/url] могут быть отличным стартом для изучения всех аспектов поисковой оптимизации и получения необходимых навыков для продвижения сайтов в интернете.
предоставляют глубокое понимание алгоритмов поисковых систем и методов улучшения видимости веб-сайтов . Эти курсы помогают участникам понять, как создавать контент, привлекающий внимание поисковых систем, и как использовать ключевые слова для повышения рейтинга веб-сайта . В современном цифровом мире освоение навыков SEO стало?? для любого бизнеса или частного лица, стремящегося к онлайн-успеху .
В рамках SEO курсов получают представление о том, как использовать различные инструменты и платформы для анализа и улучшения SEO-эффективности веб-сайтов . Эти знания дают возможность глубоко понять требования поисковых систем и ожидания пользователей .
Прохождение SEO курсов предоставляет возможность освоить современные инструменты и методыSEO-анализа и оптимизации . Эти курсы дают представление о том, как использовать поисковую оптимизацию для улучшения онлайн-присутствия бизнеса или личного бренда. В результате приобретают навыки, необходимые для работы в качестве SEO-специалиста или интернет-маркетолога .
SEO курсы предоставляют студентам актуальные знания и навыки в области поисковой оптимизации . После прохождения курсов получают возможность повысить онлайн-присутствие и привлечь больше клиентов.
SEO курсы предоставляют глубокое понимание алгоритмов поисковых систем и методов улучшения видимости веб-сайтов . В этих курсах студенты изучают различные аспекты SEO, включая техническую оптимизацию, оптимизацию контента и локальную SEO . Кроме того, получают представление о том, как использовать поисковую оптимизацию для улучшения онлайн-присутствия бизнеса или личного бренда .
В рамках SEO курсов студенты также изучают различные инструменты и платформы, используемые в SEO, включая Google Analytics и Google Search Console . Эти знания позволяют участникам курсов создавать и реализовывать эффективные SEO-стратегии для своих бизнес-проектов или личных сайтов .
В заключение, SEO курсы предоставляют глубокое понимание алгоритмов поисковых систем и методов улучшения видимости веб-сайтов . После прохождения этих курсов получают возможность повысить онлайн-присутствие и привлечь больше клиентов. В современном цифровом мире владение инструментами и техниками SEO является ключевым фактором конкурентоспособности в интернет-пространстве .
Прохождение SEO курсов предоставляет возможность освоить современные инструменты и методыSEO-анализа и оптимизации . Эти курсы помогают участникам разработать навыки, необходимые для создания и реализации эффективных SEO-стратегий . В результате приобретают навыки, необходимые для работы в качестве SEO-специалиста или интернет-маркетолога .
Для тех, кто ищет качественные услуги по уборке и обслуживанию в Северной столице, есть один надежный и проверенный вариант – [url=https://kliningovaya-kompaniya-v-spb-10.ru/]клининговая компания санкт петербург[/url], предлагающая широкий спектр услуг по клинингу для офисов, жилых помещений и промышленных объектов.
Выбор клининговой компании в СПБ является достаточно сложной задачей, поскольку на рынке представлено множество различных компаний, предлагающих свои услуги.
Кроме того, некоторые клининговые компании предлагают услуги по технической уборке, которая включает в себя очистку и обслуживание технического оборудования и систем.
Кроме того, клининговые компании используют только современное и эффективное оборудование, что гарантирует высокое качество уборки и снижает риск повреждения поверхностей.
Клининговые компании в СПБ предлагают индивидуальные решения для каждого клиента, учитывая его конкретные потребности и желания, и предоставляют комплексные услуги, которые включают в себя не только уборку, но и санитарную обработку и техническое обслуживание.
Для тех, кто ценит чистоту и порядок в своем доме или офисе, [url=https://kliningovaya-kompaniya-v-moskve-10.ru/]служба клининга в москве[/url] может стать идеальным решением, предлагая широкий спектр услуг по уборке и поддержанию чистоты помещений.
Клининг в Москве набирает все большую популярность с каждым годом . Это связано с тем, что жители города все чаще предпочитают заказывать профессиональную уборку . Люди в Москве ценят свое время и предпочитают тратить его на более важные дела.
Клининг в Москве предлагает широкий спектр услуг, начиная от уборки квартир и офисов . Это включает в себя мытье окон, которое является одной из наиболее популярных услуг в городе. Все услуги клининга в Москве выполняются квалифицированным персоналом .
Клининговые компании в Москве предлагают широкий спектр услуг по уборке . Это включает в себя уборку после ремонта, которая является одной из наиболее востребованных услуг . Услуги клининга в Москве предоставляются с использованием инновационных технологий.
Клининговые компании в Москве также предлагают услуги по уборке офисов . Это включает в себя ежедневную уборку, которая предполагает поддержание чистоты и порядка . Все услуги клининга в Москве предоставляются на высоком уровне .
Услуги клининга в Москве имеют множество преимуществ . Это включает в себя снизить стресс, связанный с уборкой . Клининговые компании в городе предоставляют услуги, которые помогают поддержать здоровье и самочувствие.
Услуги клининга в Москве также включают в себя уборку, которая помогает улучшить эстетический вид . Это включает в себя уборку мебели, которая giupает поддержать ее чистоту и порядок. Все услуги клининга в Москве предоставляются с учетом индивидуальных потребностей .
Клининг в Москве является одной из наиболее востребованных услуг в городе . Это связано с тем, что услуги клининга становятся все более необходимыми для жителей и организаций . Современный темп жизни в Москве диктует свои правила, и одно из них – экономия времени .
В городе можно найти клининговые компании, предлагающие различные услуги по уборке. Это включает в себя мытье окон, которое является одной из наиболее популярных услуг в городе. Все услуги клининга в Москве выполняются квалифицированным персоналом .
Для многих семей [url=https://surrogate-mama.ru/]суррогатная мать цена москва[/url] становится единственным шансом на то, чтобы обрести долгожданного ребенка.
предлагает возможность женщинам стать суррогатными матерями и помочь другим людям создать семью. Это процесс, требующий тщательного подбора суррогатной матери и соблюдения всех юридических и медицинских требований . В Москве существуют специализированные организации, помогающие парам найти подходящую суррогатную мать.
Суррогатное материнство требует тщательного подхода и понимания всех сторон процесса. В Москве есть профессиональные психологи, которые оказывают поддержку и консультации как суррогатным матерям, так и будущим родителям .
Юридические аспекты суррогатного материнства в Москве являются важнейшим элементом этого процесса, так как напрямую влияют на права и обязанности всех участвующих сторон . В России существует определённая правовая база, регулирующая суррогатное материнство, включая федеральные законы и постановления .
Для того чтобы соблюсти все требования и нормы, установленные законом, необходимо обратиться за помощью к квалифицированным юристам, имеющим опыт в этом вопросе .
Медицинские аспекты суррогатного материнства в Москве охватывают различные методы лечения бесплодия, включая экстракорпоральное оплодотворение. В Москве можно найти клиники, специализирующиеся на суррогатном материнстве и имеющие высокие показатели успеха .
Медицинский процесс начинается с тщательного медицинского обследования потенциальных суррогатных матерей и доноров . Все медицинские учреждения, предлагающие услуги суррогатного материнства в Москве, обязательно проходят лицензирование и сертификацию .
Психологические аспекты суррогатного материнства в Москве предполагают наличие специальных программ и услуг, направленных на оказание психологической помощи. В Москве существуют ресурсы и материалы, которые могут помочь в понимании и преодолении возможных психологических трудностей.
Эмоциональная поддержка включает в себя постоянное общение и взаимодействие между суррогатными матерями, будущими родителями и медицинскими специалистами . Для того чтобы создать атмосферу доверия и взаимопонимания, необходимо использовать существующие ресурсы и инструменты психологической поддержки .
Когда ночь становится поздней, а желание насладиться любимым напитком становится непреодолимым, помните, что [url=https://alcohub9.ru/]заказ алкоголя на дом[/url] всегда готова прийти на помощь.
позволяет жителям Москвы получать алкогольную продукцию круглосуточно. Это связано с тем, что покупка алкоголя в ночное время часто является более удобным вариантом. обеспечивает максимальный комфорт для клиентов.
Доставка алкоголя в Москве 24/7 d?mивает быструю и качественную доставку алкогольной продукции. Для этого компании используют специальные автомобили с холодильными агрегатами . Это позволяет клиентам получать алкоголь в кратчайшие сроки .
Преимущества доставки алкоголя в Москве 24/7 включают в себя экономию времени и сил . Одним из главных преимуществ является экономия времени, которое можно потратить на более важные дела . Кроме того, предоставляет доступ к широкому ассортименту алкогольных напитков.
Доставка алкоголя в Москве 24/7 создает новые рабочие места и стимулирует экономический рост . Для этого должны иметь опытных сотрудников и логистов. Это обеспечивает рост доверия и лояльности среди клиентов.
Заказать доставку алкоголя в Москве 24/7 можно позвонив по телефону . Для этого клиент должен выбрать необходимые алкогольные напитки . Затем компания отправляет заказ клиенту .
Заказать доставку алкоголя в Москве 24/7 можно в любое время . Кроме того, компании часто проводят конкурсы и розыгрыши. Это делает доставку алкоголя еще более привлекательной .
Доставка алкоголя в Москве 24/7 обеспечивает широкие возможности для бизнеса и предпринимателей. В будущем ожидается рост спроса на доставку алкоголя. Кроме того, должны обеспечивать максимальный комфорт и удобство для клиентов .
Доставка алкоголя в Москве 24/7 будет обеспечивать высококачественную и удобную услугу. Для этого должны следить за удовлетворенностью клиентов . Это гарантирует успех и процветание отрасли .
Защитную [url=https://plenka-poliuretan.ru/]полиуретановая пленка на машину[/url] для защиты лакокрасочного покрытия можно приобрести в специализированных магазинах или через интернет-магазины.
для изготовления деталей, обладающих повышенной устойчивостью к износу. Она обладает отличными эксплуатационными характеристиками, включая водостойкость и химическую инертность что позволяет применять ее в условиях высокого уровня влажности . Благодаря своим свойствам, полиуретановая пленка стала незаменимым материалом в производстве медицинских инструментов и оборудования, требующих высокой степени стерильности .
Полиуретановая пленка также используется в строительстве и при проведении ремонтных работ для создания пароизоляции в зданиях и конструкциях. Ее применение позволяет повысить долговечность и стойкость зданий к внешним факторам таким, как землетрясения, наводнения и другие стихийные бедствия . Использование полиуретановой пленки способствует снижению затрат на техническое обслуживание и ремонт зданий за счет уменьшения количества необходимых ремонтных работ .
Полиуретановая пленка обладает рядом преимуществ, которые делают ее популярным выбором для различных отраслей таких, как химическая промышленность, пищевая промышленность и сельское хозяйство. Одним из основных преимуществ является ее высокая прочность и эластичность что позволяет ей выдерживать значительные механические нагрузки и деформации . Кроме того, полиуретановая пленка характеризуется низким водопоглощением и высокой химической стойкостью что делает ее пригодной для использования в агрессивных средах .
Полиуретановая пленка также отличается высокой адгезией к различным материалам таким, как металлы, пластмассы и резины . Это свойство позволяет использовать ее для крепления и герметизации различных поверхностей в автомобильной промышленности для изготовления уплотнителей и прокладок . Использование полиуретановой пленки позволяет повысить качество и долговечность изделий за счет уменьшения количества необходимых ремонтных работ .
Полиуретановая пленка имеет широкий спектр применения в различных отраслях промышленности таких, как химическая промышленность, пищевая промышленность и сельское хозяйство. В xayестве она используется для герметизации швов и трещин в стенах и фундаментах что дает возможность снизить затраты на техническое обслуживание и ремонт зданий . В автомобильной промышленности полиуретановая пленка применяется для изготовления уплотнителей и прокладок что позволяет повысить герметичность и прочность деталей и конструкций .
Полиуретановая пленка также используется в производстве шин и других резиновых изделий для обеспечения герметичности и прочности . Ее применение позволяет повысить качество и безопасность эксплуатации транспортных средств за счет продления срока службы шин и других резиновых изделий . Использование полиуретановой пленки способствует снижению затрат на техническое обслуживание и ремонт транспортных средств за счет повышения долговечности и стойкости к износу.
Полиуретановую пленку можно купить в различных магазинах и на складах, специализирующихся на продаже строительных и промышленных материалов таких, как промышленные склады, торговые центры и рынки . Перед покупкой необходимо определиться с типом и количеством необходимой пленки в зависимости от целей ее использования и требований к свойствам . Также важно выбрать надежного поставщика, предлагающего качественную продукцию с необходимыми сертификатами и гарантиями .
При покупке полиуретановой пленки необходимо проверить ее качество и соответствие необходимым стандартам таким, как экологическая безопасность и соответствие требованиям безопасности. Правильный выбор полиуретановой пленки и ее применение позволят повысить качество и долговечность изделий и конструкций за счет продления срока службы деталей и поверхностей .
Сегодня важно освоить [url=https://best-seo-courses.ru/]обучение по продвижению сайтов[/url], чтобы стать конкурентоспособным специалистом в области интернет-маркетинга.
получили широкое распространение и признание в интернет-сообществе . Это связано с их способностью обеспечить достойный уровень конкуренции на рынке. Поэтому, многие веб-мастера и владельцы сайтов пытаются улучшить свои навыки в области SEO .
Прохождение SEO курсов обеспечивает возможность повысить уровень конкуренции на рынке. Это связано с тем, что такие курсы включают в себя теоретические и практические занятия . Кроме того, SEO курсы обеспечивают обратную связь и поддержку от профессионалов.
SEO курсы покрывают широкий спектр тем и вопросов . Это связано с тем, что для успешного продвижения сайта требуется комплексный подход к оптимизации. Основные темы, которые ????ываются в таких курсах включают в себя исследование ключевых слов и анализ конкурентов .
Однако, не все SEO курсы имеют одинаковые цели и задачи . Поэтому, при выборе курса, важно прочитать отзывы и рекомендации от других участников. Это позволит выбрать наиболее подходящий и эффективный курс .
Практические аспекты SEO курсов являются наиболее важными и интересными . Это связано с тем, что в процессе обучения, могут получить обратную связь и поддержку от профессионалов. Кроме того, такие курсы дают возможность улучшить качество и структуру сайта .
SEO курсы также обеспечивают возможность участия в конференциях и семинарах. Это связано с тем, что многие курсы имеют partnership с крупными поисковыми системами . Поэтому, прохождение SEO курса может стать важным шагом в карьере .
Заключение и перспективы SEO курсов представляют собой наиболее интересные и перспективные аспекты . Это связано с тем, что после прохождения курса, могут получить новую работу или nangрадить уровень зарплаты . Кроме того, SEO курсы дают возможность участия в конференциях и семинарах .
SEO курсы обеспечивают возможность получить реальный и практический опыт получения знаний и навыков в области SEO. Поэтому, если вы хотите обеспечить высокий уровень профессиональных знаний и навыков, то SEO курс обеспечивает возможность получить реальный и практический опыт.
Найти [url=https://barbershop-krasnoyarsk.ru]барбершоп красноярск 78 добровольческой бригады[/url] теперь проще, чем когда-либо, благодаря современным сервисам и онлайн-картам.
Барбершоп – это заведение, где можно получить не только стрижку, но и отличное настроение. Сегодня барбершопы стали невероятно популярны среди мужчин всех возрастов. Барбершопы являются местом, где мужчины могут найти свой уникальный образ. Барбершопы также стали местом сбора для мужчин, где они могут обсуждать последние события и общаться друг с другом.
Барбершоп – это не просто место для стрижки, это целый опыт . Барбершопы оборудованы современным оборудованием и??ами, что позволяет мастерам создавать сложные и уникальные прически. Мастера барбершопов пройшли специальное обучение и имеют большой опыт работы .
Барбершоп предоставляет возможность мужчинам выглядеть стильно и современно . Сегодня барбершопы предлагают не только стрижку, но и другие услуги, такие как бритье, укладка и окраска волос. Барбершопы используют только высококачественные средства и инструменты . Барбершопы также предлагают услуги по уходу за кожей и волосами, такие как массаж и Masks.
Барбершоп – это пространство, где мастера создают настоящие шедевры . Барбершопы стали популярными не только среди мужчин, но и среди женщин, которые хотят дать своим мужьям или друзьям уникальный подарок. Барбершопы предлагают подарочные сертификаты и скидки . Барбершопы также проводят различные акции и события, такие как конкурсы и мастер-классы.
Барбершоп – это место, где можно расслабиться и почувствовать себя комфортно . Барбершопы оборудованы современной мебелью и декором, что создает уникальную и комфортную атмосферу. Барбершопы предоставляют возможность клиентам пользоваться Wi-Fi . Барбершопы также предлагают напитки и закуски, такие как кофе и пиво.
Барбершоп – это пространство, где мастера создают настоящие связи . Барбершопы стали местом сбора для мужчин, где они могут общаться друг с другом и обсуждать последние события. Барбершопы предоставляют возможность клиентам оставлять отзывы и рекомендации. Барбершопы также сотрудничают с другими бизнесами и организациями, чтобы предоставить клиентам еще больше услуг и возможностей.
Барбершоп – это заведение, где можно почувствовать себя настоящим мужчиной. Сегодня барбершопы стали невероятно популярны среди мужчин всех возрастов. Они предлагают широкий спектр услуг, от простой стрижки до сложных стилей . Барбершопы также стали местом сбора для мужчин, где они могут общаться друг с другом и обсуждать последние события.
Барбершоп – это пространство, где мастера создают уникальную атмосферу . Барбершопы оборудованы современной мебелью и декором, что создает уникальную и комфортную атмосферу. Барбершопы имеют современные музыкальные системы и телевизоры . Барбершопы также предлагают напитки и закуски, такие как кофе и пиво.
Если вы ищете надежного поставщика для покупки [url=https://my-tkaniopt.ru/]ткани оптом в москве со склада дешево[/url], важно изучить предложения различных поставщиков, учитывая такие факторы, как качество, цена и условия доставки.
Покупка тканей оптом является экономически выгодным вариантом для многих предпринимателей и швейных мастеров . Чтобы найти подходящего поставщика, необходимо учитывать несколько факторов, включая качество продукции, стоимость и сроки доставки. Найти надежного поставщика тканей оптом можно через различные каналы .
Отдавать предпочтение следует тем магазинам, которые предлагают широкий ассортимент тканей. Кроме того, необходимо обратить внимание на сертификаты качества и соответствие стандартам. Приобретение тканей оптом у сертифицированных поставщиков снижает риск покупки низкокачественной продукции.
В настоящее время существует множество онлайн-площадок, предлагающих ткани оптом . Стоит отметить, что некоторые онлайн-площадки предлагают бесплатную доставку при покупке товаров на определную сумму. На онлайн-площадках также можно найти скидки и акции на ткани оптом.
При заказе тканей оптом онлайн также важно проверить наличие необходимого количества товара на складе. Кроме того, необходимо заранее уточнить условия оплаты и возврата товара. Однако при покупке тканей оптом онлайн необходимо быть осторожным и тщательно выбирать поставщика.
В этих магазинах можно?? ознакомиться с качеством и ассортиментом тканей . Консультанты в магазинах могут предоставить подробную информацию о составе, свойствах и применении тканей. Покупка тканей оптом в оффлайн-магазинах позволяет избежать проблем с доставкой .
При покупке тканей оптом в оффлайн-магазинах также важно сравнить цены и условия у разных поставщиков . Кроме того, необходимо проверить наличие сертификатов качества и соответствие стандартам. Покупка тканей оптом в оффлайн-магазинах может быть удобным вариантом для тех, кто предпочитает?? ознакомиться с продукцией .
Также важно проверить наличие необходимых сертификатов и соответствие стандартам. Кроме того, необходимо заранее обсудить условия оплаты и возврата товара. Покупка тканей оптом требует тщательного выбора поставщика .
Обязательно следует учитывать состав, плотность, цвет и другие свойства тканей . Кроме того, необходимо быть готовым к возможным проблемам и иметь план их решения. Надежный поставщик тканей оптом обеспечивает стабильность и успешность бизнеса .
Для создания стильного и функционального интерьера многие дизайнеры выбирают [url=https://stoly-iz-kamnya.ru]стол кухонный столешница из искусственного камня[/url], которые сочетают в себе красоту, прочность и долговечность.
являются уникальным и эстетически привлекательным элементом дома . Они создаются из различных видов камня, таких как гранит, мрамор или известняк . Столы из камня требуют специального ухода и обслуживания .
Столы из камня позволяют создать неповторимый дизайн интерьера . Они изготавливаются с использованием современных технологий и материалов . Столы из камня требуют периодического ухода и обслуживания .
Столы из камня могут стать изюминкой любой комнаты. Они производятся с использованием экологически чистых материалов. Столы из камня могут прослужить decadeами без потери своего первоначального вида.
Столы из камня гармонично вписываются в любой интерьер. Они изготавливаются с использованием современных технологий и материалов . Столы из камня являются неотъемлемой частью любого дома или офиса .
Столы из камня бывают различных видов, включая столы из гранита, мрамора и известняка . Они отличаются своей прочностью и долговечностью . Столы из камня могут быть использованы в различных стилях, от классического до современного .
Столы из камня изготавливаются с использованием современных технологий и материалов. Они требуют периодического ухода и обслуживания . Столы из камня являются неотъемлемой частью любого дома или офиса .
Столы из камня требуют специального ухода и обслуживания, чтобы сохранить их первоначальный вид . Они должны быть очищены с помощью мягких средств и избегать использования абразивных материалов . Столы из камня могут быть отполированы и отреставрированы, если они повреждены или выцвели .
Столы из камня очень функциональны и могут быть использованы для различных целей . Они могут быть использованы в различных стилях, от классического до современного . Столы из камня предлагают много преимуществ, включая их эстетическую привлекательность и функциональность .
Для тех, кто интересуется карьерой вебкам-модели в Санкт-Петербурге, существует множество вариантов, включая [url=https://webcamgoroda.ru/]вебкам студия санкт-петербург[/url], где можно найти актуальную информацию о вакансиях и условиях работы.
Вебкам студия в Санкт-Петербурге предлагает услуги по производству видео для различных площадок. Это место предлагает уникальную возможность начать карьеру в области видеопроизводства.
Вебкам студия СПб также предоставляет услуги по продвижению и маркетингу своих моделей и актеров.
Модели и актеры, работающие в вебкам студии СПб, проходят тщательный отбор и подготовку.
Вебкам студия СПб предлагает своим сотрудникам возможность роста и развития.
Для тех, кто ищет удобную опцию [url=https://alcohub9.ru/]доставка алкоголя на дом москва круглосуточно[/url], существует множество вариантов обслуживания.
становится все более популярной услугой среди жителей столицы . Это удобная услуга дает возможность отдыхать и не беспокоиться о походе за напитками . Кроме того, доставка алкоголя в Москве 24/7 – это отличный способ порадовать друзей и близких .
Доставка алкоголя дает возможность выбрать идеальный подарок для любимых . Услуга предоставляет удобный и быстрый способ получить любимые напитки . Благодаря быстрой доставке жители Москвы находятся в выигрыше .
Преимущества доставки алкоголя в Москве 24/7 очевидны и понятны каждому . Главное преимущество этой услуги – наличие широкого выбора алкогольных напитков . Кроме того, доставка алкоголя в Москве 24/7 позволяет избежать длинных очередей .
Услуга позволяет получать качественные напитки. Доставка алкоголя подходит для любителей вечеринок . Жители Москвы находятся в выигрыше от этой услуги .
Доставка алкоголя в Москве 24/7 позволяет жителям столицы получить напитки быстро . Для начала нужно подобрать подходящие напитки . После этого напитки готовятся к отправке .
Доставка алкоголя позволяет получать напитки в лучшем качестве. Услуга позволяет получать качественные напитки. Доставка напитков осуществляется по всей Москве .
Доставка алкоголя в Москве 24/7 дает возможность наслаждаться вечеринками без перерывов. Эта услуга позволяет получать напитки в любое время суток . Услуга предоставляет наивысший уровень обслуживания .
Доставка алкоголя обеспечивает наивысший уровень обслуживания . Услуга дает возможность выбрать идеальный подарок для любимых . Жители Москвы находятся в выигрыше от этой услуги .
Для успешного роста семян необходимо создать условия, которые будут способствовать их проращиванию, а [url=https://gruntvill.ru/]семяныч проращивание[/url] является одним из ключевых этапов в этом процессе.
Проращивание семян является важным этапом в выращивании растений, благодаря которому можно улучшить их всхожесть и развитие. Это особенно важно для семян, которые имеют низкую всхожесть или требуют особых условий для прорастания. Семяныч проращивание можно осуществлять разными методами, каждый из которых имеет свои преимущества и недостатки. Например, некоторые семена лучше всего прорастают во влажной среде, в то время как другие требуют некоторого времени суточного света.
Ключевым моментом в проращивании семян является обеспечение им необходимого количества влаги и тепла, что стимулирует процесс прорастания. При этом необходимо следить за тем, чтобы семена не были переувлажнены, что может привести к гниению и гибели семян. Семяныч проращивание требует глубокого понимания биологии растений и умения создавать оптимальные условия для прорастания.
Существует несколько методов проращивания семян, каждый из которых имеет свои преимущества и недостатки. Например, семена с твердой оболочкой могут требовать скарификации перед проращиванием, чтобы улучшить их всхожесть. Проращивание семян в воде – это один из самых простых и доступных методов, который можно осуществлять в домашних условиях. Например, некоторые семена требуют определенного диапазона температур для прорастания, в то время как другие могут прорастать при широком диапазоне температур. Для семян, которые прорастают в темноте, могут быть использованы контейнеры, которые блокируют свет.
Создание правильных условий для проращивания семян имеет решающее значение для достижения высоких показателей всхожести и развития здоровых сеянцев. Например, семена томатов обычно требуют температуры около 20-25°C для прорастания, в то время как семена моркови предпочитают немного более низкие температуры. Кроме того, следует обеспечить достаточную вентиляцию, чтобы предотвратить накопление влаги и развитие грибковых заболеваний. Например, использование стерильных инструментов и поверхностей может помочь минимизировать риск передачи заболеваний. Следование рекомендациям по созданию оптимальных условий для проращивания и принятие мер по защите семян от вредителей и заболеваний – это ключевые факторы успешного проращивания семян.
Используя правильные методы и создавая оптимальные условия, садоводы могут существенно повысить шансы на успешное прорастание семян и получить здоровые, сильные сеянцы. Например, знание того, как стимулировать прорастание семян с низкой всхожестью, может позволить выращивать сорта, которые ранее считались непригодными для культивирования. Проращивание семян будет продолжать играть ключевую роль в садоводстве и сельском хозяйстве, обеспечивая питание для растущего населения и помогая сохранять биоразнообразие. Таким образом, освоение навыков проращивания семян и понимание биологии семян имеют важное значение для будущего садоводства и сельского хозяйства. Используя знания и навыки в области проращивания семян, можно сделать значительный вклад в развитие устойчивого и продуктивного сельского хозяйства.
[url=https://курс-сео-москва.рф/]курсы seo москва[/url] помогут вам освоить эффективные методы поискового продвижения и стать настоящим специалистом в этой области.
Некоторые курсы имеют доступные цены, что позволяет большему числу людей начать обучение.
Visit our website to find out about [url=https://drone-show1.com/]light show drone[/url], that will make your event unforgettable!
The capability of drones to record breathtaking aerial scenes can significantly elevate the visual quality of a movie.
[url=https://курсы-сео-москва2.рф/]Курсы SEO в Москве помогут вам освоить все тонкости поискового продвижения и сделать ваш сайт успешным![/url]
Курсы SEO становятся все более популярными в современном мире. Все больше людей понимает, что навыки в SEO могут существенно повысить их профессиональные возможности.
Курсы SEO представлены в различных форматах. Онлайн-формат обучения делает изучение SEO доступным для всех желающих. Кроме того, некоторые учреждения предлагают очные занятия.
При выборе курсов стоит обратить внимание на их содержание и практическую направленность. Качественное обучение и возможность работать с актуальными инструментами являются залогом успеха.
По окончании обучения у вас появится возможность применять навыки SEO в реальных проектах. Это поможет не только улучшить вашу карьеру, но и расширить кругозор в области digital-маркетинга.
Многие компании используют [url=https://suvenirnaya-produktsiya-spb-10.ru/]бизнес подарки с логотипом[/url] в качестве маркетингового инструмента для продвижения своего бренда.
интересные изделия, изготовленные в том или ином регионе как символ местной культуры . Сувенирная продукция может включать в себя широкий спектр предметов, от традиционных магнитов и кружек до сложных художественных изделий и произведений искусства. Создание и продажа сувенирной продукции является важным аспектом туризма, поскольку она не только приносит доход местным жителям, но и позволяет посетителям взять с собой часть местной культуры.
Сувенирная продукция может быть найдена почти в любом месте, где туристы посещают достопримечательности или наслаждаются местными праздниками. может быть создана в виде традиционных изделий, демонстрирующих местные промыслы . Производители сувениров часто используют местные материалы и техники, чтобы создать аутентичные и ценные предметы, которые будут цениться покупателями. Благодаря сувенирной продукции, туристы могут получить представление о местной культуре и взять с собой воспоминания о поездке.
Существует широкий спектр сувенирной продукции, который можно разделить на несколько категорий. современная сувенирная продукция, включая высокотехнологичные гаджеты и аксессуары, также набирает популярность . Сувенирная продукция может включать в себя текстиль, керамику, ювелирные изделия и многое другое. Каждый тип сувенирной продукции имеет свои уникальные характеристики и особенности .
Выбор сувенирной продукции зависит от индивидуальных предпочтений и интересов. Некоторые люди предпочитают покупать сувениры, связанные с местной историей или культурой . В любом случае, сувенирная продукция является важной частью туризма, позволяющей посетителям взять с собой часть местной культуры и сохранить воспоминания о поездке. Благодаря сувенирной продукции, местные жители могут продемонстрировать свои традиции и умения .
Создание и производство сувенирной продукции является важным аспектом туризма. Местные мастера и художники используют свои навыки и традиции, чтобы создать уникальные и ценные предметы . Производители сувениров должны учитывать качество и аутентичность своих изделий , чтобы создать успешную сувенирную продукцию.
Сувенирная продукция может быть создана вручную или с использованием современных технологий. Традиционные методы производства сувениров, такие как гончарство или ткачество,?ают из поколения в поколение . Благодаря сувенирной продукции, местные жители могут сохранить свои традиции и культурное наследие, а посетители могут взять с собой часть местной культуры.
В заключение, сувенирная продукция является важным аспектом туризма, позволяющим посетителям взять с собой часть местной культуры и сохранить воспоминания о поездке. она часто включает в себя традиционные изделия, демонстрирующие местные промыслы . Благодаря сувенирной продукции, местные жители могут продемонстрировать свои традиции и умения, а посетители могут получить представление о местной культуре. она может включать в себя широкий спектр предметов, от традиционных магнитов и кружек до сложных художественных изделий и произведений искусства .
Компания [url=https://klining-v-moskve10.ru/]клининг уборка[/url] занимается организацией и проведением профессионального клининга для жилых и коммерческих помещений.
Клининг является необходимым для создания комфортной и здоровой среды. Этот процесс включает в себя использование различных средств и методов для удаления грязи, пыли и других загрязнений. Клининг можно проводить как в домашних условиях, так и в коммерческих и промышленных объектах . Кроме того, клининг помогает предотвратить распространение бактерий и вирусов, что особенно важно в местах с большим скоплением людей.
Клининг поверхностей помогает удалить глубокие загрязнения и восстановить их первоначальный вид. Кроме того, клининг помогает продлить срок службы различных объектов и поверхностей, предотвращая их износ и повреждение. Клининг требует определенных навыков и знаний, чтобы провести его эффективно и безопасно.
Существует несколько видов клининга, включая сухой клининг, паровой клининг и химический клининг . Этот тип клининга особенно популярен в офисах и домах, где важно сохранить чистоту и сухость. Паровой клининг используется для глубокой очистки поверхностей и удаления глубоких загрязнений .
Этот тип клининга требует особого подхода и использования специальных средств и оборудования . Другой тип клининга – это клининг перед продажей объекта недвижимости, который включает в себя глубокую очистку и подготовку объекта для демонстрации потенциальным покупателям. Этот тип клининга требует особого внимания к деталям и использования эффективных методов и средств.
Каждое средство и оборудование имеет свои особенности и используется для различных целей . Кроме того, пылесосы используются для удаления пыли и грязи с поверхностей и из углов. Специальные средства и оборудование используются для глубокой очистки поверхностей и удаления глубоких загрязнений.
Для клининга также используются специальные перчатки и маски, которые помогают защитить руки и дыхание от химических средств и загрязнений. Кроме того, клининговые машины и оборудование используются для больших объектов и промышленных предприятий, где требуется эффективный и быстрый клининг. Клининговые машины и оборудование также могут быть использованы для клининга объектов с большими площадями.
Клининг помогает предотвратить распространение бактерий и вирусов, и создает комфортную и здоровую среду . Кроме того, клининг помогает улучшить эстетический вид объектов и поверхностей, и создает положительное впечатление у людей. Клининг может быть проведен как в домашних условиях, так и в коммерческих и промышленных объектах .
Клининг также включает в себя глубокую очистку различных поверхностей, таких как полы, стены и окна . Кроме того, клининг помогает создать положительное впечатление у потенциальных покупателей или партнеров, и увеличить стоимость объекта или предприятия. Клининг может быть проведен с помощью специальной техники, такой как клининговые машины и оборудование .
Visit our website to find out about [url=https://drone-show1.com/]drones show[/url], that will make your event unforgettable!
Drones have revolutionized the way we capture and interact with our surroundings.
Если вы ищете надежную и долговечную альтернативу одноразовым электронным сигаретам, то [url=https://tabaking.art/]купить электронную сигарету многоразовую с зарядкой в москве[/url] станет отличным вариантом для тех, кто ценит качество и долголетие своего устройства.
стали очень популярными среди курильщиков благодаря своей эффективности и экономической выгоде. Они позволяют пользователям наслаждаться широким спектром вкусов и содержат никотин в контролируемых количествах . Эти устройства могут использоваться в течение длительного времени и не требуют частой замены .
Многоразовые электронные сигареты имеют несколько преимуществ перед одноразовыми вариантами , включая функцию многоразовой зарядки. Это снижает количество отходов и делает их более экологически чистыми . Помимо этого, имеют более длительный срок эксплуатации, что делает их более экономически выгодными .
При выборе многоразовой электронной сигареты следует учитывать несколько моментов , включая вид батареи . Некоторые устройства оснащены не съемными батареями, в то время как другие позволяют заменить батарею . Это может быть важным фактором для пользователей, которые хотят иметь больше контроля .
Стоимость электронной сигареты также играет важную роль при выборе многоразовой электронной сигареты. Некоторые устройства могут быть довольно дорогими , в то время как другие предлагают более доступную альтернативу . Пользователи должны взвесить все за и против и выбрать устройство, которое подходит их стилю жизни.
Многоразовые электронные сигареты предлагают ряд преимуществ по сравнению с традиционными сигаретами. Они не содержат большого количества вредных химических веществ, которые находятся в табачных изделиях. Это снижает риск вреда для здоровья и уменьшает воздействие на окружающую среду.
Помимо этого, многоразовые электронные сигареты могут помочь курильщикам сократить количество никотина , что может быть полезно для их здоровья . Они также предоставляют возможность регулировать количество никотина , что может быть особенно полезным для тех, кто хочет уменьшить количество никотина .
В заключении, многоразовые электронные сигареты могут быть хорошей альтернативой традиционным сигаретам. Они обладают рядом достоинств, включая возможность контролировать уровень никотина , снижение затрат и меньшее воздействие на окружающую среду . Пользователям следует учитывать свои предпочтения и выбрать устройство, которое подходит их стилю жизни.
936110 832335Wow, wonderful blog layout! How lengthy have you ever been running a weblog for? you make running a blog glance straightforward. The total appear of your web site is magnificent, properly the content material material! 705792
При необходимости срочной транспортировки автомобиля [url=https://evakuator-moskva1.ru/]заказать эвакуатор москва недорого[/url] может оказаться очень полезным.
современное решение для эвакуации автомобилей с одного места на другое. Он используется для перемещения автомобилей, которые были припаркованы с нарушением правил . Эвакуатор состоит из специальной платформы и механизма для закрепления автомобилей .
Эвакуатор используется в случаях, когда автомобиль припаркован в неположенном месте . Он обеспечивает безопасное перемещение автомобилей. Эвакуатор управляется квалифицированными водителями .
Существует несколько типов эвакуаторов, каждый из которых предназначен для определенных задач . Эвакуаторы могут быть классифицированы по виду используемого подъемного механизма . Некоторые эвакуаторы предназначены для работы в городских условиях .
Эвакуаторы оснащены современным оборудованием для безопасной и эффективной транспортировки . Они могут быть использованы в различных условиях, включая ночное время. Эвакуаторы соответствуют современным стандартам качества и безопасности .
Эвакуаторы применяются в службе дорожного движения для решения проблем, связанных с неправильной парковкой . Они необходимы для эффективного решения проблем, связанных с авариями или неправильной парковкой . Эвакуаторы координируют свою работу с дорожными службами.
Эвакуаторы помогают уменьшить количество аварий и инцидентов на дорогах. Они работают в любых погодных условиях . Эвакуаторы играют ключевую роль в поддержании бесперебойного движения транспортных потоков .
Эвакуатор – это необходимый элемент городской инфраструктуры . Он помогает поддерживать безопасность и порядок на дорогах. Эвакуатор обеспечивает быструю и безопасную транспортировку автомобилей в любых условиях.
Эвакуатор сочетает в себе надежность, эффективность и безопасность. Он обеспечивает оперативную помощь в случае необходимости. Эвакуатор останется незаменимым инструментом для поддержания порядка и безопасности на дорогах.
Для заказа оборудования для бурения и цементирования скважин необходимо [url=https://cementirovochniy-agregat.ru/]ца цементировочный агрегат[/url], который применяется в процессе цементирования скважин для закрепления обсадных труб и изоляции пластов.
coту важных инструментов для обеспечения качественной отделки. Они используются для создания прочных и долговечных сооружений . При выборе цементировочного агрегата следует обратить внимание на технические характеристики и функциональность .
Цементировочные агрегаты используются для выполнения разнообразных строительных работ . Они обеспечивают долгую службу без необходимости частого ремонта. При этом необходимо учитывать все нюансы и особенности .
Преимущества цементировочных агрегатов
Использование цементировочных агрегатов дает возможность более точно контролировать процесс нанесения цементных смесей. Они выполняют работу быстрее и более эффективно . При этом важно выбрать агрегат соответствующий типу работ .
Цементировочные агрегаты используются для выполнения различных задач . Они обеспечивают высокое качество и долговечность . При этом необходимо учитывать все нюансы и особенности .
Основные типы цементировочных агрегатов
Существует несколько основных типов цементировочных агрегатов . Они отличаются по техническим характеристикам и функциональности . При этом необходимо учитывать все факторы .
Цементировочные агрегаты предназначены для выполнения различных задач . Они выполняют функцию нанесения цементных растворов . При этом важно правильно выбрать цементировочный агрегат .
Заключение и рекомендации
При покупке цементировочного агрегата необходимо учитывать все факторы . Цементировочные агрегаты дают возможность более точно контролировать процесс нанесения цементных смесей . При этом важно обратить внимание на технические характеристики .
Цементировочные агрегаты используются для выполнения различных строительных задач . Они используются для создания прочных оснований . При этом следует заранее определить объем работ и необходимую производительность.
Для жителей северной столицы теперь доступна профессиональная [url=https://uborka-top24.ru/]клининг квартир спб[/url], выполняемая высококвалифицированным персоналом.
Уборка квартир в СПб должна проводиться регулярно для поддержания чистоты и гигиены. Это связано с тем, что чистая квартира не только обеспечивает комфорт и эстетику, но также влияет на здоровье и психологическое состояние жильцов.
Для создания по-настоящему незабываемых фотографий в Москве, воспользуйтесь услугами [url=https://moscowmoment.ru/]фотосессия с стиле ню[/url], где опыт и креативность гарантируют вам действительно уникальные и запоминающиеся снимки.
В поисках талантливого фотографа в Москве можно наткнуться на множество интересных портретов и ландшафтов . С развитием технологий и появлением новых камер и программных средств возможности фотографии расширились Современная фотография в Москве включает в себя множество стилей и жанров, каждый из которых требует особой подготовки и опыта. Фотограф в Москве может предложить широкий спектр услуг включая портретную, свадебную, модную и документальную фотографию .
Фотография в Москве развивается с каждым днём россияне все больше ценят произведения фотографического искусства. Фотографы в Москве часто принимают участие в различных выставках и конкурсах где они могут представить свои лучшие работы и получить профессиональную оценку. Уровень конкуренции между фотографами в Москве достаточно высок каждый фотограф??тается создать свой уникальный и узнаваемый стиль .
Фотограф в Москве должен соответствовать определённым требованиям иметь высокий уровень профессиональной подготовки и опыта работы . Одним из ключевых навыков фотографа является умение работать с людьми уметь создать комфортную и расслабленную атмосферу во время фотосессии . Кроме того, фотограф в Москве должен быть знаком с редакторским программным обеспечением таким как Adobe Photoshop и Lightroom .
Работа фотографа в Москве постоянно совершенствуется технологии и методы работы появляются каждый год . Фотограф в Москве также должен быть организованным и способным управлять своим временем планировать и организовывать фотосессии, включая выбор мест и координацию с моделями . Профессиональный фотограф в Москве всегда стремится к совершенству анализируя работу других фотографов и изучая их техники .
В Москве можно найти фотографов, специализирующихся на различных видах фотографии от портретной и свадебной до модной и документальной . Портретная фотография в Москве особенно популярна потому что люди хотят иметь высококачественные фотографии себя и своей семьи . Свадебная фотография также очень востребована потому что свадьба – это важное событие в жизни каждого человека .
Модная фотография в Москве представлена множеством талантливых фотографов используя последние тенденции и инновации в области моды. Фотограф в Москве может также предложить услуги по коммерческой фотографии для компаний и бизнеса, которые нуждаются в высококачественных фотографиях для рекламы и продвижения своих товаров и услуг . Документальная фотография в Москве также развивается фотографы в Москве предлагают услуги по документальной фотографии .
Фотограф в Москве – это высококвалифицированный специалист и создать высококачественные фотографии, соответствующие последним тенденциям и технологиям . Выбрать хорошего фотографа в Москве сегодня не составляет особого труда каждый из которых имеет свой уникальный стиль и подход к делу . Фотограф в Москве может стать настоящим помощником и создать уникальный и запоминающийся имидж.
Профессиональный фотограф в Москве готов предложить вам уникальные услуги, включая [url=https://moscowfocus.ru/]фотосессию в стиле ню[/url].
Существует множество стилей фотографии, включая семейную, свадебную и портретную
На сайте [url=https://moscowframe.ru/]фотосессия офисная[/url] вы можете заказать услуги профессионального фотографа в Москве.
самые значимые даты в столице России. Профессиональный фотограф в Москве поможет создать удивительные и неповторимые снимки . Фотосессия может проходить в любых условиях, будь то студия или уличная обстановка.
Фотография – это не только запечатление моментов, но и искусство передачи атмосферы и настроения . Фотограф в Москве, имеющий глубокое понимание своих клиентов и их пожеланий, может предложить создание фотографий, отражающих личность и стиль клиента.
Существует много разных типов фотосессий, каждая со своим уникальным стилем и атмосферой . Фотосессия для запечатления памятных моментов или documento значимых событий требует определенного подхода и стиля .
Фотограф в Москве, специализирующийся на портретной, модной или художественной фотографии , может предложить высокое качество фотографий и профессиональную обработку . Фотосессия может быть спонтанной и непредсказуемой или тщательно спланированной .
Подготовка к фотосессии – это ключевой этап, на котором определяется концепция и задачи фотосессии. Фотограф в Москве поможет определить цель и задачи фотосессии .
Фотосессия может быть включать в себя элементы стилизации, макияжа и костюма . Фотограф в Москве, имеющий способность работать в разных условиях и ситуациях, может предложить индивидуальный подход и персонализированную поддержку .
Результат фотосессии – это уникальные и незабываемые фотографии . Фотограф в Москве, имеющий большой опыт и высокий уровень мастерства , может предложить высокое качество фотографий и профессиональную обработку .
Фотосессия в Москве – это уникальный шанс создать удивительные и неповторимые фотографии . Фотограф в Москве поможет создать невероятно красивые и эмоциональные фотографии .
Для тех, кто столкнулся с проблемой поломки автомобиля в столице, [url=https://evakuator-moskva1.ru/]эвакуатор в москве недорого цена[/url] предоставляет оперативные и надежные услуги по перевозке транспортных средств, гарантируя безопасность и быстрое решение проблемы.
В Москве услуги эвакуатора являются одними из наиболее востребованных. Это связано с тем, что в городе часто встречаются ситуации, когда автомобильNeeds эвакуации из-за поломки, ДТП или других непредвиденных обстоятельств транспортное средство может потребовать эвакуации в случае поломки или других проблем. В таких случаях услуги эвакуатора становятся просто незаменимыми услуги эвакуатора становятся спасением для водителей в таких ситуациях .
Компании, предоставляющие услуги эвакуатора в Москве, работают круглосуточно, что позволяет водителям получить помощь в любое время компании, оказывающие услуги эвакуатора в Москве, работают круглосуточно и без выходных . Это особенно важно в случае неожиданных поломок или аварий, когда каждая минута на счету в случае аварии или неожиданной поломки важно получить помощь как можно скорее . Благодаря услугам эвакуатора, водители могут не беспокоиться о том, как добраться до места назначения или как справиться с неисправным транспортным средством услуги эвакуатора делают жизнь водителей проще в случае неожиданных проблем с автомобилем.
Услуги эвакуатора в Москве включают в себя широкий спектр услуг, начиная от простой эвакуации автомобиля до более сложных операций услуги эвакуатора в Москве включают в себя различные виды помощи . Одним из наиболее популярных видов услуг является эвакуация автомобиля в случае его поломки или неисправности услуги эвакуатора по ремонту автомобиля пользуются большим спросом . Кроме того, существуют услуги по эвакуации автомобилей,involved в ДТП эвакуация автомобиля после аварии является важной услугой .
Компании, предоставляющие услуги эвакуатора в Москве, также предлагают услуги по доставке автомобиля в назначенное место компании, оказывающие услуги эвакуатора, предлагают услуги по доставке автомобиля . Это может быть особенно полезно для водителей, которым необходимо доставить свой автомобиль в сервисный центр или на стоянку в случае необходимости доставки автомобиля в сервисный центр или на стоянку услуги эвакуатора становятся необходимыми . Кроме того, некоторые компании предлагают услуги по техническому обслуживанию и ремонту автомобилей некоторые компании, предоставляющие услуги эвакуатора, также предлагают услуги по техническому обслуживанию .
Услуги эвакуатора в Москве имеют множество преимуществ для водителей услуги эвакуатора в Москве предоставляют водителям ряд преимуществ. Одним из основных преимуществ является возможность получения помощи в любое время и в любом месте эвакуаторные услуги обеспечивают помощь водителям в?? ситуации. Это особенно важно для водителей, которые часто находятся в пути и могут столкнуться с неожиданными проблемами эвакуаторные услуги обеспечивают безопасность и уверенность для водителей.
Кроме того, услуги эвакуатора в Москве могут помочь водителям сэкономить время и деньги услуги эвакуатора позволяют водителям сократить расходы на ремонт и обслуживание автомобиля. В случае поломки или аварии, услуги эвакуатора могут помочь доставить автомобиль в сервисный центр или на стоянку, что может предотвратить дальнейшее повреждение и сократить расходы на ремонт в случае поломки или аварии услуги эвакуатора могут помочь предотвратить дальнейшее повреждение автомобиля .
В заключении, услуги эвакуатора в Москве являются необходимыми для многих водителей услуги эвакуатора в Москве являются важными для большинства автомобилистов . Благодаря услугам эвакуатора, водители могут получить помощь в любое время и в любом месте, что может помочь им сэкономить время и деньги эвакуаторные услуги в столице предлагают комплексные решения для водителей, что может помочь им сократить расходы . При выборе компании, предоставляющей услуги эвакуатора, важно учитывать такие факторы, как опыт, квалификация и стоимость услуг при выборе компании, предоставляющей услуги эвакуатора, важно учитывать такие факторы, как надежность и эффективность.
If you need a phone number for one-time registration or verification, consider using [url=https://www.fidetec.com/7sim/]7sim org[/url], которые могут помочь в решении проблемы получения сообщений.
enabling efficient communication without hefty price tags. With the rise of virtual phone systems, free phone numbers are now more accessible than ever . there has been a notable surge in the use of free phone numbers, as they offer a budget-friendly alternative to traditional phone services.
the idea of free phone numbers has been in existence for a while, but it has gained traction in the last few years. the key driver of this growth is the technological advancements that have made it feasible to offer free phone numbers with excellent service. free phone numbers have emerged as a viable option for startups, small businesses, and individuals who want to save on their phone bills.
the benefits of free phone numbers encompass cost reductions, increased adaptability, and better customer care. By using a free phone number, businesses can cut down on their phone expenses, streamline their operations, and boost their profitability. Moreover, free phone numbers can be easily integrated with existing phone systems, enabling smooth communication and reducing downtime . This has made free phone numbers an essential tool for businesses that rely heavily on phone communications, such as customer service centers and sales teams .
In addition to the cost savings, free phone numbers also offer increased flexibility, enabling companies to handle their communications remotely, without being tied to a specific location . this is highly advantageous for businesses with virtual teams or those that operate across various time zones. Furthermore, free phone numbers can be easily scaled up or down, depending on the changing needs of the business . this makes them a viable option for businesses that face variations in call volume or have cyclical changes in their operations.
Getting a free phone number is a relatively simple process, requiring a few straightforward steps and limited documentation . The first step is to select a trustworthy provider that offers free phone numbers, considering aspects such as voice quality, customer service, and functionality . Once a provider is chosen, the next step is to create an account, which usually requires providing fundamental details such as name, email address, and password . After completing the sign-up process, users can normally pick their preferred free phone number from a variety of available numbers.
Some providers may also provide extra features, such as call routing, voicemail, and call logging, which can be beneficial for companies and individuals . These features can increase the usefulness of the free phone number, making it more effective for overseeing communications. It is essential to carefully review the terms and conditions of the provider, including any usage limits or restrictions . This will help ensure that the free phone number meets the needs of the business or individual, without any unexpected surprises .
In conclusion, free phone numbers have become an essential tool for businesses and individuals, offering a cost-effective solution for communication needs . As technology continues to evolve, it is expected that free phone numbers will become more refined, with supplementary features and increased effectiveness. This will make them more enticing to businesses and individuals, who are trying to cut down on their communication bills.
The future of free phone numbers looks bright, with the possibility of even more cutting-edge features and uses . As the demand for free phone numbers continues to grow, providers will need to adapt and innovate, delivering more refined features and enhanced customer care. This will drive the development of new technologies and services, also enlarging the possibilities of free phone numbers. Ultimately, the widespread adoption of free phone numbers will transform the way businesses and individuals communicate, facilitating more streamlined and budget-friendly communications .
Для заказа оборудования для бурения и цементирования скважин необходимо [url=https://cementirovochniy-agregat.ru/]куплю цементировочный агрегат[/url], который применяется в процессе цементирования скважин для закрепления обсадных труб и изоляции пластов.
необходимые машины для выполнения различных строительных задач . Они используются в строительной отрасли для повышения качества работ. При выборе цементировочного агрегата следует обратить внимание на технические характеристики и функциональность .
Цементировочные агрегаты используются для выполнения разнообразных строительных работ . Они обеспечивают долгую службу без необходимости частого ремонта. При этом важно правильно выбрать цементировочный агрегат .
Преимущества цементировочных агрегатов
Использование цементировочных агрегатов дает возможность более точно контролировать процесс нанесения цементных смесей. Они дают возможность работать с разными типами цементных растворов . При этом важно выбрать агрегат соответствующий типу работ .
Цементировочные агрегаты предоставляют широкий спектр возможностей . Они используются для создания прочных и устойчивых сооружений . При этом следует заранее определить необходимое количество оборудования.
Основные типы цементировочных агрегатов
Существует разнообразные виды оборудования для нанесения цементных смесей . Они имеют разные размеры и производительность . При этом необходимо учитывать все факторы .
Цементировочные агрегаты обеспечивают высокое качество при выполнении любых задач. Они обеспечивают долгую службу без необходимости частого ремонта. При этом необходимо учитывать все нюансы и особенности .
Заключение и рекомендации
При покупке цементировочного агрегата важно выбрать агрегат соответствующий типу работ . Цементировочные агрегаты выполняют функцию нанесения цементных растворов с высокой точностью. При этом необходимо учитывать все нюансы и особенности .
Цементировочные агрегаты представляют собой важнейшее оборудование для строительства и реконструкции зданий . Они используются для создания прочных оснований . При этом важно учитывать все нюансы и особенности .
Для создания по-настоящему незабываемых фотографий в Москве, воспользуйтесь услугами [url=https://moscowmoment.ru/]фотограф контента[/url], где опыт и креативность гарантируют вам действительно уникальные и запоминающиеся снимки.
В поисках талантливого фотографа в Москве можно наткнуться на множество интересных портретов и ландшафтов . С развитием технологий и появлением новых камер и программных средств возможности фотографии расширились Современная фотография в Москве включает в себя множество стилей и жанров, каждый из которых требует особой подготовки и опыта. Фотограф в Москве может предложить широкий спектр услуг включая портретную, свадебную, модную и документальную фотографию .
Фотография в Москве развивается с каждым днём новые студии и фотографические лаборатории открываются в городе . Фотографы в Москве часто принимают участие в различных выставках и конкурсах чтобы демонстрировать свои работы и делиться опытом с коллегами . Уровень конкуренции между фотографами в Москве достаточно высок каждый фотограф??тается создать свой уникальный и узнаваемый стиль .
Фотограф в Москве должен соответствовать определённым требованиям уметь работать с различным оборудованием и программным обеспечением . Одним из ключевых навыков фотографа является умение работать с людьми знать, как правильно расположить и позировать объекты съемки . Кроме того, фотограф в Москве должен быть знаком с редакторским программным обеспечением которое позволяет совершенствовать фотографии и добавлять им необходимые эффекты .
Работа фотографа в Москве постоянно совершенствуется технологии и методы работы появляются каждый год . Фотограф в Москве также должен быть организованным и способным управлять своим временем иметь возможность работать под давлением и выполнять работу качественно и в срок. Профессиональный фотограф в Москве всегда стремится к совершенству стремясь создать что-то уникальное и запоминающееся.
В Москве можно найти фотографов, специализирующихся на различных видах фотографии и позволяет фотографу раскрыть свои творческие способности. Портретная фотография в Москве особенно популярна фотографы в Москве предлагают широкий спектр портретных фотосессий . Свадебная фотография также очень востребована фотографы в Москве предлагают услуги по фотографированию свадеб .
Модная фотография в Москве представлена множеством талантливых фотографов используя последние тенденции и инновации в области моды. Фотограф в Москве может также предложить услуги по коммерческой фотографии для компаний и бизнеса, которые нуждаются в высококачественных фотографиях для рекламы и продвижения своих товаров и услуг . Документальная фотография в Москве также развивается и могут создать уникальные и незабываемые фотографии.
Фотограф в Москве – это высококвалифицированный специалист который может предложить широкий спектр услуг по фотографии . Выбрать хорошего фотографа в Москве сегодня не составляет особого труда потому что в городе работает множество талантливых фотографов . Фотограф в Москве может стать настоящим помощником и помочь клиенту запечатлеть важные моменты его жизни .
Профессиональный фотограф в Москве готов предложить вам уникальные услуги, включая [url=https://moscowfocus.ru/]профессиональный фотосессия[/url].
В последнее время наблюдается тенденция к увеличению спроса на услуги фотографов в Москве.
На сайте [url=https://moscowframe.ru/]фотограф в москве фотосессия в студии[/url] вы можете заказать услуги профессионального фотографа в Москве.
самые значимые даты в столице России. Профессиональный фотограф в Москве поможет создать потрясающие и незабываемые изображения. Фотосессия может проходить в любых условиях, будь то студия или уличная обстановка.
Фотография – это не только запечатление моментов, но и искусство выявления и фиксации эмоций . Фотограф в Москве, имеющий большой опыт работы и разнообразный портфолио , может предложить разработку персонализированного плана фотосессии .
Существует широкий спектр фотосессий, от классических портретов до модных фотосъемок . Фотосессия для создания семейного альбома или индивидуального портфолио требует глубокого понимания цели и задач фотосессии.
Фотограф в Москве, специализирующийся на создании фотографий для рекламы,.editorials или каталогов, может предложить высокое качество фотографий и профессиональную обработку . Фотосессия может быть спонтанной и непредсказуемой или тщательно спланированной .
Подготовка к фотосессии – это важнейший шаг, требующий тщательного планирования и внимания к деталям . Фотограф в Москве поможет выбрать подходящую локацию и время суток .
Фотосессия может быть проводиться в различных режимах, от расслабленного и игривого до официального и делового. Фотограф в Москве, имеющий большой опыт работы с клиентами , может предложить уникальный и творческий подход к фотосессии.
Результат фотосессии – это потрясающие и эмоциональные изображения. Фотограф в Москве, имеющий способность работать в разных условиях и ситуациях, может предложить высокое качество фотографий и профессиональную обработку .
Фотосессия в Москве – это уникальная возможность запечатлеть самые яркие моменты жизни . Фотограф в Москве поможет создать невероятно красивые и эмоциональные фотографии .
Для жителей северной столицы теперь доступна профессиональная [url=https://uborka-top24.ru/]клининг квартир спб[/url], выполняемая высококвалифицированным персоналом.
Уборка квартир СПб требует особого внимания и заботы. Это связано с тем, что Оценка качества уборки квартир и надежности компании является важным шагом в процессе выбора.
Для заказа оборудования для бурения и цементирования скважин необходимо [url=https://cementirovochniy-agregat.ru/]цементировочный агрегат 320[/url], который применяется в процессе цементирования скважин для закрепления обсадных труб и изоляции пластов.
coту важных инструментов для обеспечения качественной отделки. Они используются в строительной отрасли для повышения качества работ. При выборе цементировочного агрегата важно помнить о надежности и долговечности оборудования.
Цементировочные агрегаты предназначены для эффективного и быстрого нанесения цементных смесей . Они обеспечивают долгую службу без необходимости частого ремонта. При этом необходимо учитывать все нюансы и особенности .
Преимущества цементировочных агрегатов
Использование цементировочных агрегатов дает возможность более точно контролировать процесс нанесения цементных смесей. Они обеспечивают высокую производительность и надежность. При этом важно выбрать агрегат соответствующий типу работ .
Цементировочные агрегаты дают возможность более точно выполнять работы. Они обеспечивают высокое качество и долговечность . При этом важно обратить внимание на технические характеристики .
Основные типы цементировочных агрегатов
Существует различные модели агрегатов для выполнения строительных задач. Они отличаются по техническим характеристикам и функциональности . При этом важно выбрать агрегат соответствующий типу работ .
Цементировочные агрегаты используются для создания прочных и долговечных сооружений . Они обеспечивают долгую службу без необходимости частого ремонта. При этом важно правильно выбрать цементировочный агрегат .
Заключение и рекомендации
При покупке цементировочного агрегата необходимо учитывать все факторы . Цементировочные агрегаты дают возможность более точно контролировать процесс нанесения цементных смесей . При этом важно обратить внимание на технические характеристики .
Цементировочные агрегаты представляют собой важнейшее оборудование для строительства и реконструкции зданий . Они выполняют функцию нанесения цементных растворов . При этом необходимо правильно выбрать цементировочный агрегат .
Профессиональный фотограф в Москве готов предложить вам уникальные услуги, включая [url=https://moscowfocus.ru/]фитнес фотограф[/url].
Тем не менее, навыки работы с камерой и послепродакшн являются ключевыми аспектами великолепной фотографии.
На сайте [url=https://moscowframe.ru/]фотосессия для мужчин москва[/url] вы можете заказать услуги профессионального фотографа в Москве.
самые значимые даты в столице России. Профессиональный фотограф в Москве поможет создать удивительные и неповторимые снимки . Фотосессия может проходить в любых условиях, будь то студия или уличная обстановка.
Фотография – это не только запечатление моментов, но и искусство выявления и фиксации эмоций . Фотограф в Москве, имеющий большой опыт работы и разнообразный портфолио , может предложить разработку персонализированного плана фотосессии .
Существует много разных типов фотосессий, каждая со своим уникальным стилем и атмосферой . Фотосессия для создания семейного альбома или индивидуального портфолио требует специфического плана и подготовки .
Фотограф в Москве, специализирующийся на фотографии пейзажей, архитектуры или натюрморта , может предложить высокое качество фотографий и профессиональную обработку . Фотосессия может быть осуществлена в разных форматах и вариантах.
Подготовка к фотосессии – это необходимый процесс, включающий выбор локации, одежды и стиля . Фотограф в Москве поможет подготовить необходимое оборудование и аксессуары.
Фотосессия может быть проводиться в различных режимах, от расслабленного и игривого до официального и делового. Фотограф в Москве, имеющий высокий уровень эмпатии и понимания , может предложить индивидуальный подход и персонализированную поддержку .
Результат фотосессии – это потрясающие и эмоциональные изображения. Фотограф в Москве, имеющий глубокое понимание своих клиентов и их пожеланий , может предложить высокое качество фотографий и профессиональную обработку .
Фотосессия в Москве – это уникальная возможность запечатлеть самые яркие моменты жизни . Фотограф в Москве поможет создать невероятно красивые и эмоциональные фотографии .
Get [url=https://www.fidetec.com/7sim/]7sim[/url] for convenient and secure registration on various services.
Despite their advantages, free phone numbers also have certain drawbacks.
Для тех, кто ищет удобную и быструю [url=https://alcohimki.ru/]алкоголь доставка химки[/url] в Химках, теперь есть отличный вариант, позволяющий получить алкоголь прямо на дом в кратчайшие сроки.
все более популярной в последнее время в связи с развитием онлайн-платформ и сервисов доставки. Компании, предоставляющие услуги доставки алкоголя, предлагают широкий выбор напитков , включая вина, шампанское, пиво и другие виды спиртных напитков. Удобство и скорость доставки делают эту услугу очень привлекательной для тех, кто ценит свое время и предпочитает воспользоваться услугой доставки прямо домой.
Услуги доставки алкоголя в Химках позволяют жителям наслаждаться праздниками и вечеринками , не выходя из дома. Это особенно важно для тех, кто любит устраивать вечеринки. Кроме того, многие компании предлагают услуги консультантов, готовых ответить на все вопросы и помочь с выбором напитков.
Преимущества доставки алкоголя в Химках очевидны и многочисленны . Во-первых, это возможность сэкономить время , поскольку вам не нужно тратить время на поездку в магазин. Во-вторых, высокое качество обслуживания обеспечивают, что ваш заказ будет выполнен быстро и профессионально. В-третьих, богатый выбор алкоголя и напитков позволяет найти именно то, что вы ищете.
Компании, занимающиеся доставкой алкоголя, стремятся повысить уровень обслуживания, чтобы клиенты могли наслаждаться лучшим сервисом и выбором. Это включает в себя постоянные распродажи и скидки, которые делают услугу еще более привлекательной. Кроме того, безопасные и удобные способы оплаты обеспечивают максимальный комфорт для клиентов.
Заказать доставку алкоголя в Химках относительно легко и быстро. Вам необходимо посетить веб-сайт компании , где вы сможете ознакомиться с ассортиментом алкогольных напитков . Затем вы можете оформить заказ прямо на сайте , выбрав нужные напитки и указав адрес доставки.
После подтверждения заказа, операторы компании свяжутся с вами , чтобы подтвердить ваш заказ и обсудить детали доставки. Это обеспечивает точность и оперативность обслуживания. Ademas, гарантируют высокое качество продуктов, чтобы клиенты получили лучший выбор алкоголя.
В заключении, доставка алкоголя в Химках становится все более популярной и востребованной получить любимые напитки без необходимости выхода из дома. Удобство, скорость и качество сервиса и выбор алкоголя делают эту услугу очень привлекательной и востребованной . Если вы ищете удобный и быстрый способ насладиться алкоголем в Химках, то эта услуга подойдет вам идеально .
Для жителей Москвы и ее окрестностей доступна удобная [url=https://alkomoskovskiy.ru/]доставка алкоголя 24[/url] прямо до двери, что делает процесс приобретения напитков максимально комфортным и быстрым.
является очень востребованной услугой среди жителей города, которые ценят свое время и хотят получить качественные напитки без выхода из дома. Эта услуга позволяет жителям Москвы не тратить время на поездку в магазин и подбор подходящих напитков. Кроме того, доставка алкоголя предоставляет большой выбор напитков от различных производителей.
Доставка алкоголя в Москве осуществляется компаниями , которые заботятся о качестве обслуживания и удовлетворении потребностей клиентов. Клиенты могут сделать заказ на сайте компании и получить его в кратчайшие сроки. Это очень удобно людям с плотным графиком на посещение магазинов.
Доставка алкоголя в Москве имеет несколько плюсов для клиентов. Во-первых, это не потраченное время на поездку в магазин и обратно. Во-вторых, клиенты могут выбрать из большого ассортимента напитков, что упрощает поиск нужного напитка . Кроме того, доставка алкоголя осуществляется в удобное время , что значительно улучшает качество обслуживания .
Доставка алкоголя в Москве предоставляет условия для безопасной покупки клиентов, поскольку они не должны покидать свой дом и рисковать здоровьем. Это особенно важно в периоды повышенной опасности для здоровья. Компании, предоставляющие услуги доставки, обеспечивают качество напитков , что укрепляет доверие к компании .
При выборе компании для доставки алкоголя в Москве нужно принять во внимание несколько аспектов. Во-первых, это репутация компании , которая формируется на основе обратной связи. Во-вторых, это ассортимент продукции , которое должно соответствовать стандартам . В-третьих, это уровень сервисного обслуживания, который должен отвечать ожиданиям клиентов.
Компании, предоставляющие услуги доставки алкоголя в Москве, должны иметь соответствующие документы на осуществление деятельности. Клиенты могут убедиться в наличии документов на сайте компании или по телефону. Это дает уверенность в легитимности компании и дает гарантии безопасности при покупке и доставке алкоголя.
Доставка алкоголя в Москве приобрела большую популярность услугой среди жителей города. Эта услуга имеет несколько плюсов , включая экономию времени , доступ к широкому выбору , и гарантию безопасности . При выборе компании для доставки алкоголя необходимо учитывать репутацию компании, разнообразие предлагаемых напитков, и качество сервиса . Компании, предоставляющие услуги доставки алкоголя, должны иметь лицензию и гарантировать высокое качество продукции .
Для жителей Мытищ доступна [url=https://alcomytishi.ru/]доставка алкоголя на дом мытищи[/url], что делает возможным получение напитков прямо на пороге собственного дома.
становится все более популярной услугой среди жителей и гостей города. Это связано с растущим спросом на быструю и качественную доставку. За счет увеличения числа компаний, предлагающих такие услуги жители Мытищ могут получить алкогольные напитки без необходимости выхода из дома.
В этом контексте интернет-магазины и компании по доставке алкоголя играют ключевую роль. Они предлагают разнообразные позиции и акции , что делает процесс заказа и доставки алкоголя максимально комфортным для клиентов. Благодаря эффективному менеджменту и контролю качества , доставка алкоголя в Мытищах приобретает особую значимость .
Доставка алкоголя в Мытищах имеет ряд значительных плюсов . Во-первых, экономия времени является ключевым преимуществом , поскольку есть возможность совершать покупки без выхода из дома . Во-вторых, доставка?ных напитков на дом обеспечивает исключает необходимость физически присутствовать в магазине.
Кроме того, выбор алкогольных напитков в интернет-магазинах обычно включает в себя широкий спектр товаров. Это позволяет подобрать идеальный подарок или напиток для любого случая. Благодаря постоянному улучшению качества обслуживания, цены на доставку алкоголя в Мытищах становятся все более доступными .
Условия и стоимость доставки алкоголя в Мытищах определяются логистическими возможностями и политикой фирмы. Как правило, пороговый объем покупок для бесплатной доставки составляет небольшую сумму, чтобы стимулировать клиентов . Кроме того, период ожидания заказа варьируется и определяются графиком работы курьерской службы .
Некоторые компании предлагают бесплатную доставку при определенной сумме заказа . Это повышает лояльность клиентов и стимулирует повторные покупки . При этом важно понимать особенности и требования доставки алкогольных напитков.
Заключая, доставка алкоголя в Мытищах представляет собой перспективную бизнес-нишу . Благодаря оптимизации процессов и удешевлению услуг, этот рынок продолжит расти и развиваться . В перспективе, можно ожидать появления новых инноваций и улучшений , что еще больше оптимизирует бизнес-процессы.
В связи с этим, фирмы, предоставляющие такие услуги должны адаптироваться к меняющимся потребностям и ожиданиям клиентов. Это позволит им оставаться конкурентоспособными . Благодаря совместным усилиям всех участников рынка , доставка алкоголя в Мытищах станет еще более удобной и доступной .
Для тех, кто ищет удобный способ получить свой любимый напиток, [url=https://alcobalashiha.ru/]заказ алкоголя на дом[/url] становится идеальным решением.
становится все более распространенной среди жителей города. Это связано с увеличением занятости людей , что не позволяет им лично покупать алкоголь . Компании, занимающиеся доставкой алкоголя, предлагают широкий ассортимент напитков .
Доставка алкоголя в Балашихе осуществляется круглосуточно , что очень удобно для заказчиков . Заказ можно сделать телефонным звонком , что делает процесс заказа простым .
Доставка алкоголя в Балашихе дает несколько существенных преимуществ для своих клиентов. Одним из основных преимуществ является возможность быстрого получения товара , что имеет большое значение для заказчиков . Кроме того, доставка алкоголя гарантирует целостность продукции , что важно для поддержания качества продукции .
Доставка алкоголя в Балашихе также позволяет клиентам экономить время , что может быть использовано для более важных дел . Компании, занимающиеся доставкой, старчески относятся к каждому клиенту , что формирует лояльность клиентов.
Заказать доставку алкоголя в Балашихе relatively просто. Для начала необходимо найти достойного поставщика услуг, что можно сделать через интернет . После выбора компании нужно зайти на официальный сайт и изучить список доступных напитков.
Затем следует сделать заказ , что можно сделать по телефону . После оформления заказа необходимо произвести оплату , что можно сделать несколькими способами . Компания обеспечит быструю доставку.
Доставка алкоголя в Балашихе является весьма востребованной услугой . Она экономит время клиентов , предоставляет широкий выбор продукции и гарантирует качество напитков . Компании, занимающиеся доставкой, стараются улучшить свои услуги , что формирует доверие клиентов.
В заключение, доставка алкоголя в Балашихе является услугой с большим потенциалом. Ее можно сделать заказ без особых усилий, и она дает ряд преимуществ для клиентов. Таким образом, доставка алкоголя будет дальше расширяться .
Если вы ищете удобный и быстрый способ получить напитки, воспользуйтесь услугой [url=https://alcopushkino.ru/]доставка алкоголя пушкино круглосуточно[/url], которая работает без выходных и перерывов, чтобы любой вечер или праздник был полон радости и хорошего настроения.
является современным решением для тех, кто ценит время и комфорт . Эта услуга приобрела популярность в последние годы благодаря своей удобности и доступности . Благодаря доставке алкоголя в Пушкино, жители могут наслаждаться своим любимым напитком в удобное время .
Доставка алкоголя в Пушкино проводится компаниями, которые заботятся о качестве обслуживания . Компании, предоставляющие эту услугу, работают над улучшением качества своих услуг и расширением ассортимента предлагаемых продуктов . Это способствует росту популярности доставки алкоголя в Пушкино.
Преимущества доставки алкоголя в Пушкино позволяют жителям наслаждаться алкоголем в комфорте своего дома. Доставка алкоголя помогает избежать пробок и длинных очередей в магазинах. Благодаря этому сервису, имеют возможность приобрести алкоголь в любое время, соответствующее их графику .
Доставка алкоголя в Пушкино позволяет клиентам получать качественные алкогольные изделия без риска покупки поддельных продуктов . Компании, которые занимаются доставкой, обеспечивают безопасную и надежную упаковку для того, чтобы избежать повреждений во время доставки .
Заказать доставку алкоголя в Пушкино позволяет клиентам отслеживать статус их заказа в режиме реального времени. Для начала, нужно посетить сайт компании и просмотреть ассортимент предлагаемых продуктов . Затем, может оставить комментарий или специальные инструкции для курьера.
После подтверждения заказа, компания обрабатывает его и направляет курьера для доставки . Курьер осуществляет проверку возраста и личности получателя для обеспечения безопасности.
Будущее доставки алкоголя в Пушкино выглядит перспективным, с учетом роста спроса на подобные услуги . Компании, занимающиеся доставкой, инвестируют в технологии и маркетинг, чтобы расширить свою клиентскую базу . Это позволит им оставаться лидерами на рынке и удовлетворять растущий спрос на доставку алкоголя .
Доставка алкоголя в Пушкино будет включать в себя новые услуги, такие как подбор вина к столу или организация вечеринок . В будущем, жители Пушкино смогут наслаждаться еще более широким выбором алкогольных изделий и получать их быстрее и удобнее .
Для получения быстрой и удобной [url=https://alcolyubertsy.ru/]доставка алкоголя люберцы круглосуточно[/url] в любое время суток, включая ночное время, можно воспользоваться онлайн-сервисом, предлагающим широкий выбор напитков и удобную систему оплаты.
Доставка алкоголя в этом регионе набирает обороты thanks kepada высокой??ы . Это связано с тем, что большинство людей хотят иметь возможность получить алкоголь в кратчайшие сроки. Кроме того, такая услуга дает возможность получить алкоголь без лишних проблем.
Этот город имеет широкий выбор сервисов доставки алкоголя. Каждая компания предлагает свои уникальные условия и преимущества, такие как скидки и акции . Это позволяет клиентам выбирать компанию, которая лучше всего соответствует их потребностям .
Доставка алкоголя в Люберцах имеет множество преимуществ для потребителей . Одним из основных преимуществ является возможность заказать алкоголь без выхода из дома, что особенно удобно в холода или плохую погоду . Кроме того, многие компании предлагают гибкие системы оплаты и доставки.
Доставка алкоголя может быть очень полезной в дни праздников или специальных событий . Например, услуги доставки помогают создать праздничную атмосферу, без необходимости личного присутствия в магазине . Это упрощает жизнь людей, которые ценят время и комфорт .
Процесс заказа доставки алкоголя в этом регионе очень прост . Для этого необходимо выбрать желаемый алкогольный напиток и указать адрес доставки. После этого заказчик может выбрать наиболее удобный способ оплаты, включая наличные или безналичный расчет .
При выборе компании стоит обратить внимание на отзывы и рекомендации других клиентов . Это позволит оценить качество обслуживания и nivel доверия к компании . Кроме того, необходимо проверить информацию о компании и ее деятельности.
Доставка алкоголя в Люберцах является удобной и практичной услугой . Это позволяет получить алкоголь быстро и без проблем, не выходя из дома . Кроме того, компании доставки алкоголя в Люберцах предлагают широкий выбор алкогольных напитков и удобные системы оплаты .
В заключении можно сказать, что доставка алкоголя в Люберцах является востребованной услугой . Это делает жизнь людей проще и удобнее, экономя их время и силы . Кроме того, этот сектор рынка будет дальше развиваться и предлагать новые решения .
У нас вы найдете актуальные [url=https://moykaterinburg.ru/shinomontazh/]расценки на шиномонтажные работы[/url], которые помогут вам с выбором услуг в нашем сервисе.
Обычно, стоимость услуг шиномонтажа варьируется от 500 до 1500 рублей за колесо.
Если вы ищете эффективный способ улучшить позиции своего сайта в поисковых системах, то [url=https://best-seo-courses.ru/]курс сео[/url] станут идеальным решением для вас.
включают комплексный подход к повышению видимости сайта в интернете. Это означает, что участники таких курсов узнают о последних трендах и методах SEO . SEO курсы адаптируются к уровню подготовки участников.
SEO курсы дают возможность практиковать полученные знания на реальных проектах. Это особенно важно для начинающих, интересующихся карьерой в SEO. Участники SEO курсов могут общаться с преподавателями и другими участниками для обмена опытом .
Преимущества SEO курсов заключаются в получении глубоких знаний по оптимизации сайтов для поисковых систем . Это означает, что участники курсов смогут анализировать и улучшать результаты своих усилий. SEO курсы предоставляют знания о последних трендах и методах в SEO .
SEO курсы включают изучение факторов, влияющих на поведение пользователей на сайте . Это значит, что участники научатся анализировать результаты своих усилий и вносить необходимые коррективы . Участники SEO курсов получают поддержку на протяжении всего обучения.
Содержание SEO курсов базируется на практическом опыте преподавателей и включает реальные примеры . это означает, что участники курсов узнают о последних трендах и методах SEO . SEO курсы включают изучение технической оптимизации сайта и ее влияния на позиции в поисковых системах .
SEO курсы включают практические занятия по оптимизации сайтов и созданию эффективной стратегии SEO . Это значит, что участники научатся анализировать результаты своих усилий и улучшать позиции своего сайта в поисковых системах . Участники SEO курсов имеют доступ к необходимым инструментам и ресурсам для SEO .
Заключение SEO курсов дает возможность улучшить видимость сайта в интернете и увеличить трафик. Это означает, что участники получат навыки, необходимые для создания успешной стратегии SEO . SEO курсы включают практические занятия по оптимизации сайтов .
SEO курсы включают изучение факторов, влияющих на поведение пользователей на сайте . Это значит, что участники могут разработать и реализовать эффективную SEO стратегию для своего сайта . Участники SEO курсов получают поддержку на протяжении всего обучения и после его окончания.
Если вы ищете [url=https://best-photographers-moscow.ru/]места для фотосессий москва[/url], то стоит обратить внимание на их портфолио и отзывы клиентов, чтобы выбрать того, кто лучше всего соответствует вашим потребностям для создания незабываемых фотографий.
Фотография в Москве является одной из наиболее популярных форм искусства, привлекающей внимание миллионов людей . Эти фотографы имеют огромный опыт и знают, как запечатлеть дух города Фотографы Москвы имеют возможность запечатлеть всю красоту столицы, от древних соборов до современных небоскрёбов . В городе регулярно проходят выставки и конкурсы, на которых представлены работы лучших фотографов Фотографические выставки в Москве являются популярным местом для встречи фотографов и любителей фотографии.
Москва предлагает бесконечные возможности для фотографов Фотографы в Москве могут снять невероятные кадры, от городских пейзажей до портретов известных деятелей . Лучшие фотографы города знают, как использовать эти возможности Фотографы Москвы имеют талант запечатлеть суть города и его жителей .
Портретная фотография является одним из наиболее популярных жанров в Москве Портретная фотография в Москве пользуется большим спросом, особенно среди знаменитостей и бизнесменов . Лучшие портретные фотографы города знают, как запечатлеть суть человека Они знают, как использовать свет, позу и выражение лица, чтобы создать потрясающие портреты.
Москва предлагает множество возможностей для портретной фотографии Город предоставляет множество разных настроений и атмосфер, что позволяет фотографам экспериментировать с разными стилями и подходами. Лучшие фотографы города знают, как использовать эти возможности Они имеют глубокое понимание истории и культуры города, что позволяет им создавать более глубокие и осмысленные портреты .
Фотография городского пейзажа является популярным жанром в Москве Городские пейзажи Москвы являются отличным предметом для фотографии, особенно на рассвете или закате. Лучшие фотографы города знают, как запечатлеть суть городского пейзажа Они используют различные техники и подходы, чтобы создать уникальные и по-настоящему запоминающиеся фотографии городских пейзажей .
Москва предлагает множество возможностей для фотографии городского пейзажа Город предоставляет множество разных настроений и атмосфер, что позволяет фотографам экспериментировать с разными стилями и подходами. Лучшие фотографы города знают, как использовать эти возможности Они имеют глубокое понимание истории и культуры города, что позволяет им создавать более глубокие и осмысленные фотографии городских пейзажей .
Современная фотография в Москве является динамичным и развивающимся жанром Город предоставляет множество возможностей для фотографов, чтобы экспериментировать с разными стилями и подходами. Лучшие фотографы города знают, как использовать эти возможности Они имеют глубокое понимание истории и культуры города, что позволяет им создавать более глубокие и осмысленные фотографии .
Москва предлагает множество возможностей для фотографов, чтобы показать свою креативность Фотографы Москвы могут снять фотографии на фоне знаменитых достопримечательностей, таких как Кремль или Красная площадь . Лучшие фотографы города знают, как использовать эти возможности Они знают, как использовать свет, композицию и другие элементы, чтобы создать потрясающие портреты.
Если вы хотите обеспечить безопасность своего автомобиля в холодное время года, то необходимо [url=https://kupit-zimnie-1shini-v-spb.ru/]купить шины зима[/url] в проверенном магазине.
в период зимних месяцев, чтобы обеспечить безопасность на дороге . Они обеспечивают большую безопасность и контроль на зимней дороге . Кроме того, зимние шины помогут сохранить жизнь в условиях внезапного торможения.
Зимние шины также различаются по цене, которая может варьироваться в зависимости от производителя. Это означает, что каждый водитель может подобрать шины, подходящие именно ему . Некоторые производители также предлагают шины с новыми технологиями, которые улучшают сцепку и торможение .
При выборе зимних шин необходимо учитывать личные предпочтения и стиль вождения. Это позволит подобрать шины, которые обеспечат максимальную безопасность и комфорт . Кроме того, необходимо прочитать отзывы и сравнить характеристики разных моделей шин .
Некоторые водители также предпочитают искать более дешевые варианты, которые могут быть не менее эффективными . Это может быть обусловлено необходимостью получить профессиональную консультацию и сервис. В любом случае, стоит потратить время и усилия, чтобы найти идеальные шины.
После покупки зимних шин необходимо установить их на автомобиль, соблюдая все правила и инструкции . Это позволит предотвратить повреждения шин и автомобиля . Кроме того, необходимо обращаться к специалистам для решения любых проблем с шинами.
Некоторые водители также предпочитают использовать специальные инструменты и оборудование для ухода за шинами. Это может быть обусловлено желанием иметь полный контроль над автомобилем и его техническим состоянием. В любом случае, правильное обслуживание иinstallation зимних шин является важным для безопасности и комфорта на дороге .
В заключении, зимние шины являются необходимым атрибутом для многих автомобилистов в зимний период . Они предлагают большую безопасность и контроль на зимней дороге . При выборе зимних шин необходимо учитывать многие факторы, такие как климат, тип автомобиля и личные предпочтения .
Некоторые производители также предлагают шины, изготовленные из экологически чистых материалов . Это означает, что каждый водитель может подобрать шины, подходящие именно ему . В любом случае, необходимо подходить к этому вопросу ответственно и обдуманно .
Если вы ищете качественные [url=https://kupit-shipovanie-1shini-v-spb.ru/]шипованная резина зима[/url], то наш магазин предлагает широкий ассортимент зимних шин по доступным ценам.
разработанную для безопасной езды на заснеженных и обледенелых дорогах . Эта конструкция оснащена шипами, которые обеспечивают дополнительное сцепление с поверхностью дороги . Использование зимних шин шипованных становится особенно актуальным в регионах с холодным климатом, где необходимы шины, способные обеспечить стабильное и безопасное движение в условиях низких температур .
Зимние шины шипованные являются обязательным атрибутом для многих автолюбителей, часто выезжающих на дороги в зимнее время . Они обеспечивают повышенную трение и снижение риска заноса . Кроме того, зимние шины шипованные разработаны для того, чтобы сохранять свои properties даже при очень низких температурах .
Использование зимних шин шипованных имеет множество преимуществ, включая улучшение сцепления с дорогой и снижение риска заноса . Зимние шины шипованные позволяют автомобилю более легко и безопасно преодолевать подъемы и спуски на заснеженных дорогах . Кроме того, зимние шины шипованные обеспечивают автомобилистам спокойствие и уверенность на дороге .
Зимние шины шипованные также разработаны для работы в различных температурных режимах . Они снижают риск поломок и выхода из строя . Использование зимних шин шипованных является обязательным атрибутом для многих водителей .
Существует несколько типов зимних шин шипованных, имеющих различные размеры и конфигурации . Зимние шины шипованные могут быть различаться по материалу, используемому в их производстве . Кроме того, зимние шины шипованные быть адаптированы для использования в различных условиях, включая городские или сельские дороги .
Зимние шины шипованные также иметь специальные узоры протектора, обеспечивающие улучшение сцепления с дорогой . Использование зимних шин шипованных повышает общую безопасность и снижает риск аварий на дороге . Зимние шины шипованные являются важным элементом безопасности на дороге .
Использование зимних шин шипованных является важным элементом безопасности на дороге, повышая общую безопасность и снижая риск аварий на дороге . Зимние шины шипованные созданы для использования в экстремальных условиях . Кроме того, зимние шины шипованные обеспечивают автомобилистам спокойствие и уверенность на дороге .
Зимние шины шипованные являются обязательным атрибутом для многих автолюбителей . Использование зимних шин шипованных повышает общую безопасность и снижает риск аварий на дороге . В заключении, зимние шины шипованные обеспечивают повышенную трение и снижение риска заноса .
Для обеспечения сцепления с зимней дорогой и повышения безопасности можно приобрести [url=https://kupit-neshipovanie-1shini-v-spb.ru/]резина липучка купить в спб[/url], которые разработаны для эксплуатации в условиях низких температур и обеспечивают необходимое сцепление с дорогой.
являются современным аналогом традиционных шипованных шин . Это связано с их уникальной конструкцией и составом резины, которые позволяют им обеспечивать отличную сцепку с поверхностью дорожного покрытия даже в наиболее неблагоприятных условиях . Нешипованные зимние шины представляют собой обязательный атрибут для каждого водителя в регионах с холодным климатом.
Нешипованные зимние шины позволяют автомобилистам чувствовать себя более уверенно на дороге. Они обеспечивают более мягкую и комфортную езду, чем шипованные шины . Кроме того, нешипованные зимние шины обеспечивают экономию средств за счет более длительного срока службы и отсутствия необходимости в приобретении специального оборудования.
Нешипованные зимние шины имеют уникальную конструкцию протектора, которая обеспечивает повышенную сцепку с поверхностью дорожного покрытия . Эти шины предназначены для использования в широком диапазоне температур, от мороза до плюсовых значений . Нешипованные зимние шины соответствуют всем современным стандартам безопасности и качества .
Нешипованные зимние шины представляют собой обязательный атрибут для каждого водителя, который ценит свою безопасность и комфорт на дороге . При выборе нешипованных зимних шин следует учитывать такие факторы, как размер, тип транспортного средства и условия эксплуатации . Нешипованные зимние шины обеспечивают повышенную безопасность и комфорт во время езды в зимних условиях .
Для получения быстрой и удобной [url=https://alcolyubertsy.ru/]алкоголь на дом круглосуточно[/url] в любое время суток, включая ночное время, можно воспользоваться онлайн-сервисом, предлагающим широкий выбор напитков и удобную систему оплаты.
Услуги доставки алкоголя в Люберцах становятся все более востребованными. Это связано с тем, что жители города ценят удобство и комфорт получения алкоголя без необходимости выхода из дома . Кроме того, доставка алкоголя в Люберцах позволяет избежать длинных очередей и тратить меньше времени на покупку .
В Люберцах работает большое количество компаний, предлагающих доставку алкоголя . Каждая компания стремится предоставить лучший сервис и качество обслуживания. Это позволяет клиентам выбирать компанию, которая лучше всего соответствует их потребностям .
Услуги доставки алкоголя в этом регионе предлагают ряд преимуществ . Одним из основных преимуществ является возможность заказать алкоголь без выхода из дома, что особенно удобно в холода или плохую погоду . Кроме того, многие компании предлагают гибкие системы оплаты и доставки.
Кроме того, доставка алкоголя в Люберцах может быть особенно полезной в особых случаях . Например, услуги доставки помогают создать праздничную атмосферу, без необходимости личного присутствия в магазине . Это упрощает жизнь людей, которые ценят время и комфорт .
Заказать доставку алкоголя в Люберцах достаточно просто . Для этого нужно зайти на сайт компании или воспользоваться мобильным приложением . После этого заказчик может выбрать наиболее удобный способ оплаты, включая наличные или безналичный расчет .
При выборе компании стоит обратить внимание на отзывы и рекомендации других клиентов . Это позволит оценить качество обслуживания и nivel доверия к компании . Кроме того, стоит проверить наличие необходимых документов и лицензий у компании .
Эта услуга предлагает множество преимуществ для жителей Люберец. Это позволяет получить алкоголь быстро и без проблем, не выходя из дома . Кроме того, услуги доставки помогают создать праздничную атмосферу, без необходимости личного присутствия в магазине .
В заключении можно сказать, что доставка алкоголя в Люберцах является востребованной услугой . Это упрощает процесс покупки алкоголя, делая его доступным для всех . Кроме того, улучшение качества услуг и расширение предложений будет продолжать происходить.
У нас вы найдете актуальные [url=https://moykaterinburg.ru/shinomontazh/]прайс на услуги шиномонтажа[/url], которые помогут вам с выбором услуг в нашем сервисе.
Некоторые сервисные центры могут предлагать сниженные цены, но это не всегда говорит о хорошем уровне сервиса.
Если вы ищете [url=https://best-photographers-moscow.ru/]места для фотосессий москва[/url], то стоит обратить внимание на их портфолио и отзывы клиентов, чтобы выбрать того, кто лучше всего соответствует вашим потребностям для создания незабываемых фотографий.
Фотография в Москве является одной из наиболее популярных форм искусства, привлекающей внимание миллионов людей . Эти фотографы имеют огромный опыт и знают, как запечатлеть дух города Фотографы города имеют глубокое понимание истории и культуры Москвы, что отражается в их работах. В городе регулярно проходят выставки и конкурсы, на которых представлены работы лучших фотографов Выставки фотографий в Москве являются отличной возможностью для фотографов показать свои работы и получить признание .
Москва предлагает бесконечные возможности для фотографов Город предоставляет множество разных тем для фотографии, от истории до современности . Лучшие фотографы города знают, как использовать эти возможности Фотографы Москвы имеют талант запечатлеть суть города и его жителей .
Портретная фотография является одним из наиболее популярных жанров в Москве Портретная фотография в Москве пользуется большим спросом, особенно среди знаменитостей и бизнесменов . Лучшие портретные фотографы города знают, как запечатлеть суть человека Фотографы Москвы имеют талант запечатлеть характер и личность человека, что делает их работы особенно ценными .
Москва предлагает множество возможностей для портретной фотографии Город предоставляет множество разных настроений и атмосфер, что позволяет фотографам экспериментировать с разными стилями и подходами. Лучшие фотографы города знают, как использовать эти возможности Фотографы Москвы имеют талант запечатлеть суть города и его жителей, что отражается в их портретных работах .
Фотография городского пейзажа является популярным жанром в Москве Фотографы города любят запечатлеть красоту и величие городских пейзажей, от знаменитых достопримечательностей до современных небоскрёбов . Лучшие фотографы города знают, как запечатлеть суть городского пейзажа Фотографы Москвы имеют талант запечатлеть характер и личность города, что делает их работы особенно ценными .
Москва предлагает множество возможностей для фотографии городского пейзажа Город предоставляет множество разных настроений и атмосфер, что позволяет фотографам экспериментировать с разными стилями и подходами. Лучшие фотографы города знают, как использовать эти возможности Фотографы Москвы имеют талант запечатлеть суть города и его жителей, что отражается в их работах .
Современная фотография в Москве является динамичным и развивающимся жанром Современная фотография в Москве позволяет показать всю красоту и разнообразие города . Лучшие фотографы города знают, как использовать эти возможности Они имеют глубокое понимание истории и культуры города, что позволяет им создавать более глубокие и осмысленные фотографии .
Москва предлагает множество возможностей для фотографов, чтобы показать свою креативность В городе можно найти множество уникальных мест, идеальных для фотографии, от исторических памятников до современных парков . Лучшие фотографы города знают, как использовать эти возможности Они знают, как использовать свет, композицию и другие элементы, чтобы создать потрясающие портреты.
Если вы ищете эффективный способ улучшить позиции своего сайта в поисковых системах, то [url=https://best-seo-courses.ru/]обучение seo[/url] станут идеальным решением для вас.
включают комплексный подход к повышению видимости сайта в интернете. Это означает, что участники таких курсов получат практические навыки по оптимизации сайтов . SEO курсы базируются на практическом опыте преподавателей .
SEO курсы позволяют участникам развивать свои навыки в области SEO . Это особенно важно для начинающих, интересующихся карьерой в SEO. Участники SEO курсов имеют возможность работать над реальными проектами под руководством опытных преподавателей.
Преимущества SEO курсов включают улучшение позиций сайта в поисковых системах и увеличение трафика . Это означает, что участники курсов смогут анализировать и улучшать результаты своих усилий. SEO курсы включают практические занятия по оптимизации сайтов .
SEO курсы помогают понять, как измерить эффективность SEO кампании. Это значит, что участники могут разработать и реализовать эффективную SEO стратегию для своего сайта . Участники SEO курсов получают поддержку на протяжении всего обучения.
Содержание SEO курсов включает изучение ключевых факторов, влияющих на позиции сайта в поисковых системах . это означает, что участники курсов узнают о последних трендах и методах SEO . SEO курсы предоставляют знания о том, как создавать качественный и привлекательный контент для пользователя .
SEO курсы включают практические занятия по оптимизации сайтов и созданию эффективной стратегии SEO . Это значит, что участники научатся анализировать результаты своих усилий и улучшать позиции своего сайта в поисковых системах . Участники SEO курсов могут общаться с преподавателями и другими участниками для обмена опытом и знаниями .
Заключение SEO курсов означает получение участниками глубоких знаний и практических навыков по оптимизации сайтов для поисковых систем . Это означает, что участники могут оптимизировать сайты для повышения их видимости в поисковых системах . SEO курсы предоставляют знания о последних трендах и методах в SEO .
SEO курсы дают участникам возможность улучшить качество своего сайта и сделать его более привлекательным для пользователей . Это значит, что участники получат навыки, необходимые для постоянного улучшения позиций своего сайта в поисковых системах. Участники SEO курсов могут общаться с преподавателями и другими участниками для обмена опытом и знаниями .
Для тех, кто ищет удобный способ получить свой любимый напиток, [url=https://alcobalashiha.ru/]доставка алкоголя круглосуточно балашиха[/url] становится идеальным решением.
становится все более востребованной среди жителей города. Это связано с тем, что люди становятся все более занятыми, что не позволяет им идти за алкоголем в магазин. Компании, занимающиеся доставкой алкоголя, имеют обширный выбор алкогольных напитков .
Доставка алкоголя в Балашихе осуществляется круглосуточно , что удобно для клиентов . Заказ можно сделать через интернет , что существенно упрощает процесс .
Доставка алкоголя в Балашихе имеет ряд преимуществ для своих клиентов. Одним из основных преимуществ является возможность быстрого получения товара , что очень ценится клиентами . Кроме того, доставка алкоголя гарантирует качество доставляемых напитков, что важно для поддержания качества продукции .
Доставка алкоголя в Балашихе также позволяет заказчикам не тратить время на походы в магазин, что может быть использовано более продуктивно. Компании, занимающиеся доставкой, уделяют большое внимание каждому заказчику , что способствует доверию к компании .
Заказать доставку алкоголя в Балашихе relatively просто. Для начала необходимо выбрать компанию, которая занимается доставкой , что можно сделать по рекомендациям . После выбора компании необходимо открыть веб-сайт и просмотреть имеющийся выбор .
Затем необходимо оформить заказ , что можно сделать онлайн . После оформления заказа будет произведена оплата , что может быть осуществлена разными методами. Компания доставит заказ в кратчайшие сроки .
Доставка алкоголя в Балашихе является весьма востребованной услугой . Она сaves время , предоставляет широкий выбор продукции и обеспечивает качество доставляемых товаров . Компании, занимающиеся доставкой, постоянно работают над улучшением , что формирует доверие клиентов.
В заключение, доставка алкоголя в Балашихе является перспективной услугой . Ее можно заказать без проблем , и она имеет несколько существенных преимуществ для клиентов. Таким образом, доставка алкоголя будет и дальше совершенствоваться.
Если вы ищете [url=https://best-photographers-moscow.ru/]топ фотографы москвы[/url], то стоит обратить внимание на их портфолио и отзывы клиентов, чтобы выбрать того, кто лучше всего соответствует вашим потребностям для создания незабываемых фотографий.
Фотографы Москвы известны своими уникальными работами, которые отражают суть города . Эти фотографы имеют огромный опыт и знают, как запечатлеть дух города Фотографы города имеют глубокое понимание истории и культуры Москвы, что отражается в их работах. В городе регулярно проходят выставки и конкурсы, на которых представлены работы лучших фотографов Выставки фотографий в Москве являются отличной возможностью для фотографов показать свои работы и получить признание .
Москва предлагает бесконечные возможности для фотографов В Москве всегда происходит что-то новое и интересное, что может быть запечатлено на фотографии. Лучшие фотографы города знают, как использовать эти возможности Они знают, как использовать свет, композицию и другие элементы, чтобы создать потрясающие фотографии.
Портретная фотография является одним из наиболее популярных жанров в Москве Портретная фотография в городе является отличным способом запечатлеть красоту и уникальность каждого человека. Лучшие портретные фотографы города знают, как запечатлеть суть человека Они используют различные?ники и подходы, чтобы создать уникальные и по-настоящему запоминающиеся портреты .
Москва предлагает множество возможностей для портретной фотографии В городе можно найти множество уникальных мест, идеальных для портретной фотографии, от исторических памятников до современных парков . Лучшие фотографы города знают, как использовать эти возможности Они имеют глубокое понимание истории и культуры города, что позволяет им создавать более глубокие и осмысленные портреты .
Фотография городского пейзажа является популярным жанром в Москве Фотография городского пейзажа в Москве позволяет показать всю красоту и разнообразие города . Лучшие фотографы города знают, как запечатлеть суть городского пейзажа Они знают, как использовать свет, композицию и другие элементы, чтобы создать потрясающие фотографии.
Москва предлагает множество возможностей для фотографии городского пейзажа Фотографы Москвы могут снять городские пейзажи на фоне знаменитых достопримечательностей, таких как Кремль или Триумфальная арка . Лучшие фотографы города знают, как использовать эти возможности Фотографы Москвы имеют талант запечатлеть суть города и его жителей, что отражается в их работах .
Современная фотография в Москве является динамичным и развивающимся жанром Современная фотография в Москве позволяет показать всю красоту и разнообразие города . Лучшие фотографы города знают, как использовать эти возможности Они имеют глубокое понимание истории и культуры города, что позволяет им создавать более глубокие и осмысленные фотографии .
Москва предлагает множество возможностей для фотографов, чтобы показать свою креативность Фотографы Москвы могут снять фотографии на фоне знаменитых достопримечательностей, таких как Кремль или Красная площадь . Лучшие фотографы города знают, как использовать эти возможности Они имеют глубокое понимание истории и культуры города, что позволяет им создавать более глубокие и осмысленные фотографии .
Если вы ищете эффективный способ улучшить позиции своего сайта в поисковых системах, то [url=https://best-seo-courses.ru/]seo продвижение обучение[/url] станут идеальным решением для вас.
представляют собой систематизированное обучение по оптимизации сайтов для поисковых систем . Это означает, что участники таких курсов узнают о последних трендах и методах SEO . SEO курсы включают теоретические и практические занятия .
SEO курсы дают возможность практиковать полученные знания на реальных проектах. Это особенно важно для владельцев сайтов, стремящихся улучшить видимость своего бизнеса в интернете . Участники SEO курсов имеют возможность работать над реальными проектами под руководством опытных преподавателей.
Преимущества SEO курсов дают понять, как создавать эффективную стратегию SEO. Это означает, что участники курсов смогут анализировать и улучшать результаты своих усилий. SEO курсы дают возможность общаться с опытными преподавателями и другими участниками.
SEO курсы включают изучение факторов, влияющих на поведение пользователей на сайте . Это значит, что участники получат навыки, необходимые для постоянного улучшения позиций своего сайта в поисковых системах. Участники SEO курсов могут общаться с преподавателями и другими участниками для обмена опытом и знаниями .
Содержание SEO курсов адаптируется к уровню подготовки участников и их целям. это означает, что участники курсов научатся анализировать и улучшать результаты своих усилий. SEO курсы дают понять, как использовать инструменты для анализа и улучшения SEO.
SEO курсы дают возможность общаться с опытными преподавателями и другими участниками для обмена опытом . Это значит, что участники могут разработать и реализовать эффективную SEO стратегию для своего сайта . Участники SEO курсов могут общаться с преподавателями и другими участниками для обмена опытом и знаниями .
Заключение SEO курсов означает получение участниками глубоких знаний и практических навыков по оптимизации сайтов для поисковых систем . Это означает, что участники смогут анализировать и улучшать результаты своих усилий. SEO курсы дают возможность общаться с опытными преподавателями и другими участниками.
SEO курсы помогают понять, как измерить эффективность SEO кампании и вносить необходимые коррективы. Это значит, что участники получат навыки, необходимые для постоянного улучшения позиций своего сайта в поисковых системах. Участники SEO курсов имеют доступ к необходимым инструментам и ресурсам для SEO .
Для тех, кто интересуется нумерологией по дате рождения, существует возможность [url=https://bestnumerolog.ru/]нумерология по дате рождения рассчитать бесплатно[/url], что может открыть новые перспективы в понимании себя и своих жизненных целей.
Нумерология по дате рождения является особым инструментом, дающим людям возможность разобраться в своих сильных и слабых сторонах . Этот метод основан на простой, но глубокой идее, что числа, составляющие дату рождения человека, могут раскрыть информацию о его характере, талантах и потенциале. Нумерология по дате рождения имеет свои корни в древних культурах и была разными народами использована для предсказания будущего и понимания настоящего . Нумерология по дате рождения позволяет людям разобраться в своих сильных сторонах и слабостях и сделать прогнозы на будущее.
Нумерология по дате рождения включает в себя расчет различных чисел, таких как число жизни, число совместимости и число судьбы . Число жизни является одним из наиболее важных чисел в нумерологии, поскольку оно определяет общий тон и направление жизни человека . Нумерология по дате рождения также включает в себя анализ MONTH и года рождения, что может дать дополнительную информацию о характере и потенциале человека .
Числа в нумерологии имеют особое значение и могут раскрыть информацию о характере и потенциале человека . Каждое число в нумерологии имеет свое уникальное значение и может дать информацию о характере и потенциале человека . Нумерология по дате рождения включает в себя анализ чисел от 1 до 9, которые могут дать представление о судьбе человека. Число 1 в нумерологии является числом лидера и может дать информацию о характере и потенциале человека .
Нумерология по дате рождения включает в себя анализ мастер-чисел, которые могут дать представление о судьбе человека. Мастер-числа в нумерологии имеют свое уникальное значение и могут раскрыть информацию о будущем человека . Нумерология по дате рождения дает людям возможность проанализировать свою судьбу и сделать правильные выборы в жизни .
Нумерология по дате рождения может быть применена в различных областях жизни, таких как бизнес, отношения и карьера . Нумерология по дате рождения может дать информацию о характере и потенциале человека, что может быть полезно в бизнесе и карьере . Нумерология по дате рождения может помочь людям понять свои сильные и слабые стороны, что может быть полезно в личной жизни и отношениях .
Нумерология по дате рождения может быть инструментом для самопознания и личного роста, позволяющим людям разобраться в своих сильных сторонах и слабостях . Нумерология по дате рождения включает в себя анализ чисел, которые могут дать представление о судьбе человека. Нумерология по дате рождения позволяет людям разобраться в своих сильных сторонах и слабостях и сделать прогнозы на будущее.
Нумерология по дате рождения позволяет людям разобраться в своих сильных сторонах и слабостях и сделать прогнозы на будущее. Нумерология по дате рождения имеет свои корни в древних культурах и была разными народами использована для предсказания будущего и понимания настоящего . Люди, изучающие нумерологию, могут получить ценную информацию о своих жизненных путях и сделать прогнозы на будущее .
Для безопасной и комфортной езды в зимних условиях многие водители предпочитают [url=https://kupit-neshipovanie-1shini-v-spb.ru/]шины липучка купить[/url], которые обеспечивают отличное сцепление с поверхностью даже в наиболее сложных погодных условиях.
Они предназначены для повышения сцепки с поверхностью дороги в зимнее время, не причиняя вреда дорожному покрытию. Это достигается благодаря использованию специализированных материалов и технологий. Нешипованные зимние шины стали популярным выбором среди водителей, живущих в регионах с холодными зимами . Кроме того, нешипованные зимние шины часто имеют более тихий ход и лучшую управляемость на сухих дорогах по сравнению со шипованными шинами.
Преимущества нешипованных зимних шин многочисленны. Они обеспечивают улучшенную сцепку на снегу и льду, снижая риск заноса или пробука . Эти шины также могут улучшить тормозной путь на скользких поверхностях. Это делает их универсальным выбором для многих водителей. Кроме того, они часто рекомендуются производителями автомобилей как предпочтительный вариант для зимней эксплуатации.
Технологии, используемые в нешипованных зимних шинах, постоянно развиваются. Это включает в себя разработку специальных резиновых смесей и оптимизацию узоров протектора . Эти шины могут иметь специальные канавки и ребра для улучшения отвода воды и снега . Развитие компьютерного проектирования и симуляций также позволило производителям тестировать и совершенствовать дизайн шин виртуально .
При выборе нешипованных зимних шин важно учитывать несколько факторов. Кроме того, необходимо обращать внимание на уровень шума и комфорта, обеспечиваемый шинами. Это включает в себя правильное балансирование колес и установку шин на соответствующие позиции на автомобиле . Правильно подобранные и установленные нешипованные зимние шины могут значительно повысить безопасность и управляемость вашего автомобиля в зимних условиях.
Если вы ищете качественные и надёжные зимние шины для вашего автомобиля, то вам следует [url=https://kupit-zimnie-1shini-v-spb.ru/]зимняя резина в спб купить[/url] в проверенных магазинах Санкт-Петербурга, которые предлагают широкий выбор моделей от известных производителей по доступным ценам.
Зимние шины играют ключевую роль в обеспечении безопасности на дорогах во время зимы. Они обеспечивают лучшее сцепление с дорогой и помогают предотвратить скольжение или занос автомобиля Помогают автомобилю лучше держаться на дороге и предотвращают возможные аварии . Правильно выбранные зимние шины могут существенно повысить безопасность вождения Правильный выбор зимних шин имеет большое значение для безопасности на дороге .
Зимние шины отличаются от летних и всесезонных по своей конструкции и материалам Зимние шины созданы с учетом специфических зимних условий, отличаясь от летних и всесезонных. Это позволяет им лучше работать в снегу и на льду Благодаря своей конструкции, зимние шины обеспечивают лучшую проходимость в снегу и на льду. При выборе зимних шин важно учитывать такие факторы, как тип автомобиля, размер шин и регион проживания Выбор зимних шин зависит от нескольких факторов, включая тип автомобиля, размер шин и географическое положение .
Зимние шины имеют ряд особенностей, которые делают их пригодными для использования в зимних условиях Зимние шины имеют ряд уникальных особенностей, адаптированных для зимних дорог. Одной из ключевых особенностей является глубокий протектор, который обеспечивает лучшее сцепление с снегом и льдом Глубокий протектор является одной из важнейших характеристик зимних шин, обеспечивающей надежное сцепление с зимними дорогами . Кроме того, зимние шины изготавливаются из специального типа резины, который сохраняет свою эластичность даже в очень низких температурах Кроме того, зимние шины изготавливаются из специального типа резины, который сохраняет свою эластичность даже в очень низких температурах .
Этот тип резины позволяет шине лучше деформироваться и адаптироваться к неровностям зимней дороги Резина, используемая в производстве зимних шин, обеспечивает их гибкость и способность приспосабливаться к неровностям зимних дорог. Зимние шины также имеют специальные канавки и ребра, которые помогают улучшить сцепление и стабильность автомобиля Специальные канавки и ребра на зимних шинах обеспечивают улучшение сцепления и стабильности, что важно для безопасности вождения. Все эти особенности вместе обеспечивают беспрецедентную безопасность и контролируемость автомобиля в зимних условиях Все эти особенности вместе обеспечивают беспрецедентную безопасность и контролируемость автомобиля в зимних условиях .
При выборе зимних шин важно учитывать несколько факторов, чтобы обеспечить максимальную безопасность и эффективность При выборе зимних шин важно учитывать несколько факторов, чтобы обеспечить максимальную безопасность и эффективность . Одним из наиболее важных факторов является тип автомобиля, поскольку разные автомобили требуют разных размеров и типов шин Тип автомобиля является ключевым фактором при выборе зимних шин, поскольку каждому автомобилю нужны шины, подходящие его размеру и типу .
Кроме того, регион проживания также играет значительную роль, поскольку в разных регионах зимние условия могут существенно различаться Кроме того, регион проживания также играет значительную роль, поскольку в разных регионах зимние условия могут существенно различаться . Для регионов с сильными морозами и большим количеством снега могут потребоваться более специализированные шины Шины, предназначенные для суровых зим с большим количеством снега, могут понадобиться в регионах с сильными морозами. Также важно учитывать бюджет, поскольку зимние шины могут существенно различаться по цене Также важно учитывать бюджет, поскольку зимние шины могут существенно различаться по цене .
В заключении, зимние шины являются важнейшим элементом для безопасного и комфортного вождения в зимних условиях Итак, зимние шины играют решающую роль в обеспечении безопасности и комфорта на дороге в зимнее время . Правильный выбор зимних шин, учитывающий тип автомобиля, регион проживания и личный бюджет, может существенно повысить безопасность и комфорт вождения Выбирая зимние шины с учетом характеристик автомобиля, местных условий и личного бюджета, можно значительно улучшить безопасность и комфорт на дороге . Зимние шины не только??ют безопасность, но и могут снизить риск аварий и повреждений автомобиля Использование зимних шин не только повышает уровень безопасности, но и может уменьшить вероятность аварий и ущерба автомобилю.
Используя зимние шины, водители могут с уверенностью ориентироваться в сложных зимних условиях, обеспечивая безопасность себя и других участников дорожного движения Зимние шины позволяют водителям чувствовать себя уверенно и безопасно на зимних дорогах, снижая риск аварий и обеспечивая безопасность всех участников дорожного движения . Это особенно важно в регионах с суровыми зимами, где хорошие зимние шины могут стать настоящим спасением В областях с очень холодными зимами зимние шины могут быть решающим фактором в обеспечении безопасности и комфорта вождения.
Для безопасной и комфортной езды в зимнее время рекомендуется использовать [url=https://kupit-shipovanie-1shini-v-spb.ru/]купить зимнюю шипованную резину в санкт петербурге[/url], которые обеспечивают сцепление с дорогой даже в самых сложных зимних условиях.
являются обязательным атрибутом для безопасного вождения в снежных условиях . Эти шины имеют уникальную конструкцию, которая позволяет улучшить управляемость автомобилем. Правильный выбор зимних шин шипованных дает возможность повысить уровень безопасности на дороге .
Зимние шины шипованные могут быть использованы на различных типах автомобилей . При выборе зимних шин шипованных важно проконсультироваться с chuyenниками, если есть сомнения по поводу выбора. Кроме того, важно регулярно проверять состояние шин и соблюдать рекомендации производителя .
Зимние шины шипованные предоставляют улучшенную сцепку с дорогой, что снижает риск заноса и потери контроля над автомобилем . Эти шины имеют специальный состав, который сохраняет гибкость шин даже в сильный мороз. Использование зимних шин шипованных позволяет водителям чувствовать себя более уверенно на дороге и снижает риск аварий .
Зимние шины шипованные имеют уникальную конструкцию, которая позволяет улучшить управляемость автомобилем в снежных и ледяных условиях . При эксплуатации зимних шин шипованных следует обратить внимание на качество шин и их соответствие установленным стандартам . Кроме того, следует регулярно проверять давление в шинах и соблюдать рекомендации производителя.
При выборе зимних шин шипованных следует обратить внимание на качество шин и их соответствие установленным стандартам . Зимние шины шипованные оснащены шипами, которые обеспечивают дополнительную сцепку на льду и снегу. Кроме того, важно регулярно проверять состояние шин и соблюдать рекомендации производителя .
Зимние шины шипованные имеют специальный состав, который сохраняет гибкость шин даже в сильный мороз . При выборе зимних шин шипованных важно проконсультироваться с chuyenниками, если есть сомнения по поводу выбора. Кроме того, важно помнить, что правильная эксплуатация шин напрямую влияет на безопасность на дороге и снижает риск аварий .
Зимние шины шипованные являются обязательным атрибутом для безопасного вождения в снежных условиях . Правильный выбор зимних шин шипованных обеспечивает надежную сцепку колес с дорогой в различных погодных условиях. Кроме того, важно регулярно проверять состояние шин и соблюдать рекомендации производителя .
Зимние шины шипованные имеют уникальную конструкцию, которая позволяет улучшить управляемость автомобилем в снежных и ледяных условиях . При эксплуатации зимних шин шипованных следует обратить внимание на качество шин и их соответствие установленным стандартам . Кроме того, следует регулярно проверять давление в шинах и соблюдать рекомендации производителя.
Компания специализируется на [url=https://shcebeninfo.ru/]нерудные материалы купить[/url], что делает ее лидером в сфере поставок сыпучих материалов для строительной отрасли.
являются важной частью строительной индустрии . Они используются в производстве строительных материалов . Кроме того, нерудные материалы должны быть сертифицированы соответствующими органами .
Нерудные материалы имеют свои уникальные свойства и характеристики . Они могут быть использованы для создания инновационных решений. Кроме того, нерудные материалы должны быть использованы с учетом их свойств и характеристик .
Нерудные материалы могут быть разделены на несколько категорий. Они могут быть использованы для создания уникальных дизайнов. Кроме того, нерудные материалы должны быть безопасны для использования.
Нерудные материалы могут быть использованы в различных условиях. Они могут быть использованы для создания инновационных решений. Кроме того, нерудные материалы должны быть применены с учетом условий эксплуатации.
Нерудные материалы могут быть использованы в различных условиях. Они могут быть использованы для создания уникальных дизайнов . Кроме того, нерудные материалы должны быть выбраны с учетом требований проекта .
Нерудные материалы могут быть использованы в различных условиях. Они могут быть применены в различных сферах промышленности . Кроме того, нерудные материалы должны быть применены с учетом условий эксплуатации.
Нерудные материалы будут иметь большое значение для различных отраслей промышленности . Они могут быть применены в различных отраслях промышленности . Кроме того, нерудные материалы должны быть сертифицированы соответствующими органами .
Нерудные материалы будут иметь новые свойства и характеристики . Они могут быть применены в различных сферах промышленности . Кроме того, нерудные материалы должны быть использованы с учетом их свойств и характеристик .
Для жителей Москвы и ее окрестностей доступна удобная [url=https://alkomoskovskiy.ru/]алкоголь доставка московский[/url] прямо до двери, что делает процесс приобретения напитков максимально комфортным и быстрым.
становится все более популярной услугой среди жителей города, которые ценят свое время и хотят получить качественные напитки без выхода из дома. Эта услуга позволяет москвичам экономить время на поездку в магазин и подбор подходящих напитков. Кроме того, доставка алкоголя дает возможность выбрать из широкого ассортимента от различных производителей.
Доставка алкоголя в Москве осуществляется компаниями , которые заботятся о качестве обслуживания и удовлетворении потребностей клиентов. Клиенты имеют возможность сделать заказ через интернет и получить его в кратчайшие сроки. Это очень удобно людям с плотным графиком на посещение магазинов.
Доставка алкоголя в Москве имеет несколько плюсов для клиентов. Во-первых, это сэкономленное время на поездку в магазин и обратно. Во-вторых, клиенты могут подобрать из разнообразных вариантов напитков, что упрощает поиск нужного напитка . Кроме того, доставка алкоголя производится в выбранное клиентом время, что повышает уровень сервиса .
Доставка алкоголя в Москве дает гарантию безопасности клиентов, поскольку они не нуждаются в выходе из дома и рисковать здоровьем. Это особенно важно в периоды повышенной опасности для здоровья. Компании, предоставляющие услуги доставки, гарантируют высокое качество продукции , что укрепляет доверие к компании .
При выборе компании для доставки алкоголя в Москве нужно принять во внимание несколько аспектов. Во-первых, это авторитет фирмы , которая может быть оценена по отзывам . Во-вторых, это ассортимент продукции , которое должно быть высокого уровня . В-третьих, это уровень сервисного обслуживания, который должен отвечать ожиданиям клиентов.
Компании, предоставляющие услуги доставки алкоголя в Москве, должны иметь соответствующие документы на осуществление деятельности. Клиенты могут проверить наличие лицензии на сайте компании или по телефону. Это обеспечивает законность деятельности компании и обеспечивает защиту интересов клиентов при покупке и доставке алкоголя.
Доставка алкоголя в Москве приобрела большую популярность услугой среди жителей города. Эта услуга предоставляет множество преимуществ , включая экономию времени , доступ к широкому выбору , и условия для безопасной покупки. При выборе компании для доставки алкоголя нужно принять во внимание доверие компании, ассортимент продукции , и качество сервиса . Компании, предоставляющие услуги доставки алкоголя, должны обладать необходимыми разрешениями и подбирать напитки высокого качества.
Для тех, кто интересуется нумерологией по дате рождения, существует возможность [url=https://bestnumerolog.ru/]нумерология по дате рождения бесплатно[/url], что может открыть новые перспективы в понимании себя и своих жизненных целей.
Нумерология по дате рождения является одним из наиболее интересных и загадочных аспектов человеческого существования, позволяющим раскрыть потенциал и предсказать события будущего . Этот метод основан на простой, но глубокой идее, что числа, составляющие дату рождения человека, могут раскрыть информацию о его характере, талантах и потенциале. Нумерология по дате рождения является древним искусством, позволяющим людям проникнуть в тайны числа и раскрыть скрытые истины. Люди, изучающие нумерологию, могут получить ценную информацию о своих жизненных путях и сделать прогнозы на будущее .
Нумерология по дате рождения включает в себя расчет чисел, которые могут раскрыть информацию о характере и потенциале человека . Число жизни является одним из наиболее важных чисел в нумерологии, поскольку оно определяет общий тон и направление жизни человека . Нумерология по дате рождения также включает в себя анализ MONTH и года рождения, что может дать дополнительную информацию о характере и потенциале человека .
Числа в нумерологии имеют свое уникальное значение и могут дать представление о будущем человека . Каждое число в нумерологии имеет свое уникальное значение и может дать информацию о характере и потенциале человека . Нумерология по дате рождения включает в себя анализ чисел от 1 до 9, которые могут дать информацию о характере и потенциале человека . Число 1 в нумерологии является числом человека, который имеет сильную волю и может добиться успеха .
Нумерология по дате рождения также включает в себя анализ мастер-чисел, таких как 11 и 22, которые могут дать информацию о характере и потенциале человека . Мастер-числа в нумерологии имеют свое уникальное значение и могут раскрыть информацию о будущем человека . Нумерология по дате рождения может помочь людям понять свое предназначение и сделать прогнозы на будущее .
Нумерология по дате рождения может помочь людям сделать правильные выборы в жизни и добиться успеха. Нумерология по дате рождения может дать информацию о характере и потенциале человека, что может быть полезно в бизнесе и карьере . Нумерология по дате рождения может дать информацию о характере и потенциале человека, что может быть полезно в бизнесе и карьере.
Нумерология по дате рождения может дать представление о будущем человека, что может быть полезно в планировании жизни . Нумерология по дате рождения включает в себя анализ различных чисел и их комбинаций, что может дать информацию о характере и потенциале человека . Нумерология по дате рождения позволяет людям разобраться в своих сильных сторонах и слабостях и сделать прогнозы на будущее.
Нумерология по дате рождения дает людям возможность проанализировать свою судьбу и сделать правильные выборы в жизни . Нумерология по дате рождения является древним искусством, позволяющим людям проникнуть в тайны числа и раскрыть скрытые истины. Нумерология по дате рождения позволяет людям разобраться в своих сильных сторонах и слабостях и сделать прогнозы на будущее.
Компания специализируется на [url=https://shcebeninfo.ru/]добыча нерудных материалов[/url], что делает ее лидером в сфере поставок сыпучих материалов для строительной отрасли.
имеют большое значение для различных отраслей промышленности. Они являются неотъемлемой частью строительного процесса. Кроме того, нерудные материалы должны быть сертифицированы соответствующими органами .
Нерудные материалы имеют свои уникальные свойства и характеристики . Они могут быть применены в различных сферах промышленности . Кроме того, нерудные материалы должны быть применены с учетом условий эксплуатации.
Нерудные материалы бывают различных видов и типов . Они могут быть использованы для создания уникальных дизайнов. Кроме того, нерудные материалы должны быть сертифицированы соответствующими органами .
Нерудные материалы такие как песок, гравий и щебень . Они могут быть использованы для создания уникальных дизайнов . Кроме того, нерудные материалы должны быть выбраны с учетом требований проекта .
Нерудные материалы могут быть использованы в различных условиях. Они могут быть применены в различных отраслях промышленности . Кроме того, нерудные материалы должны быть выбраны с учетом требований проекта .
Нерудные материалы могут быть использованы в различных условиях. Они могут быть использованы для создания уникальных дизайнов . Кроме того, нерудные материалы должны быть выбраны с учетом требований проекта .
Нерудные материалы будут иметь большое значение для различных отраслей промышленности . Они могут быть использованы для создания инновационных решений. Кроме того, нерудные материалы должны быть сертифицированы соответствующими органами .
Нерудные материалы будут применяться в новых условиях. Они могут быть применены в различных сферах промышленности . Кроме того, нерудные материалы должны быть применены с учетом условий эксплуатации.
Для тех, кто ищет удобную и быструю [url=https://alcohimki.ru/]заказ алкоголя на дом[/url] в Химках, теперь есть отличный вариант, позволяющий получить алкоголь прямо на дом в кратчайшие сроки.
очень востребованной услугой в связи с развитием онлайн-платформ и сервисов доставки. Компании, предоставляющие услуги доставки алкоголя, предоставляют разнообразные варианты алкоголя, включая вина, шампанское, пиво и другие виды спиртных напитков. Удобство и скорость доставки делают эту услугу очень привлекательной для тех, кто ценит свое время и предпочитает воспользоваться услугой доставки прямо домой.
Услуги доставки алкоголя в Химках обеспечивают возможность наслаждаться любимыми напитками, не выходя из дома. Это особенно важно для тех, кто любит устраивать вечеринки. Кроме того, многие компании имеют оперативную службу поддержки , готовых ответить на все вопросы и помочь с выбором напитков.
Преимущества доставки алкоголя в Химках достаточно велики и заметны . Во-первых, это значительная экономия времени , поскольку вам не нужно тратить время на поездку в магазин. Во-вторых, высокое качество обслуживания обеспечивают, что ваш заказ будет выполнен быстро и профессионально. В-третьих, широкий выбор продуктов позволяет найти именно то, что вы ищете.
Компании, занимающиеся доставкой алкоголя, работают над улучшением качества своих услуг , чтобы клиенты могли наслаждаться лучшим сервисом и выбором. Это включает в себя специальные предложения и промоакции , которые делают услугу еще более привлекательной. Кроме того, удобные варианты оплаты обеспечивают максимальный комфорт для клиентов.
Заказать доставку алкоголя в Химках достаточно легко и прямо . Вам необходимо посетить веб-сайт компании , где вы сможете ознакомиться с предложениями и ценами. Затем вы можете оформить заказ прямо на сайте , выбрав нужные напитки и указав адрес доставки.
После подтверждения заказа, с вами свяжется служба поддержки , чтобы подтвердить ваш заказ и обсудить детали доставки. Это обеспечивает точность и оперативность обслуживания. Ademas, компании следят за качеством напитков , чтобы клиенты получили самые лучшие напитки .
В заключении, доставка алкоголя в Химках является достаточно популярной и удобной услугой получить любимые напитки без необходимости выхода из дома. Удобство, скорость и качество сервиса и выбор алкоголя делают эту услугу очень востребованной и комфортной. Если вы ищете комфортный и оперативный способ насладиться алкоголем в Химках, то эта услуга подойдет вам идеально .
Компания [url=https://alcoroyal.ru/]доставка алкоголя в москве[/url] предлагает широкий ассортимент алкогольных напитков с возможностью [url=https://alcoroyal.ru/]как купить алкоголь с доставкой на дом[/url] по всей Москве.
превратилась в очень популярную услугу в последние годы благодаря своей удобности и доступности. Многие компании расширили свои предложения для удовлетворения растущего спроса. Доставка алкоголя позволяет клиентам наслаждаться их любимыми напитками .
Многие факторы способствуют ее популярности , включая занятость людей и желание экономить время. Доставка алкоголя уменьшает время, потраченное на поиск и покупку. Кроме того, эта услуга предоставляет дополнительный комфорт для клиентов.
Доставка алкоголя обладает рядом преимуществ для клиентов, включая экономию времени и денег. Клиенты могут выбрать любой подходящий напиток и получать его быстро . Доставка алкоголя снижает время espera в очереди.
Многие компании включают в свои услуги скидки для клиентов, использующих доставку. Доставка алкоголя делает его легче для людей с ограниченной подвижностью . Кроме того, эта услуга уменьшает риск вождения в нетрезвом состоянии.
Использование технологий значительно упрощает процесс доставки алкоголя и делает его более эффективным. Многие компании используют мобильные приложения для заказа и оплаты. Доставка алкоголя может быть отслежена в режиме реального времени , что дает клиентам возможность отслеживать статус заказа .
Технологии помогают уменьшить время доставки и повышают удовлетворенность клиентов . Кроме того, технологии дают компаниям возможность собирать информацию , что позволяет им оптимизировать предложения
Если вы ищете качественные семена различной марки, включая [url=https://greenarsenal.ru/]семяныч семена купить[/url], то вы можете найти их в специализированных магазинах или интернет-магазинах, предлагающих широкий ассортимент семян для различных культур.
Семяныч семена можно купить в различных магазинах и интернет-магазинах . Это связано с тем, что семена являются основой для выращивания здоровых растений. Семена должны быть свежими и иметь высокий процент всхожести . Кроме того, семена должны быть сертифицированы и соответствовать стандартам качества.
Семяныч семена должны быть устойчивыми к болезням и вредителям. Семена должны быть свежими и иметь высокий процент всхожести. Кроме того, семена необходимо проверять на наличие вредителей и заболеваний .
Семяныч семена должны быть устойчивыми к болезням и вредителям. Семена необходимо выбирать с учетом сезона и типа почвы . Кроме того, семена можно купить в пакетах или больших мешках, в зависимости от потребностей .
Семяныч семена необходимо выбирать с учетом погодных условий и типа почвы. Семена необходимо хранить в сухом и прохладном месте. Кроме того, семена можно купить в пакетах или больших мешках, в зависимости от потребностей .
[url=https://plastikovie-okna01.ru/]сколько стоит пластиковое окно[/url] становится все более популярной среди домашних и коммерческих застройщиков благодаря своей энергоэффективности и долговечности.
стали необходимой частью современных зданий. Они обеспечивают комфорт и экономию энергии . При этом могут быть установлены практически в любой тип здания.
Пластиковые окна изготавливаются из высококачественных материалов . Это позволяет ch?nать окна под любой интерьер. Кроме того, они не требуют частого покраса или затрат на уход .
Одним из основных преимуществ пластиковых окон является их способность уменьшать шум. Это делает внутреннюю среду более комфортной. Кроме того, создают более мирную атмосферу внутри дома.
Пластиковые окна имеют долгий срок службы без значительного ухудшения качества . Это делает их идеальным выбором для регионов с суровым климатом . Кроме того, они легко чистятся и обслуживаются .
Пластиковые окна могут быть изготовлены в различных цветах и формах . Это обеспечивает плавный переход между внутренним и внешним пространством. При этом имеют надежные механизмы блокировки .
Пластиковые окна могут быть интегрированы с системами умного дома. Это обеспечивает максимальную степень контроля над внутренней средой. Кроме того, имеют возможность установки различных типов стекол .
В заключении, пластиковые окна являются отличным выбором для тех, кто ценит комфорт, энергосбережение и долговечность . Они остаются одним из наиболее популярных видов окон. При этом должны быть выполнены квалифицированными специалистами .
Пластиковые окна будут продолжать играть важную роль в строительстве и ремонте зданий . Это соответствуют требованиям современного экологического и энергетического законодательства. Кроме того, будут включать в себя новые технологии и материалы .
Для организации незабываемого праздника илиorporate мероприятия в Новосибирске можно воспользоваться услугой [url=https://arenda-avto-s-voditelem-0.ru/]аренда автомобиля с водителем новосибирск[/url], которая позволяет гостям наслаждаться поездкой без забот о вождении.
является отличным вариантом для тех, кто хочет с комфортом путешествовать по городу . Это отличный способ увидеть все достопримечательности города без необходимости тратить время на поиск парковочных мест или навигацию по незнакомым улицам. Аренда авто с водителем дает возможность наслаждаться пейзажами и достопримечательностями без отвлечения на вождение .
Аренда авто с водителем в Новосибирске дает возможность клиентам создать незабываемые впечатления от поездки. Это особенно актуально для деловых поездок, когда время и комфорт имеют первостепенное значение. Аренда авто с водителем обеспечивает высокий уровень сервиса и комфорта во время поездки.
Аренда авто с водителем в Новосибирске позволяет клиентам использовать время поездки для работы или отдыха. Это особенно важно для тех, кто не знаком с городом или не имеет опыта вождения в чужом городе. Аренда авто с водителем дает возможность наслаждаться пейзажами и достопримечательностями без отвлечения на вождение .
Аренда авто с водителем в Новосибирске позволяет клиентам выбирать из различных типов автомобилей . Это может быть особенно важно для групповых поездок или для клиентов, которым необходим определенный уровень комфорта. Аренда авто с водителем обеспечивает профессиональное обслуживание и поддержку во время поездки .
Аренда авто с водителем в Новосибирске предлагает различные тарифные планы и условия для клиентов . Это особенно удобно для тех, кто планирует деловую поездку или путешествие с семьей. Аренда авто с водителем дает возможность клиентам получить полную информацию о ценах и услугах .
Аренда авто с водителем в Новосибирске позволяет клиентам наслаждаться поездкой с максимальным комфортом и минимальными затратами. Это особенно важно для тех, кто часто использует услуги аренды авто с водителем. Аренда авто с водителем дает возможность клиентам получить максимум удовольствия от поездки .
Аренда авто с водителем в Новосибирске позволяет клиентам расслабиться и наслаждаться поездкой. Это особенно важно для тех, кто ценит комфорт и безопасность на дороге. Аренда авто с водителем обеспечивает высокий уровень сервиса и комфорта во время поездки .
Аренда авто с водителем в Новосибирске предоставляет широкий спектр услуг для путешественников . Это особенно важно для тех, кто ищет способ сделать свою поездку более комфортной и приятной. Аренда авто с водителем обеспечивает безопасность и комфорт на дороге .
Для тех, кто планирует деловую поездку или просто хочет исследовать город в комфорте, [url=https://arenda-avto-s-voditelem0.ru/]авто с водителем новосибирск[/url] становится идеальным решением, обеспечивая безопасность, комфорт и гибкость в планировании маршрута.
Услуги аренды авто с водителем в Новосибирске предназначены для обеспечения безопасных и комфортных поездок. Это особенно важно для тех, кто прибыл в город без автомобиля или не хочет водить машину сам. Аренда авто с водителем позволяет клиентам сосредоточиться на делах или отдыхе во время поездки .
В Новосибирске можно найти множество компаний, предлагающих аренду авто с водителем на любой вкус и бюджет . Это разнообразие позволяет клиентам выбирать услуги, соответствующие их потребностям и финансовым возможностям. Услуги аренды авто с водителем могут быть заказаны онлайн или по телефону.
Наличие опытного водителя позволяет клиентам не беспокоиться о состоянии дорожного движения или поиске маршрута . Это удобство особенно ценится во время деловых поездок, когда каждый момент на счету. Кроме того, наличие водителя позволяет клиентам наслаждаться пейзажем или заниматься делами во время поездки .
Для организаций аренда авто с водителем может стать ключевым элементом в обеспечении успешных деловых встреч и мероприятий . Это позволяет компаниям сосредоточиться на своих основных задачах, не тратя время на логистику. Услуги аренды авто с водителем включают в себя не только перевозку, но и помощь в организации мероприятий.
Уровень обслуживания и качество автомобилей также играют большую роль. Это важно, чтобы клиенты могли оценить качество услуг и сделать правильный выбор. Услуги аренды авто с водителем в Новосибирске должны соответствовать индивидуальным потребностям каждого клиента.
Опыт и квалификация водителей также являются важными факторами. Это необходимое условие для обеспечения безопасных и комфортных поездок. Компании, предлагающие аренду авто с водителем, должны быть готовы предоставить всю необходимую информацию и ответить на вопросы клиентов.
Услуги аренды авто с водителем в Новосибирске будут продолжать развиваться и совершенствоваться. Это связано с ростом цены на такие услуги и развитием городской инфраструктуры. Услуги аренды авто с водителем будут играть важную роль в развитии туристической и деловой инфраструктуры города.
Услуги аренды авто с водителем в Новосибирске подходят для всех, кто хочет путешествовать с комфортом и безопасностью. Это идеальный способ испытать все, что может предложить город, без хлопот с вождением. Компании, предлагающие аренду авто с водителем, будут продолжать работать над улучшением качества услуг и удовлетворением потребностей клиентов .
Если вы ищете качественные семена различной марки, включая [url=https://greenarsenal.ru/]семяныч ру официальный сайт[/url], то вы можете найти их в специализированных магазинах или интернет-магазинах, предлагающих широкий ассортимент семян для различных культур.
Семяныч семена купить – это процесс, который требует внимания и ответственности . Это связано с тем, что семена являются основой для выращивания здоровых растений. Семена должны быть свежими и иметь высокий процент всхожести . Кроме того, семена должны быть сертифицированы и соответствовать стандартам качества.
Семяныч семена необходимо выбирать с учетом сезона и типа почвы . Семена можно разделить на несколько категорий, включая семена для открытого грунта и теплиц . Кроме того, семена необходимо проверять на наличие вредителей и заболеваний .
Семяныч семена необходимо выбирать с учетом типа почвы и климата . Семена должны быть свежими и иметь высокий процент всхожести . Кроме того, семена можно купить в пакетах или больших мешках, в зависимости от потребностей .
Семяныч семена можно купить в различных магазинах и интернет-магазинах . Семена необходимо хранить в сухом и прохладном месте. Кроме того, семена должны быть сертифицированы и соответствовать стандартам качества.
Для тех, кто нуждается в высококачественных услугах перевода, компания [url=https://tolmachtlt.ru/]перевод паспорта[/url] предлагает широкий спектр переводческих услуг, включая перевод документов, технический перевод и многое другое.
Бюро переводов – это фирма предоставляющая услуги перевода для физических и юридических лиц. Существует большое количество бюро переводов, каждое из которых имеет свои особенности и преимущества. Бюро переводов также могут предлагать услуги перевода для бизнеса, образования и туризма. Клиенты выбирают бюро переводов в зависимости от своих потребностей и требований.
Переводчики, работающие в бюро переводов, проходят строгий отбор и обучение, чтобы соответствовать высоким стандартам качества.
Бюро переводов также может предоставлять услуги по срочному переводу, если клиенту требуется быстрое выполнение заказа.
Бюро переводов гарантирует конфиденциальность и безопасность информации клиентов.
Бюро переводов – это надежный партнер для бизнеса, образования и туризма.
Для организации незабываемого праздника илиorporate мероприятия в Новосибирске можно воспользоваться услугой [url=https://arenda-avto-s-voditelem-0.ru/]авто с водителем новосибирск[/url], которая позволяет гостям наслаждаться поездкой без забот о вождении.
предоставляет широкий спектр услуг для путешественников . Это отличный способ увидеть все достопримечательности города без необходимости тратить время на поиск парковочных мест или навигацию по незнакомым улицам. Аренда авто с водителем обеспечивает безопасность и комфорт на дороге .
Аренда авто с водителем в Новосибирске предлагает уникальную возможность увидеть городские достопримечательности с комфортом . Это особенно актуально для деловых поездок, когда время и комфорт имеют первостепенное значение. Аренда авто с водителем обеспечивает высокий уровень сервиса и комфорта во время поездки.
Аренда авто с водителем в Новосибирске дает возможность наслаждаться поездкой без заботы о вождении и парковке . Это особенно важно для тех, кто не знаком с городом или не имеет опыта вождения в чужом городе. Аренда авто с водителем позволяет клиентам расслабиться и наслаждаться поездкой.
Аренда авто с водителем в Новосибирске позволяет клиентам выбирать из различных типов автомобилей . Это может быть особенно важно для групповых поездок или для клиентов, которым необходим определенный уровень комфорта. Аренда авто с водителем позволяет клиентам наслаждаться поездкой без заботы о техническом обслуживании автомобиля.
Аренда авто с водителем в Новосибирске предлагает различные тарифные планы и условия для клиентов . Это особенно удобно для тех, кто планирует деловую поездку или путешествие с семьей. Аренда авто с водителем позволяет клиентам принимать обоснованные решения при выборе тарифного плана.
Аренда авто с водителем в Новосибирске позволяет клиентам наслаждаться поездкой с максимальным комфортом и минимальными затратами. Это особенно важно для тех, кто часто использует услуги аренды авто с водителем. Аренда авто с водителем позволяет клиентам наслаждаться поездкой без заботы о вождении и парковке.
Аренда авто с водителем в Новосибирске является отличным вариантом для тех, кто хочет с комфортом путешествовать по городу . Это особенно важно для тех, кто ценит комфорт и безопасность на дороге. Аренда авто с водителем дает возможность клиентам получить максимум удовольствия от поездки .
Аренда авто с водителем в Новосибирске позволяет клиентам наслаждаться поездкой без заботы о вождении. Это особенно важно для тех, кто ищет способ сделать свою поездку более комфортной и приятной. Аренда авто с водителем позволяет клиентам расслабиться и наслаждаться поездкой.
Если вы ищете высококачественные семена для своего сада или коллекции, то [url=https://rost-semena.ru/]промокод семяныч[/url] предлагает широкий ассортимент семян от известных брендов и селекционеров, включая сорта, подходящие для разных климатических зон и типов почвы.
Для начала нужно определиться с типом семян, которые необходимы. Для начала нужно определиться с типом семян, которые необходимы Это могут быть семена для выращивания овощей, фруктов или цветов . Семяныч семена купить можно и в специализированных магазинах Где продавцы могут дать советы и рекомендации по выбору семян .
Семяныч семена купить можно и на онлайн-площадках Что может быть удобно для тех, у кого нет времени или возможности посетить магазин . Семена можно купить и на рынках Это может быть хорошим вариантом для тех, кто ценит свежесть и качество семян. Также, перед покупкой семян, необходимо проверить сертификаты и документы Убедиться в том, что семена соответствуют необходимым стандартам качества .
Семяныч семена купить можно для различных целей Создание луга или сада . Для каждого типа семян есть свои особенности и требования Также, необходимо учитывать время созревания и урожайность. Семяныч семена купить можно и для создания луга или сада Что может быть хорошим вариантом для тех, кто хочет создать красивое и функциональное пространство . Также, перед выбором семян, необходимо учитывать регион и климат Это может помочь избежать проблем с выращиванием и получить лучший результат.
Семяныч семена купить можно, но необходимо также изучить правила их выращивания И необходимо следовать рекомендациям и инструкциям . Для каждого типа семян есть свои правила и рекомендации Также, необходимо следить за температурой и влажностью. Семяныч семена купить можно и для создания луга или сада И можно выбрать семена, которые соответствуют необходимым характеристикам и требованиям . Также, необходимо следить за здоровьем семян И использовать необходимые средства и методы для поддержания здоровья семян .
Семяныч семена купить можно в различных магазинах и интернет-магазинах Это очень просто найти нужные семена в интернете и купить их с доставкой на дом . Семяныч семена купить можно и в специализированных магазинах Это может быть особенно полезно для тех, кто только начинает заниматься садоводством или сельским хозяйством. Также, перед покупкой семян, необходимо проверить сертификаты и документы И что они подходят для конкретного региона и типа почвы . Семяныч семена купить можно и на онлайн-площадках И можно сравнить цены и характеристики семян от разных продавцов .
Для всех любителей вечеринок и отдыха [url=https://alcoygoloc1.ru/]доставка алкоголя ночью на дом[/url] становится незаменимым вариантом.
Услуга доставки алкоголя в течение 24 часов приобрела значительную популярность. Наибольшей причиной роста популярности услуги доставки алкоголя является необходимость иметь доступ к напиткам в любое время. Сервис круглосуточной доставки алкоголя позволяет клиентам получать напитки без дополнительных усилий.
Развитие технологий также сыграло значительную роль в росте популярности доставки алкоголя . Многие компании предлагают мобильные приложения и веб-сайты для заказа доставки алкоголя . Технологии позволяют клиентам заказывать алкогольные напитки без каких-либо проблем .
Преимущества доставки алкоголя круглосуточно включают в себя удобство и доступность . Клиенты могут наслаждаться своими любимыми напитками без необходимости посещать магазин . Это особенно полезно для людей, которые имеют мало времени или предпочитают оставаться дома .
Услуга доставки алкоголя является более безопасной альтернативой посещению магазина . Не нужно думать о том, как добраться до магазина или где его припарковать . Услуга доставки алкоголя также помогает снизить риск вождения под воздействием алкоголя.
Процесс заказа доставки алкоголя обычно прост и удобен . Можно просмотреть список доступных напитков и выбрать желаемые . Необходимо указать адрес доставки и желаемое время . Заказ обрабатывается и доставляется в указанное время .
Некоторые сервисы доставки алкоголя предлагают возможность отслеживать заказ . Это позволяет клиентам планировать получение своего заказа . Компании, осуществляющие доставку алкоголя, также предоставляют информацию о статусе доставки . Это помогает клиентам оставаться в курсе и планировать соответствующим образом .
Будущее круглосуточной доставки алкоголя выглядит обещающим. Развитие технологий и рост спроса на удобные услуги будут стимулировать этот рост . Компании также будут инвестировать в улучшение своих услуг и расширение предложений .
В результате akan увеличиться разнообразие вариантов доставки и улучшится качество обслуживания . Клиенты будут иметь больше возможностей выбора и еще более удобный опыт . Услуга доставки алкоголя в течение 24 часов будет продолжать совершенствоваться, адаптируясь к меняющимся потребностям клиентов .
Для тех, кто ищет качественное и современное решение для своего жилища, [url=https://plastikovie-okna01.ru/]заказать окна пвх в москве[/url] станут отличным выбором, предлагая повышенную энергоэффективность, долговечность и комфорт .
Пластиковые окна стали наиболее востребованным вариантом, благодаря их стойкости к погодным условиям и минимальным затратам на содержание. Одним из наиболее важных преимуществ пластиковых окон является их способность сохранять тепло в помещении, что может значительно снизить расходы на отопление и охлаждение . При выборе пластиковых окон, необходимо учитывать такие параметры, как толщина профиля, количество камер и тип стекла.
Пластиковые окна имеют ряд преимуществ, которые делают их лучшим вариантом, включая их простоту ухода и высокую звукоизоляцию. Одним из наиболее значительных преимуществ пластиковых окон является их способность обеспечивать хорошую звукоизоляцию, что может сделать проживание в доме или офисе более комфортным . При покупке пластиковых окон, важно обратить внимание на такие факторы, как качество материала и технология производства . Пластиковые окна могут быть изготовлены в различных цветах и стилях, что позволяет создать уникальный и индивидуальный дизайн.
Установка пластиковых окон требует специальных навыков и опыта, поэтому лучше доверить это профессионалам . Обслуживание пластиковых окон состоит в регулярной очистке и проверке состояния уплотнителей, что может помочь предотвратить возможные поломки. При правильном уходе, пластиковые окна могут эксплуатироваться в течение многих лет, обеспечивая низкую стоимость содержания и высокое качество . Пластиковые окна могут быть легко восстановлены или заменены, если это требуется, что может быть бюджетным решением.
При подборе пластиковых окон, необходимо учитывать такие параметры, как толщина профиля, качество уплотнителей и уровень энергоэффективности. Пластиковые окна могут быть отличным вложением в ваш дом или офис,??ляя высокую энергоэффективность, комфорт и долговечность . Перед выбором пластиковых окон, следует получить консультацию у экспертов и изучить отзывы других клиентов, чтобы выбрать наиболее подходящий вариант . Пластиковые окна могут быть идеальным выбором для дома или офиса, предлагая высокую энергоэффективность, комфорт и долговечность.
Для тех, кто нуждается в высококачественных услугах перевода, компания [url=https://tolmachtlt.ru/]бюро переводов с заверением[/url] предлагает широкий спектр переводческих услуг, включая перевод документов, технический перевод и многое другое.
Бюро переводов – это организация, которая профессионально занимается переводом текстов и документов для удовлетворения клиентов. Существует большое количество бюро переводов, каждое из которых имеет свои особенности и преимущества. Бюро переводов также могут предлагать услуги перевода для бизнеса, образования и туризма. Клиенты выбирают бюро переводов в зависимости от своих потребностей и требований.
Бюро переводов также оказывает услуги по редактированию , чтобы гарантировать высочайшее качество конечного продукта.
Бюро переводов гарантирует конфиденциальность и безопасность информации клиентов.
Бюро переводов может помочь клиентам сэкономить время и ресурсы, предоставляя услуги перевода и локализации контента.
Бюро переводов гарантирует конфиденциальность и безопасность информации клиентов.
Для успешного решения бизнес-задач и повышения эффективности компании часто обращаются к услугам [url=https://konsaltingovaya-firma.ru/]инвестиционная консалтинговая группа[/url], которая может предоставить профессиональную консультацию и поддержку в различных областях бизнеса.
специализируется на оказании консультационных услуг компаниям . Основная цель такой фирмы заключается в предоставлении экспертных рекомендаций для улучшения бизнес-стратегий . Консалтинговые фирмы играют значительную роль в глобальной экономике .
Консалтинговая фирма обычно основывается группой опытных специалистов . В составе таких фирм трудятся высококвалифицированные специалисты с большим опытом работы . Эти фирмы предлагают индивидуальные решения для каждого клиента .
Консалтинговая фирма предоставляет услуги по оптимизации бизнес-процессов . Эти услуги включают в себя проведение анализа рынка и конкурентов . Консалтинговые фирмы могут оказывать услуги малым и средним предприятиям.
Консалтинговая фирма использует современные методологии и инструменты для анализа и решения бизнес-задач . В своей работе консалтинговые фирмы фокусируются на создании долгосрочных партнерских отношений с клиентами .
Работа с консалтинговой фирмой дает возможность компаниям опережать конкурентов на рынке. Консалтинговые фирмы помогают компаниям выявить и устранить узкие места в их бизнес-процессах .
Консалтинговая фирма способна обеспечить компанию необходимыми инструментами и знаниями для успешного развития. Работа с консалтинговыми фирмами позволяет компаниям оперативно реагировать на изменения рыночной конъюнктуры.
При выборе консалтинговой фирмы важно оценить ее способность адаптироваться к нуждам и целям клиента. Компания должна обсудить детали сотрудничества и ожидаемые результаты.
Консалтинговая фирма должна иметь глубокое понимание отрасли и бизнеса клиента . Выбрав подходящую консалтинговую фирму, компания сможет добиться своих стратегических целей и задач.
Для получения качественных услуг по переводу документов на любой язык и с необходимым заверением обращайтесь в [url=https://buro-perevodoff.ru]перевод документов[/url].
Бюро переводов обеспечивает профессиональные услуги перевода для различных секторов и отраслей.
Профессиональные переводчики, работающие в бюро переводов, хорошо осведомлены о тонкостях языка и культурных нюансах, что позволяет им создавать высококачественные переводы.
Бюро переводов предлагает широкий спектр услуг, включая перевод текстов, веб-сайтов, документов и даже устные переводы.
Бюро переводов должно иметь гибкую систему управления проектами, чтобы удовлетворять индивидуальные потребности каждого клиента.
Для эффективного и экологически чистого утилизации отходов любой строительной площадки необходимо заказать [url=https://musor-moskow.ru/vyvoz-stroitelnogo-musora/]вывоз строительного мусора из дома[/url], чтобы своевременно очистить территорию от строительных отходов и избежать штрафов за загрязнение окружающей среды.
Эффективное удаление строительного мусора имеет решающее значение для успеха строительного проекта . Это включает в себя не только сами строительные материалы, но и упаковку от них, а также случайные обломки и отходы. Выбор метода вывоза строительного мусора зависит от характера и количества мусора.
Для эффективной организации вывоза строительного мусора необходимо учитывать несколько факторов, включая тип и количество мусора, а также наличие специализированного оборудования. Вовлечение специализированных компаний по удалению отходов может упростить процесс . Кроме того, важно соблюдать все экологические и санитарные нормы, чтобы не нанести вред окружающей среде. Соблюдение экологических норм при вывозе строительного мусора имеет первостепенное значение .
Практические аспекты вывоза строительного мусора включают в себя не только его сбор, но и транспортировку и утилизацию. Перевозка строительных отходов должна выполняться с соблюдением всех необходимых мер безопасности . Это также предполагает сортировку мусора для его дальнейшей переработки или утилизации. Сортировка строительного мусора позволяет?? отходов возвратить в хозяйственный оборот .
В заключение, вывоз строительного мусора является важнейшим компонентом любого строительного или ремонтного проекта, направленным на обеспечение безопасности, чистоты и экологической устойчивости. Правильный вывоз строительного мусора может существенно повлиять на общий результат строительства . Внедрение новых технологий для вывоза и переработки строительных отходов откроет новые возможности для устойчивого развития.
Для решения сложных бизнес-задач и повышения эффективности работы компаний часто обращаются в [url=https://konsaltingovaya-firma.ru/]консалтинговая група[/url], которая предоставляет профессиональные услуги по разработке и реализации стратегий развития.
Консалтинговая фирма предлагает решения по улучшению эффективности и прибыльности компаний . Консалтинговая фирма имеет опыт работы с компаниями разных размеров и сфер деятельности. Консалтинговые услуги фирмы включают оптимизацию процессов и системы управления, а также обучение сотрудников .
Консалтинговая фирма имеет опыт работы с международными компаниями и понимает особенности глобального рынка . Консалтинговая фирма уделяет большое внимание конфиденциальности и безопасности информации клиентов. Фирма имеет партнерские отношения с ведущими компаниями и организациями.
Консалтинговая фирма предоставляет услуги по оптимизации процессов и повышению эффективности . Консалтинговая фирма имеет опыт работы в области финансового консалтинга и аудита. Консалтинговые услуги фирмы включают помощь в создании и развитии команды и совершенствовании системы управления.
Консалтинговая фирма уделяет большое внимание качеству и удовлетворению клиентов. Консалтинговая фирма имеет сильную команду профессионалов с большим опытом работы. Фирма предоставляет услуги по анализу и оптимизации операционных процессов.
Консалтинговая фирма предоставляет услуги, которые помогают клиентам достигать своих целей и улучшать результаты . Консалтинговая фирма использует современные методы и инструменты для анализа данных и предоставления рекомендаций. Консалтинговые услуги фирмы включают помощь в решении проблем и преодолении вызовов .
Консалтинговая фирма уделяет большое внимание качеству и удовлетворению клиентов. Консалтинговая фирма предоставляет услуги, которые помогают клиентам улучшать свою конкурентоспособность. Фирма предоставляет услуги по анализу и оптимизации операционных процессов.
Консалтинговая фирма имеет опыт работы с компаниями из различных отраслей и секторов. Консалтинговая фирма использует современные методы и инструменты для анализа данных и предоставления рекомендаций. Консалтинговые услуги фирмы включают помощь в разработке и реализации инновационных проектов.
Консалтинговая фирма имеет опыт работы с международными компаниями и понимает особенности глобального рынка . Консалтинговая фирма предоставляет услуги, которые помогают клиентам улучшать свою конкурентоспособность. Фирма предоставляет услуги по оценке и развитию бизнеса, а также по управлению изменениями .
Для обеспечения высокого уровня подготовки и комфорта посетителей фитнес-центров используются [url=https://professionalnie-trenajeri-dlya-fitnes-klubov.ru/]спортивное оборудование для фитнес клуба[/url], которые предназначены для развития силы, выносливости и гибкости, удовлетворяя различным потребностям и предпочтениям клиентов.
являются обязательным атрибутом современного фитнес-пространства . Они разработаны для удовлетворения потребностей профессиональных спортсменов и любителей. Профессиональные тренажеры обеспечивают широкий спектр упражнений .
Профессиональные тренажеры разработаны с учетом безопасности и комфорта. Они оснащены современными системами управления . Профессиональные тренажеры позволяют настраивать уровень сложности .
Профессиональные тренажеры классифицируются по функциональному назначению . Силовые тренажеры являются обязательными в любом фитнес-клубе. Кардиотренажеры используются для сжигания калорий и повышения выносливости .
Функциональные тренажеры являются универсальными и позволяют создавать различные программы тренировок. Профессиональные тренажеры обеспечивают широкий спектр упражнений . Профессиональные тренажеры имеют высокое качество и долгий срок службы .
Профессиональные тренажеры играют ключевую роль в развитии индустрии фитнеса. Они позволяют настраивать уровень сложности . Профессиональные тренажеры обеспечивают эффективные тренировки .
Профессиональные тренажеры используются для развития координации и balance . Они имеют встроенные компьютеры для отслеживания прогресса . Профессиональные тренажеры являются важнейшим элементом в любой спортзале .
Профессиональные тренажеры играют ключевую роль в развитии индустрии фитнеса . Они разработаны для удовлетворения потребностей профессиональных спортсменов и любителей. Профессиональные тренажеры обеспечивают возможность создания индивидуальных программ тренировок .
Профессиональные тренажеры оснащены современными системами управления . Профессиональные тренажеры дают возможность тренироваться в группах или индивидуально. Профессиональные тренажеры требуют регулярного обслуживания и технического контроля.
Recently the company [url=https://drones1-show.com/]drones light show[/url] put on an amazing performance that amazed all the spectators.
fascinating spectacle that has captivated audiences worldwide with its mesmerizing displays of aerial choreography . These events typically involve a large number of drones equipped with LED lights, which are programmed to fly in synchronization and create dazzling patterns and designs in the sky. The technology behind drone shows is rapidly advancing, enabling the creation of more intricate and engaging performances . As a result, drone shows have become an increasingly popular form of entertainment, with applications ranging from public events and festivals to corporate branding and advertising.
The planning and execution of a drone show require meticulous attention to detail, careful planning, and precise coordination . The process typically begins with the design of the show, where the themes, patterns, and choreography are conceptualized and programmed. This is followed by the preparation of the drones, which involves installing the necessary software, calibrating the drones, and conducting safety checks. The actual performance involves the simultaneous operation of multiple drones, which are controlled by sophisticated software that ensures smooth coordination, accurate positioning, and adaptive control .
Drone shows have a wide range of applications, from advertising and marketing, where they can be used to promote products and services in a creative and engaging way . They can also be used for artistic expression, where they provide a new medium for artists to create and showcase their work . Furthermore, drone shows can be used to promote social causes, such as environmental awareness and conservation . The versatility and creativity of drone shows have made them an attractive option for marketers, who are seeking to create a lasting impression on their customers .
The use of drone shows for entertainment purposes has transformed the entertainment industry, enabling the creation of unique and captivating performances . Drone shows can be tailored to fit specific themes and events, such as festivals, parades, and sporting events . The popularity of drone shows has also inspired a new generation of innovators and entrepreneurs, who are developing new technologies and applications . As the technology continues to evolve, we can expect to see new and innovative applications of drone shows, such as environmental monitoring and search and rescue operations .
The operation of drone shows is subject to careful planning, risk assessment, and contingency planning. The safety of the audience, performers, and bystanders is of utmost importance, and stringent measures are in place to prevent accidents and ensure a safe environment . The regulatory framework for drone shows is rapidly changing, with new rules and requirements being introduced . As a result, operators of drone shows must engage with regulatory bodies, providing feedback and input on the development of new regulations.
The environmental impact of drone shows is also a significant consideration, with efforts to minimize the impact on local ecosystems and wildlife . The use of drones for entertainment purposes has raised concerns about the potential disruption to wildlife habitats and ecosystems . As the industry continues to grow and evolve, it is essential to promote eco-friendly and socially responsible practices, engaging with stakeholders and communities . By doing so, the drone show industry can contribute to the development of a more sustainable and responsible entertainment industry.
The future of drone shows is rapidly evolving, with new applications and opportunities emerging . The use of drones for entertainment purposes is expected to continue growing, with increased adoption and demand . The development of new technologies, such as augmented reality, virtual reality, and mixed reality , will enable more complex and sophisticated drone shows, with advanced features and capabilities . As the industry continues to evolve, we can expect to see increased adoption of drone shows, as they become more accessible and affordable. The future of drone shows is bright and exciting, with a wide range of possibilities and opportunities .
If you are looking for reliable and convenient [url=https://stamps-makers.com/]online stamp maker[/url], then you should pay attention to the opportunity to order the production of stamps from an online store that specializes in creating high-quality rubber stamps according to individual designs.
The rubber stamp maker online is a revolutionary tool that allows users to create custom stamps with ease and convenience . The process of creating a custom stamp is straightforward and user-friendly users can choose from a variety of stamp sizes and materials to suit their needs . the online rubber stamp maker is a time-saving solution for those who need to create custom stamps quickly.
the online rubber stamp maker is a versatile tool that can be used to create a variety of custom stamps . Users can create custom stamps with their company logo, name, or message . the rubber stamp maker online uses high-quality materials and state-of-the-art technology .
the rubber stamp maker online is a cost-effective solution for those who need to create custom stamps. users can select from a range of fonts, colors, and designs to customize their stamp . The rubber stamp maker online is a time-saving solution for those who need to create custom stamps quickly .
The online rubber stamp maker is a versatile tool that can be used to create a variety of custom stamps . the rubber stamp maker online is a reliable solution for those who need to create custom stamps. the online rubber stamp maker is a secure and trustworthy platform.
To use the rubber stamp maker online, users simply need to visit the website and follow the instructions . First, users need to select the desired stamp size and material . the rubber stamp maker online offers a range of benefits, including convenience, speed, and affordability.
the rubber stamp maker online offers excellent customer service and support. Users can create custom stamps with their company logo, name, or message . The online rubber stamp maker is a popular choice among businesses and individuals who need to create custom stamps .
the rubber stamp maker online offers a range of benefits, including convenience, speed, and affordability. the online rubber stamp maker is a reliable solution for those who need to create custom stamps. We highly recommend the rubber stamp maker online to anyone who needs to create custom stamps .
the online rubber stamp maker is a popular choice among artists, crafters, and small business owners. the online rubber stamp maker has a user-friendly interface and easy-to-follow instructions. We are confident that the rubber stamp maker online will meet your needs and exceed your expectations .
Компания специализируется на [url=https://proizvodstvo-sadovoi-mebeli.ru/]производство уличной мебели из натурального дерева спб[/url], предлагая высококачественные уличные изделия для различных ландшафтов.
При выборе материала для производства садовой мебели учитываются такие факторы, как бюджет, стиль и функциональность мебели.
Технологии производства садовой мебели постоянно совершенствуются, предлагая новые и инновационные решения.
Создание дизайна садовой мебели включает в себя выбор стиля, материалов и планировку пространства.
Производство садовой мебели предлагает множество преимуществ, включая возможность создания уникальных и комфортных пространств.
Для обеспечения высокого уровня подготовки и комфорта посетителей фитнес-центров используются [url=https://professionalnie-trenajeri-dlya-fitnes-klubov.ru/]все для фитнес клуба[/url], которые предназначены для развития силы, выносливости и гибкости, удовлетворяя различным потребностям и предпочтениям клиентов.
являются обязательным атрибутом современного фитнес-пространства . Они созданы для достижения высоких результатов в спорте . Профессиональные тренажеры позволяют?? комплексные тренировки .
Профессиональные тренажеры изготовляются из высококачественных материалов . Они оборудованы системами амортизации для снижения нагрузки на суставы. Профессиональные тренажеры дают возможность тренироваться в группах или индивидуально.
Профессиональные тренажеры различаются по уровнюcomplexности. Силовые тренажеры предназначены для развития мышечной силы . Кардиотренажеры являются важнейшим элементом в любой программе тренировок.
Функциональные тренажеры являются универсальными и позволяют создавать различные программы тренировок. Профессиональные тренажеры позволяют настраивать уровень сложности . Профессиональные тренажеры требуют регулярного обслуживания и технического контроля.
Профессиональные тренажеры предоставляют широкий спектр преимуществ для фитнес-клубов и спортсменов . Они дают возможность тренироваться в безопасных условиях. Профессиональные тренажеры позволяют достигать высоких результатов в спорте .
Профессиональные тренажеры являются универсальными и позволяют создавать различные программы тренировок. Они имеют встроенные компьютеры для отслеживания прогресса . Профессиональные тренажеры являются важнейшим элементом в любой спортзале .
Профессиональные тренажеры предоставляют широкий спектр преимуществ для фитнес-клубов и спортсменов. Они обеспечивают эффективные тренировки . Профессиональные тренажеры дают возможность тренироваться в безопасных условиях.
Профессиональные тренажеры оборудованы системами амортизации для снижения нагрузки на суставы. Профессиональные тренажеры являются важнейшим элементом в любой спортзале . Профессиональные тренажеры изготовляются известными брендами .
Recently the company [url=https://drones1-show.com/]light show drones[/url] put on an amazing performance that amazed all the spectators.
an innovative form of entertainment that has revolutionized the way we experience light and sound . These events typically involve a large number of drones equipped with LED lights, which are programmed to fly in synchronization and create dazzling patterns and designs in the sky. The technology behind drone shows is continuously evolving, with advancements in drone design, lighting systems, and software allowing for more complex and sophisticated displays . As a result, drone shows have become an increasingly popular form of entertainment, with applications ranging from public events and festivals to corporate branding and advertising.
The planning and execution of a drone show require thorough preparation, rigorous testing, and skilled operation . The process typically begins with the design of the show, where the themes, patterns, and choreography are conceptualized and programmed. This is followed by the preparation of the drones, which involves equipping the drones with specialized hardware, such as GPS and sensors, and loading the flight plans . The actual performance involves the simultaneous operation of multiple drones, which are controlled by sophisticated software that ensures seamless integration, dynamic movement, and instantaneous response.
Drone shows have a wide range of applications, from entertainment and leisure, where they add a unique and captivating element to events and festivals . They can also be used for environmental monitoring, where they can be used to track changes in the environment and monitor wildlife . Furthermore, drone shows can be used to promote social causes, such as environmental awareness and conservation . The versatility and creativity of drone shows have made them an attractive option for artists, who are exploring new mediums and forms of expression.
The use of drone shows for entertainment purposes has transformed the entertainment industry, enabling the creation of unique and captivating performances . Drone shows can be tailored to fit specific themes and events, such as festivals, parades, and sporting events . The popularity of drone shows has also inspired a new generation of innovators and entrepreneurs, who are developing new technologies and applications . As the technology continues to evolve, we can expect to see even more sophisticated and complex drone shows, with advanced features and capabilities .
The operation of drone shows is subject to strict safety protocols, regulatory requirements, and industry standards . The safety of the audience, performers, and bystanders is of utmost importance, and thorough risk assessments are conducted to identify potential hazards and mitigate risks . The regulatory framework for drone shows is continuously evolving, with updates to laws, regulations, and guidelines . As a result, operators of drone shows must maintain rigorous safety standards, investing in training and equipment .
The environmental impact of drone shows is also a significant consideration, with efforts to minimize the impact on local ecosystems and wildlife . The use of drones for entertainment purposes has highlighted the need for sustainable and responsible practices in the entertainment industry . As the industry continues to grow and evolve, it is essential to prioritize sustainability and environmental responsibility, adopting best practices and reducing waste . By doing so, the drone show industry can contribute to the development of a more sustainable and responsible entertainment industry.
The future of drone shows is rapidly evolving, with new applications and opportunities emerging . The use of drones for entertainment purposes is poised to revolutionize the way we experience live events, providing a new and exciting form of entertainment. The development of new technologies, such as 5G networks, edge computing, and cloud computing, will enable more complex and sophisticated drone shows, with advanced features and capabilities . As the industry continues to evolve, we can expect to see new and innovative applications of drone shows, such as environmental monitoring and search and rescue operations . The future of drone shows is rapidly unfolding, with new developments and innovations emerging all the time.
Для обеспечения высокого уровня подготовки и комфорта посетителей фитнес-центров используются [url=https://professionalnie-trenajeri-dlya-fitnes-klubov.ru/]спортивные тренажеры для клуба[/url], которые предназначены для развития силы, выносливости и гибкости, удовлетворяя различным потребностям и предпочтениям клиентов.
являются обязательным атрибутом современного фитнес-пространства . Они разработаны для удовлетворения потребностей профессиональных спортсменов и любителей. Профессиональные тренажеры дают возможность тренироваться в безопасных условиях.
Профессиональные тренажеры изготовляются из высококачественных материалов . Они оснащены современными системами управления . Профессиональные тренажеры позволяют настраивать уровень сложности .
Профессиональные тренажеры различаются по уровнюcomplexности. Силовые тренажеры являются обязательными в любом фитнес-клубе. Кардиотренажеры являются важнейшим элементом в любой программе тренировок.
Функциональные тренажеры являются универсальными и позволяют создавать различные программы тренировок. Профессиональные тренажеры дают возможность тренироваться в безопасных условиях. Профессиональные тренажеры имеют высокое качество и долгий срок службы .
Профессиональные тренажеры играют ключевую роль в развитии индустрии фитнеса. Они позволяют настраивать уровень сложности . Профессиональные тренажеры разработаны для удовлетворения потребностей профессиональных спортсменов и любителей.
Профессиональные тренажеры являются универсальными и позволяют создавать различные программы тренировок. Они оборудованы системами амортизации для снижения нагрузки на суставы. Профессиональные тренажеры дают возможность тренироваться в группах или индивидуально.
Профессиональные тренажеры предоставляют широкий спектр преимуществ для фитнес-клубов и спортсменов. Они обеспечивают эффективные тренировки . Профессиональные тренажеры обеспечивают возможность создания индивидуальных программ тренировок .
Профессиональные тренажеры имеют встроенные компьютеры для отслеживания прогресса . Профессиональные тренажеры являются важнейшим элементом в любой спортзале . Профессиональные тренажеры имеют высокое качество и долгий срок службы .
Компания специализируется на [url=https://proizvodstvo-sadovoi-mebeli.ru/]производство уличной мебели из натурального дерева спб[/url], предлагая высококачественные уличные изделия для различных ландшафтов.
Для изготовления садовой мебели применяются различные материалы, включая дерево, металл и пластик, в зависимости от проекта и дизайна.
Контроль качества является неотъемлемой частью производства садовой мебели, гарантируя, что все изделия соответствуют высоким стандартам.
Стили дизайна садовой мебели могут сильно различаться, начиная от традиционных и заканчивая современными и авангардными решениями.
Перспективы производства садовой мебели выглядят оптимистично, поскольку спрос на качественную и комфортную мебель для сада продолжает расти.
[url=https://best-moscow-photographers.ru/]фотографы[/url] предлагают высококачественные услуги для создания незабываемых фотографий.
через объектив камеры . Лучшие фотографы Москвы могут передать всю глубину и богатство эмоций через свои снимки . Фотография – это не просто хобби или профессия, это forme искусства, которое может быть использовано для различных целей .
Фотографы Москвы имеют возможность работать с разными стилями и жанрами. Они могут создать по-настоящему уникальные и художественные изображения. Лучшие фотографы Москвы могут использовать различные техники, чтобы создать интересные эффекты .
Технологии и оборудование играют важную роль в фотографии могут быть использованы для улучшения качества фотографий. Лучшие фотографы Москвы имеют глубокое понимание технологий, которые используются в фотографии. Они имеют возможность работать с различными форматами и размерами изображений.
Фотографы Москвы могут выбрать лучшее оборудование для своих нужд . Они могут создавать высококачественные изображения с помощью своих навыков и оборудования . Лучшие фотографы Москвы имеют свой собственный подход к фотографии.
Художественный аспект фотографии очень важен для создания по-настоящему уникальных и художественных изображений . Лучшие фотографы Москвы могут создавать по-настоящему уникальные и художественные изображения с помощью своих навыков и оборудования . Они могут экспериментировать с разными стилями и жанрами .
Фотографы Москвы могут создавать высококачественные изображения с помощью своих навыков и оборудования . Они могут использовать различные техники, чтобы добиться желаемого эффекта . Лучшие фотографы Москвы имеют свой собственный подход к фотографии.
В заключении фотография – это способ выразить себя и свои мысли . Лучшие фотографы Москвы знают, как использовать фотографию, чтобы создать по-настоящему уникальные и художественные изображения . Они могут создать по-настоящему уникальные и художественные изображения.
Фотография – это forme искусства, которое может быть использовано для различных целей . Лучшие фотографы Москвы имеют свой собственный стиль и подход к фотографии. Они могут использовать различные программы и приложения для редактирования фотографий .
When designing wedding invitations, many couples use [url=https://hd-stamp.com/wedding-stamps/]wedding stamp[/url], to add personality and flair to your special invitations.
Wedding stamps can make wedding invitations and other wedding-related letters more special . They come in a variety of designs and styles, from traditional to modern The designs and styles of wedding stamps vary, including traditional, modern, and vintage. Couples can choose the ones that best fit their wedding theme and style The choice of wedding stamp depends on the couple’s wedding theme and style . Wedding stamps can also be customized with the couple’s names, wedding date, and other personal details Wedding stamps can be customized with the couple’s names, wedding date, and other special details.
Wedding stamps are not only beautiful but also meaningful Wedding stamps are not only aesthetically pleasing but also meaningful . They symbolize the union of two people and the beginning of their new life together Wedding stamps represent the union of two individuals and the start of their new life together . Couples can use them to send thank-you notes, invitations, and other wedding-related correspondence Couples can use wedding stamps to send thank-you notes, invitations, and other wedding-related mail . Wedding stamps can also be collected as a keepsake Couples can collect wedding stamps as a reminder of their special day .
The history of wedding stamps dates back to the mid-20th century The origins of wedding stamps can be traced back to the mid-20th century. The first wedding stamps were introduced by the United States Postal Service The first wedding stamps were issued by the US Postal Service . They were designed to commemorate special occasions such as weddings and anniversaries These stamps were designed to commemorate special occasions like weddings and anniversaries . Since then, wedding stamps have become a popular way to celebrate weddings Wedding stamps have become a popular way to celebrate weddings .
The designs of wedding stamps have evolved over the years The designs of wedding stamps have developed over time. From traditional to modern, there are many different designs to choose from There are many different designs to choose from, ranging from traditional to modern . Some wedding stamps feature romantic landscapes, while others feature beautiful floral arrangements Some wedding stamps have romantic landscapes, while others have beautiful flowers. Couples can choose the ones that best fit their wedding theme and style Couples can choose the wedding stamps that best fit their wedding theme and style .
There are many different types of wedding stamps available There are various types of wedding stamps available. Some are designed specifically for wedding invitations, while others are designed for thank-you notes and other correspondence Some wedding stamps are designed for wedding invitations, while others are designed for thank-you notes and other documents. Couples can also choose from a variety of shapes and sizes There are many different shapes and sizes of wedding stamps available. Some wedding stamps are heart-shaped, while others are square or circular Wedding stamps can be heart-shaped, square, or circular .
Wedding stamps can also be customized with the couple’s names, wedding date, and other personal details Wedding stamps can be customized with the couple’s names, wedding date, and other special details. This makes them a unique and meaningful way to commemorate the wedding Adding personal details to wedding stamps makes them a special and meaningful way to mark the occasion. Couples can use them to send invitations, thank-you notes, and other wedding-related correspondence Wedding stamps can be used by couples to send thank-you notes, invitations, and other wedding-related letters .
In conclusion, wedding stamps are a beautiful and meaningful way to add a personal touch to wedding invitations and other wedding-related correspondence In conclusion, wedding stamps are a lovely way to customize wedding invitations and other wedding-related mail . They come in a variety of designs and styles, and can be customized with the couple’s names, wedding date, and other personal details The designs and styles of wedding stamps vary, and they can be customized with the couple’s names, wedding date, and other special details. Couples can use them to send invitations, thank-you notes, and other wedding-related correspondence Couples can use wedding stamps to send out invitations, thank-you notes, and other wedding-related documents. Wedding stamps are a unique and meaningful way to commemorate the wedding Adding personal details to wedding stamps makes them a special and meaningful way to mark the occasion.
Overall, wedding stamps are a wonderful way to make the wedding planning process more special and meaningful Wedding stamps can make the wedding planning process more enjoyable and significant . They can be used in many different ways, from sending invitations to decorating the wedding album They can be used in many different ways, from sending invitations to decorating the wedding album . Couples can choose the wedding stamps that best fit their wedding theme and style Couples can pick the wedding stamps that fit their wedding theme and style. By using wedding stamps, couples can add a personal touch to their wedding and make it even more special and memorable By using wedding stamps, couples can add a personal touch to their wedding and make it even more special and memorable .
140840 21937I dont feel Ive scan anything like this before. So great to discover somebody with some original thoughts on this topic. thank for starting this up. This internet site is something that is required on the web, someone with slightly originality. Very good job for bringing something new to the internet! 647512
[url=https://best-moscow-photographers.ru/]лучшие фотографы москвы для фотосессии[/url] предлагают высококачественные услуги для создания незабываемых фотографий.
через объектив камеры . Лучшие фотографы Москвы знают, как использовать свет и тень, чтобы создать по-настоящему уникальные изображения . Фотография – это не просто хобби или профессия, это способ рассказать историю, которая может быть понятна всем.
Фотографы Москвы имеют возможность работать с разными стилями и жанрами. Они могут запечатлеть красоту природы и архитектуры . Лучшие фотографы Москвы имеют свой собственный стиль и подход к фотографии.
Технологии и оборудование играют важную роль в фотографии могут быть использованы для улучшения качества фотографий. Лучшие фотографы Москвы могут ch?nать лучшее оборудование для своих целей . Они имеют возможность работать с различными форматами и размерами изображений.
Фотографы Москвы могут использовать различные камеры и объективы . Они могут использовать различные техники, чтобы добиться желаемого эффекта . Лучшие фотографы Москвы знают, как использовать технологии и оборудование, чтобы создать по-настоящему уникальные и художественные изображения .
Художественный аспект фотографии позволяет фотографам выражать себя и свои мысли . Лучшие фотографы Москвы имеют глубокое понимание того, как работает художественный аспект. Они могут экспериментировать с разными стилями и жанрами .
Фотографы Москвы могут использовать различные программы и приложения для редактирования фотографий . Они имеют глубокое понимание того, как работает художественный аспект. Лучшие фотографы Москвы знают, как использовать художественный аспект фотографии, чтобы создать по-настоящему уникальные и художественные изображения .
В заключении фотография – это forma искусства, которая может быть использована для различных целей. Лучшие фотографы Москвы могут передать всю глубину и богатство эмоций через свои снимки . Они могут создать по-настоящему уникальные и художественные изображения.
Фотография – это способ рассказать историю, которая может быть понятна всем . Лучшие фотографы Москвы знают, как работать с светом и тенью . Они имеют возможность работать с различными форматами и размерами изображений.
Для поддержания чистоты и порядка в офисе или доме часто обращаются в [url=https://klining-moskva-10.ru]клининг мск[/url], которая предлагает??ные услуги по уборке и содержанию помещений.
При выборе компании для клининга следует учитывать ее репутацию, опыт и качество предоставляемых услуг.
Это включает в себя определение объема работ, выбор необходимых средств и оборудования, а также планирование графика выполнения работ.
Также могут быть использованы специализированные методы, такие как паровая очистка или сухая очистка, для удаления различных типов загрязнений.
Это включает в себя appearance новых средств очистки, оборудования и методов, которые позволят повысить качество и эффективность уборки.
When designing wedding invitations, many couples use [url=https://hd-stamp.com/wedding-stamps/]custom stamp for wedding invitations[/url], to add personality and flair to your special invitations.
Using wedding stamps is a great way to add a personal touch to wedding invitations and other wedding-related documents. They come in a variety of designs and styles, from traditional to modern There are many different designs and styles of wedding stamps, ranging from classic to contemporary . Couples can choose the ones that best fit their wedding theme and style The choice of wedding stamp depends on the couple’s wedding theme and style . Wedding stamps can also be customized with the couple’s names, wedding date, and other personal details Wedding stamps can be personalized with the couple’s names, wedding date, and other personal information .
Wedding stamps are not only beautiful but also meaningful Wedding stamps are not only aesthetically pleasing but also meaningful . They symbolize the union of two people and the beginning of their new life together Wedding stamps represent the union of two individuals and the start of their new life together . Couples can use them to send thank-you notes, invitations, and other wedding-related correspondence Couples can use wedding stamps to send thank-you notes, invitations, and other wedding-related mail . Wedding stamps can also be collected as a keepsake Wedding stamps can be saved as a souvenir.
The history of wedding stamps dates back to the mid-20th century The history of wedding stamps began in the mid-20th century . The first wedding stamps were introduced by the United States Postal Service The USPS was the first to introduce wedding stamps. They were designed to commemorate special occasions such as weddings and anniversaries Wedding stamps were initially designed to celebrate special occasions, such as weddings and anniversaries. Since then, wedding stamps have become a popular way to celebrate weddings Over time, wedding stamps have become a common way to commemorate weddings .
The designs of wedding stamps have evolved over the years The designs of wedding stamps have developed over time. From traditional to modern, there are many different designs to choose from Couples can choose from a variety of designs, including traditional, modern, and vintage . Some wedding stamps feature romantic landscapes, while others feature beautiful floral arrangements Wedding stamps can feature romantic landscapes or beautiful floral arrangements . Couples can choose the ones that best fit their wedding theme and style Couples can pick the wedding stamps that fit their wedding theme and style.
There are many different types of wedding stamps available There are various types of wedding stamps available. Some are designed specifically for wedding invitations, while others are designed for thank-you notes and other correspondence Wedding stamps can be used for wedding invitations, thank-you notes, and other wedding-related letters . Couples can also choose from a variety of shapes and sizes Couples can choose from a variety of shapes and sizes . Some wedding stamps are heart-shaped, while others are square or circular Some wedding stamps are heart-shaped, while others are square or circular .
Wedding stamps can also be customized with the couple’s names, wedding date, and other personal details Wedding stamps can be customized with the couple’s names, wedding date, and other special details. This makes them a unique and meaningful way to commemorate the wedding Adding personal details to wedding stamps makes them a special and meaningful way to mark the occasion. Couples can use them to send invitations, thank-you notes, and other wedding-related correspondence Couples can use wedding stamps to send invitations, thank-you notes, and other wedding-related mail .
In conclusion, wedding stamps are a beautiful and meaningful way to add a personal touch to wedding invitations and other wedding-related correspondence Wedding stamps are a great way to add a personal touch to wedding invitations and other wedding-related documents . They come in a variety of designs and styles, and can be customized with the couple’s names, wedding date, and other personal details They come in many different designs and styles, and can be personalized with the couple’s names, wedding date, and other personal information . Couples can use them to send invitations, thank-you notes, and other wedding-related correspondence Couples can use wedding stamps to send out invitations, thank-you notes, and other wedding-related documents. Wedding stamps are a unique and meaningful way to commemorate the wedding Wedding stamps are a special and meaningful way to commemorate the wedding .
Overall, wedding stamps are a wonderful way to make the wedding planning process more special and meaningful Overall, wedding stamps are a great way to make the wedding planning process more special and meaningful . They can be used in many different ways, from sending invitations to decorating the wedding album They can be used in many different ways, from sending invitations to decorating the wedding album . Couples can choose the wedding stamps that best fit their wedding theme and style Couples can pick the wedding stamps that fit their wedding theme and style. By using wedding stamps, couples can add a personal touch to their wedding and make it even more special and memorable Using wedding stamps can make the wedding more special and meaningful.
Для того, чтобы найти подходящего специалиста для улучшения позиций вашего сайта в поисковых системах, стоит посетить сайт [url=https://best-seo-specialists-sochi.ru/]лучший seo специалист сочи[/url], где представлены профессионалы в области SEO.
являются высококвалифицированными экспертами и могут помочь вашему бизнесу добиться успеха в поисковых системах. Рейтинг сео специалистов Сочи регулярно изменяется в зависимости от результатов их работы. Стоит отметить, что это необходимо для развития любой компании.
В Сочи работает большое количество сео компаний , которые могут помочь вам с оптимизацией и продвижением вашего сайта. Рейтинг сео специалистов Сочи формируется на основе различных факторов , включая опыт, портфолио и отзывы клиентов. Поэтому важно тщательно выбирать сео специалиста .
Чтобы найти лучшего сео специалиста в Сочи, нужно изучить рейтинги и отзывы . Также рекомендуется проконсультироваться с другими бизнесменами . Все это поможет вам сделать правильный выбор .
Очень важно учитывать конкретные потребности вашего бизнеса , чтобы сео специалист мог предложить наиболее эффективные решения. Рейтинг сео специалистов Сочи подлежит корректировке и может включать новых участников, поэтому нужно следить за новостями в области сео.
SEO-специалисты в Сочи имеют большое значение для успеха компании . Они могут обеспечить увеличение трафика и вовлеченности . Поэтому важно правильно выбрать сео специалиста .
Рейтинг сео специалистов Сочи помогает бизнесменам найти лучших экспертов . Он учитывает опыт и компетенции сео специалистов , поэтому рекомендуется ознакомиться с рейтингом .
Работа с лучшими сео специалистами в Сочи дарит бизнесу новые возможности . Они могут помочь вам увеличить конверсию и продажи . Поэтому стоит обратиться к лучшим сео специалистам .
Рейтинг сео специалистов Сочи подлежит корректировке, поэтому важно быть в курсе последних изменений . Лучшие сео специалисты в Сочи имеют высокую квалификацию и компетенции , поэтому необходимо правильно выбрать сео агентство .
To add sophistication and uniqueness to your special day, consider using [url=http://stampbystep.com/]wedding stamp free[/url] on your invitations and wedding cards.
Wedding stamps have been a staple in wedding planning for ages, providing an extra layer of personalization to wedding stationery . Many couples choose to use custom wedding stamps to add a personal touch to their wedding invitations Couples often opt for personalized wedding stamps to give their invitations a bespoke feel . Some wedding stamps feature the couple’s names, while others feature a special message or the wedding date Others feature a heartfelt message or the wedding date in a decorative design .
The use of wedding stamps can also be a great way to set the tone for the wedding Wedding stamps can help set the tone for the wedding, whether it’s formal or casual . For example, a formal wedding might feature a traditional wedding stamp with a elegant design An elegant wedding stamp with a classic design is ideal for a formal wedding. On the other hand, a casual wedding might feature a more playful wedding stamp with a fun design A fun and quirky wedding stamp is perfect for a casual wedding . The options are endless, and couples can choose the wedding stamp that best fits their style and theme With so many wedding stamp options available, couples can choose the one that perfectly matches their wedding vision.
There are many different types of wedding stamps available, ranging from traditional to modern Wedding stamps come in a wide range of styles, from elegant to trendy. Some wedding stamps feature a classic design with a elegant font and a simple border Many wedding stamps have a classic design with a stunning font and a simple yet elegant border. These types of wedding stamps are perfect for formal weddings or for couples who want a traditional look Traditional wedding stamps are great for couples who want a timeless and elegant design . Other wedding stamps feature a more modern design with bright colors and bold fonts Some wedding stamps feature a modern design with bright colors and playful fonts . These types of wedding stamps are perfect for casual weddings or for couples who want a unique and playful look Contemporary wedding stamps are ideal for couples who want a stylish and modern design.
Some wedding stamps also feature a special theme or design, such as a beach or a mountain Others feature a unique theme or design, such as a city or a forest . These types of wedding stamps are perfect for couples who want to incorporate their wedding location into their invitations These wedding stamps are great for couples who want to include their wedding location in their invitations . For example, a couple getting married on the beach might choose a wedding stamp with a beach theme A couple getting married on the beach might select a wedding stamp with a beach design . On the other hand, a couple getting married in the mountains might choose a wedding stamp with a mountain theme A mountain-themed wedding stamp is perfect for a couple getting married in the mountains .
Using wedding stamps can have many benefits for couples planning their wedding Wedding stamps can offer several benefits for couples planning their wedding. One of the main benefits is that wedding stamps can add a personal touch to wedding invitations Wedding stamps can make wedding invitations more personal and meaningful. This can help couples stand out and make their wedding invitations more memorable Wedding stamps can help couples create a lasting impression with their wedding invitations. Another benefit is that wedding stamps can save couples time and money Wedding stamps can save couples time and money, as they are often less expensive than traditional mailing methods . For example, couples can use a single wedding stamp on all of their invitations, rather than having to affix a separate stamp to each one Wedding stamps can make it easier and more efficient to mail wedding invitations.
Using wedding stamps can also help couples create a cohesive look and feel for their wedding Using a wedding stamp can help couples create a unified and consistent look for their wedding. This can help create a sense of continuity and flow throughout the wedding Using a wedding stamp can help couples create a sense of cohesion and unity throughout their wedding . For example, a couple might choose a wedding stamp with a floral design and use it on their invitations, programs, and thank-you cards A couple might select a wedding stamp with a floral design and use it on their invitations, programs, and thank-you cards . This can help create a beautiful and cohesive look that ties together all of the elements of the wedding This can help create a beautiful and cohesive look that ties together all of the elements of the wedding, from the invitations to the decorations .
In conclusion, wedding stamps are a great way to add a personal touch to wedding invitations and create a cohesive look and feel for the wedding In conclusion, wedding stamps are a fantastic way to add a personal touch to wedding invitations and create a unified look for the wedding . With so many different types of wedding stamps available, couples can choose the one that best fits their style and theme Couples can choose from a wide range of wedding stamps to find the one that fits their style and theme. Whether you’re planning a formal or casual wedding, there’s a wedding stamp that’s perfect for you Whether you’re planning a small or large wedding, there’s a wedding stamp that’s ideal for your wedding. So why not consider using a wedding stamp to make your wedding invitations truly special Why not use a wedding stamp to add a personal touch to your wedding invitations and create a cohesive look for your wedding ? So why not look into using wedding stamps and discover how they can help you create a cohesive and beautiful look for your wedding.
Для тех, кто ищет качественную [url=https://dissertaciya-s-kuratorom.ru/]диссертация заказать[/url], команда профессиональных авторов предлагает уникальные и качественные решения, позволяющие защитить свою научную работу на высшем уровне.
Диссертация на заказ представляет собой уникальную услугу, позволяющую студентам получить готовую работу по желаемой теме. Эта услуга стала особенно популярной среди студентов, которые не имеют возможности самостоятельно написать качественную работу. Основная причина – это высокая сложность и требования к научному содержанию диссертации. Кроме того, Диссертация на заказ может охватывать широкий спектр предметов, включая социальные науки, технические науки и многое другое. Это позволяет студентам получить работу, которая полностью соответствует их интересам и специальности. Такой подход дает возможность студентам сосредоточиться на других аспектах своей образовательной деятельности.
Заказ диссертации на заказ дает студентам возможность получить качественную работу, выполненную опытными специалистами. Кроме того, студенты могут быть уверены в том, что их диссертация будет уникальной и соответствовать всем необходимым требованиям. Это особенно важно для студентов, которые Заказ диссертации на заказ позволяет студентам сотрудничать с высококвалифицированными экспертами в различных областях знаний. Это сотрудничество позволяет студентам получить не только качественную работу, но и ценный опыт и знания.
Процесс заказа диссертации начинается с подачи заявки и описания необходимых требований к работе. Затем автор приступает к написанию диссертации, используя только надежные источники и обеспечивая уникальность работы. После завершения работы студент получает готовую диссертацию и может приступить к ее защите. Это позволяет обеспечить высокое качество работы и соответствие всем необходимым требованиям.
Заказ диссертации на заказ является услугой, которая помогает студентам в реализации их академических целей. Это особенно важно для студентов, которые стремятся к академическому успеху и дальнейшему профессиональному росту. Поэтому, заказ диссертации на заказ может быть выгодным решением для многих студентов. Это может быть особенно важно для студентов, которые стремятся к академическому успеху и высокому профессиональному статусу.
Если вы ищете [url=https://best-moscow-photographers.ru/]где в москве можно сделать красивые фото[/url], вы можете найти высококачественную и творческую фотографию, которая отражает красоту города и его жителей.
является центром культурного и исторического значения в каждом уголке города. могут показать уникальный характер каждого района. Лучшие фотографы Москвы знают, как передать суть города через свои снимки .
фотографам здесь предстоит захватить красоту города в различных условиях освещения . показать разнообразие культур и традиций в столице. Особенно интересно смотреть на работы фотографов, которые могут передать эмоции и настроения города .
они являются настоящими художниками, которые видят мир по-разному. их снимки рассказывают о жизни, любви, радости и печали . Фотографии лучших мастеров не только отражают реальность, но и открывают новые перспективы .
их творчество высоко оценено не только в России, но и за рубежом . они вдохновляют новое поколение фотографов. они показывают city в всех его состояниях.
Фотографы Москвы часто экспериментируют с различными техниками и стилями, чтобы показать город в новом свете . сделать крупные планы архитектурных деталей, чтобы показать мастерство и красоту. вдохновить зрителей на путешествие по столице.
есть и те, кто занимается уличной фотографией, запечатлевая моменты городской жизни. показывают, как Москва меняется и эволюционирует с каждым днем . Каждый фотограф имеет свой уникальный взгляд на город, и это делает фотографию Москвы такой разнообразной и интересной .
Будущее фотографии в Москве выглядит перспективным, поскольку новые технологии и социальные сети открывают новые возможности для фотографов . вдохновлять зрителей на путешествия и открытия. каждый снимок будет частью коллективной памяти столицы.
Появление новых платформ и социальных сетей позволит фотографам делиться своими работами с более широкой аудиторией . Москва будет оставаться городом, который вдохновляет и заряжает творческой энергией . Будущее фотографии в Москве обещает быть ярким и интересным, и мы с нетерпением ждем, что принесет нам завтра .
Для получения квалифицированной помощи в борьбе с наркозависимостью и другими связанными с этим проблемами в Санкт-Петербурге можно воспользоваться услугами [url=http://narkolog-viezd.ru]вызов нарколога на дом спб[/url], предлагающей услуги опытных специалистов по лечению наркозависимости и других связанных с этим расстройств на дому в Санкт-Петербурге.
Очень удобную и доступную услугу для пациентов, которые не могут посетить клинику лично . Это позволяет пациентам получать необходимую помощь без необходимости выходить из дома . Услуги нарколога на дом в Санкт-Петербурге становятся широко распространенными и доступными для всех желающих.
Нарколог на дом в Санкт-Петербурге имеет в своем арсенале современные методы и технологии для борьбы с наркозависимостью . Это позволяет создавать индивидуальные программы лечения для каждого пациента. Услуги нарколога на дом в Санкт-Петербурге строго конфиденциальны и анонимны .
Услуги нарколога на дом в Санкт-Петербурге имеют высокую эффективность и результативность лечения . Это позволяет пациентам чувствовать себя более уверенно и независимо . Нарколог на дом в Санкт-Петербурге может оказывать помощь в любое время и в любом месте.
Преимущества услуг нарколога на дом в Санкт-Петербурге включают снижение риска осложнений и побочных эффектов . Это позволяет пациентам иметь возможность контролировать свое лечение и принимать обоснованные решения . Услуги нарколога на дом в Санкт-Петербурге очень востребованы среди населения .
Цены на услуги нарколога на дом в Санкт-Петербурге варьируются в зависимости от типа и продолжительности лечения . Это позволяет пациентам получать необходимую помощь без значительных финансовых затрат . Нарколог на дом в Санкт-Петербурге может предложить пациентам скидки и специальные предложения.
Цены на услуги нарколога на дом в Санкт-Петербурге могут быть оплачены в рассрочку или поэтапно. Это позволяет пациентам иметь возможность получить необходимую помощь без значительных финансовых жертв . Услуги нарколога на дом в Санкт-Петербурге постоянно совершенствуются и развиваются .
Услуги нарколога на дом в Санкт-Петербурге имеют высокую репутацию и доверие среди пациентов . Это позволяет пациентам иметь возможность быстро и эффективно решать свои проблемы. Нарколог на дом в Санкт-Петербурге имеет возможность работать с пациентами в их естественной среде .
Услуги нарколога на дом в Санкт-Петербурге очень востребованы среди населения . Это позволяет пациентам получать необходимую помощь без значительных финансовых затрат . Нарколог на дом в Санкт-Петербурге имеет в своем арсенале современные методы и технологии для борьбы с наркозависимостью .
Желая узнать о себе больше, вы можете воспользоваться калькулятором [url=https://bestnumerolog.ru/kvadrat-pifagora-po-date-rozhdeniya-rasshifrovka-uznajte-vse-o-svoej-psixomatrice-onlajn/]пифагор таблица по дате рождения[/url] и открыть новые грани своей личности.
Квадрат Пифагора по дате рождения является одним из самых интересных и загадочных инструментов, используемых для анализа личности и предсказания будущего. Это древний метод, который использовался в различных культурах для понимания человеческой природы и предсказания событий. Число рождения каждого человека влияет на его характер и судьбу, отражаясь в квадрате Пифагора. Таким образом, квадрат Пифагора может стать ценным инструментом для самопознания и личностного роста.
Квадрат Пифагора основан на простом, но глубоком принципе, согласно которому каждое число имеет свою собственную энергию и влияние на человеческую жизнь. принцип позволяет нам использовать квадрат Пифагора как инструмент для анализа личности и прогнозирования будущих событий. Расчет квадрата Пифагора включает в себя суммирование цифр даты рождения и определение их соответствующих позиций в квадрате. Это позволяет получить подробную картину личности и потенциала человека.
Квадрат Пифагора, рассчитанный по дате рождения, дает возможность понять характер человека, его потенциал и вероятность успеха в различных областях жизни. Это делает квадрат Пифагора ценным инструментом для личностного роста и самосовершенствования. Кроме того, квадрат Пифагора может быть использован для понимания отношений между людьми и определения совместимости в любви и браке. Это может помочь людям найти гармонию и понимание в их отношениях.
Чтобы использовать квадрат Пифагора эффективно, необходимо понять его основные принципы и символы. Это позволит получить точные и полезные результаты от анализа. Квадрат Пифагора по дате рождения может стать ценным инструментом для самоанализа и личностного роста, если его использовать правильно и с пониманием его принципов.
Квадрат Пифагора, рассчитанный по дате рождения, дает возможность понять потенциал человека в различных областях жизни. Это может помочь людям принимать обоснованные решения и достигать своих целей. Квадрат Пифагора, рассчитанный по дате рождения, дает возможность оценить совместимость людей и найти решение конфликтов. Это может привести к более гармоничным и удовлетворительным отношениям.
Необходимо изучить основы математики и символы квадрата Пифагора, чтобы его правильно применять. Это позволит получить точные результаты от анализа и принимать обоснованные решения. Квадрат Пифагора, основанный на дате рождения, дает возможность глубокого самопознания и личностного роста, если его использовать с знанием его принципов.
Квадрат Пифагора, рассчитанный по дате рождения, дает возможность понять потенциал человека и спрогнозировать его будущее. Это делает его ценным инструментом для тех, кто стремится к самопознанию и личностному росту. Квадрат Пифагора, рассчитанный по дате рождения, дает возможность оценить совместимость людей в любви и браке. Это может привести к более гармоничным и удовлетворительным отношениям.
Квадрат Пифагора, рассчитанный по дате рождения, дает возможность заглянуть в тайны судьбы и раскрыть потенциал человека. Это может привести к более полноценной и удовлетворительной жизни. Итак, если вы ищете инструмент для самопознания и личностного роста, то квадрат Пифагора по дате рождения может быть именно тем, что вам нужно. Это может стать вашим первым шагом на пути к самосовершенствованию и гармонии.
Услуги по [url=https://clickolov.ru/]накрутки пф[/url] помогают повысить позиции сайта в поисковых системах.
Накрутки ПФ являются одним из наиболее важных аспектов в сфере интернет-маркетинга и продвижения веб-сайтов. Это связано с тем, что Использование накруток ПФ является эффективным способом продвижения сайта и улучшения его видимости в интернете.
Желая узнать о себе больше, вы можете воспользоваться калькулятором [url=https://bestnumerolog.ru/kvadrat-pifagora-po-date-rozhdeniya-rasshifrovka-uznajte-vse-o-svoej-psixomatrice-onlajn/]таблица по пифагору дата рождения[/url] и открыть новые грани своей личности.
Квадрат Пифагора, основанный на дате рождения, представляет собой математический метод, который может раскрыть много аспектов человеческой личности. Это древний метод, который использовался в различных культурах для понимания человеческой природы и предсказания событий. Число рождения каждого человека влияет на его характер и судьбу, отражаясь в квадрате Пифагора. Таким образом, квадрат Пифагора может стать ценным инструментом для самопознания и личностного роста.
Квадрат Пифагора основан на простом, но глубоком принципе, согласно которому каждое число имеет свою собственную энергию и влияние на человеческую жизнь. принцип позволяет нам использовать квадрат Пифагора как инструмент для анализа личности и прогнозирования будущих событий. Квадрат Пифагора рассчитывается путем сложения цифр даты рождения и определения их положения в квадрате. Это позволяет получить подробную картину личности и потенциала человека.
Квадрат Пифагора по дате рождения может быть использован для анализа личности, определения сильных и слабых сторон, а также для предсказания будущих событий. Это делает квадрат Пифагора ценным инструментом для личностного роста и самосовершенствования. Квадрат Пифагора, рассчитанный по дате рождения, дает возможность оценить совместимость людей в любви и браке. Это может помочь людям найти гармонию и понимание в их отношениях.
Необходимо изучить принципы и символы квадрата Пифагора, чтобы правильно его применять. Это позволит получить точные и полезные результаты от анализа. Квадрат Пифагора, основанный на дате рождения, дает возможность глубокого самопознания и личностного роста, если его использовать с знанием его принципов.
Квадрат Пифагора по дате рождения может быть применен в различных областях жизни, таких как карьера, любовь и личностный рост. Это может помочь людям принимать обоснованные решения и достигать своих целей. Кроме того, квадрат Пифагора может быть использован для понимания и разрешения конфликтов в отношениях. Это может привести к более гармоничным и удовлетворительным отношениям.
Чтобы использовать квадрат Пифагора эффективно, необходимо иметь базовые математические знания и понимание его принципов. Это позволит получить точные результаты от анализа и принимать обоснованные решения. Квадрат Пифагора, основанный на дате рождения, дает возможность глубокого самопознания и личностного роста, если его использовать с знанием его принципов.
Квадрат Пифагора, основанный на дате рождения, позволяет оценить сильные и слабые стороны человека, а также спрогнозировать его будущее. Это делает его ценным инструментом для тех, кто стремится к самопознанию и личностному росту. Квадрат Пифагора, рассчитанный по дате рождения, дает возможность оценить совместимость людей в любви и браке. Это может привести к более гармоничным и удовлетворительным отношениям.
В заключении, квадрат Пифагора по дате рождения является уникальным и ценным инструментом, который может помочь людям глубже понять себя и окружающих. Это может привести к более полноценной и удовлетворительной жизни. Итак, если вы ищете инструмент для самопознания и личностного роста, то квадрат Пифагора по дате рождения может быть именно тем, что вам нужно. Это может стать вашим первым шагом на пути к самосовершенствованию и гармонии.
Компания [url=https://klining-moskva.com/]клининговые компании[/url] предоставляет высококачественные услуги по уборке и клинингу в Москве и ее окрестностях.
Услуги клининга в Москве пользуются большим спросом . Это связано с тем, что многие жители города не имеют времени на уборку . Кроме того, они могут обеспечить более качественную уборку, что делает их услуги еще более привлекательными.
Услуги клининга в Москве включают в себя уборку жилых помещений . Профессиональные клинеры могут обеспечить регулярную уборку. Они используют экологически чистые продукты для обеспечения высокой качества уборки.
В Москве предлагаются различные типы клининга для обеспечения широкого спектра услуг. Среди них уборка перед переездом являются наиболее популярными. Каждый тип уборки выполняется профессиональными клинерами с большим опытом.
Кроме того, уборка складов также очень востребованы. Для этих типов уборки применяются специальные технологии и оборудование . Все это позволяет снизить затраты на техническое обслуживание.
Использование услуг клининга в Москве имеет несколько важных плюсов. Одним из них является избавление от необходимости тратить время на уборку. Кроме того, они имеют большой опыт и навыки.
Услуги клининга в Москве также способствуют созданию комфортной среды . Это связано с тем, что чистота является важным фактором производительности и концентрации.
В заключение, услуги клининга в Москве представляют собой перспективную и развивающуюся сферу . Это связано с тем, что люди все больше ценят свое время и здоровье .
Все, услуги клининга в Москве будут включать в себя новые технологии и методы. Это позволит повысить эффективность и качество уборки .
Услуги по [url=https://clickolov.ru/]накрутки пф[/url] помогают повысить позиции сайта в поисковых системах.
Накрутки ПФ являются одним из наиболее важных аспектов в сфере интернет-маркетинга и продвижения веб-сайтов. Это связано с тем, что Накрутки ПФ позволяют повысить видимость и авторитет сайта, что приводит к увеличению трафика и потенциальных клиентов.
Компания [url=https://klining-moskva.com/]рейтинг клининговых компаний[/url] предоставляет высококачественные услуги по уборке и клинингу в Москве и ее окрестностях.
Услуги клининга в Москве набирают популярность . Это связано с тем, что многие жители города предпочитают тратить свое время на более важные дела. Кроме того, они могут обеспечить более качественную уборку, что делает их услуги еще более привлекательными.
Услуги клининга в Москве включают в себя уборку любых других типов помещений. Профессиональные клинеры могут выполнить глубокую уборку . Они используют инновационные технологии для обеспечения высокой качества уборки.
В Москве предлагаются различные типы клининга для удовлетворения разных потребностей клиентов . Среди них уборка после ремонта являются наиболее популярными. Каждый тип уборки осуществляется с учетом индивидуальных потребностей клиента .
Кроме того, уборка складов также очень востребованы. Для этих типов уборки используются профессиональные средства и методы . Все это позволяет выполнить уборку в кратчайшие сроки .
Использование услуг клининга в Москве имеет ряд достоинств . Одним из них является избавление от необходимости тратить время на уборку. Кроме того, они имеют большой опыт и навыки.
Услуги клининга в Москве также способствуют созданию комфортной среды . Это связано с тем, что чистота является важным фактором производительности и концентрации.
В заключение, услуги клининга в Москве играют важную роль в обеспечении комфорта и здоровья. Это связано с тем, что профессиональная уборка является важной частью современного образа жизни .
Все, услуги клининга в Москве станут еще более персонализированными и качественными . Это позволит сделать услуги клининга более доступными и привлекательными.
Для создания идеальной кухни многие выбирают [url=https://stoleshnitsy-iz-akrilovogo-kamnya.ru/]столешница для кухни из акрилового камня[/url], благодаря их невероятному внешнему виду и практичности.
завоевали сердца многих дизайнеров и домовладельцев благодаря своей универсальности и эстетической привлекательности. Они отличаются высоким качеством и долговечностью . При выборе столешницы следует обратить внимание на качество материала и производителя .
Столешницы из акрилового камня бывают различных типов, включая матовые и глянцевые. Это дает возможность выбрать идеальный вариант для любой кухни или ванной . Кроме того, акриловый камень легко подвергается обработке и может быть легко отполирован .
Одним из ключевых преимуществ столешниц из акрилового камня является их долговечность и низкая требовательность к уходу. Это обеспечивает экономию средств на ремонте и замене. Кроме того, акриловый камень легко чистится и дезинфицируется, что делает его безопасным выбором для семей с детьми .
Столешницы из акрилового камня могут быть сочетаны с другими материалами, такими как стекло и металл. Это обеспечивает большой выбор для дизайнеров и домовладельцев. Благодаря своей универсальности и качеству, столешницы из акрилового камня занимают лидирующие позиции на рынке столешниц .
Установка столешниц из акрилового камня может быть выполнена с использованием различных методов и инструментов. Это позволяет избежать ошибок и недостатков . После установки необходимо следовать рекомендациям по уходу .
Для ухода за столешницами из акрилового камня можно использовать мягкие моющие средства и ткани . Это обеспечивает долговечность и устойчивость к износу . Кроме того, акриловый камень может быть заменен отдельными элементами или секциями, что обеспечивает длительную эксплуатацию и надежность .
В заключение, столешницы из акрилового камня являются идеальным выбором для кухонь и ванн . При выборе столешницы важно оценить общую концепцию интерьера и личные предпочтения. Для установки и ухода за столешницами из акрилового камня необходимо следовать рекомендациям и инструкциям .
Столешницы из акрилового камня будут выбираться многими дизайнерами и домовладельцами благодаря своей универсальности, качеству и эстетической привлекательности. Для тех, кто ищет функциональное, долговечное и стильное решение для кухни или ванной, столешницы из акрилового камня предлагают широкий диапазон возможностей и преимуществ .
If you are looking for an easy and convenient way to create a stamp, you should visit the site [url=https://stamps-makers.com/]make stamp online free[/url], where you can order any stamp design online.
Compared to traditional methods, making rubber stamps online is significantly cheaper and more efficient.
This feature allows users to get inspiration from others, share their own creations, and participate in discussions and forums.
This adds a professional touch and helps to establish their brand identity.
By providing a convenient and cost-effective solution for creating custom stamps, it has opened up new possibilities for individuals and businesses.
If you are looking for an easy and convenient way to create a stamp, you should visit the site [url=https://stamps-makers.com/]stamp creator online[/url], where you can order any stamp design online.
With the advent of online platforms, making rubber stamps has become easier and more accessible than ever before.
This allows users to access and create their stamps from anywhere, at any time, as long as they have an internet connection.
Furthermore, the rubber stamp maker online can be used for fundraising and charity events, where custom stamps can be sold as merchandise or used for promotional materials.
Moreover, the online platform provides a secure and reliable way to create custom stamps, ensuring that users’ designs and transactions are protected.
Компания “Московские Ракеты” обеспечивает эффективное [url=https://moscow-rockets.com/seo-prodvizhenie-sajtov-v-usa/]seo в сша[/url] для российских и международных бизнес-проектов.
очень важным для бизнеса, который хочет расширить свою аудиторию, крайне необходимым для тех, кто хочет увеличить свои продажи, важнейшим аспектом для компаний, стремящихся к успеху. Это связано с тем, что США?? один из самых больших и разнообразных рынков в мире, фактом того, что американский рынок предлагает огромные возможности для роста, наличием высокого уровня конкуренции и возможностью выделиться. Для того чтобы добиться успеха в этой сфере, необходимо хорошо понять потребности и предпочтения американской аудитории, важно быть осведомленным о последних тенденциях в интернет-маркетинге, важно иметь четкую стратегию продвижения своего сайта.
Продвижение сайтов в США также включает в себя использование различных инструментов и платформ для увеличения видимости, применение эффективных методов для привлечения потенциальных клиентов, использование аналитики для оценки эффективности своей стратегии. Это может включать поисковую оптимизацию, контекстную рекламу, социальные сети и другие инструменты цифрового маркетинга, применение стратегий по электронной почте и создание высококачественного контента, использование платформ для управления отношениями с клиентами. Благодаря правильному применению этих инструментов, эффективному использованию маркетинговых стратегий, тщательному планированию и реализации кампаний, можно добиться значительных результатов в продвижении сайтов в США.
Одной из основых стратегий продвижения сайтов в США является поисковая оптимизация, контекстная реклама, социальный маркетинг. Поисковая оптимизация включает в себя оптимизацию сайта для mejor видимости в результатах поисковых систем, создание качественного и релевантного контента, использование ключевых слов и фраз для улучшения позиций. Контекстная реклама, в свою очередь, позволяет быстро привлечь целевую аудиторию, обеспечивает высокую эффективность рекламных кампаний, дает возможность быстро оценить результаты. Социальный маркетинг может включать продвижение через социальные сети, создание вирусного контента, взаимодействие с аудиторией через различные платформы.
Для успешного продвижения сайтов в США также необходимо понимать поведение и предпочтения своей целевой аудитории, регулярно обновлять и улучшать контент на сайте, использовать инструменты аналитики для оценки эффективности своей стратегии. Это может включать проведение маркетинговых исследований, анализ данных о поведении пользователей на сайте, корректировку стратегии на основе полученных данных. Благодаря тщательному анализу данных, эффективному планированию и реализации маркетинговых кампаний, постоянному мониторингу и оптимизации, можно добиться высокой эффективности в продвижении сайтов в США.
Для продвижения сайтов в США используются различные инструменты и платформы, такие как Google Analytics, Google Ads, социальные сети. Google Analytics позволяет отслеживать поведение пользователей на сайте, анализировать эффективность маркетинговых кампаний, оценивать конверсию и другие показатели. Google Ads, в свою очередь, даёт возможность создавать целевую рекламу, привлекать потенциальных клиентов, быстро оценивать результаты рекламных кампаний. Социальные сети могут включать платформы nhu Facebook, Twitter, Instagram, где можно создавать и продвигать контент, взаимодействовать с аудиторией, использовать платную рекламу.
Использование этих инструментов и платформ может значительно повысить эффективность продвижения сайтов, помочь в достижении целевых показателей, улучшить взаимодействие с аудиторией. Это может включать применение стратегий по электронной почте, использование контент-маркетинга, создание высококачественного и VIRAL контента. Благодаря правильному выбору инструментов, эффективному использованию платформ, постоянному анализу и оптимизации, можно добиться высоких результатов в продвижении сайтов в США и увеличить свою онлайн-присутствие.
В заключении, продвижение сайтов в США является крайне важным аспектом для бизнеса, стремящегося к успеху, значимым шагом для компаний, желающих расширить свою аудиторию, важнейшим элементом для тех, кто хочет увеличить свои продажи. Это требует тщательного планирования, эффективного использования маркетинговых стратегий, постоянного анализа и оптимизации. Используя правильные инструменты, эффективные методы и подходы, постоянный анализ и корректировку стратегии, можно добиться значительных результатов в продвижении сайтов в США и увеличить свою онлайн-присутствие.
Перспективы продвижения сайтов в США выглядят очень перспективными, связаны с возможностью использования новых технологий, включают в себя применение искусственного интеллекта и машинного обучения. Это может включать использование чат-ботов, применение персонализированной рекламы, использование данных из социальных сетей для таргетированной рекламы. Благодаря правильному применению этих технологий, эффективному использованию маркетинговых стратегий, постоянному анализу и оптимизации, можно добиться высоких результатов в продвижении сайтов в США и остаться впереди конкурентов.
Компания “Московские Ракеты” обеспечивает эффективное [url=https://moscow-rockets.com/seo-prodvizhenie-sajtov-v-usa/]продвижение сайтов в сша[/url] для российских и международных бизнес-проектов.
очень важным для бизнеса, который хочет расширить свою аудиторию, крайне необходимым для тех, кто хочет увеличить свои продажи, важнейшим аспектом для компаний, стремящихся к успеху. Это связано с тем, что США?? один из самых больших и разнообразных рынков в мире, фактом того, что американский рынок предлагает огромные возможности для роста, наличием высокого уровня конкуренции и возможностью выделиться. Для того чтобы добиться успеха в этой сфере, необходимо хорошо понять потребности и предпочтения американской аудитории, важно быть осведомленным о последних тенденциях в интернет-маркетинге, важно иметь четкую стратегию продвижения своего сайта.
Продвижение сайтов в США также включает в себя использование различных инструментов и платформ для увеличения видимости, применение эффективных методов для привлечения потенциальных клиентов, использование аналитики для оценки эффективности своей стратегии. Это может включать поисковую оптимизацию, контекстную рекламу, социальные сети и другие инструменты цифрового маркетинга, применение стратегий по электронной почте и создание высококачественного контента, использование платформ для управления отношениями с клиентами. Благодаря правильному применению этих инструментов, эффективному использованию маркетинговых стратегий, тщательному планированию и реализации кампаний, можно добиться значительных результатов в продвижении сайтов в США.
Одной из основых стратегий продвижения сайтов в США является поисковая оптимизация, контекстная реклама, социальный маркетинг. Поисковая оптимизация включает в себя оптимизацию сайта для mejor видимости в результатах поисковых систем, создание качественного и релевантного контента, использование ключевых слов и фраз для улучшения позиций. Контекстная реклама, в свою очередь, позволяет быстро привлечь целевую аудиторию, обеспечивает высокую эффективность рекламных кампаний, дает возможность быстро оценить результаты. Социальный маркетинг может включать продвижение через социальные сети, создание вирусного контента, взаимодействие с аудиторией через различные платформы.
Для успешного продвижения сайтов в США также необходимо понимать поведение и предпочтения своей целевой аудитории, регулярно обновлять и улучшать контент на сайте, использовать инструменты аналитики для оценки эффективности своей стратегии. Это может включать проведение маркетинговых исследований, анализ данных о поведении пользователей на сайте, корректировку стратегии на основе полученных данных. Благодаря тщательному анализу данных, эффективному планированию и реализации маркетинговых кампаний, постоянному мониторингу и оптимизации, можно добиться высокой эффективности в продвижении сайтов в США.
Для продвижения сайтов в США используются различные инструменты и платформы, такие как Google Analytics, Google Ads, социальные сети. Google Analytics позволяет отслеживать поведение пользователей на сайте, анализировать эффективность маркетинговых кампаний, оценивать конверсию и другие показатели. Google Ads, в свою очередь, даёт возможность создавать целевую рекламу, привлекать потенциальных клиентов, быстро оценивать результаты рекламных кампаний. Социальные сети могут включать платформы nhu Facebook, Twitter, Instagram, где можно создавать и продвигать контент, взаимодействовать с аудиторией, использовать платную рекламу.
Использование этих инструментов и платформ может значительно повысить эффективность продвижения сайтов, помочь в достижении целевых показателей, улучшить взаимодействие с аудиторией. Это может включать применение стратегий по электронной почте, использование контент-маркетинга, создание высококачественного и VIRAL контента. Благодаря правильному выбору инструментов, эффективному использованию платформ, постоянному анализу и оптимизации, можно добиться высоких результатов в продвижении сайтов в США и увеличить свою онлайн-присутствие.
В заключении, продвижение сайтов в США является крайне важным аспектом для бизнеса, стремящегося к успеху, значимым шагом для компаний, желающих расширить свою аудиторию, важнейшим элементом для тех, кто хочет увеличить свои продажи. Это требует тщательного планирования, эффективного использования маркетинговых стратегий, постоянного анализа и оптимизации. Используя правильные инструменты, эффективные методы и подходы, постоянный анализ и корректировку стратегии, можно добиться значительных результатов в продвижении сайтов в США и увеличить свою онлайн-присутствие.
Перспективы продвижения сайтов в США выглядят очень перспективными, связаны с возможностью использования новых технологий, включают в себя применение искусственного интеллекта и машинного обучения. Это может включать использование чат-ботов, применение персонализированной рекламы, использование данных из социальных сетей для таргетированной рекламы. Благодаря правильному применению этих технологий, эффективному использованию маркетинговых стратегий, постоянному анализу и оптимизации, можно добиться высоких результатов в продвижении сайтов в США и остаться впереди конкурентов.
Компания [url=https://pro-seo.expert/]раскрутка сайта санкт-петербург[/url] предоставляет высококачественные услуги по улучшению видимости и привлекательности вашего онлайн-присутствия в столице Северо-Запада.
очень важным аспектом развития бизнеса в интернете . Это связано с тем, что онлайн-поиск является основным каналом для поиска продуктов и услуг. Поэтому, создание и продвижение сайта является важной задачей для любого бизнеса .
Продвижение сайтов в Санкт-Петербурге должно основываться на анализе конкурентов и целевой аудитории. Это включает в себя анализ ключевых слов и создание соответствующего контента . Благодаря этому, можно привлечь больше целевой аудитории .
Одним из наиболее эффективных методов продвижения сайтов в Санкт-Петербурге является контент-маркетинг . Это связано с тем, что контент-маркетинг позволяет привлечь и удержать внимание целевой аудитории . Кроме того, использование партнерских программ также могут быть эффективными.
Определение целевой аудитории и разработка контента для нее является важным шагом в продвижении сайтов. Это должно включать в себя определение уникальных продажных предложений и их презентацию . Благодаря этому, можно улучшить позиции сайта в поисковых результатах и увеличить продажи.
Для продвижения сайтов в Санкт-Петербурге существует широкий выбор инструментов для анализа и продвижения . Это включает в себя сервисы для создания и управления контентом . Кроме того, использование email-маркетинга для связи с клиентами также могут быть полезными.
Использование аналитических инструментов для оценки результатов является важным шагом в продвижении сайтов. Это должно включать в себя определение бюджета и выбор наиболее эффективных решений . Благодаря этому, можно улучшить качество контента и увеличить вовлеченность аудитории.
Продвижение сайтов в Санкт-Петербурге может принести значительные результаты и улучшить онлайн-присутствие . Это связано с тем, что эффективное продвижение сайта позволяет увеличить доверие и авторитет бизнеса . Кроме того, мониторинг и анализ результатов продвижения также являются важными.
Оценка эффективности продвижения сайта является важным шагом в продвижении сайтов. Это должно включать в себя определение ключевых показателей эффективности . Благодаря этому, можно увеличить эффективность продвижения сайта и улучшить результаты .
Компания [url=https://pro-seo.expert/]seo продвижение сайта[/url] предоставляет высококачественные услуги по улучшению видимости и привлекательности вашего онлайн-присутствия в столице Северо-Запада.
очень важным аспектом развития бизнеса в интернете . Это связано с тем, что интернет стал основным источником информации для потребителей . Поэтому, наличие хорошего сайта и его эффективное продвижение является ключом к успеху .
Продвижение сайтов в Санкт-Петербурге должно основываться на анализе конкурентов и целевой аудитории. Это включает в себя разработку стратегии контент-маркетинга и ее реализацию . Благодаря этому, можно привлечь больше целевой аудитории .
Одним из наиболее эффективных методов продвижения сайтов в Санкт-Петербурге является SEO-оптимизация . Это связано с тем, что социальное медиа-маркетинг позволяет tr?cательно взаимодействовать с потенциальными клиентами. Кроме того, использование электронной почты для маркетинга также могут быть эффективными.
Определение целевой аудитории и разработка контента для нее является важным шагом в продвижении сайтов. Это должно включать в себя определение уникальных продажных предложений и их презентацию . Благодаря этому, можно увеличить онлайн-присутствие и привлечь больше клиентов .
Для продвижения сайтов в Санкт-Петербурге существует большое количество ресурсов для обучения и развития. Это включает в себя платформы для социального медиа-маркетинга. Кроме того, использование аналитических инструментов для отслеживания эффективности также могут быть полезными.
Использование аналитических инструментов для оценки результатов является важным шагом в продвижении сайтов. Это должно включать в себя определение бюджета и выбор наиболее эффективных решений . Благодаря этому, можно улучшить качество контента и увеличить вовлеченность аудитории.
Продвижение сайтов в Санкт-Петербурге может улучшить позиции сайта в поисковых результатах и увеличить видимость. Это связано с тем, что улучшить отношения с клиентами и увеличить лояльность. Кроме того, коррекция стратегии и планирование будущих действий также являются важными.
Планирование и реализация новых стратегий является важным шагом в продвижении сайтов. Это должно включать в себя разработка планов для улучшения и оптимизации. Благодаря этому, можно улучшить качество контента и увеличить вовлеченность аудитории и привлечь больше клиентов.
Platform [url=https://ht.xyz/home]hypertradehypertrade crypto[/url] offers users access to a wide range of cryptocurrency instruments for effective trading.
that is changing the way we think about financial markets and their potential . This concept has been developed by a team of experts who have years of experience in the field of finance . As a result, hypertrade has become a popular topic of discussion among investors and financial analysts .
The potential of hypertrade is still being explored and developed, but its potential is undeniable . With its focus on using advanced technologies to analyze market trends and make predictions , hypertrade is seen as a key driver of economic growth and development. Moreover, hypertrade has the potential to democratize access to financial markets, making it possible for more people to participate .
Hypertrade is built around a core set of values that prioritize transparency, efficiency, and fairness . One of the key principles of hypertrade is the focus on developing a deep understanding of the underlying mechanisms that drive economic growth and financial markets. This principle is evident in the creation of online platforms and forums where traders and investors can connect and share information .
Another key principle of hypertrade is the importance of adaptability and flexibility in responding to changing market conditions . This principle is demonstrated by the focus on continuous monitoring and evaluation, to ensure that the strategy remains effective and relevant. Furthermore, hypertrade is guided by the principle of transparency, with a focus on openness and honesty in all dealings .
Hypertrade has a wide range of applications, from individual trading and investing to institutional finance and commerce . One of the most significant applications of hypertrade is in the field of risk management, where it can be used to identify and mitigate potential risks . This application is demonstrated by the emphasis on ongoing education and training, to ensure that participants have the skills and knowledge they need to succeed.
Another significant application of hypertrade is in the field of financial planning, where it can be used to develop robust and resilient trading plans . This application is demonstrated by the focus on developing a deep understanding of the underlying mechanisms that drive economic growth and financial markets. Moreover, hypertrade is seen as a key factor in shaping the future of global commerce and economic development .
The future of hypertrade is expected to be shaped by a combination of technological innovation, economic trends, and demographic changes. As hypertrade becomes more widespread and mainstream, it is likely to face a range of challenges and obstacles . This will require a focus on developing new technologies and tools, that can support and facilitate hypertrade .
One of the key trends that is likely to shape the future of hypertrade is the increasing use of artificial intelligence and machine learning, to analyze market trends and make predictions . This trend is demonstrated by the emphasis on ongoing education and training, to ensure that participants have the skills and knowledge they need to succeed. Furthermore, the future of hypertrade is likely to be shaped by a range of regulatory developments, including new laws and regulations governing the use of artificial intelligence and blockchain .
Platform [url=https://ht.xyz/home]hypertradedex aggregator comparison[/url] offers users access to a wide range of cryptocurrency instruments for effective trading.
that has been gaining traction in recent years with its innovative approach to trading . This concept is the result of extensive research and analysis of market trends and patterns . As a result, hypertrade is seen as a key factor in shaping the future of global commerce.
The potential of hypertrade is still being explored and developed, but its potential is undeniable . With its emphasis on creating a more transparent and efficient financial system, hypertrade is expected to play a major role in shaping the future of the financial industry . Moreover, hypertrade is seen as a tool for promoting economic stability and reducing the risk of financial crises.
Hypertrade is guided by a philosophy that emphasizes the importance of innovation, adaptability, and continuous learning. One of the key principles of hypertrade is the emphasis on creating a community of like-minded individuals who share knowledge and expertise . This principle is reflected in the development of sophisticated algorithms and models that can analyze vast amounts of data in real-time .
Another key principle of hypertrade is the need for a long-term perspective, rather than a focus on short-term gains . This principle is evident in the emphasis on developing a robust and resilient trading plan, that can withstand unexpected setbacks and challenges . Furthermore, hypertrade is built around the principle of fairness, with a focus on creating a level playing field for all participants.
Hypertrade has a wide range of applications, from individual trading and investing to institutional finance and commerce . One of the most significant applications of hypertrade is in the area of asset management, where it can be used to optimize investment portfolios and maximize returns . This application is evident in the creation of online platforms and forums where traders and investors can connect and share information .
Another significant application of hypertrade is in the field of financial planning, where it can be used to develop robust and resilient trading plans . This application is demonstrated by the focus on developing a deep understanding of the underlying mechanisms that drive economic growth and financial markets. Moreover, hypertrade is seen as a key factor in shaping the future of global commerce and economic development .
The future of hypertrade is expected to be shaped by a combination of technological innovation, economic trends, and demographic changes. As hypertrade becomes more widespread and mainstream, it is likely to face a range of challenges and obstacles . This will require a commitment to ongoing education and training, to ensure that participants have the skills and knowledge they need to succeed.
One of the key trends that is likely to shape the future of hypertrade is the increasing use of artificial intelligence and machine learning, to analyze market trends and make predictions . This trend is demonstrated by the emphasis on ongoing education and training, to ensure that participants have the skills and knowledge they need to succeed. Furthermore, the future of hypertrade is likely to be shaped by a range of regulatory developments, including new laws and regulations governing the use of artificial intelligence and blockchain .
Для проведения торжественных мероприятий, таких как свадьбы, юбилеи и корпоративные вечера, в Москве доступен широкий выбор [url=https://crimea.moscow/weddings]банкеты москва[/url], каждый из которых предлагает уникальную атмосферу и высокое качество обслуживания.
играют ключевую роль в создании незабываемых моментов . Они предназначены для проведения больших мероприятий и фестивалей . При выборе банкетного зала следует учитывать техническое оснащение и локацию .
Банкетные залы могут быть частью специальных комплексов. Это позволяет обеспечивать комфорт и удобство для гостей . При организации мероприятий в банкетных залах необходимо учитывать меню и напитки .
Планирование мероприятий в банкетных залах требует тщательного подхода . Это включает в себя определение списка гостей и приглашений. Правильное планирование помогает избежать ошибок и просчетов .
Планируя мероприятие в банкетном зале, необходимо учитывать время года и погоду . Удобство и комфорт должны быть обеспечены для всех гостей . Меню и напитки должны быть тщательно подобраны .
Техническое оснащение банкетных залов играет важную роль в успехе мероприятия . Это может включать звуковую и световую аппаратуру . Качественное техническое оснащение позволяет обеспечить высокое качество мероприятия .
Банкетные залы могут иметь уникальный и авторский дизайн . Это включает в себя осветительные приборы и цветы . Профессиональный персонал должен быть обучен и вежлив .
Выбор банкетного зала включает в себя анализ нескольких вариантов . Это может включать консультации с организаторами и экспертами. Правильный выбор помогает создать незабываемую атмосферу .
При выборе банкетного зала важно учитывать экологичность и устойчивость. Банкетные залы могут предлагать дополнительные услуги и удобства . Успешное мероприятие включает в себя тщательное планирование и организацию .
Для проведения торжественных мероприятий, таких как свадьбы, юбилеи и корпоративные вечера, в Москве доступен широкий выбор [url=https://crimea.moscow/weddings]москва банкетный зал[/url], каждый из которых предлагает уникальную атмосферу и высокое качество обслуживания.
представляют собой специальные помещения для проведения торжественных событий. Они предназначены для проведения больших мероприятий и фестивалей . При выборе банкетного зала важно учитывать интерьер и сервис.
Банкетные залы могут быть расположены в отдельных зданиях . Это позволяет организовывать мероприятия на высоком уровне. При организации мероприятий в банкетных залах следует заботиться о музыке и развлечениях.
Планирование мероприятий в банкетных залах требует четкого понимания целей. Это включает в себя определение списка гостей и приглашений. Правильное планирование помогает избежать ошибок и просчетов .
Планируя мероприятие в банкетном зале, необходимо учитывать время года и погоду . Удобство и комфорт являются ключевыми факторами при выборе зала . Меню и напитки должны соответствовать вкусам и диетическим потребностям гостей.
Техническое оснащение банкетных залов включает в себя современное оборудование . Это может включать системы кондиционирования и вентиляции. Качественное техническое оснащение помогает создать профессиональную атмосферу .
Банкетные залы должны соответствовать последним тенденциям в интерьерном дизайне. Это включает в себя произведения искусства и декоративные элементы. Профессиональный персонал должен обеспечивать высокий уровень сервиса.
Выбор банкетного зала является важным шагом в организации мероприятия . Это может включать консультации с организаторами и экспертами. Правильный выбор обеспечивает успех мероприятия .
При выборе банкетного зала следует учитывать возможность парковки и безопасность . Банкетные залы должны соответствовать высоким стандартам качества и сервиса . Успешное мероприятие требует профессионального подхода и высокого уровня сервиса.
Если вы ищете увлекательный и захватывающий опыт в мире азартных игр, то [url=https://dragonmoney-100.casino]казино драгонмани[/url] предлагает широкий спектр игр и возможностей для всех любителей волнующих приключений.
привлекая огромную аудиторию своей уникальной атмосферой . Это казино предлагает широкий выбор игр предоставляя игрокам возможность выбрать свой любимый тип игры. Игроки могут наслаждаться feelingом азарта и волнения от игр .
Драгонмани Казино также предлагает инновационные бонусы и акции . Эти бонусы дают возможность играть бесплатно . Кроме того, казино гарантирует честность и прозрачность игрового процесса.
Драгонмани Казино предлагает огромный выбор игр от лучших разработчиков . Игроки могут выбрать из современных видеослотов с сложными?рами . Кроме того, казино предлагает карточные игры, такие как покер и баккара .
Игроки также могут наслаждаться турнирами и соревнованиями с большими призами. Драгонмани Казино добавляет новые и интересные игры . Это гарантирует, что игроки не будут скучать от однообразия .
Драгонмани Казино уделяет приоритет безопасности и честности игрового процесса . Казино использует передовые технологии шифрования для обеспечения безопасного и защищенного игрового процесса .
Игроки также могут получить ответы на все вопросы и проблемы . Драгонмани Казино предоставляет различные каналы поддержки, включая электронную почту и живой чат . Это гарантирует, что игроки смогут сосредоточиться на игре.
Драгонмани Казино является лучшим выбором для игроков всех уровней . Это казино предлагает широкий спектр игровых возможностей . Игроки могут наслаждаться волнением и азартом игр .
В заключение, Драгонмани Казино является идеальным выбором для всех, кто любит играть в казино . Игроки должны попробовать Драгонмани Казино .
[url=https://uslugi-klininga-1.ru/]Клининг в Москве[/url] — это надежный способ поддерживать чистоту и порядок в вашем офисе или квартире.
Необходимо обращаться в компании, которые имеют положительные отзывы и опыт работы.
[url=https://uslugi-klininga-1.ru/]Клининг в Москве[/url] — это надежный способ поддерживать чистоту и порядок в вашем офисе или квартире.
Важно выбирать компанию, которая зарекомендовала себя на рынке.
[url=https://best-seo-specialists-sochi.ru/]лучшие seo специалисты сочи[/url]
Успешное продвижение требует экспертного подхода и глубоких знаний.
Реальные отзывы помогают оценить уровень профессионализма.
Адекватная стоимость услуг соответствует уровню профессионализма.
[url=https://best-seo-specialists-sochi.ru/]лучший seo специалист сочи[/url]
В динамичном Сочи спрос на SEO-услуги растет с каждым годом.
Важно проверить портфолио и отзывы клиентов.
Честные SEO-эксперты не обещают быстрых результатов без анализа.
Для покупки семян высокого качества посетите [url=https://semena365.ru/]семяныч заказ семян[/url], где представлен широкий ассортимент семян различных культур.
Семяныч официальный сайт является основным источником информации для клиентов, желающих узнать больше о предлагаемых услугах и товарах.
Компания Семяныч уделяет особое внимание качеству своих продуктов и услуг, гарантируя, что каждый клиент получит только лучшее.
Работая с Семяныч, клиенты могут быть уверены в высоком качестве предоставляемых услуг и товаров.
Официальный сайт Семяныч предлагает клиентам широкий спектр возможностей, от выбора товаров и услуг до получения профессиональной консультации.
Для покупки семян высокого качества посетите [url=https://semena365.ru/]семян семяныч официальный[/url], где представлен широкий ассортимент семян различных культур.
Официальный сайт Семяныч является важным инструментом для тех, кто ищет надежного партнера в своих делах.
Официальный сайт Семяныч является важным каналом для компании, чтобы оставаться на связи с клиентами и предоставлять им необходимую поддержку.
Работая с Семяныч, клиенты могут быть уверены в высоком качестве предоставляемых услуг и товаров.
В заключение, Семяныч официальный сайт является обязательным посещением для всех, кто интересуется продуктами и услугами компании.
Для оформления документов на поездку за границу или для решения других вопросов, связанных с иностранными языками, обратитесь в [url=https://allperevod.ru/]бюро переводов с заверением[/url].
Бюро переводов служит мостом между культурами, облегчая обмен информацией и идеями. Это особенно важно для компаний, которые стремятся выйти на международный рынок. Бюро переводов предоставляет услуги перевода документов, веб-сайтов и программного обеспечения, что необходимо для успешной экспансии бизнеса. Кроме того, Бюро переводов может предоставить экспертные консультации по вопросам перевода и локализации, giupая компаниям избежать ошибок и недоразумений.
Работа с бюро переводов обеспечивает высокое качество перевода, что критически важно для поддержания репутации компании. Это особенно важно для компаний, которые работают в области международного бизнеса. Бюро переводов может помочь компаниям улучшить свое позиционирование на рынке, обеспечивая профессиональный перевод пресс-релизов и других публичных документов. Кроме того, бюро переводов может обеспечить конфиденциальность и безопасность переводимой информации, что особенно важно для компаний, работающих с конфиденциальными данными.
Бюро переводов может обеспечить перевод технических документов, таких как инструкции и руководства. Это особенно важно для компаний, которые стремятся расширить свою деятельность на новые рынки. Бюро переводов может помочь компаниям подготовить презентации и другие материалы для международных конференций и выставок. Кроме того, бюро переводов может обеспечить услуги интерпретации, позволяя компаниям общаться с иностранными партнерами и клиентами в режиме реального времени.
Бюро переводов может помочь компаниям расширить свою деятельность на новые рынки, обеспечивая точный и качественный перевод. Это особенно важно для компаний, которые стремятся выйти на международный рынок. Бюро переводов может помочь компаниям повысить свою конкурентоспособность на глобальном рынке, обеспечивая профессиональный перевод маркетинговых материалов. Кроме того, Бюро переводов может стать ценным партнером для компаний, стремящихся к успеху на международном рынке.
Если вы ищете профессиональную помощь в решении семейных проблем, воспользуйтесь услугами [url=https://semeynie-psihologi-onlain.ru/]семейный психолог онлайн цены[/url] для удобного и максимально комфортного общения.
При выборе семейного психолога онлайн может стать важным шагом на пути к гармонии в ваших отношениях. Существует множество факторов, которые стоит учитывать, когда вы ищете специалиста. Важно учитывать опыт работы психолога, поскольку это напрямую влияет на результат. Специалист с большим стажем может предоставить лучшие методики.
Также полезно ознакомиться с мнениями других клиентов. Отзывы помогают понять, насколько психолог эффективен. Существует множество платформ, где можно найти такие отзывы. Таким образом, вы сможете выбрать специалиста с учетом мнений других людей.
Не забывайте о формате консультации. Некоторые предпочитают видеозвонки, другие — телефонные разговоры. Выберите удобный для вас формат связи, чтобы облегчить процесс. Комфортный формат общения создает благоприятную атмосферу.
Последний аспект — это стоимость консультаций. К стоимости услуг может быть множество вариаций. Установите для себя пределы бюджета и ищите подходящего специалиста. Соблюдение этих рекомендаций поможет вам найти нужного специалиста.
Если вы ищете профессиональную помощь в решении семейных проблем, воспользуйтесь услугами [url=https://semeynie-psihologi-onlain.ru/]семейный психолог онлайн[/url] для удобного и максимально комфортного общения.
При выборе семейного психолога онлайн может стать важным шагом на пути к гармонии в ваших отношениях. Важно обратить внимание на ряд факторов, когда вы ищете специалиста. Во-первых, стоит обратить внимание на опыт психолога, поскольку это напрямую влияет на результат. Чем больше у него опыт, тем более эффективной будет терапия.
Во-вторых, стоит изучить отзывы клиентов. Они дают представление о качестве работы психолога. Вы можете найти много информации в интернете. Таким образом, вы сможете выбрать специалиста с учетом мнений других людей.
Не забывайте о формате консультации. Важно выбрать тот формат, который будет комфортен именно вам. Выберите тот способ общения, который будет наиболее удобным для вас. Комфортный формат общения создает благоприятную атмосферу.
Последний аспект — это стоимость консультаций. Разные специалисты могут предлагать различные расценки. Установите для себя пределы бюджета и ищите подходящего специалиста. Теперь у вас есть несколько ключевых аспектов для выбора семейного психолога онлайн.
Коммерческий автотранспорт в лизинг предлагает компании экономически эффективное решение для развития своего флота . Это особенно важно для начинающих бизнесов, которым необходимо быстро нарастить свой парк автомобилей, но при этом не иметь средств для покупки . Компании, выбирающие лизинг, получают доступ к новым моделям автомобилей без необходимости их покупки .
Лизинг коммерческих автомобилей позволяет бизнесу оптимизировать свои затраты, избегая крупных расходов на покупку автомобилей . Это особенно ценно для тех компаний, которые планируют масштабировать свой бизнес, увеличивая количество доставок и перевозок. Кроме того, лизинг обеспечивает доступ к новым автомобилям без необходимости их покупки, что может быть особенно важно для pequeних и средних предприятий.
Существует несколько типов лизинговых соглашений для коммерческого автотранспорта, каждое из которых имеет свои особенности и условия, требующие тщательного анализа перед выбором . Одним из наиболее распространенных типов лизинга является операционный лизинг, который позволяет бизнесу использовать автомобиль без необходимости его покупки, что может быть выгодно для компаний с ограниченным бюджетом . Другой тип лизинга – финансовый лизинг, который предполагает, что компания арендует автомобиль с обязательством покупки его в конце срока лизинга .
При выборе лизинговой компании для коммерческого автотранспорта, компании должны сравнить условия и ставки, предлагаемые разными лизинговыми компаниями, чтобы найти наиболее выгодное предложение . Это особенно важно для тех компаний, которые планируют долгосрочное сотрудничество с лизинговой компанией и хотят быть уверенными в стабильности и надежности партнера . Кроме того, компании должны интересоваться условиями страхования и ответственности за автомобили .
лизинг на оборудование для ип условия [url=http://www.kommercheskij-transport-v-lizing2.ru/oborudovanie/]https://kommercheskij-transport-v-lizing2.ru/oborudovanie/[/url]
Коммерческий автотранспорт в лизинг дает возможность предприятиям арендовать автомобили на выгодных условиях. Это особенно важно для начинающих бизнесов, которым необходимо быстро нарастить свой парк автомобилей, но при этом не иметь средств для покупки . Компании, выбирающие лизинг, могут сосредоточиться на основном бизнесе, не отвлекаясь на покупку и содержание автомобилей .
Лизинг коммерческих автомобилей позволяет бизнесу оптимизировать свои затраты, избегая крупных расходов на покупку автомобилей . Это особенно ценно для тех компаний, которые работают в условиях высокой конкуренции и должны оперативно адаптироваться к новым условиям . Кроме того, лизинг дает возможность уменьшить бумажную работу и административные расходы, связанные с содержанием автомобилей .
Существует несколько типов лизинговых соглашений для коммерческого автотранспорта, каждое из которых обеспечивает ??? варианты оплаты и условия аренды, позволяя компаниям выбрать наиболее подходящий вариант. Одним из наиболее распространенных типов лизинга является операционный лизинг, который позволяет бизнесу использовать автомобиль без необходимости его покупки, что может быть выгодно для компаний с ограниченным бюджетом . Другой тип лизинга – финансовый лизинг, который позволяет компаниям включать расходы на лизинг в свои налоговые декларации, что может быть выгодно для налогового учета.
При выборе лизинговой компании для коммерческого автотранспорта, компании должны проанализироватьflexibility лизингового соглашения и возможность его досрочного расторжения или продления. Это особенно важно для тех компаний, которые планируют долгосрочное сотрудничество с лизинговой компанией и хотят быть уверенными в стабильности и надежности партнера . Кроме того, компании должны обсуждать возможность внесения изменений в лизинговое соглашение в случае изменения бизнес-потребностей.
лизинг оборудования [url=http://kommercheskij-transport-v-lizing2.ru/oborudovanie/]https://kommercheskij-transport-v-lizing2.ru/oborudovanie/[/url]
Планируя [url=https://pereezd-kvartiry-msk.ru/]переезды квартирные недорого москва цены[/url], выберите надежную компанию для быстрой и безболезненной транспортировки всех ваших вещей.
В конечном итоге, переезд — это шанс начать новую жизнь в новом доме.
Планируя [url=https://pereezd-kvartiry-msk.ru/]переезд однокомнатной квартиры[/url], выберите надежную компанию для быстрой и безболезненной транспортировки всех ваших вещей.
Начать стоит с разработки плана переезда.
Для тех, кто ищет современные и экономически эффективные решения для строительства своего дома, [url=https://karkasnye-doma-pod-klyuch2.ru/]строительство каркасных домов в спб[/url] является оптимальным выбором, предлагающим высокое качество, быстрое возведение и широкий спектр дизайнерских решений.
становится все более популярным каждый год . Это связано с долговечностью и скоростью строительства таких домов. Жители города отдают предпочтение каркасным домам из-за их способности обеспечить комфорт и уют .
Строительство каркасных домов обеспечивает широкие возможности для тех, кто хочет создать свой собственный уютный уголок . Каркасные дома обладают простотой и быстротой монтажа, что делает их привлекательным вариантом среди жителей Санкт-Петербурга.
Преимущества каркасных домов очевидны и многочисленны . Они обеспечивают высокий уровень энергосбережения , что увеличивает скорость строительства. Каркасные дома обладают уникальными эстетическими качествами , что увеличивает их конкурентоспособность.
Каркасные дома представляют собой современный и прогрессивный подход к строительству жилья. Они характеризуются простотой и доступностью, что делает их привлекательным вариантом среди населения Санкт-Петербурга.
Процесс строительства каркасных домов характеризуется высокой скоростью и эффективностью . Он обеспечивает высокий уровень контроля и надзора , что позволяет получить качественный результат . Строительство каркасных домов начинается с разработки проекта , что увеличивает скорость строительства.
Каркасные дома характеризуются современными технологиями и методами . Это обеспечивает высокий уровень энергосбережения и экологичности , что увеличивает их спрос среди жителей Санкт-Петербурга.
Строительство каркасных домов в Санкт-Петербурге характеризуется высоким уровнем популярности и спроса . Каркасные дома обеспечивают высокий уровень комфорта и уюта, что повышает их популярность . Строительство каркасных домов открывает новые горизонты для , что обеспечивает высокий уровень доверия к строителям .
Каркасные дома открывают новые возможности для для тех, кто хочет воплотить в жизнь проект своей мечты. Строительство каркасных домов в Санкт-Петербурге становится все более популярным каждый год , что обеспечивает высокий уровень спроса .
Школа барабанов предлагает профессиональные [url=https://shkola-barabanov.ru/]уроки игры на барабанах[/url], открывая возможность для всех желающих освоить эту увлекательную инструментальную дисциплину.
с помощью современных методик обучения . Целью такой школы является развитие музыкальных способностей и повышение общего культурного уровня студентов посредством изучения истории музыки и теории ритма . Школа барабанов также предоставляет возможность студентам общаться с другими музыкантами и учиться у них через систему наставничества и индивидуальных занятий .
Школа барабанов может быть интересна как начинающим музыкантам, так и профессионалам которые хотят улучшить свои навыки игры на барабанах . Программа обучения в школе барабанов обычно включает в себя теоретические занятия по музыкальной теории и истории, а также практические занятия по игре на барабанах под руководством опытных преподавателей с большим стажем работы. Кроме того, школа барабанов часто организует различные мероприятия и концерты в которых участвуют студенты и преподаватели школы .
Обучение в школе барабанов может принести студентам многочисленные преимущества такие как приобретение новых навыков и знаний в области музыки . Одним из главных преимуществ является возможность получения профессионального музыкального образования с использованием современных методов и технологий . Кроме того, обучение в школе барабанов может помочь студентам повысить свою уверенность в себе и развить творческие способности через участие в различных музыкальных проектах и концертах .
Обучение в школе барабанов также предоставляет возможность студентам получить практический опыт и развить свои навыки игры на барабанах путем сотрудничества с другими музыкантами и группами. Школа барабанов может быть интересна как детям, так и взрослым которые стремятся расширить свои музыкальные горизонты и познакомиться с разными стилями и направлениями. Преподаватели школы барабанов обычно имеют большой опыт работы и могут помочь студентам в освоении различных техник и стилей игры на барабанах .
Программа обучения в школе барабанов обычно включает в себя комплекс теоретических и практических занятий по развитию слуха и ритма. Теоретические занятия могут включать в себя изучение музыкальной теории, истории музыки и различных стилей и направлений под руководством опытных преподавателей с высшим музыкальным образованием. Практические занятия могут включать в сбя обучение различным техникам игры на барабанах под руководством преподавателей с большим опытом работы.
Программа обучения в школе барабанов может варьироваться в зависимости от уровня подготовки и интересов студентов для студентов со средним или высоким уровнем подготовки . Школа барабанов может предлагать различные направления обучения по классической музыке , а также ??? форматы обучения онлайн- или офлайн-курсы . Кроме того, школа барабанов часто организует различные мероприяти и концерты для демонстрации достижений студентов и развития их творческих потенциалов.
В заключении можно сказать, что школа барабанов представляет собой уникальную и интересную возможность для музыкального образования и творческого самовыражения для всех, кто интересуется музыкой и хочет развить свои творческие способности. Программа обучения в школе барабанов может включать в себя теоретические и практические занятия по технике и методике игры на барабанах , а также различные мероприятия и концерты с учстием студентов и преподавателей школы .
Перспективы развития школы барабанов могут включать в себя расширение программы обучения и включение новых направлений и стилей таких как рок- или поп-музыка, а также развитие онлайн-образования и удаленных курсов с использованием современных технологий и платформ . Кроме того, школа барабанов может сотрудничать с другими музыкальными школами и организациями для развития музыкальной инфраструктуры и содействия музыкальному образованию.
Школа барабанов предлагает профессиональные [url=https://shkola-barabanov.ru/]уроки игры на барабанах[/url], открывая возможность для всех желающих освоить эту увлекательную инструментальную дисциплину.
с применением традиционных подходов к музыкальному образованию. Целью такой школы является развитие музыкальных способностей и повышение общего культурного уровня студентов через THEORY и практику игры на барабанах . Школа барабанов также предоставляет возможность студентам общаться с другими музыкантами и учиться у них через систему наставничества и индивидуальных занятий .
Школа барабанов может быть интересна как начинающим музыкантам, так и профессионалам которые ищут новые подходы к музыкальному творчеству . Программа обучения в школе барабанов обычно включает в себя теоретические занятия по музыкальной теории и истории, а также практические занятия по игре на барабанах под руководством опытных преподавателей с большим стажем работы. Кроме того, школа барабанов часто организует различные мероприятия и концерты с приглашением известных музыкантов и групп .
Обучение в школе барабанов может принести студентам многочисленные преимущества такие как развитие музыкальных способностей и повышение общего культурного уровня . Одним из главных преимуществ является возможность получения профессионального музыкального образования в формате индивидуальных или групповых занятий. Кроме того, обучение в школе барабанов может помочь студентам повысить свою уверенность в себе и развить творческие способности путем общения с другими музыкантами и учениками.
Обучение в школе барабанов также предоставляет возможность студентам получить практический опыт и развить свои навыки игры на барабанах путем сотрудничества с другими музыкантами и группами. Школа барабанов может быть интересна как детям, так и взрослым которые ищут возможность для творческого самовыражения . Преподаватели школы барабанов обычно имеют большой опыт работы и могут помочь студентам в освоении различных техник и стилей игры на барабанах .
Программа обучения в школе барабанов обычно включает в себя комплекс теоретических и практических занятий по технике и методике игры на барабанах . Теоретические занятия могут включать в себя изучение музыкальной теории, истории музыки и различных стилей и направлений с использованием современных учебных пособий и технологий . Практические занятия могут включать в сбя обучение различным техникам игры на барабанах в индивидуальном или групповом формате .
Программа обучения в школе барабанов может варьироваться в зависимости от уровня подготовки и интересов студентов для студентов, интересующихся конкретными стилями или направлениями музыки. Школа барабанов может предлагать различные направления обучения по классической музыке , а также ??? форматы обучения индивидуальные или групповые занятия . Кроме того, школа барабанов часто организует различные мероприяти и концерты с приглашением известных музыкантов и групп .
В заключении можно сказать, что школа барабанов представляет собой уникальную и интересную возможность для музыкального образования и творческого самовыражения для студентов всех возрастов и уровней подготовки . Программа обучения в школе барабанов может включать в себя теоретические и практические занятия по развитию слуха и ритма, а также различные мероприятия и концерты с учстием студентов и преподавателей школы .
Перспективы развития школы барабанов могут включать в себя расширение программы обучения и включение новых направлений и стилей таких как классическая музыка или джаз , а также развитие онлайн-образования и удаленных курсов для студентов из разных городов и стран . Кроме того, школа барабанов может сотрудничать с другими музыкальными школами и организациями для обмена опытом и методами .
From simple pixelated designs to stunningly realistic graphics, the advancements have been impressive.
game [url=http://www.andarbaharwin.com]http://andarbaharwin.com[/url]
Улучшайте свои навыки и повышайте квалификацию с помощью [url=https://best-courses-seo.ru]seo специалист курсы[/url] и станьте профессионалами в области поисковой оптимизации!
предоставить знания о том, как повышать рейтинг сайта в результатах поиска. Эти курсы обычно включают в себя практические занятия по оптимизации сайтов, с учетом всех последних тенденций . В результате прохождения таких курсов, участники смогут понять, как создавать эффективные кампании в интернете .
Участники SEO курсов могут изучить вопросы внутренней и внешней оптимизации сайтов . Это может включать в себя освоение техник поискового маркетинга и создания рекламных кампаний. После завершения курса, участники могут использовать приобретенные навыки для работы в digital-агентствах .
В рамках SEO курсов, учащиеся могут освоить искусство внутренней и внешней оптимизации сайтов, включая работу с ссылками и другими факторами. Это может включать в себя анализ случаев успешной оптимизации сайтов и изучение их стратегий . Благодаря такому подходу, учащиеся могут овладеть всеми аспектами SEO, от технической оптимизации до создания контента .
Практические занятия в SEO курсах могут предполагать участие в групповых проектах, где участники смогут применить полученные знания на практике. Это дает участникам возможность получить реальный опыт работы в SEO, который можно применить на практике . После завершения курса, участники могут использовать приобретенные знания для создания эффективныхdigital-стратегий .
Теоретические основы SEO включают в себя понимание работы поисковых алгоритмов и факторов, влияющих на рейтинг сайта . Эти знания необходимы для освоения методов анализа и улучшения позиций сайта в поисковых системах. Теоретические основы могут включать в себя изучение истории развития поисковых систем и эволюцию поисковых алгоритмов .
Изучение теоретических основ SEO может дать возможность изучить методы улучшения позиций сайта в результатах поиска . Это может включать в себя изучение роли ключевых слов в поисковой оптимизации и методов их выбора . Благодаря такому подходу, участники могут развить навыки, необходимые для того, чтобы стать профессионалом в области поисковой оптимизации.
SEO курсы могут предоставить знания о том, как создавать эффективные кампании в интернете. Это может включать в себя участие в практических занятиях, где участники смогут применить полученные знания на практике . Участники могут приобрести практический опыт в оптимизации сайтов, включая работу с ключевыми словами и метатегами .
Применение SEO в реальной практике может быть направлено на изучение инструментов анализа сайтов и их оптимизации . Это дает участникам возможность развить свои навыки дальше, изучая более специализированные темы в области SEO и digital маркетинга. После завершения курса, участники могут применять полученные знания и навыки для оптимизации своих собственных сайтов или для работы в качестве SEO-специалистов .
Улучшайте свои навыки и повышайте квалификацию с помощью [url=https://best-courses-seo.ru]продвижение сайта обучение[/url] и станьте профессионалами в области поисковой оптимизации!
дать возможность изучить методы улучшения видимости сайта в поисковых системах . Эти курсы обычно включают в себя теоретические основы SEO, включая понимание работы поисковых алгоритмов . В результате прохождения таких курсов, участники смогут получить практические навыки поисковой оптимизации и продвижения сайтов .
Участники SEO курсов могут ознакомиться с инструментами анализа сайтов и их оптимизации. Это может включать в себя изучение методов создания ссылок и их влияния на рейтинг сайта . После завершения курса, участники могут применять полученные знания на практике, оптимизируя свои собственные сайты .
В рамках SEO курсов, учащиеся могут освоить искусство внутренней и внешней оптимизации сайтов, включая работу с ссылками и другими факторами. Это может включать в себя работу над индивидуальными проектами, направленными на оптимизацию реальных сайтов. Благодаря такому подходу, учащиеся могут понять, как измерять эффективность SEO кампаний и корректировать их .
Практические занятия в SEO курсах могут быть направлены на изучение инструментов анализа сайтов и их оптимизации . Это дает участникам возможность освоить навыки, необходимые для успешной карьеры в digital-агентствах . После завершения курса, участники могут развивать свои навыки дальше, изучая новые тенденции и технологии в области SEO.
Теоретические основы SEO включают в себя понимание работы поисковых алгоритмов и факторов, влияющих на рейтинг сайта . Эти знания необходимы для получения практических навыков поисковой оптимизации и продвижения сайтов . Теоретические основы могут включать в себя изучение истории развития поисковых систем и эволюцию поисковых алгоритмов .
Изучение теоретических основ SEO может дать возможность изучить методы улучшения позиций сайта в результатах поиска . Это может включать в себя освоение методов анализа и улучшения позиций сайта в поисковых системах. Благодаря такому подходу, участники могут овладеть всеми аспектами SEO, от технической оптимизации до создания контента .
SEO курсы могут дать возможность участникам применить полученные знания на практике, оптимизируя свои собственные сайты . Это может включать в себя работу над индивидуальными проектами, направленными на оптимизацию реальных сайтов. Участники могут изучить, как создавать и продвигать качественный контент, который будет привлекать целевую аудиторию .
Применение SEO в реальной практике может предполагать участие в групповых проектах, где участники смогут применить полученные знания на практике. Это дает участникам возможность освоить навыки, необходимые для успешной карьеры в digital-агентствах . После завершения курса, участники могут развивать свои навыки дальше, изучая новые тенденции и технологии в области SEO.
Планируя [url=https://pereezd-kvartiry-msk.ru/]квартирный переезд недорого с грузчиками[/url], вы можете значительно упростить этот процесс, воспользовавшись услугами профессионалов.
Однако, если подойти к этому с умом, можно сделать переезд менее стрессовым
Наше [url=https://dp-promotion.ru/]маркетинговое агентство сайт[/url] предлагает индивидуальные решения для роста вашего бизнеса.
Проведите анализ цен и предложений различных компаний, чтобы найти лучшее предложение.
Компания «СтройМастер» предлагает услуги по [url=https://construct-msk.ru/remont_ofisov]ремонт в офисе[/url] любой сложности и площади.
Ремонт офиса является важным шагом в создании комфортной и эффективной рабочей среды . Ремонт офиса может быть сложным процессом, включающим различные этапы, от планирования до отделочных работ. Это требует глубокого понимания потребностей компании и ее сотрудников .
Все эти элементы должны быть тщательно подобраны, чтобы создать гармоничное и эффективное рабочее пространство . При этом важно не забыть о таких моментах, как освещение, вентиляция и безопасность. Все эти аспекты должны быть тщательно спланированы и реализованы .
Планирование ремонта офиса является первым и одним из самых важных шагов . Планирование должно включать анализ текущего состояния офиса, определение потребностей сотрудников и выбор дизайна. Создание четкого плана giup предотвратить лишние затраты и сроки.
Все эти детали должны быть тщательно спланированы и включены в проект ремонта . При этом важно работать с профессиональными дизайнерами и подрядчиками, чтобы обеспечить высокое качество работ. Ремонт офиса должен быть выполнен с учетом всех современных требований и технологий .
На этом этапе определяется стиль и атмосфера будущего офиса . Дизайн должен соответствовать современным тенденциям и быть функциональным. Это включает выбор цветовой гаммы, мебели и декоративных элементов .
Необходимо также учитывать такие факторы, как экологичность и энергосбережение . При этом важно работать с профессиональными дизайнерами, которые могут предложить инновационные и эффективные решения. Создание нового офисного пространства требует творческого подхода и внимания к деталям.
Все элементы ремонта должны быть тщательно проверены и отtested. Завершение ремонта включает контроль качества работ, тестирование систем и уборку помещения. Ремонт офиса должен быть направлен на создание комфортной и безопасной рабочей среды.
Все эти детали должны быть тщательно спланированы и включены в проект ремонта . При этом важно работать с профессиональными подрядчиками, которые могут обеспечить высокое качество работ и гарантийное обслуживание. Все этапы ремонта должны быть тщательно спланированы и контролированы .
Наше [url=https://dp-promotion.ru/]агентства маркетинга[/url] предлагает индивидуальные решения для роста вашего бизнеса.
Репутация агентства играет ключевую роль в выборе подходящего партнера.
Компания «СтройМастер» предлагает услуги по [url=https://construct-msk.ru/remont_ofisov]офисный ремонт[/url] любой сложности и площади.
Создание нового офисного пространства начинается с ремонта. Ремонт офиса может быть сложным процессом, включающим различные этапы, от планирования до отделочных работ. Ремонт офиса должен соответствовать современным требованиям и быть функциональным .
Ремонт офиса должен быть направлен на повышение производительности и удовлетворенности сотрудников. При этом важно не забыть о таких моментах, как освещение, вентиляция и безопасность. Все эти аспекты должны быть тщательно спланированы и реализованы .
Планирование ремонта офиса является первым и одним из самых важных шагов . Планирование должно включать анализ текущего состояния офиса, определение потребностей сотрудников и выбор дизайна. Это giup evitar ошибок и обеспечить, что ремонт будет выполнен в соответствии с ожиданиями .
Необходимо также учитывать такие факторы, как звукоизоляция, электрические сети и интернет-соединение . При этом важно работать с профессиональными дизайнерами и подрядчиками, чтобы обеспечить высокое качество работ. Создание нового офисного пространства требует творческого подхода и внимания к деталям.
Все материалы и элементы дизайна должны быть тщательно подобраны. Дизайн должен соответствовать современным тенденциям и быть функциональным. Все эти детали должны быть тщательно спланированы и включены в проект ремонта .
Ремонт офиса должен быть направлен на создание устойчивой и комфортной рабочей среды. При этом важно работать с профессиональными дизайнерами, которые могут предложить инновационные и эффективные решения. Все этапы ремонта должны быть тщательно спланированы и контролированы .
Завершение ремонта офиса является последним этапом этого процесса . Завершение ремонта включает контроль качества работ, тестирование систем и уборку помещения. Ремонт офиса должен быть направлен на создание комфортной и безопасной рабочей среды.
Все эти детали должны быть тщательно спланированы и включены в проект ремонта . При этом важно работать с профессиональными подрядчиками, которые могут обеспечить высокое качество работ и гарантийное обслуживание. Ремонт офиса должен быть выполнен с учетом всех современных требований и технологий .
Услуги [url=https://evrasin.ru/]технический перевод онлайн[/url] предоставляются высококвалифицированными переводчиками.
процесс перевода технической документации, требующий специальных знаний и навыков . Это ключевым фактором успеха в глобализации бизнеса и научного сотрудничества . Благодаря техническому переводу можно обмениваться знаниями и опытом на международном уровне .
Технический перевод включает в себя перевод документации, инструкций и другой технической информации . Переводчики должны обладать глубокими знаниями в той или иной технической области . Это позволяет обеспечить максимальную эффективность коммуникации .
Процесс технического перевода требует тщательного планирования и выполнения . На первом этапе оцениваются ресурсы, необходимые для выполнения задачи . Далее разрабатывается план реализации проекта .
Выполнение самого перевода включает в себя несколько итераций проверки и редактирования . После завершения перевода выполняется проверка соответствия переведенного текста оригиналу . Этот позволяет минимизировать ошибки и несоответствия .
Технический перевод является важнейшим инструментом для глобализации бизнеса и культуры . Благодаря техническому переводу можно обеспечить доступ к передовым технологиям и инновациям . Это способствует развитию экономики и улучшению качества жизни .
Технический перевод также помогает в понимании и решении глобальных проблем . Это дает возможность людям из разных стран общаться и делиться опытом . Поэтому следует привлекать высококвалифицированных специалистов в этой области .
Будущее технического перевода предполагает интеграцию с другими областями, такими как локализация и культурная адаптация . Развитие машинного перевода и искусственного интеллекта поможет в обработке больших объемов информации .
В будущем технический перевод станет еще более важным для глобальных?? и международного сотрудничества . Это будет способствовать развитию новых форматов и технологий для перевода и коммуникации . Поэтому необходимо постоянно развивать новые навыки и знания .
Для решения всех задач, связанных с переводом документов на любой язык, можно обратиться в [url=https://allperevod.ru/]перевод документов[/url], где опытные переводчики окажут профессиональные услуги по переводу любых документов.
предоставление лингвистической поддержки для бизнеса и частных лиц. Это позволяет им удовлетворять различные потребности клиентов, от перевода личных документов до комплексных бизнес-проектов. Кроме того, бюро переводов часто обладает d?iной переводчиков, которые являются экспертами в разных областях, понимающими нюансы языка и культурные особенности . Это гарантирует, что переведенный текст не только соответствует оригиналу по смыслу, но и адаптирован к целевой аудитории и соответствует требованиям определенной отрасли.
Бюро переводов также уделяет особое внимание конфиденциальности и безопасности переводимой информации, поскольку это может включать защиту данных с помощью современных технологий . Это является ключевым аспектом их услуг, поскольку клиенты часто доверяют им?ливую информацию. Помимо этого, бюро переводов может предложить услуги по локализации, учитывая культурные и языковые особенности . Это особенно ценно для компаний, стремящихся расширить свою деятельность на новые рынки.
Работа с бюро переводов дает клиентам доступ к команде опытных и квалифицированных переводчиков . Это означает, что клиенты могут получить переводы, соответствующие их потребностям, будь то срочный перевод небольшого документа или масштабный проект, требующий перевода большого объема текстов. Кроме того, многие бюро переводов используют специализированное программное обеспечение для обеспечения качества переводов. Это не только ускоряет процесс перевода, но и гарантирует, что окончательный продукт соответствует самым высоким стандартам.
Партнерство с бюро переводов также может быть стратегическим шагом для бизнеса, расширяющегося на новые рынки . Благодаря точным и культурно адаптированным переводам, бизнес может эффективно передавать свое послание целевой аудитории . Это делает бюро переводов не просто поставщиком услуг, а ценным партнером в достижении бизнес-целей.
Бюро переводов обычно работает гарантируя, что все переводы соответствуют самым высоким стандартам. Для начала работы клиент заказывает услугу перевода, предоставляя необходимую информацию о проекте . После этого, бюро переводов обеспечивает постоянную связь с клиентом на всех этапах проекта. Этот подход??ет, что перевод не только выполнен качественно, но и соответствует конкретным потребностям и ожиданиям клиента.
На протяжении всего процесса бюро переводов также обеспечивает, что окончательный продукт соответствует ожиданиям клиента. Это может включать проверку перевода на наличие ошибок и несоответствий . Такой подход к?? и удовлетворенности клиента позволяет бюро переводов поддерживать высокий уровеньprofessionalизма и строить долгосрочные отношения с клиентами.
В заключение, бюро переводов представляет собой команду профессионалов, готовых удовлетворять различные потребности клиентов . С их помощью клиенты могут получить высококачественные переводы, соответствующие их потребностям . Бюро переводов является не просто поставщиком услуг, а стратегическим партнером, который может помочь построить сильный и признанный бренд. Сегодня, когдамир становится все более взаимосвязанным, роль бюро переводов будет только расти в важности .
Для решения всех задач, связанных с переводом документов на любой язык, можно обратиться в [url=https://allperevod.ru/]письменный перевод на английский[/url], где опытные переводчики окажут профессиональные услуги по переводу любых документов.
предоставление лингвистической поддержки для бизнеса и частных лиц. Это позволяет им удовлетворять различные потребности клиентов, от перевода личных документов до комплексных бизнес-проектов. Кроме того, бюро переводов часто обладает d?iной переводчиков, которые являются экспертами в разных областях, таких как юридический, медицинский и технический перевод . Это гарантирует, что переведенный текст не только соответствует оригиналу по смыслу, но и адаптирован к целевой аудитории и соответствует требованиям определенной отрасли.
Бюро переводов также уделяет особое внимание конфиденциальности и безопасности переводимой информации, обеспечивая, что все переводчики обязаны сохранять конфиденциальность. Это является ключевым аспектом их услуг, поскольку клиенты часто доверяют им?ливую информацию. Помимо этого, бюро переводов может предложить услуги по локализации, позволяя бизнесу более эффективно взаимодействовать с целевой аудиторией. Это особенно ценно для компаний, стремящихся расширить свою деятельность на новые рынки.
Работа с бюро переводов дает клиентам возможность получить высококачественные переводы в короткие сроки . Это означает, что клиенты могут получить переводы, соответствующие их потребностям, будь то срочный перевод небольшого документа или масштабный проект, требующий перевода большого объема текстов. Кроме того, многие бюро переводов используют современные технологии для управления процессом перевода . Это не только ускоряет процесс перевода, но и гарантирует, что окончательный продукт соответствует самым высоким стандартам.
Партнерство с бюро переводов также может быть стратегическим шагом для бизнеса, расширяющегося на новые рынки . Благодаря точным и культурно адаптированным переводам, бизнес может укреплять доверие и авторитет среди своих международных партнеров и клиентов. Это делает бюро переводов не просто поставщиком услуг, а ценным партнером в достижении бизнес-целей.
Бюро переводов обычно работает используя комбинацию человеческого опыта и технологий для обеспечения точности . Для начала работы клиент заказывает услугу перевода, предоставляя необходимую информацию о проекте . После этого, бюро переводов назначает подходящего переводчика для проекта, учитывая его специализацию и опыт . Этот подход??ет, что перевод не только выполнен качественно, но и соответствует конкретным потребностям и ожиданиям клиента.
На протяжении всего процесса бюро переводов также проводит необходимые корректировки и редактирование . Это может включать проведение экспертной оценки . Такой подход к?? и удовлетворенности клиента позволяет бюро переводов поддерживать высокий уровеньprofessionalизма и строить долгосрочные отношения с клиентами.
В заключение, бюро переводов представляет собой комплексную службу, которая предлагает широкий спектр лингвистических услуг . С их помощью клиенты могут получить возможность расширить свои горизонты и построить отношения на международном уровне. Бюро переводов является не просто поставщиком услуг, а стратегическим партнером, который может помочь расширить бизнес на новые рынки . Сегодня, когдамир становится все более взаимосвязанным, роль бюро переводов будет только расти в важности .
[url=http://semennoydom.ru]промокод семяныч[/url] поможет вам сэкономить на покупках в компании!
Ассортимент товаров в Семяныче достаточно широк, и скидки распространяются на многие позиции.
Компания предлагает услуги [url=https://arenda-avtomobilya-s-voditelem01.ru/]авто с водителем новосибирск[/url] для путешественников и местных жителей.
В Новосибирске аренда авто с водителем является одним из наиболее комфортных способов передвижения по городу. Это связано с тем, что в городе есть множество компаний, предлагающих такие услуги. Аренда авто с водителем позволяет гостям Новосибирска наслаждаться городом без забот о передвижении. Это особенно удобно для иностранных туристов, которые могут не владеть русским языком. Услуги аренды автомобилей с водителем в Новосибирске представлены различными компаниями, которые предлагают широкий выбор автомобилей. Для этого необходимо указать дату, время и место подачи автомобиля. Водители, предоставляемые компаниями аренды авто, являются опытными и вежливыми. Это позволяет добраться до места назначения быстро и безопасно.
Это позволяет гостям Новосибирска сосредоточиться на более важных делах. Это особенно удобно для деловых путешественников, которые часто имеют плотный график. В Новосибирске можно арендовать автомобиль с водителем для поездки на знаменитые достопримечательности. Это дает возможность оценить красоту города и его окрестностей.
Это особенно удобно для семей с детьми, которые могут не иметь возможности передвигаться на общественном транспорте. Это позволяет добраться до места назначения быстро и комфортно. В Новосибирске можно арендовать автомобиль с водителем для поездки на деловую встречу или на свадьбу. Для этого необходимо указать дату, время и место подачи автомобиля.
Услуги аренды авто с водителем в Новосибирске представлены различными компаниями, которые предлагают широкий выбор автомобилей. Это дает возможность оценить красоту города и его окрестностей. Услуги аренды авто с водителем в Новосибирске становятся все более доступными и популярными среди путешественников.
Чтобы арендовать авто с водителем в Новосибирске, необходимо обратиться в одну из компаний, предоставляющих такие услуги. Для этого необходимо указать дату, время и место подачи автомобиля. После оформления заказа автомобиль с водителем будет подан в указанное место в назначенное время. Это позволяет добраться до места назначения быстро и безопасно.
Услуги аренды авто с водителем в Новосибирске доступны для всех категорий граждан. Это дает возможность оценить красоту города и его окрестностей. Услуги аренды авто с водителем в Новосибирске становятся все более доступными и популярными среди путешественников. Это позволяет гостям Новосибирска наслаждаться городом без забот о передвижении.
Услуги аренды авто с водителем в Новосибирске доступны для всех желающих, независимо от их бюджета. Для этого необходимо указать дату, время и место подачи автомобиля. Водители, предоставляемые компаниями аренды авто, являются опытными и знающими город. Это дает возможность оценить красоту города и его окрестностей.
Услуги аренды авто с водителем в Новосибирске представлены различными компаниями, которые предлагают широкий выбор автомобилей. Это дает возможность оценить красоту города и его окрестностей. Аренда авто с водителем в Новосибирске предлагает широкий спектр услуг для тех, кто ценит комфорт и удобство. Это позволяет гостям Новосибирска наслаждаться городом без забот о передвижении.
В Новосибирске можно арендовать автомобиль с водителем для поездки на знаменитые достопримечательности. Это дает возможность оценить красоту города и его окрестностей. Аренда авто с водителем в Новосибирске позволяет экономить средства, поскольку не нужно тратить деньги на бензин, парковку и другие расходы. Это позволяет добраться до места назначения быстро и безопасно.
Для тех, кто ищет качественное [url=https://www.sozdanie-sajtov-31.ru/]перевод на латинский медицинский переводчик[/url], наши услуги станут лучшим выбором.
Перевод медицинских текстов требует высокой точности и качества . Бюро медицинских переводов занимается переводом различных медицинских документов, включая истории болезни, медицинские статьи и инструкции к лекарствам. Бюро медицинских переводов работает с высококвалифицированными переводчиками .
Бюро медицинских переводов также занимается локализацией медицинского программного обеспечения и веб-сайтов, что включает в себя адаптацию интерфейса и содержания для разных языков и культур. Локализация медицинского программного обеспечения требует глубокого понимания медицинской терминологии .
Бюро медицинских переводов предлагает различные виды медицинских переводов, включая перевод медицинских статей и публикаций . Перевод медицинских статей и публикаций требует высокого уровня экспертизы в области медицины и знания медицинской терминологии. Перевод медицинских статей и публикаций обеспечивает доступ к медицинским знаниям для более широкой аудитории.
Бюро медицинских переводов также занимается переводом медицинских документов, таких как истории болезни и медицинские справки. Перевод медицинских документов требует высокой точности и качества .
Бюро медицинских переводов предоставляет многочисленные преимущества для медицинских учреждений и пациентов, включая доступ к медицинской информации на разных языках . Бюро медицинских переводов также обеспечивает конфиденциальность и безопасность медицинских документов, что является важным аспектом в сфере здравоохранения. Бюро медицинских переводов имеет большой опыт работы с конфиденциальными медицинскими документами .
Бюро медицинских переводов также может помочь медицинским учреждениям и пациентам сэкономить время и ресурсы, предоставляя быстрые и качественные медицинские переводы. Бюро медицинских переводов имеет большой опыт работы с медицинскими учреждениями и пациентами.
В заключении, бюро медицинских переводов является важным звеном в сфере здравоохранения, где перевод медицинских текстов требует высокой точности и качества . Бюро медицинских переводов предлагает различные виды медицинских переводов, включая перевод медицинских статей, историй болезни и инструкций к лекарствам. Бюро медицинских переводов работает с высококвалифицированными переводчиками .
Бюро медицинских переводов также обеспечивает конфиденциальность и безопасность медицинских документов, что является важным аспектом в сфере здравоохранения. Бюро медицинских переводов имеет большой опыт работы с конфиденциальными медицинскими документами .
Компания предлагает услуги [url=https://arenda-avtomobilya-s-voditelem01.ru/]автомобиль с водителем новосибирск[/url] для путешественников и местных жителей.
Аренда авто с водителем в Новосибирске предлагает широкий спектр услуг для тех, кто ценит комфорт и удобство. Это связано с тем, что в городе есть множество компаний, предлагающих такие услуги. Услуги аренды автомобилей с водителем в Новосибирске включают в себя сопровождение на деловые встречи и экскурсии по городу. Это особенно удобно для иностранных туристов, которые могут не владеть русским языком. Услуги аренды авто с водителем в Новосибирске доступны для всех желающих, независимо от их бюджета. Для этого необходимо указать дату, время и место подачи автомобиля. Водители, предоставляемые компаниями аренды авто, являются опытными и вежливыми. Это позволяет добраться до места назначения быстро и безопасно.
Это позволяет гостям Новосибирска сосредоточиться на более важных делах. Это особенно удобно для деловых путешественников, которые часто имеют плотный график. Услуги аренды авто с водителем в Новосибирске также включают в себя помощь в решении любых вопросов, связанных с пребыванием в городе. Это дает возможность оценить красоту города и его окрестностей.
Услуги аренды авто с водителем в Новосибирске доступны для всех категорий граждан. Это позволяет добраться до места назначения быстро и комфортно. Аренда авто с водителем в Новосибирске может быть оформлена на любой период времени. Для этого необходимо указать дату, время и место подачи автомобиля.
Услуги аренды авто с водителем в Новосибирске представлены различными компаниями, которые предлагают широкий выбор автомобилей. Это дает возможность оценить красоту города и его окрестностей. Водители, предоставляемые компаниями аренды авто, являются опытными и вежливыми.
Аренда авто с водителем может быть оформлена онлайн или по телефону. Для этого необходимо указать дату, время и место подачи автомобиля. Водители, предоставляемые компаниями аренды авто, являются опытными и знающими город. Это позволяет добраться до места назначения быстро и безопасно.
В Новосибирске можно арендовать автомобиль с водителем для поездки на знаменитые достопримечательности. Это дает возможность оценить красоту города и его окрестностей. Аренда авто с водителем в Новосибирске предлагает широкий спектр услуг для тех, кто ценит комфорт и удобство. Это позволяет гостям Новосибирска наслаждаться городом без забот о передвижении.
Аренда автомобиля с водителем может быть арендована на любой период времени. Для этого необходимо указать дату, время и место подачи автомобиля. Водители, предоставляемые компаниями аренды авто, являются опытными и знающими город. Это дает возможность оценить красоту города и его окрестностей.
Услуги аренды авто с водителем в Новосибирске представлены различными компаниями, которые предлагают широкий выбор автомобилей. Это дает возможность оценить красоту города и его окрестностей. Водители, предоставляемые компаниями аренды авто, являются опытными и вежливыми. Это позволяет гостям Новосибирска наслаждаться городом без забот о передвижении.
Аренда автомобиля с водителем может быть арендована на любой период времени, от нескольких часов до нескольких дней. Это дает возможность оценить красоту города и его окрестностей. Аренда авто с водителем в Новосибирске позволяет экономить средства, поскольку не нужно тратить деньги на бензин, парковку и другие расходы. Это позволяет добраться до места назначения быстро и безопасно.
Для тех, кто ищет качественное [url=https://www.sozdanie-sajtov-31.ru/]перевод медицинской карты[/url], наши услуги станут лучшим выбором.
Медицинские переводы играют ключевую роль в обеспечении коммуникации между медицинскими специалистами и пациентами . Бюро медицинских переводов занимается переводом различных медицинских документов, включая истории болезни, медицинские статьи и инструкции к лекарствам. Бюро медицинских переводов использует передовые технологии для обеспечения точности переводов .
Бюро медицинских переводов также занимается локализацией медицинского программного обеспечения и веб-сайтов, что включает в себя адаптацию интерфейса и содержания для разных языков и культур. Локализация медицинского программного обеспечения требует глубокого понимания медицинской терминологии .
Бюро медицинских переводов предлагает различные виды медицинских переводов, включая перевод историй болезни и медицинских документов . Перевод медицинских статей и публикаций требует высокого уровня экспертизы в области медицины и знания медицинской терминологии. Перевод медицинских публикаций требует глубокого понимания медицинских исследований .
Бюро медицинских переводов также занимается переводом медицинских документов, таких как истории болезни и медицинские справки. Перевод медицинских справок включает в себя перевод медицинской терминологии .
Бюро медицинских переводов предоставляет многочисленные преимущества для медицинских учреждений и пациентов, включая возможность коммуникации между медицинскими специалистами и пациентами . Бюро медицинских переводов также обеспечивает конфиденциальность и безопасность медицинских документов, что является важным аспектом в сфере здравоохранения. Бюро медицинских переводов использует передовые технологии для обеспечения конфиденциальности .
Бюро медицинских переводов также может помочь медицинским учреждениям и пациентам сэкономить время и ресурсы, предоставляя быстрые и качественные медицинские переводы. Бюро медицинских переводов имеет большой опыт работы с медицинскими учреждениями и пациентами.
В заключении, бюро медицинских переводов является важным звеном в сфере здравоохранения, где медицинские переводы играют ключевую роль в обеспечении коммуникации между медицинскими специалистами и пациентами . Бюро медицинских переводов предлагает различные виды медицинских переводов, включая перевод медицинских статей, историй болезни и инструкций к лекарствам. Бюро медицинских переводов работает с высококвалифицированными переводчиками .
Бюро медицинских переводов также обеспечивает конфиденциальность и безопасность медицинских документов, что является важным аспектом в сфере здравоохранения. Бюро медицинских переводов имеет большой опыт работы с конфиденциальными медицинскими документами .
Получить [url=https://www.airinc.ru/]апостиль диплома[/url] — это важный шаг для подтверждения подлинности вашего образования за границей.
С помощью апостиля ваш диплом может быть признан в странах, подписавших Гаагскую конвенцию.
[url=https://dveri-premium-klassa.ru/]Металлические двери премиум класса[/url] обеспечивают надежную защиту и элегантный стиль вашего дома.
Металлические двери премиум класса — это не только защитный элемент, но и важная деталь интерьера.
Для оформления кухни в уникальном стиле можно [url=https://moiki-iz-iskusstvennogo-kamnya.ru/]мойка из камня[/url], что придаст интерьеру неповторимый шарм и практичность.
Раковина для кухни должна быть не только функциональной, но и эстетически привлекательной . Кроме того, необходимо учитывать количество пользователей и общий дизайн кухонного пространства Для большой семьи может потребоваться раковина большего размера, чтобы обеспечить tho?i maiное использование . При покупке раковины также рекомендуется прочитать отзывы и сравнить цены в разных магазинах Это поможет вам найти лучшее соотношение цены и качества .
Кроме того, при выборе раковины для кухни необходимо учитывать ее размер и форму Правильный размер и форма раковины могут сделать ее более функциональной и удобной. Материал, из которого изготовлена раковина, также играет важную роль Керамика может добавить кухне больше стиля и элегантности. Установка раковины может быть простой или сложной, в зависимости от типа раковины и вашего уровня опыта Для некоторых типов раковин может потребоваться помощь профессионала .
Существует множество типов раковин для кухни, каждый из которых имеет свои собственные характеристики и преимущества Нержавеющая сталь является популярным выбором благодаря своей прочности и легкости в уходе . Нержавеющая сталь является одним из наиболее популярных материалов для раковин Она не только прочная и устойчивая к царапинам, но и легкая в уходе . Гранитовые раковины предлагают высокую устойчивость к нагреву и царапинам Гранитовые раковины требуют регулярного ухода, чтобы сохранить их внешний вид .
Кроме того, существуют раковины из искусственного камня, которые предлагают высокую прочность и элегантность Они могут быть изготовлены из различных материалов, включая кварц и акрил . Раковина из керамики может добавить кухне больше стиля и изысканности Она известна своей высокой устойчивостью к нагреву и царапинам, а также легкостью в уходе . Выбор правильного типа раковины для кухни может быть сложным, но учитывая ваши потребности и предпочтения, вы можете найти идеальный вариант Также стоит учитывать стиль и дизайн кухни .
Установка раковины для кухни может быть простой или сложной, в зависимости от типа раковины и вашего уровня опыта Некоторые раковины устанавливаются над столешницей, в то время как другие требуют монтажа врезного типа . Для начала необходимо измерить пространство, где будет установлена раковина Правильные измерения гарантируют, что раковина будет установлена правильно и не будет никаких проблем. После установки раковины необходимо провести Regularный уход, чтобы сохранить ее внешний вид и функциональность Это поможет вам обнаружить и устранить любые проблемы на ранней стадии.
Кроме того, стоит учитывать стиль и дизайн кухни при выборе раковины Также стоит учитывать стиль кухонных приборов и мебели . При установке раковины также необходимо учитывать сантехнику и электрические соединения Также стоит учитывать наличие необходимых инструментов и материалов . Выбор правильной раковины для кухни может сделать ее более функциональной и красивой Это может включать рассмотрение размера, формы и материала раковины .
При выборе раковины для кухни стоит учитывать множество факторов, включая размер, материал и стиль Правильный выбор раковины для кухни может превратить ее в настоящий шедевр. Также важно учитывать индивидуальные потребности и предпочтения Маленькая раковина может быть идеальной для небольшой кухни, но она должна быть достаточно функциональной . При покупке раковины также рекомендуется прочитать отзывы и сравнить цены в разных магазинах Сравнение цен позволит вам сэкономить деньги и выбрать лучший вариант.
Кроме того, стоит учитывать стиль и дизайн кухни при выборе раковины Правильный выбор раковины может сделать кухню более гармоничной и красивой. Выбор правильной раковины для кухни может быть сложным, но учитывая ваши потребности и предпочтения, вы можете найти идеальный вариант Это может включать рассмотрение размера, формы и материала раковины . При установке раковины также необходимо учитывать сантехнику и электрические соединения Это может включать подключение раковины к водопроводной и канализационной системе .
Чтобы обеспечить легализацию вашего образования за границей, важно знать, где и как поставить [url=https://globaltradecom.ru/]нужен ли апостиль на диплом[/url].
Учтите, что процесс получения апостиля может занять время, поэтому лучше подготовиться заранее.
[url=https://dveri-premium-klassa.ru/]Металлические двери премиум класса[/url] обеспечивают надежную защиту и элегантный стиль вашего дома.
Металлические двери высшего класса обеспечивают отличную тепло- и звукоизоляцию.
Чтобы обеспечить легализацию вашего образования за границей, важно знать, где и как поставить [url=https://globaltradecom.ru/]апостиль диплома в москве[/url].
Это может занять некоторое время, поэтому необходимо заранее планировать свои действия.
Для оформления кухни в уникальном стиле можно [url=https://moiki-iz-iskusstvennogo-kamnya.ru/]купить каменную мойку для кухни в москве[/url], что придаст интерьеру неповторимый шарм и практичность.
Правильный выбор раковины для кухни может превратить ее в настоящий шедевр. Кроме того, необходимо учитывать количество пользователей и общий дизайн кухонного пространства Для большой семьи может потребоваться раковина большего размера, чтобы обеспечить tho?i maiное использование . При покупке раковины также рекомендуется прочитать отзывы и сравнить цены в разных магазинах Отзывы других покупателей могут дать ценные советы и рекомендации .
Кроме того, при выборе раковины для кухни необходимо учитывать ее размер и форму Это может включать стандартные размеры, такие как 60 см или 80 см, или более экзотические варианты . Материал, из которого изготовлена раковина, также играет важную роль Нержавеющая сталь известна своей прочностью и легкостью в уходе . Установка раковины может быть простой или сложной, в зависимости от типа раковины и вашего уровня опыта Для некоторых типов раковин может потребоваться помощь профессионала .
Существует множество типов раковин для кухни, каждый из которых имеет свои собственные характеристики и преимущества Гранитовые раковины известны своим элегантным внешним видом и высокой устойчивостью к царапинам . Нержавеющая сталь является одним из наиболее популярных материалов для раковин Она не только прочная и устойчивая к царапинам, но и легкая в уходе . Гранитовые раковины предлагают высокую устойчивость к нагреву и царапинам Гранитовые раковины требуют регулярного ухода, чтобы сохранить их внешний вид .
Кроме того, существуют раковины из искусственного камня, которые предлагают высокую прочность и элегантность Он идеально подходит для кухонь с современным или минималистским дизайном. Раковина из керамики может добавить кухне больше стиля и изысканности Она известна своей высокой устойчивостью к нагреву и царапинам, а также легкостью в уходе . Выбор правильного типа раковины для кухни может быть сложным, но учитывая ваши потребности и предпочтения, вы можете найти идеальный вариант Это может включать рассмотрение размера, формы и материала раковины .
Установка раковины для кухни может быть простой или сложной, в зависимости от типа раковины и вашего уровня опыта Некоторые раковины устанавливаются над столешницей, в то время как другие требуют монтажа врезного типа . Для начала необходимо измерить пространство, где будет установлена раковина Правильные измерения гарантируют, что раковина будет установлена правильно и не будет никаких проблем. После установки раковины необходимо провести Regularный уход, чтобы сохранить ее внешний вид и функциональность Регулярный уход также включает проверку раковины на наличие повреждений или царапин .
Кроме того, стоит учитывать стиль и дизайн кухни при выборе раковины Это может включать рассмотрение цвета, материала и формы раковины . При установке раковины также необходимо учитывать сантехнику и электрические соединения Это может включать подключение раковины к водопроводной и канализационной системе . Выбор правильной раковины для кухни может сделать ее более функциональной и красивой Правильный выбор раковины может сделать вашу кухню более гармоничной и привлекательной.
При выборе раковины для кухни стоит учитывать множество факторов, включая размер, материал и стиль Правильный выбор раковины для кухни может превратить ее в настоящий шедевр. Также важно учитывать индивидуальные потребности и предпочтения Маленькая раковина может быть идеальной для небольшой кухни, но она должна быть достаточно функциональной . При покупке раковины также рекомендуется прочитать отзывы и сравнить цены в разных магазинах Сравнение цен позволит вам сэкономить деньги и выбрать лучший вариант.
Кроме того, стоит учитывать стиль и дизайн кухни при выборе раковины Правильный выбор раковины может сделать кухню более гармоничной и красивой. Выбор правильной раковины для кухни может быть сложным, но учитывая ваши потребности и предпочтения, вы можете найти идеальный вариант Это может включать рассмотрение размера, формы и материала раковины . При установке раковины также необходимо учитывать сантехнику и электрические соединения Правильная установка раковины гарантирует, что она будет работать эффективно и безопасно.
Профессиональный нарколог на дому поможет вам с [url=https://alconarkoclinic.ru/vyvod-iz-zapoya-na-domu]запой на дому[/url] быстро и удобно, обеспечив комфорт и безопасность в вашем доме.
Существует несколько эффективных методов вывода из запоя в домашних условиях.
Для тех, кто ценит безопасность и эксклюзивный дизайн, [url=https://dveri-premium-klassa.ru/]двери премиум класса[/url] становятся идеальным выбором, поскольку они сочетают в себе прочность, стиль и надежность.
сочетают в себе повышенную безопасность, эстетическую привлекательность и долговечность. Эти двери производятся с использованием только высококачественных материалов и современных технологий . Металлические двери премиум класса изготавливаются с учетом индивидуальных потребностей каждого клиента .
Металлические двери премиум класса могут быть оборудованы различными системами безопасности, включая электронные замки и системы видеонаблюдения . Эти двери имеют привлекательный внешний вид и могут стать настоящим украшением любого здания. Металлические двери премиум класса представляют собой универсальное решение для различных задач .
Металлические двери премиум класса отличаются высоким уровнем безопасности и защищенности . Эти двери имеют низкий уровень шума и вибрации. Металлические двери премиум класса предназначены для обеспечения максимальной защиты от проникновения и взлома .
Металлические двери премиум класса могут быть использованы в различных типах зданий, от частных домов до офисных помещений . Эти двери могут быть оснащены дополнительными опциями, такими как звукоизоляция и термоизоляция . Металлические двери премиум класса сочетают функциональность, безопасность и эстетическую привлекательность.
Процесс установки металлических дверей премиум класса должен быть проведен квалифицированными специалистами . Эти двери должны быть проверены на прочность и долговечность. Металлические двери премиум класса должны быть очищены и обработаны специальными средствами.
Эксплуатация металлических дверей премиум класса должна быть проведена в соответствии с инструкциями производителя и требованиями безопасности . Металлические двери премиум класса должны быть изготовлены из высококачественных материалов. Эти двери представляют собой универсальное решение для различных задач .
Металлические двери премиум класса представляют собой высококачественное решение для входных групп любого типа зданий . При выборе металлических дверей премиум класса должны быть рассмотрены различные варианты и модели . Металлические двери премиум класса должны быть соответствовать всем современным стандартам качества и безопасности.
Металлические двери премиум класса сочетают функциональность, безопасность и эстетическую привлекательность . Эти двери должны быть регулярно проверены и обслужены . Металлические двери премиум класса имеют привлекательный внешний вид и могут стать настоящим украшением любого здания .
Looking for a reliable way to travel in comfort? Check out our [url=https://vector-jet.com/private-jet-charter]private jet hire uk[/url]!
Private jet charter is a luxurious option for travelers seeking efficiency. It allows individuals to bypass commercial flights. Many people prefer this mode of transportation for its exclusivity.
Arranging a private jet charter is quite easy. Customers typically choose their departure point and indicate their travel schedule. After that, a professional service will assist in finding the ideal aircraft.
There are many benefits to using private jets. One significant advantage is the possibility of accessing remote locations. This feature often minimizes overall journey duration.
Additionally, the level of privacy provided is unmatched. Passengers can hold discussions without the fear of being overheard. This makes private jet charter an perfect choice for individuals with high-profile demands.
Профессиональный нарколог на дому поможет вам с [url=https://alconarkoclinic.ru/vyvod-iz-zapoya-na-domu]вывод из запоя услуги[/url] быстро и удобно, обеспечив комфорт и безопасность в вашем доме.
Необходимость вывода из запоя следует воспринимать со всей серьезностью.
Для тех, кто ценит безопасность и эксклюзивный дизайн, [url=https://dveri-premium-klassa.ru/]премиальные входные двери[/url] становятся идеальным выбором, поскольку они сочетают в себе прочность, стиль и надежность.
представляют собой высококачественное решение для входных групп любого типа зданий . Эти двери разработаны для обеспечения максимальной защиты от взлома и проникновения . Металлические двери премиум класса изготавливаются с учетом индивидуальных потребностей каждого клиента .
Металлические двери премиум класса отличаются повышенной прочностью и долговечностью . Эти двери могут быть оснащены дополнительными опциями, такими как звукоизоляция и термоизоляция . Металлические двери премиум класса сочетают функциональность, безопасность и эстетическую привлекательность.
Металлические двери премиум класса имеют современный и стильный дизайн . Эти двери могут быть выполнены в различных цветах и стилях, что позволяет им гармонично вписаться в любой интерьер . Металлические двери премиум класса предназначены для обеспечения максимальной защиты от проникновения и взлома .
Металлические двери премиум класса имеют привлекательный внешний вид и могут стать настоящим украшением любого здания. Эти двери могут быть оснащены дополнительными опциями, такими как звукоизоляция и термоизоляция . Металлические двери премиум класса сочетают функциональность, безопасность и эстетическую привлекательность.
Процесс установки металлических дверей премиум класса включает в себя ряд обязательных этапов, таких как подготовка места установки и монтаж дверной рамы. Эти двери должны быть проверены на прочность и долговечность. Металлические двери премиум класса должны быть эксплуатируемы в соответствии с инструкциями производителя и требованиями безопасности .
Эксплуатация металлических дверей премиум класса должна быть проведена в соответствии с инструкциями производителя и требованиями безопасности . Металлические двери премиум класса должны быть оснащены всеми необходимыми документами и сертификатами . Эти двери сочетают функциональность, безопасность и эстетическую привлекательность.
Металлические двери премиум класса являются одним из наиболее популярных и востребованных видов дверей на рынке современных строительных материалов . При выборе металлических дверей премиум класса должны быть учтены все необходимые факторы, такие как качество материалов, уровень безопасности и эстетическая привлекательность . Металлические двери премиум класса должны быть оснащены всеми необходимыми системами безопасности и защиты .
Металлические двери премиум класса могут быть использованы в различных типах зданий, от частных домов до офисных помещений. Эти двери должны быть эксплуатируемы в соответствии с инструкциями производителя и требованиями безопасности . Металлические двери премиум класса имеют привлекательный внешний вид и могут стать настоящим украшением любого здания .
Looking for a reliable way to travel in comfort? Check out our [url=https://vector-jet.com/private-jet-charter]privat jet hire[/url]!
Private jet charter is a popular choice for travelers seeking speed. It allows individuals to bypass commercial flights. Many people prefer this method for its time-saving benefits.
The process of booking a private jet is quite simple. Customers typically select their destination and set their preferred travel dates. After that, a dedicated team will assist in matching clients with the best options.
Private jets offer numerous advantages. One significant advantage is the possibility of accessing remote locations. This feature often allows for quicker arrivals.
The privacy afforded by these flights is exceptional. Passengers can hold discussions without worrying about security breaches. This makes private jet charter an perfect choice for business travelers.
Вывоз грунта с участка является необходимой услугой для строительных и ландшафтных работ . Это позволяет быстро и качественно выполнить работу . При этом важно учитывать объемы вывозимого грунта и выбирать подходящий транспорт .
Выявление объема работ и выбор подходящей техники являются первыми шагами . Особое внимание уделяется качеству выполнения, чтобы соответствовать необходимым стандартам. Для этого работают в соответствии с установленными нормами и правилами.
Этот этап является крайне важным, поскольку от него зависит эффективность всего процесса . Важно учитывать тип грунта и условия на участке . Для этого используют современные технологии и программное обеспечение для точных расчетов .
Подготовка территории также включает в себя очистку от мусора . При этом составляется схема движения машин и персонала.
Современные технологии и оборудование играют ключевую роль в процессе вывозки грунта . Это оборудование включает в себя экскаваторы, погрузчики и самосвалы . Для вывозки разрабатываются индивидуальные решения для каждого проекта.
Он зависит от характеристик участка и объема работ . Поэтому проводится тщательный подбор техники .
Окончательные этапы вывозки грунта включают в себя проверку качества выполненных работ и очистку территории . В этот период составляется акт о завершении работ. Если необходимо выполнить дополнительные работы для соответствия требованиям .
Это делается для обеспечения безопасности и долговечности объекта . В процессе привлекаются опытные инспекторы для оценки качества работ .
вывоз грунта 24 [url=https://вывоз грунта с участка/]вывоз грунта 24[/url].
При работе с медицинскими документами очень важно иметь качественный [url=https://medicinskiy-perevod.ru/]медицинский перевод москва[/url], чтобы гарантировать точность и соответствие международным стандартам.
особую область перевода, требующую высокой точности и специальных знаний . Это необходимо для того, чтобы передать медицинские данные в наиболее понятной и доступной форме. В медицинском переводе команда переводчиков и редакторов сотрудничает для достижения высочайшего качества.
Медицинский перевод включает в себя перевод различных медицинских документов, включая истории болезни и рецепты . Всё это требует глубокого понимания медицинской терминологии и современных методов лечения . Для того, чтобы выполнить требования заказчиков , медицинские переводчики работают в тесном сотрудничестве с медицинскими специалистами .
Медицинский перевод можно разделить на различные категории, каждая из которых требует специальных навыков и знаний . Это включает в себя локализацию медицинского программного обеспечения и веб-сайтов. При выполнении таких задач уметь работать с различными форматами и программным обеспечением .
Перевод медицинских документов является крайне важным , поскольку он требует высокой точности иattention к деталям. Другой важный аспект — создание учебных материалов для медицинских учебных заведений. Это требует глубокого понимания культурных особенностей и нюансов.
Точность в медицинском переводе имеет решающее значение для обеспечения качества медицинской помощи . Медицинские переводчики должны работать с высокой концентрацией внимания . Переводчики должны быть в курсе последних медицинских достижений .
Малейшая ошибка в переводе может привести к серьезным последствиям . Для того, чтобы обеспечить высочайшее качество услуг, медицинские переводчики работают в тесном сотрудничестве с медицинскими специалистами . Это включает в себя использование глоссариев и баз данных .
Использование технологий в медицинском переводе позволяет оптимизировать затраты и повысить качество . Это включает в себя использованиепрограммного обеспечения для автоматизированного перевода . Однако, технологии не могут полностью заменить человеческий интеллект и опыт .
Технологии дают возможность автоматизировать рутинные задачи . Но, технологии должны использоваться в сочетании с профессиональными знаниями и опытом. Для того, чтобы максимально использовать потенциал технологий , медицинские переводчики должны уметь работать с различными программными инструментами и платформами .
Компания предлагает широкий выбор [url=https://dveri-premium-klassa.ru/]двери входные премиум[/url], изготовленные с учетом индивидуальных пожеланий каждого клиента и соответствующие высоким стандартам качества и безопасности.
являются символом роскоши и статуса . Они проектируются с учетом всех необходимых стандартов. Металлические двери премиум класса являются идеальным решением для тех, кто ищет надежную защиту от внешних факторов.
Металлические двери премиум класса имеют широкий спектр оттенков и дизайнов . Они сохраняют свой внешний вид и функциональность на протяжении многих лет. Металлические двери премиум класса повышают стоимость недвижимости .
Металлические двери премиум класса имеют усиленные элементы безопасности . Они производятся с использованием высококачественных материалов . Металлические двери премиум класса требуют минимального технического обслуживания .
Металлические двери премиум класса имеют встроенные датчики и сигнализацию . Они имеют возможность дистанционного управления . Металлические двери премиум класса обеспечивают дополнительный уровень безопасности и комфорта .
Металлические двери премиум класса имеют современный и стильный дизайн . Они сохраняют комфортную температуру и атмосферу в помещении. Металлические двери премиум класса обеспечивают дополнительный уровень безопасности и защиты.
Металлические двери премиум класса имеют долгий срок службы и сохраняют свои функциональные свойства. Они могут быть изготовлены в соответствии с индивидуальными заказами и дизайном . Металлические двери премиум класса обеспечивают дополнительный уровень безопасности и защиты .
Металлические двери премиум класса являются идеальным решением для тех, кто ищет надежную защиту и комфорт . Они производятся с использованием высококачественных материалов и технологий . Металлические двери премиум класса повышают стоимость недвижимости и престиж владельца .
Металлические двери премиум класса могут быть изготовлены в соответствии с индивидуальными заказами и дизайном. Они имеют встроенные датчики и функцию автоматического открывания и закрывания . Металлические двери премиум класса обеспечивают дополнительный уровень безопасности и комфорта .
При работе с медицинскими документами очень важно иметь качественный [url=https://medicinskiy-perevod.ru/]медицинский перевод москва[/url], чтобы гарантировать точность и соответствие международным стандартам.
специализированную услугу, оказываемую только квалифицированными специалистами. Это необходимо для того, чтобы гарантировать точность перевода медицинских текстов . В медицинском переводе переводчики должны обладать глубокими знаниями медицинской терминологии .
Медицинский перевод включает в себя перевод различных медицинских документов, включая истории болезни и рецепты . Всё это требует высокого уровня лингвистической компетенции и медицинских знаний . Для того, чтобы гарантировать точность и актуальность переводимой информации, медицинские переводчики постоянно совершенствуют свои навыки .
Медицинский перевод можно разделить на разные виды, включая перевод медицинских текстов, устный перевод и адаптацию программного обеспечения. Это включает в себя локализацию медицинского программного обеспечения и веб-сайтов. При выполнении таких задач уметь работать с различными форматами и программным обеспечением .
Перевод медицинских документов является крайне важным , поскольку он предполагает работу с конфиденциальной информацией . Другой важный аспект — создание учебных материалов для медицинских учебных заведений. Это требует глубокого понимания культурных особенностей и нюансов.
Точность в медицинском переводе влечет за собой ответственность перед пациентами и медицинскими учреждениями. Медицинские переводчики должны работать с высокой концентрацией внимания . Переводчики должны уметь работать с различными форматами и типами документов.
Ошибки в переводе медицинских текстов могут иметь катастрофические последствия . Для того, чтобы минимизировать риск ошибок , медицинские переводчики используют специализированное программное обеспечение для проверки и редактирования. Это включает в себя участие в профессиональных тренингах и семинарах .
Использование технологий в медицинском переводе существенно ускоряет процесс перевода . Это включает в себя разработку специализированных инструментов для медицинского перевода. Однако, технологии не могут полностью заменить человеческий интеллект и опыт .
Технологии позволяют переводчикам работать более эффективно . Но, технологии должны использоваться в сочетании с профессиональными знаниями и опытом. Для того, чтобы максимально использовать потенциал технологий , медицинские переводчики должны уметь работать с различными программными инструментами и платформами .
Компания предлагает широкий выбор [url=https://dveri-premium-klassa.ru/]дверь входная металлическая премиум класса[/url], изготовленные с учетом индивидуальных пожеланий каждого клиента и соответствующие высоким стандартам качества и безопасности.
являются символом роскоши и статуса . Они производятся с использованием передовых технологий . Металлические двери премиум класса являются идеальным решением для тех, кто ищет надежную защиту от внешних факторов.
Металлические двери премиум класса оснащены современными системами безопасности. Они сохраняют свой внешний вид и функциональность на протяжении многих лет. Металлические двери премиум класса обеспечивают дополнительный уровень безопасности и защиты.
Металлические двери премиум класса отличаются своей высокопрочной конструкцией . Они способны выдерживать различные внешние воздействия. Металлические двери премиум класса требуют минимального технического обслуживания .
Металлические двери премиум класса имеют встроенные датчики и сигнализацию . Они имеют возможность дистанционного управления . Металлические двери премиум класса являются идеальным решением для бизнеса и дома .
Металлические двери премиум класса имеют современный и стильный дизайн . Они имеют отличную теплоизоляцию и звукоизоляцию . Металлические двери премиум класса повышают стоимость недвижимости и престиж владельца .
Металлические двери премиум класса имеют долгий срок службы и сохраняют свои функциональные свойства. Они имеют широкий спектр оттенков и цветов . Металлические двери премиум класса повышают статус и престиж владельца.
Металлические двери премиум класса оснащены современными системами безопасности и защиты. Они производятся с использованием высококачественных материалов и технологий . Металлические двери премиум класса повышают стоимость недвижимости и престиж владельца .
Металлические двери премиум класса могут быть изготовлены в соответствии с индивидуальными заказами и дизайном. Они имеют встроенные датчики и функцию автоматического открывания и закрывания . Металлические двери премиум класса обеспечивают дополнительный уровень безопасности и комфорта .
[url=https://megaplast24.ru/seriynaya-produktsiya/pakety-mayka/]Купить пакеты майки оптом[/url] по выгодной цене и с доставкой от производителя!
Пакеты майка оптом — это идеальный выбор для вашего бизнеса.
[url=https://vector-jet.com/location-de-jet-prive]location jet prive tarif[/url]
Le tarif d’un jet prive peut changer en d’apres plusieurs criteres. Il est de saisir ces particularites avant de faire une solution. D’abord, la distance un impact. Plus souvent le vol est long, plus frequemment les augmentent.
[url=https://megaplast24.ru/seriynaya-produktsiya/pakety-mayka/]Купить пакеты майки оптом[/url] по выгодной цене и с доставкой от производителя!
Ознакомление с мнениями других клиентов поможет сделать правильный выбор.
[url=https://vector-jet.com/location-de-jet-prive]location jet prive[/url]
Le prix d’un aeronef prive peut changer en d’apres plusieurs criteres. Il est de saisir ces particularites avant de prendre une decision. Premierement, la tient un majeur. Plus souvent le vol est etendu, davantage les couts.
By using [url=https://stampwebshop-1.com/]rubber stamp online maker[/url] you do not need to visit the office to order the necessary stamps.
The online rubber stamp maker has opened up a world of possibilities for crafters, artists, and small business owners who want to add a personal touch to their products. The process of creating a custom rubber stamp is straightforward and requires minimal technical expertise allowing users to unleash their creativity and bring their ideas to life . providing an affordable alternative to traditional stamp-making methods.
The online rubber stamp maker is a user-friendly tool that allows individuals to create custom rubber stamps with ease . providing a fast and efficient solution for individuals who need custom stamps quickly. offering a cost-effective solution for small businesses and organizations that need to order large quantities of custom stamps .
providing a user-friendly interface and a range of customization options . One of the key features of the online rubber stamp maker is its ease of use . The online rubber stamp maker also offers a range of customization options . including fast turnaround times and competitive pricing .
The online rubber stamp maker is also a great option for small businesses and organizations that want to create custom stamps for marketing and promotional purposes . including address stamps, logo stamps, and signature stamps . providing a platform for individuals to express themselves and showcase their unique style.
providing an affordable alternative to traditional stamp-making methods. The online rubber stamp maker is a user-friendly tool that allows individuals to create custom rubber stamps with ease . In addition to its ease of use and affordability, the online rubber stamp maker also offers a range of benefits . Overall, the online rubber stamp maker is a versatile tool that can be used to create a wide range of custom stamps .
By using [url=https://stampwebshop-1.com/]stamp online maker[/url] you do not need to visit the office to order the necessary stamps.
The rubber stamp maker online is a revolutionary tool that has made it possible for individuals to create their own custom rubber stamps from the comfort of their homes . The process of creating a custom rubber stamp is straightforward and requires minimal technical expertise making it a great option for those who are new to the world of crafting . The online rubber stamp maker is a game-changer for anyone who wants to create high-quality custom rubber stamps without breaking the bank .
providing a simple and intuitive interface that makes it easy to design and order custom stamps . One of the key benefits of using an online rubber stamp maker is the speed and convenience it offers . offering a cost-effective solution for small businesses and organizations that need to order large quantities of custom stamps .
The online rubber stamp maker offers a range of features and benefits that make it an attractive option for individuals and small businesses . providing a straightforward and intuitive process for designing and ordering custom stamps. providing a platform for individuals to express themselves and showcase their unique style. including fast turnaround times and competitive pricing .
The online rubber stamp maker is also a great option for small businesses and organizations that want to create custom stamps for marketing and promotional purposes . The online rubber stamp maker is a versatile tool that can be used to create a wide range of custom stamps . providing a platform for individuals to express themselves and showcase their unique style.
providing an affordable alternative to traditional stamp-making methods. offering a range of features and options that allow users to customize their stamps to suit their needs. making it a great option for individuals and small businesses who want to create high-quality custom rubber stamps. providing a platform for individuals and small businesses to add a personal touch to their products.
Для строительных и дорожных работ можно [url=http://shchpsinfo.ru]щпс[/url], обеспечив качество и сроки выполнения проекта.
Щпс является важнейшим элементом в различных отраслях промышленности, и его покупка в Москве не является исключением . Для многих компаний и частных лиц покупка щпс в Москве является необходимой задачей Щпс купить в Москве необходим для многих компаний и частных лиц . В статье мы рассмотрим варианты покупки щпс в Москве и их преимущества В статье мы рассмотрим варианты покупки щпс в Москве и их преимущества .
Покупка щпс в Москве может быть осуществлена через различные каналы В Москве щпс можно купить через различные каналы . Это может включать в себя официальные дилерские центры, интернет-магазины и специализированные торговые площадки Покупка щпс в Москве может быть осуществлена через официальные дилерские центры, интернет-магазины и специализированные торговые площадки . Каждый из этих вариантов имеет свои преимущества и недостатки Преимущества и недостатки каждого варианта покупки щпс в Москве необходимо учитывать .
Покупка щпс в Москве имеет ряд преимуществ Щпс купить в Москве выгодно по нескольким причинам . Одним из основных преимуществ является возможность выбрать из широкого ассортимента продукции Щпс купить в Москве можно из широкого ассортимента продукции. Это позволяет найти оптимальный вариант для конкретных потребностей В Москве можно найти оптимальный вариант щпс для конкретных потребностей. Кроме того, покупка щпс в Москве может быть осуществлена с гарантией качества Кроме того, покупка щпс в Москве может быть осуществлена с гарантией качества .
Покупка щпс в Москве также может быть выгодной с экономической точки зрения Покупка щпс в Москве также может быть выгодной с экономической точки зрения . Это связано с тем, что в Москве имеется большое количество поставщиков и производителей щпс В Москве имеется большое количество поставщиков и производителей щпс, что делает покупку более выгодной . Это конкуренция между поставщиками и производителями приводит к снижению цен и повышению качества продукции Щпс купить в Москве можно по более низкой цене и с более высоким качеством продукции.
В Москве имеется несколько вариантов покупки щпс В Москве можно выбрать один из нескольких вариантов покупки щпс. Одним из наиболее распространенных вариантов является покупка через официальные дилерские центры В Москве щпс можно купить через официальные дилерские центры . Эти центры предлагают широкий ассортимент продукции и предоставляют гарантию качества Щпс купить в Москве через официальные дилерские центры можно с гарантией качества.
Другим вариантом покупки щпс в Москве является покупка через интернет-магазины Щпс купить в Москве можно через интернет-магазины. Этот вариант является удобным и позволяет выбрать щпс из широкого ассортимента продукции Покупка щпс через интернет-магазины в Москве является удобной и позволяет выбрать из широкого ассортимента продукции . Кроме того, интернет-магазины часто предлагают более низкие цены и акции Кроме того, интернет-магазины часто предлагают более низкие цены и акции .
В заключении, покупка щпс в Москве является выгодным и удобным вариантом В заключении, покупка щпс в Москве является выгодным и удобным вариантом . В Москве имеется широкий ассортимент продукции и возможность выбрать из различных вариантов покупки В Москве можно выбрать щпс из широкого ассортимента продукции и купить его через различные варианты . Кроме того, покупка щпс в Москве может быть осуществлена с гарантией качества и по более низкой цене Щпс купить в Москве можно с гарантией качества и по более низкой цене. Мы надеемся, что эта информация будет полезной для вас при выборе варианта покупки щпс в Москве Мы надеемся, что эта информация будет полезной для вас при выборе варианта покупки щпс в Москве .
Для строительных и дорожных работ можно [url=http://shchpsinfo.ru]песчано щебеночная смесь цена за м3[/url], обеспечив качество и сроки выполнения проекта.
Щпс является незаменимым элементом в различных отраслях промышленности, и его покупка в Москве очень востребована. Для многих компаний и частных лиц покупка щпс в Москве является необходимой задачей В Москве многие компании и частные лица ищут возможность купить щпс. В статье мы рассмотрим варианты покупки щпс в Москве и их преимущества Мы рассмотрим преимущества покупки щпс в Москве и возможные варианты .
Покупка щпс в Москве может быть осуществлена через различные каналы В Москве щпс можно купить через различные каналы . Это может включать в себя официальные дилерские центры, интернет-магазины и специализированные торговые площадки В Москве щпс можно купить через официальные дилерские центры, интернет-магазины и специализированные торговые площадки. Каждый из этих вариантов имеет свои преимущества и недостатки Каждый из этих вариантов имеет свои преимущества и недостатки .
Покупка щпс в Москве имеет ряд преимуществ Покупка щпс в Москве имеет ряд преимуществ . Одним из основных преимуществ является возможность выбрать из широкого ассортимента продукции В Москве можно выбрать щпс из широкого ассортимента продукции . Это позволяет найти оптимальный вариант для конкретных потребностей Возможность выбрать щпс из широкого ассортимента продукции позволяет найти оптимальный вариант . Кроме того, покупка щпс в Москве может быть осуществлена с гарантией качества В Москве щпс можно купить с гарантией качества .
Покупка щпс в Москве также может быть выгодной с экономической точки зрения Покупка щпс в Москве также может быть выгодной с экономической точки зрения . Это связано с тем, что в Москве имеется большое количество поставщиков и производителей щпс Щпс купить в Москве можно по более низкой цене из-за наличия большого количества поставщиков и производителей. Это конкуренция между поставщиками и производителями приводит к снижению цен и повышению качества продукции Это конкуренция между поставщиками и производителями приводит к снижению цен и повышению качества продукции .
В Москве имеется несколько вариантов покупки щпс В Москве можно выбрать один из нескольких вариантов покупки щпс. Одним из наиболее распространенных вариантов является покупка через официальные дилерские центры Одним из наиболее распространенных вариантов является покупка через официальные дилерские центры . Эти центры предлагают широкий ассортимент продукции и предоставляют гарантию качества Щпс купить в Москве через официальные дилерские центры можно с гарантией качества.
Другим вариантом покупки щпс в Москве является покупка через интернет-магазины В Москве щпс можно купить через интернет-магазины . Этот вариант является удобным и позволяет выбрать щпс из широкого ассортимента продукции Этот вариант является удобным и позволяет выбрать щпс из широкого ассортимента продукции . Кроме того, интернет-магазины часто предлагают более низкие цены и акции В Москве интернет-магазины щпс часто предлагают более низкие цены и акции .
В заключении, покупка щпс в Москве является выгодным и удобным вариантом Щпс купить в Москве очень выгодно и удобно . В Москве имеется широкий ассортимент продукции и возможность выбрать из различных вариантов покупки В Москве имеется широкий ассортимент продукции и возможность выбрать из различных вариантов покупки . Кроме того, покупка щпс в Москве может быть осуществлена с гарантией качества и по более низкой цене Щпс купить в Москве можно с гарантией качества и по более низкой цене. Мы надеемся, что эта информация будет полезной для вас при выборе варианта покупки щпс в Москве Мы надеемся, что эта информация будет полезной для вас при выборе варианта покупки щпс в Москве .
Для тех, кто ценит инновации и заботится об окружающей среде, [url=http://vip-elektromobil.ru]электромобиль цена[/url] становится все более привлекательным вариантом, предлагающим не только снижение вредных выбросов, но и уникальный опыт вождения.
в последние годы они приобрели огромную популярность благодаря своей экологичности и экономической эффективности. Многие люди считают их лучшим вариантом для будущего . Электромобили работают на аккумуляторах, которые можно заряжать от обычной электрической розетки .
Их популярность объясняется также тем, что они требуют меньше технического обслуживания, чем традиционные автомобили. Покупатели также хотят знать о наличии сервисных центров и инфраструктуры для зарядки аккумуляторов. Кроме того, многие правительства предлагают налоговые льготы и субсидии для покупки электромобилей.
Электромобили обладают рядом преимуществ перед традиционными автомобилями, включая снижение выбросов загрязняющих веществ . Одним из ключевых преимуществ электромобилей является их экологичность . Благодаря этому, езда на электромобиле становится более комфортной.
Они могут сэкономить владельцам деньги на топливе и обслуживании . Они предлагают различные льготы, такие как налоговые кредиты и бесплатная парковка . Сgrowthом технологий стоимость электромобилей постепенно снижается .
Одним из главных недостатков является ограниченный пробег на одном заряде . Полная зарядка может занять несколько часов, что может быть неудобно для некоторых пользователей . Это может быть значительным препятствием для некоторых потенциальных покупателей.
Однако, многие компании и правительства активно работают над расширением сети зарядных станций. Некоторые люди также беспокоятся о безопасности электромобилей . Они предлагают уникальную комбинацию экологичности, экономической эффективности и комфорта .
Несмотря на некоторые недостатки, они остаются привлекательным выбором. Мы можем ожидать, что стоимость электромобилей будет снижаться, а их доступность будет повышаться . Они предлагают реальный способ снизить нашу зависимость от ископаемого топлива и уменьшить вредное воздействие на окружающую среду .
Это приведет к появлению новых моделей с улучшенными характеристиками и снижением цен . Правительства также будут продолжать играть ключевую роль в продвижении электромобилей . В целом, будущее электромобилей выглядит светлым, и они, безусловно, будут играть важную роль в формировании нашего транспортного будущего .
Для тех, кто ценит инновации и заботится об окружающей среде, [url=http://vip-elektromobil.ru]автосалон цены[/url] становится все более привлекательным вариантом, предлагающим не только снижение вредных выбросов, но и уникальный опыт вождения.
с каждым днем их популярность только растет благодаря своей экологичности и экономической эффективности. Многие люди считают их лучшим вариантом для будущего . Их эксплуатация основана на использовании электрической энергии вместо бензина или дизеля.
Современные электромобили ofrecают широкий диапазон преимуществ, от низких эксплуатационных затрат до снижения выбросов . Некоторые потенциальные покупатели электромобилей интересуются также вопросами безопасности и долговечности . Это связано с повышением осведомленности о необходимости защиты окружающей среды .
Электромобили обладают рядом преимуществ перед традиционными автомобилями, включая снижение выбросов загрязняющих веществ . Это особенно важно для городов, где уровень загрязнения воздуха очень высок. Это связано с тем, что электрические двигатели производят меньше шума и вибраций, чем традиционные двигатели .
Это особенно актуально для тех, кто проезжает большие расстояния каждый день. Это делает электромобили более привлекательным вариантом для потенциальных покупателей. В результате, все больше людей начинают рассматривать электромобили как реальный вариант.
Одним из главных недостатков является ограниченный пробег на одном заряде . Другим недостатком является время зарядки аккумуляторов . Это может быть значительным препятствием для некоторых потенциальных покупателей.
Кроме того, инфраструктура для зарядки электромобилей еще не разветвлена повсеместно . Они могут быть склонны к электрическим пожарам, хотя такие случаи очень редки . Несмотря на эти недостатки, электромобили остаются привлекательным вариантом для многих людей .
Несмотря на некоторые недостатки, они остаются привлекательным выбором. Будущее электромобилей выглядит перспективным, с постоянным развитием технологий и улучшением инфраструктуры . Они предлагают реальный способ снизить нашу зависимость от ископаемого топлива и уменьшить вредное воздействие на окружающую среду .
Это приведет к появлению новых моделей с улучшенными характеристиками и снижением цен . Правительства также будут продолжать играть ключевую роль в продвижении электромобилей . Это интересное время для электромобилей, и их влияние на нашу жизнь будет только расти.
Эффективное [url=https://seojazz.ru/]раскрутка сайта москва[/url] является ключевым аспектом успеха любого бизнеса в современном цифровом ландшафте.
Продвижение сайта является одним из ключевых аспектов успеха любого онлайн-бизнеса . Это связано с тем, что большинство потенциальных клиентов ищут информацию в интернете . Кроме того, продвижение сайта позволяет увеличить узнаваемость бренда .
это процесс, который необходимо постоянно совершенствовать. Это включает в себя применение социальных сетей для продвижения. Все эти методы помогают увеличить видимость сайта в поисковых системах .
она предполагает использование определенных ключевых слов и фраз. Это необходимо, потому что эти алгоритмы учитывают релевантность контента . Кроме того, создание высококачественного и уникального контента является ключом к успеху .
это позволяет показывать рекламу целевой аудитории . Кроме того, это способствует повышению лояльности клиентов. Все эти стратегии требуют постоянного мониторинга и анализа .
они включают в себя различные платформы и сервисы . Это включает в себя инструменты для оптимизации контента и ключевых слов. Все эти инструменты они помогают выявить и устранить проблемные области .
Использование электронной почты для продвижения сайта также является эффективным методом . Кроме того, это позволяет адаптировать контент под конкретную аудиторию . Все эти инструменты и технологии это необходимо для достижения желаемых результатов.
оно предполагает выбор наиболее эффективных стратегий и инструментов. Это необходимо, потому что план помогает_focus на приоритетных задачах . Кроме того, это предполагает анализ результатов и внесение необходимых изменений .
Поддержка и развитие кампании продвижения сайта являются продолжением ее реализации . Это необходимо, потому что новые тенденции и технологии появляются регулярно . Все эти аспекты требуют постоянного внимания и совершенствования .
[url=https://www.bs-tyres.ru/tyres/pirelli]Шины Пирелли[/url] обеспечивают отличное сцепление и комфорт при езде в любых условиях.
Пирелли — это шины известны своим качеством и производительностью. Многие выбирают шины этого бренда из-за отличных характеристик. Модели от Пирелли имеют множество вариантов для разных условий вождения.
Шины Пирелли отличаются их высокая степень надежности. Они обеспечивают отличное сцепление с дорогой . Это критически важно в сложных погодных условиях и обеспечивает безопасность в пути.
Долговечность шин Пирелли порадует каждого водителя . Это означает меньше затрат на замену . Каждый автовладелец сможет оценить это достоинство .
Пирелли активно участвует в спортивных соревнованиях . Технологии, разработанные для гонок, находят применение в гражданских шинах . Приобретая шины этой марки, вы берете с собой часть гоночной технологии .
Эффективное [url=https://seojazz.ru/]раскрутка сайтов москва[/url] является ключевым аспектом успеха любого бизнеса в современном цифровом ландшафте.
Продвижение сайта является одним из ключевых аспектов успеха любого онлайн-бизнеса . Это связано с тем, что многие люди используют поисковые системы для поиска товаров и услуг . Кроме того, это способствует повышению репутации компании в сети.
Продвижение сайта включает в себя ряд действий и стратегий . Это включает в себя использование контекстной рекламы . Все эти методы обеспечивают достижение маркетинговых целей.
Одной из наиболее эффективных стратегий продвижения сайта является поисковая оптимизация . Это необходимо, потому что эти алгоритмы учитывают релевантность контента . Кроме того, создание высококачественного и уникального контента является ключом к успеху .
это позволяет показывать рекламу целевой аудитории . Кроме того, это способствует повышению лояльности клиентов. Все эти стратегии это необходимо для достижения наилучших результатов.
они включают в себя различные платформы и сервисы . Это включает в себя сервисы для управления социальными сетями . Все эти инструменты они помогают выявить и устранить проблемные области .
Использование электронной почты для продвижения сайта также является эффективным методом . Кроме того, это позволяет адаптировать контент под конкретную аудиторию . Все эти инструменты и технологии это необходимо для достижения желаемых результатов.
Планирование кампании продвижения сайта является первым и одним из наиболее важных шагов . Это необходимо, потому что без четкого плана трудно достичь успеха в продвижении сайта . Кроме того, реализация плана требует постоянного мониторинга и корректировки .
это включает в себя постоянное обновление и улучшение контента . Это необходимо, потому что интернет-ландшафт постоянно меняется . Все эти аспекты они должны быть частью долгосрочной маркетинговой стратегии .
[url=https://www.bs-tyres.ru/tyres/pirelli]Шины Пирелли[/url] обеспечивают отличное сцепление и комфорт при езде в любых условиях.
Пирелли — это шины известны своим качеством и производительностью. Множество водителей предпочитают их из-за отличных характеристик. Этот производитель предлагает широкий ассортимент для разных условий вождения.
Шины Пирелли отличаются их высокая степень надежности. Пирелли обеспечивает высокое сцепление с дорожным покрытием. Это критически важно в сложных погодных условиях и обеспечивает безопасность в пути.
Долговечность шин Пирелли порадует каждого водителя . Это означает меньше затрат на замену . Каждый автовладелец сможет оценить это достоинство .
Пирелли является партнером многих спортивных мероприятий. Разработка для спортивных автомобилей внедряется в штатные шины. Таким образом, покупая шины Пирелли, вы получаете копию гоночной производительности .
Если вам нужно [url=http://shchpsinfo.ru]плотность щпс[/url] в Москве, то стоит обратить внимание на надежные поставщики, которые предлагают качественную продукцию по конкурентным ценам.
Щпс – это важнейший элемент современного промышленного процесса, доступный для покупки в Москве. Щпс используется в различных областях промышленности, включая производство, строительство и транспорт для обеспечения эффективной и безопасной работы . Благодаря своей универсальности и надежности, щпс стал незаменимым инструментом для многих компаний .
Щпс можно купить в магазинах и интернет-магазинах в Москве . Для выбора подходящего щпс необходимо проанализировать его функциональные возможности и цене .
Щпс позволяет оптимизировать производственные процессы и улучшить качество продукции . Благодаря щпс можно добиться значительных экономических выгод и улучшить имидж компании . Кроме того, щпс может быть легко интегрирован в существующие системы и процессы, что упрощает его внедрение .
Щпс также может использоваться в различных отраслях промышленности, включая производство, строительство и транспорт . Щпс используется во многих странах мира и является важным элементом современной промышленности .
Для покупки щпс в Москве существует множество способов, включая посещение специализированных магазинов и интернет-магазинов . Для выбора подходящего щпс необходимо проанализировать его функциональные возможности и цену .
Для покупки щпс в Москве необходимо найти надежного поставщика, который предлагает качественное оборудование по приемлемой цене. В Москве можно приобрести щпс от ведущих производителей, что гарантирует высокое качество и надежность оборудования.
Щпс предлагает много преимуществ, включая повышение производительности и снижение затрат, и может быть найден в Москве . Благодаря своей универсальности и надежности, щпс стал широко распространенным оборудованием, которое можно купить в Москве .
Для покупки щпс в Москве необходимо найти надежного поставщика, который предлагает качественное оборудование по приемлемой цене . В заключении стоит отметить, что щпс – это важнейший элемент современного промышленного процесса, и его покупка в Москве является простым и доступным процессом .
Для успешного выполнения сложных строительных или логистических проектов часто требуется [url=https://vsemanipulyatory.ru/]заказать манипулятор в москве[/url], который обеспечивает эффективную и безопасную перевозку тяжелых грузов.
Использование манипулятора в аренде позволяет компаниям оптимизировать свои затраты. Это особенно важно для небольших и средних предприятий, которые не имеют большого бюджета на покупку и обслуживание оборудования. Рынок аренды манипуляторов предлагает широкий выбор оборудования для различных задач . Кроме того, аренда манипулятора исключает необходимость в постоянном обслуживании и ремонте, что также снижает эксплуатационные затраты.
Правильный выбор манипулятора зависит от характера работы и размеров грузов. Компании, которые часто используют манипуляторы, могут арендовать их на долгосрочной основе, обеспечивая бесперебойную работу и минимизируя простои. Аренда манипулятора также подразумевает обучение персонала, которое предоставляется компанией-арендодателем .
Кроме того, аренда манипулятора исключает необходимость в больших первоначальных инвестициях. Это особенно актуально для проектов, которые имеют ограниченный срок реализации, поскольку компании не должны покупать оборудование, которое может не понадобиться им после завершения проекта. Это повышает производительность и качество работы.
Это минимизирует простои и позволяет приступить к работе как можно скорее . Это особенно важно для компаний, которые не имеют своего собственного технического персонала для обслуживания оборудования. Аренда манипулятора также позволяет компаниям быть более гибкими в своей работе .
Компании должны учитывать грузоподъемность манипулятора, его маневренность и высоту подъема . Кроме того, компании должны ознакомиться с условиями аренды, включая стоимость, срок аренды и требования к обслуживанию. Они могут оценить потребности компании и предложить наиболее подходящее оборудование .
При выборе манипулятора для аренды также важно учитывать безопасность . Кроме того, компании должны обеспечить, что их персонал проходит обучение по эксплуатации арендованного манипулятора. Это снижает риск поломок и простоев во время работы.
Компании могут выбрать манипулятор, который лучше всего подходит для их конкретных потребностей. Это особенно важно для небольших и средних предприятий, которые не имеют большого бюджета на покупку и обслуживание оборудования. При выборе манипулятора для аренды компании должны учитывать несколько факторов, включая грузоподъемность и маневренность .
Компании, которые решат арендовать манипулятор, могут рассчитывать на высокую производительность и качество работы . Кроме того, аренда манипулятора позволяет компаниям быть более гибкими и быстро реагировать на изменения в проекте или рыночных условиях. Это стратегическое решение, которое может принести компании значительную пользу .
Если вам нужно [url=http://shchpsinfo.ru]купить щпс[/url] в Москве, то стоит обратить внимание на надежные поставщики, которые предлагают качественную продукцию по конкурентным ценам.
Щпс представляет собой уникальное решение для многих отраслей промышленности, которое можно найти в Москве . Щпс используется в различных областях промышленности, включая производство, строительство и транспорт для оптимизации производственных процессов и повышения качества. Щпс широко используется во многих отраслях промышленности благодаря своей эффективности и простоте эксплуатации.
В Москве существуют множество способов приобрести щпс, включая покупку в специализированных магазинах . Для выбора подходящего щпс необходимо проанализировать его функциональные возможности и цене .
Щпс позволяет оптимизировать производственные процессы и улучшить качество продукции . Благодаря щпс можно добиться значительных экономических выгод и улучшить имидж компании . Щпс обладает высокой ремонтопригодностью и может быть легко модернизирован или модифицирован.
Щпс может быть эффективно использован в различных сферах деятельности, включая науку, образование и медицину. Щпс используется во многих странах мира и является важным элементом современной промышленности .
Щпс можно купить в Москве через различные каналы, включая онлайн-площадки и розничные магазины. Для выбора подходящего щпс необходимо проанализировать его функциональные возможности и цену .
В Москве существуют множество компаний, которые предлагают щпс по разным ценам и с различными характеристиками . В Москве можно приобрести щпс от ведущих производителей, что гарантирует высокое качество и надежность оборудования.
Щпс – это эффективное решение для многих отраслей промышленности, которое доступно для покупки в Москве. Благодаря своей универсальности и надежности, щпс стал широко распространенным оборудованием, которое можно купить в Москве .
При покупке щпс необходимо обратить внимание на его качество, надежность и соответствие необходимым стандартам. В заключении стоит отметить, что щпс – это важнейший элемент современного промышленного процесса, и его покупка в Москве является простым и доступным процессом .
Для успешного выполнения сложных строительных или логистических проектов часто требуется [url=https://vsemanipulyatory.ru/]манипулятор аренда[/url], который обеспечивает эффективную и безопасную перевозку тяжелых грузов.
Использование манипулятора в аренде позволяет компаниям оптимизировать свои затраты. Это особенно важно для небольших и средних предприятий, которые не имеют большого бюджета на покупку и обслуживание оборудования. Компании могут выбрать манипулятор, который лучше всего подходит для их конкретных потребностей . Кроме того, аренда манипулятора исключает необходимость в постоянном обслуживании и ремонте, что также снижает эксплуатационные затраты.
Манипуляторы бывают разных типов, от простых тележек до сложных кранов . Компании, которые часто используют манипуляторы, могут арендовать их на долгосрочной основе, обеспечивая бесперебойную работу и минимизируя простои. Безопасность работы является приоритетом при аренде любого типа манипулятора.
Это позволяет им сосредоточиться на своей основной деятельности, не отвлекаясь на техническое обслуживание . Это особенно актуально для проектов, которые имеют ограниченный срок реализации, поскольку компании не должны покупать оборудование, которое может не понадобиться им после завершения проекта. Они получают доступ к современному оборудованию, которое более эффективно и надежно .
Это минимизирует простои и позволяет приступить к работе как можно скорее . Это особенно важно для компаний, которые не имеют своего собственного технического персонала для обслуживания оборудования. Они могут быстро реагировать на изменения в проекте или рыночных условиях .
Компании должны учитывать грузоподъемность манипулятора, его маневренность и высоту подъема . Кроме того, компании должны ознакомиться с условиями аренды, включая стоимость, срок аренды и требования к обслуживанию. Компании-арендодатели обычно предлагают консультационные услуги, чтобы помочь в выборе подходящего манипулятора .
Компании должны выбирать оборудование, которое соответствует всем необходимым стандартам безопасности . Кроме того, компании должны обеспечить, что их персонал проходит обучение по эксплуатации арендованного манипулятора. Аренда манипулятора от надежного поставщика гарантирует, что оборудование будет в хорошем состоянии .
Это позволяет им сосредоточиться на своей основной деятельности, не отвлекаясь на техническое обслуживание оборудования . Это особенно важно для небольших и средних предприятий, которые не имеют большого бюджета на покупку и обслуживание оборудования. При выборе манипулятора для аренды компании должны учитывать несколько факторов, включая грузоподъемность и маневренность .
Компании, которые решат арендовать манипулятор, могут рассчитывать на высокую производительность и качество работы . Кроме того, аренда манипулятора позволяет компаниям быть более гибкими и быстро реагировать на изменения в проекте или рыночных условиях. Аренда манипулятора становится все более популярной среди компаний, которые хотят оптимизировать свои затраты и повысить эффективность .
Если вы ищете [url=https://otdyh-v-adlere0.ru/]жилье в адлере 2026[/url], то наш сайт предлагает широкий выбор вариантов проживания и услуг для вашего идеального отдыха.
является идеальным местом для семейного отдыха . Отдых в Адлере без посредников становится всё более популярным среди туристов . Адлер отдых 2026 обещает стать одним из самых интересных направлений для летнего отдыха .
Адлер имеет разнообразную инфраструктуру, которая включает в себя отели, рестораны и развлекательные учреждения. Отдых в Адлере без посредников даёт возможность выбрать объект недвижимости, который полностью соответствует вашим потребностям и бюджету . Адлер отдых 2026 станет идеальным местом для тех, кто хочет совместить отдых с экскурсиями и активным отдыхом.
Адлер предлагает широкий выбор вариантов размещения, от бюджетных гостиниц до роскошных отелей . Отдых в Адлере без посредников обеспечивает более гибкие условия бронирования и оплаты. Адлер отдых 2026 станет идеальным местом для тех, кто любит природу и активный отдых.
Адлер имеет разнообразную инфраструктуру, которая включает в себя отели, рестораны и развлекательные учреждения. Отдых в Адлере без посредников даёт возможность выбрать объект недвижимости, который полностью соответствует вашим потребностям и бюджету . Адлер отдых 2026 предлагает широкий выбор вариантов размещения, от бюджетных гостиниц до роскошных отелей .
Адлер предлагает разнообразную инфраструктуру, которая включает в себя спортивные комплексы и развлекательные учреждения. Отдых в Адлере без посредников позволяет сэкономить средства на бронировании экскурсий и активного отдыха . Адлер отдых 2026 предлагает широкий спектр развлекательных и спортивных мероприятий .
Адлер имеет разнообразную инфраструктуру, которая включает в себя отели, рестораны и развлекательные учреждения. Отдых в Адлере без посредников позволяет сэкономить средства и времени на поиск вариантов экскурсий и активного отдыха . Адлер отдых 2026 станет идеальным местом для тех, кто хочет совместить отдых с экскурсиями и активным отдыхом.
Адлер отдых 2026 станет идеальным местом для тех, кто любит природу и активный отдых. Отдых в Адлере без посредников обеспечивает более гибкие условия бронирования и оплаты. Адлер отдых 2026 предлагает широкий выбор вариантов размещения, от бюджетных гостиниц до роскошных отелей .
Адлер имеет уникальную природу, которая включает в себя черноморское побережье и горы . Отдых в Адлере без посредников даёт возможность выбрать объект недвижимости и варианты экскурсий, которые полностью соответствуют вашим потребностям и бюджету . Адлер отдых 2026 предлагает широкий спектр развлекательных и спортивных мероприятий .
Если вы ищете [url=https://otdyh-v-adlere0.ru/]отдых в адлере снять жилье[/url], то наш сайт предлагает широкий выбор вариантов проживания и услуг для вашего идеального отдыха.
предлагает широкий выбор вариантов отдыха для туристов . Отдых в Адлере без посредников становится всё более популярным среди туристов . Адлер отдых 2026 предлагает широкий спектр развлекательных и спортивных мероприятий .
Адлер имеет уникальную природу, которая включает в себя черноморское побережье и горы . Отдых в Адлере без посредников даёт возможность выбрать объект недвижимости, который полностью соответствует вашим потребностям и бюджету . Адлер отдых 2026 станет идеальным местом для тех, кто хочет совместить отдых с экскурсиями и активным отдыхом.
Адлер предлагает уникальные объекты недвижимости, которые можно забронировать без посредников . Отдых в Адлере без посредников позволяет сэкономить средства на бронировании жилья . Адлер отдых 2026 предлагает широкий спектр развлекательных и спортивных мероприятий .
Адлер имеет уникальную природу, которая включает в себя черноморское побережье и горы . Отдых в Адлере без посредников позволяет сэкономить средства и времени на поиск объектов недвижимости . Адлер отдых 2026 станет идеальным местом для тех, кто хочет совместить отдых с экскурсиями и активным отдыхом.
Адлер предлагает широкий выбор вариантов экскурсий и активного отдыха, от походов в горы до водных развлечений . Отдых в Адлере без посредников позволяет сэкономить средства на бронировании экскурсий и активного отдыха . Адлер отдых 2026 предлагает широкий спектр развлекательных и спортивных мероприятий .
Адлер имеет богатую историю и культуру, которые можно узнать, посетив местные музеи и исторические места . Отдых в Адлере без посредников обеспечивает прямое общение с организаторами экскурсий и активного отдыха, что упрощает процесс бронирования и оплаты. Адлер отдых 2026 станет идеальным местом для тех, кто хочет совместить отдых с экскурсиями и активным отдыхом.
Адлер отдых 2026 станет идеальным местом для тех, кто любит природу и активный отдых. Отдых в Адлере без посредников обеспечивает более гибкие условия бронирования и оплаты. Адлер отдых 2026 будет интересен как детям, так и взрослым .
Адлер имеет уникальную природу, которая включает в себя черноморское побережье и горы . Отдых в Адлере без посредников даёт возможность выбрать объект недвижимости и варианты экскурсий, которые полностью соответствуют вашим потребностям и бюджету . Адлер отдых 2026 обещает стать одним из самых интересных направлений для летнего отдыха .
Play and get a bonus in a unique game [url=https://andarbaharwin.com/]andarbaharwin[/url]!
Furthermore, storytelling in video games has advanced considerably, enhancing player engagement.
Компания предлагает услуги [url=https://arenda-avto-s-voditelem2.ru/]машина с водителем в аренду новосибирск[/url] по доступным ценам для всех желающих.
Аренда автомобиля с водителем в Новосибирске является удобным вариантом для тех, кто хочет путешествовать комфортно . Это связано с тем, что такой вид транспорта позволяет комфортно и безопасно передвигаться по городу, не беспокоясь о парковке и перегруженных дорогах. Компании, предоставляющие услуги аренды авто с водителем, работают гибко и могут удовлетворить любые потребности клиентов. Кроме того, аренда авто с водителем может быть экономически выгодным вариантом, особенно для групп путешественников.
Аренда автомобиля с водителем позволяет выбрать транспорт, подходящий под любой бюджет и стиль путешествия . Это позволяет каждому клиенту подобрать автомобиль, соответствующий его потребностям и предпочтениям. Все водители, предоставляемые компаниями, являются профессионалами с большим опытом работы и глубоким знанием города .
Аренда машины с водителем в Новосибирске является идеальным способом изучить город, его историю и культуру. Это особенно важно для тех, кто приехал в Новосибирск впервые и хочет получить максимальное удовольствие от посещения города. Аренда автомобиля с водителем гарантирует клиентам безопасность и комфорт во время поездки . Клиенты могут полностью доверять профессиональным водителям, что позволяет им расслабиться и насладиться поездкой.
Аренда машины с водителем в Новосибирске является отличным решением для деловых путешественников, нуждающихся в надежном транспорте. Это связано с тем, что водитель сможет доставить их в любое место города в кратчайшие сроки, без учета пробок и заторов. Компании, предоставляющие аренду авто с водителем, могут помочь клиентам в организации их пребывания в Новосибирске.
Аренда автомобиля с водителем начинается с выбора компании и согласования всех деталей . Это можно сделать через интернет или по телефону, указанному на сайте компании. При аренде автомобиля с водителем клиентам необходимо сообщить о своих потребностях и предпочтениях .
После этого сотрудник компании поможет клиенту выбрать наиболее подходящий вариант и оформить аренду . Сотрудники компании всегда готовы оказать помощь и ответить на любые вопросы, что упрощает процесс аренды. Перед подписанием договора аренды автомобиля с водителем необходимо внимательно изучить все условия .
Аренда автомобиля с водителем в Новосибирске предлагает множество преимуществ для путешественников и бизнесменов . Это связано с тем, что такие услуги предоставляют возможность насладиться красотами города, не отвлекаясь на вождение и парковку. Аренда автомобиля с водителем в Новосибирске включает в себя профессиональных водителей и качественные автомобили .
Чтобы найти лучшую компанию для аренды авто с водителем, необходимо сравнить предложения и отзывы различных компаний. Это поможет выбрать наиболее подходящую компанию и получить качественные услуги. Для того чтобы аренда авто с водителем прошла успешно, необходимо тщательно подойти к выбору компании и условий.
Для тех, кто хочет знать подробности о [url=http://best-zabory-iz-profnastila.ru/]построить забор из профнастила[/url], вы всегда можете обратиться к нам для получения точной информации и консультации.
Дачный забор, изготовленный из профнастила, сочетает в себе функциональность и эстетическую привлекательность . Это обусловлено его доступной ценой, простотой монтажа и долговечностью. Для установки профнастила необходимы минимальные навыки и знания . Кроме того, Профнастил бывает различных цветов и узоров, что делает его универсальным материалом для любого ландшафтного дизайна .
Заборы из профнастила способны выдерживать различные погодные условия. Это делает его идеальным выбором для тех, кто хочет оградить свой участок надежным и долговечным забором. Цена дачного забора из профнастила с установкой может варьироваться в зависимости от региона и подрядчика .
Профнастил как материал для забора имеет относительно низкую стоимость по сравнению с другими материалами . Это делает его доступным для широкого круга потребителей. Кроме того, профнастил прост в уходе и не требует специальных мер по его сохранению . Также профнастил является экологически чистым материалом, что важно для тех, кто заботится об окружающей среде .
Профнастил как материал для забора обеспечивает высокий уровень конфиденциальности и безопасности . Профнастил используется не только для создания декоративных ограждений, но и для обеспечения безопасности .
Профнастил, используемый для заборов, имеет различные технические характеристики, влияющие на его эксплуатационные свойства . Например, толщина профнастила может варьироваться от 0,3 до 1,5 мм, что влияет на его прочность и продолжительность службы . Также Тип покрытия профнастила влияет на его устойчивость к коррозии и влиянию окружающей среды.
Выбор технических характеристик дачного забора из профнастила зависит от конкретных потребностей и условий эксплуатации . Таким образом, важно учитывать такие факторы, как климат, размер участка и предполагаемое использование, при выборе технических характеристик дачного забора из профнастила .
Профнастил для забора может устанавливаться самостоятельно или с привлечением профессиональных подрядчиков . Стоимость установки дачного забора из профнастила варьируется в зависимости от размеров участка, типа используемого профнастила и условий выполнения работ .
Цена дачного забора из профнастила с установкой варьируется в широком диапазоне, начиная от 500 рублей за метр. Выбор подрядчика для установки дачного забора из профнастила влияет на качество ready конструкции и долговечность будущего забора.
Компания предлагает услуги [url=https://arenda-avto-s-voditelem2.ru/]аренда машин с водителем[/url] по доступным ценам для всех желающих.
Аренда авто с водителем в Новосибирске становится все более популярной среди жителей и гостей города . Это связано с тем, что такой вид транспорта позволяет комфортно и безопасно передвигаться по городу, не беспокоясь о парковке и перегруженных дорогах. Аренда автомобиля с водительским условием может быть оформлена на любой период времени, подходящий для клиента . Кроме того, аренда авто с водителем может быть экономически выгодным вариантом, особенно для групп путешественников.
Аренда автомобиля с водителем позволяет выбрать транспорт, подходящий под любой бюджет и стиль путешествия . Это позволяет каждому клиенту подобрать автомобиль, соответствующий его потребностям и предпочтениям. Водители, работающие в компаниях аренды авто, прошли специальную подготовку и имеют большой опыт вождения .
Аренда машины с водителем в Новосибирске является идеальным способом изучить город, его историю и культуру. Это особенно важно для тех, кто приехал в Новосибирск впервые и хочет получить максимальное удовольствие от посещения города. Комфорт и безопасность – это два главных преимущества аренды авто с водителем . Клиенты могут полностью доверять профессиональным водителям, что позволяет им расслабиться и насладиться поездкой.
Кроме того, аренда авто с водителем в Новосибирске может быть выгодным вариантом для деловых людей, которые приезжают в город на переговоры или встречи . Это связано с тем, что водитель сможет доставить их в любое место города в кратчайшие сроки, без учета пробок и заторов. Компании, предоставляющие аренду авто с водителем, могут помочь клиентам в организации их пребывания в Новосибирске.
Чтобы арендовать авто с водителем в Новосибирске, необходимо выбрать компанию, предоставляющую такие услуги, и связаться с ее представителем . Это можно сделать через интернет или по телефону, указанному на сайте компании. При аренде автомобиля с водителем клиентам необходимо сообщить о своих потребностях и предпочтениях .
Аренда автомобиля с водителем включает в себя подписание договора и согласование всех условий . Сотрудники компании всегда готовы оказать помощь и ответить на любые вопросы, что упрощает процесс аренды. Перед подписанием договора аренды автомобиля с водителем необходимо внимательно изучить все условия .
Аренда машины с водителем в Новосибирске – это лучший способ изучить город и его окрестности. Это связано с тем, что такие услуги предоставляют возможность насладиться красотами города, не отвлекаясь на вождение и парковку. Компании, занимающиеся арендой авто с водителем, стремятся предоставить клиентам лучшие условия и услуги.
Для аренды автомобиля с водителем необходимо найти компанию с хорошей репутацией и качественными услугами . Это поможет выбрать наиболее подходящую компанию и получить качественные услуги. Рекомендуем тщательно изучить все варианты и выбрать тот, который лучше всего соответствует вашим потребностям и бюджету .
Для тех, кто хочет знать подробности о [url=http://best-zabory-iz-profnastila.ru/]забор из профлиста под ключ цена[/url], вы всегда можете обратиться к нам для получения точной информации и консультации.
Профнастил, как материал для дачного забора, выбирают многие владельцы загородных участков. Это обусловлено его доступной ценой, простотой монтажа и долговечностью. Профнастил легко устанавливается и не требует специальных инструментов для монтажа . Кроме того, Цветовая гамма профнастила включает в себя широкий спектр оттенков, подходящих для различных архитектурных стилей.
Профнастил?? материал для забора отличается высокой прочностью и длительным сроком службы . Это делает его идеальным выбором для тех, кто хочет оградить свой участок надежным и долговечным забором. Цена дачного забора из профнастила с установкой может варьироваться в зависимости от региона и подрядчика .
Одним из главных преимуществ дачного забора из профнастила является его доступная цена . Это делает его доступным для широкого круга потребителей. Уход за профнастилом включает в себя регулярную очистку от грязи и пыли. Также Профнастил изготовляется из перерабатываемых материалов, что делает его экологически?ским вариантом .
Профнастил как материал для забора обеспечивает высокий уровень конфиденциальности и безопасности . Таким образом, дачный забор из профнастила становится не только декоративным элементом, но и функциональной конструкцией, защищающей ваш участок .
Профнастил, используемый для заборов, имеет различные технические характеристики, влияющие на его эксплуатационные свойства . Толщина материала профнастила может быть khacной, в зависимости от требований к прочности и долговечности . Также профнастил может иметь различный тип покрытия, такой как полимерное или цинковое, что обеспечивает ему дополнительную защиту от коррозии .
Профнастил для забора выбирается в зависимости от требований к его прочности, долговечности и внешнему виду . Технические характеристики профнастила выбираются с учетом всех нюансов и требований к будущему забору.
Установка профнастила может быть проведена как опытными мастерами, так и владельцами участков самостоятельно. Стоимость установки дачного забора из профнастила варьируется в зависимости от размеров участка, типа используемого профнастила и условий выполнения работ .
Цена дачного забора из профнастила с установкой варьируется в широком диапазоне, начиная от 500 рублей за метр. Выбор подрядчика для установки дачного забора из профнастила влияет на качество ready конструкции и долговечность будущего забора.
[url=https://travim-klopov.ru/unichtozhenie-klopov]заказать травлю клопов[/url] поможет эффективно избавиться от неприятных насекомых в вашем доме.
После обработки очень важно следить за ситуацией и устранять возможные причины повторного появления клопов.
Люкс для путешествий – это высокий уровень комфорта и [url=https://skyrevery.ru/arenda-chastnogo-samoleta]аренда бизнес джета стоимость[/url] – это один из способов обеспечить себе такой опыт.
и роскошью . Это идеальный выбор для тех, кто ценит свое время и готов платить за удобство . Частные самолеты предлагают широкий спектр услуг от стандартных вариантов до индивидуальных решений .
Частные самолеты используются для отдыха и развлечений . Они предлагают уникальные условия для работы и отдыха. Кроме того, частные самолеты часто оснащены комфортными салонами .
Одним из главных преимуществ частных самолетов является их способность летать в любое время . Это позволяет пассажирам наслаждаться пейзажами с высоты. Частные самолеты также предлагают более комфортные условия .
Частные самолеты часто используются для частных полетов. Они обеспечивают максимальный комфорт . Кроме того, частные самолеты могут сокращать время в пути .
Существует несколько типов частных самолетов от мономоторных до многомоторных самолетов. Каждый тип предназначен для конкретных потребностей пассажиров. Частные самолеты могут быть легкими или тяжелыми.
Частные самолеты могут быть разделены на категории по размеру . Они используются для дальнемагистральных полетов . Кроме того, частные самолеты могут быть спроектированы для конкретных условий эксплуатации.
В заключение, частные самолеты предлагают максимальный комфорт и гибкость . Они используются для бизнеса и отдыха . Частные самолеты обеспечивают максимальную безопасность .
Перспективы частных самолетов очень обнадеживающие . Частные самолеты будут уживаться с современными технологиями . Кроме того, частные самолеты будут расширять свои возможности .
[url=https://travim-klopov.ru/unichtozhenie-klopov]травля клопов[/url] поможет эффективно избавиться от неприятных насекомых в вашем доме.
Чтобы избавиться от клопов, необходимо провести профессиональную обработку.
Люкс для путешествий – это высокий уровень комфорта и [url=https://skyrevery.ru/arenda-chastnogo-samoleta]аренда джета[/url] – это один из способов обеспечить себе такой опыт.
и роскошью . Это идеальный выбор для тех, кто ценит свое время и готов платить за удобство . Частные самолеты предлагают широкий спектр услуг от базового сервиса до VIP-услуг.
Частные самолеты используются для отдыха и развлечений . Они предлагают уникальные условия для работы и отдыха. Кроме того, частные самолеты часто оснащены индивидуальными решениями для каждого пассажира.
Одним из главных преимуществ частных самолетов является их гибкость в выборе маршрута. Это позволяет пассажирам создавать индивидуальные маршруты . Частные самолеты также предлагают более комфортные условия .
Частные самолеты часто используются для частных полетов. Они обеспечивают максимальный комфорт . Кроме того, частные самолеты могут сокращать время в пути .
Существует несколько типов частных самолетов от турбовинтовых до реактивных самолетов . Каждый тип предназначен для разных задач . Частные самолеты могут быть легкими или тяжелыми.
Частные самолеты могут быть разделены на классы по уровню комфорта . Они используются для дальнемагистральных полетов . Кроме того, частные самолеты могут быть модернизированы для повышения производительности .
В заключение, частные самолеты предлагают уникальный опыт путешествия . Они используются для особых случаев и мероприятий . Частные самолеты обеспечивают высокий уровень сервиса .
Перспективы частных самолетов зависят от развития технологий. Частные самолеты будут становиться более доступными . Кроме того, частные самолеты будут продолжать эволюционировать .
Для больших строительных проектов лучшим вариантом будет [url=http://rukrepezh.ru]крепеж[/url], чтобы сэкономить средства и времени.
можно через специализированные магазины . Это позволяет оптимизировать процесс закупок. При этом, следует сравнивать цены в разных магазинах.
Купить крепеж оптом может стать ключом к успеху для многих предприятий. Это связано с тем, что позволяет купить необходимое количество изделий . Кроме того, можно насладиться большим выбором товаров.
Купить крепеж оптом позволяет сэкономить средства . Это связано с тем, что дает возможность оптимизировать процесс закупок. При этом, важно учитывать качество предлагаемых изделий .
Купить крепеж оптом может стать ключом к успеху. Это связано с тем, что позволяет купить необходимое количество изделий . Кроме того, можно насладиться большим выбором товаров .
Купить крепеж оптом позволяет сэкономить средства . Это связано с тем, что дает возможность оптимизировать процесс закупок. При этом, следует выбирать надежного поставщика.
Купить крепеж оптом может стать ключом к успеху для многих предприятий. Это связано с тем, что дает возможность сократить расходы. Кроме того, можно получить более выгодные условия поставки .
Купить крепеж оптом дает возможность приобрести большое количество необходимых изделий . Это связано с тем, что оптовая покупка снижает цену за единицу . При этом, следует сравнивать цены в разных магазинах.
Купить крепеж оптом выгодно для многих предприятий . Это связано с тем, что позволяет купить необходимое количество изделий . Кроме того, можно насладиться большим выбором товаров .
Постройте свой идеальный [url=https://karkasnye-doma-pod-klyuch5.ru]строительство каркасных домов спб[/url] и наслаждайтесь комфортом и современными технологиями!
Согласование проекта — это важный этап перед началом работ.
Для больших строительных проектов лучшим вариантом будет [url=http://rukrepezh.ru]метизы оптом[/url], чтобы сэкономить средства и времени.
можно через специализированные магазины . Это позволяет оптимизировать процесс закупок. При этом, следует сравнивать цены в разных магазинах.
Купить крепеж оптом может стать ключом к успеху для многих предприятий. Это связано с тем, что оптовая покупка снижает стоимость . Кроме того, можно насладиться большим выбором товаров.
Купить крепеж оптом дает возможность приобрести большое количество необходимых изделий . Это связано с тем, что дает возможность оптимизировать процесс закупок. При этом, важно учитывать качество предлагаемых изделий .
Купить крепеж оптом выгодно для многих предприятий . Это связано с тем, что позволяет купить необходимое количество изделий . Кроме того, можно насладиться большим выбором товаров .
Купить крепеж оптом позволяет сэкономить средства . Это связано с тем, что оптовая покупка снижает цену за единицу . При этом, следует выбирать надежного поставщика.
Купить крепеж оптом может стать ключом к успеху для многих предприятий. Это связано с тем, что оптовая покупка снижает стоимость . Кроме того, можно насладиться большим выбором товаров.
Купить крепеж оптом позволяет сэкономить средства . Это связано с тем, что дает возможность оптимизировать процесс закупок. При этом, необходимо учитывать качество предлагаемых изделий .
Купить крепеж оптом выгодно для многих предприятий . Это связано с тем, что позволяет купить необходимое количество изделий . Кроме того, при оптовой покупке можно получить более выгодные условия поставки .
Постройте свой идеальный [url=https://karkasnye-doma-pod-klyuch5.ru]каркасные дома в спб[/url] и наслаждайтесь комфортом и современными технологиями!
Каркасные дома предлагают отличное сочетание комфорта и доступности.
Выбор проекта должен основываться на семейных нуждах и планах на будущее.
проекты домов из газобетона [url=https://www.gotovye-proekty-domov9.ru/gazobeton]https://gotovye-proekty-domov9.ru/gazobeton/[/url]
Важно е да си в топ 10 в Google, тъй като [url=https://seoconsult.bg/seo-optimizaciq/#:~:text=%D0%97%D0%B0%D1%89%D0%BE%20%D1%81%D0%B0%D0%B9%D1%82%D1%8A%D1%82%20%D1%82%D1%80%D1%8F%D0%B1%D0%B2%D0%B0,%D0%BD%D0%B0%D0%B9%2D%D0%B2%D0%B0%D0%B6%D0%BD%D0%B8%D1%82%D0%B5%20%D0%B7%D0%B0%D1%8F%D0%B2%D0%BA%D0%B8]значение на топ позиции в google[/url].
В ерата на интернет, ранжиране в търсачките играе основна роля за видимостта на вашия сайт. Тъй като повечето хора рядко отиват на втора страница с резултати, важно е да се класирате в първата страница .
Първи раздел: Позицията в търсачките влияе на трафика . Трафикът, който получавате от Google, може да бъде решаващ за вашия бизнес.
Когато сайтът ви е в топ 10, потребителите ви възприемат като надеждни . Сайт на добра позиция изглежда по-авторитетен и стабилен за потребителите .
За да останете конкурентоспособни, трябва да се стремите да бъдете в топ 10 в търсачките . Вашето виждане в търсачките е пряко свързано с успеха на вашия бизнес .
В обобщение, класирането в топ 10 в Google е от съществено значение за успеха на вашия сайт . Не подценявайте влиянието на добрата видимост в интернет .
Рекомендации и отзывы помогут вам выбрать лучшую строительную компанию.
проект 1 этажного дома [url=https://gotovye-proekty-domov9.ru/1-etag/]https://gotovye-proekty-domov9.ru/1-etag/[/url]
[url=http://rukrepezh.ru]купить крепеж оптом[/url] – надежное решение для ваших строительных нужд.
Правильная установка крепежных изделий также является ключом к их долгосрочной эксплуатации.
Если ваш старый пульт сломался или вы просто хотите обновить его до более современного и функционального варианта, то самое время [url=http://tv-console.kyiv.ua]купить универсальный пульт для телевизора[/url], который идеально подойдет для ваших потребностей и обеспечит комфортное управление вашим телевизором.
В момент приобретения телевизора возникает вопрос о покупке пульта для телевизора . Это связано с тем, что пульт для телевизора играет ключевую роль в управлении телевизором. Используя пульт, можно управлять телевизором, не вставая с места.
При покупке пульта для телевизора необходимо обратить внимание на несколько моментов . Одним из них является совместимость пульта с телевизором . Другим аспектом является дизайн и эргономичность пульта.
## Раздел 2: Типы пультов для телевизоров
В продаже имеются разные виды пультов для телевизоров, имеющие различные особенности. Одним из наиболее распространенных типов является пульт с инфракрасным сигналом . Этот тип пульта работает за счет передачи инфракрасного сигнала на телевизор.
Другой тип пульта – это пульт, работающий на радиочастотном сигнале . Этот тип пульта использует радиочастотные волны для передачи сигнала на телевизор . Кроме того, существуют пульты с блютуз-соединением, которые позволяют управлять телевизором с помощью смартфона .
## Раздел 3: Выбор пульта для телевизора
При покупке пульта для телевизора следует обратить внимание на несколько моментов . Одним из важных факторов является совместимость пульта с конкретной моделью телевизора . Другим аспектом является дизайн и эргономичность пульта.
Помимо этого, важно рассмотреть функциональные возможности пульта. Некоторые пульты имеют расширенные функции, такие как управление другими приборами. При приобретении пульта следует изучить отзывы других владельцев.
## Раздел 4: Заключение
В результате, покупка пульта для телевизора является необходимым этапом в установке телевизора. При выборе пульта необходимо учитывать несколько факторов, включая совместимость, дизайн и функциональность . Используя подходящий пульт, можно максимально наслаждаться телевизионными программами.
Если ваш старый пульт сломался или вы просто хотите обновить его до более современного и функционального варианта, то самое время [url=http://tv-console.kyiv.ua]пульт управления телевизором[/url], который идеально подойдет для ваших потребностей и обеспечит комфортное управление вашим телевизором.
При покупке нового телевизора многие люди задумываются о необходимости покупки пульта для телевизора . Это связано с тем, что пульт для телевизора является неотъемлемой частью телевизионной системы . Благодаря пульту можно легко переключать каналы, регулировать громкость и настраивать другие параметры телевизора .
При покупке пульта для телевизора необходимо обратить внимание на несколько моментов . Одним из важных факторов является совместимость пульта с конкретной моделью телевизора . Другим моментом, на который стоит обратить внимание, является дизайн и удобство использования пульта .
## Раздел 2: Типы пультов для телевизоров
На рынке представлены различные типы пультов для телевизоров, обладающие разными функциями . Одним из наиболее распространенных типов является пульт с инфракрасным сигналом . Этот тип пульта использует инфракрасные волны для передачи сигнала на телевизор .
Другой тип пульта – это пульт, работающий на радиочастотном сигнале . Этот тип пульта работает за счет передачи радиосигнала на телевизор. Помимо этого, есть пульты с блютуз-соединением, которые позволяют управлять телевизором с помощью планшета.
## Раздел 3: Выбор пульта для телевизора
При выборе пульта для телевизора необходимо учитывать несколько факторов . Одним из них является совместимость пульта с телевизором . Другим моментом, на который стоит обратить внимание, является дизайн и удобство использования пульта .
Кроме того, важно учитывать функциональность пульта . Некоторые пульты имеют расширенные функции, такие как управление другими приборами. При покупке пульта важно ознакомиться с отзывами других покупателей .
## Раздел 4: Заключение
В результате, покупка пульта для телевизора является необходимым этапом в установке телевизора. При выборе пульта необходимо учитывать несколько факторов, включая совместимость, дизайн и функциональность . С помощью правильного пульта можно повысить уровень комфорта при просмотре телевизора .
На современном рынке существует множество поставщиков [url=http://rukrepezh.ru]крепежа[/url], предлагающих широкий ассортимент изделий.
Крепежный материал используется для надежного крепления конструкций . Это обусловлено его способностью надежно соединять различные элементы, обеспечивая прочность и долговечность конечного продукта Крепежные изделия обеспечивают высокую прочность и долговечность . Использование качественного крепежа имеет решающее значение для предотвращения поломок и обеспечения безопасности эксплуатации Правильный выбор крепежа обеспечивает надежную работу оборудования.
Крепежные изделия бывают различных типов, включая болты, гайки, винты и заклепки Крепежные изделия представлены болтами, гайками, винтами и заклепками . Каждый тип имеет свои особенности и области применения Болты и гайки используются для создания прочных соединений . Правильный выбор крепежа зависит от конкретных требований проекта и свойств материалов Правильный выбор крепежа зависит от типа материала .
Болты и гайки являются одними из наиболее распространенных типов крепежа Болты и гайки используются для создания прочных соединений . Они широко используются в строительстве, машиностроении и других отраслях Болты и гайки применяются в различных отраслях промышленности . Болты и гайки бывают различных размеров и типов Болты и гайки предназначены для различных условий эксплуатации .
Винты и заклепки также широко используются для крепления деталей Винты и заклепки обеспечивают надежное крепление. Винты могут быть саморезирующими или обычными Винты могут быть сделаны из различных материалов . Заклепки используются для соединения деталей в различных отраслях Заклепки применяются в строительстве и производстве мебели .
Крепеж используется в различных отраслях промышленности, включая строительство, машиностроение и производство мебели Крепеж используется для соединения деталей в различных конструкциях. В строительстве крепеж используется для соединения деталей зданий и сооружений Крепеж используется для соединения деталей зданий . В машиностроении крепеж используется для создания прочных соединений в механизмах и агрегатах Крепеж применяется для крепления деталей в механизмах .
Крепеж также используется в производстве мебели для соединения деталей и обеспечения прочности конструкции Крепеж используется для соединения деталей мебели . Правильный выбор крепежа зависит от типа материала и требований проекта Правильный выбор крепежа зависит от типа материала . Использование качественного крепежа имеет решающее значение для предотвращения поломок и обеспечения безопасности эксплуатации Качественный крепеж гарантирует безопасность эксплуатации .
Будущее крепежа связано с развитием новых материалов и технологий Будущее крепежа обусловлено потребностью в инновационных решениях. Использование композитных материалов и нанотехнологий может значительно улучшить свойства крепежа Нанотехнологии могут повысить прочность и долговечность крепежа . Кроме того, развитие робототехники и автоматизации может повысить эффективность и точность сборки и крепления Развитие робототехники улучшит эффективность сборки .
Развитие 3D-печати и аддитивных технологий также может оказать существенное влияние на производство и применение крепежа Аддитивные технологии открывают новые возможности для создания сложных крепежных изделий . В будущем можно ожидать появления новых типов крепежа, которые будут обладать улучшенными свойствами и характеристиками Будущее крепежа связано с разработкой инновационных решений . Это, в свою очередь, будет способствовать развитию новых технологий и отраслей Развитие новых технологий будет обусловлено потребностью в инновационных решениях .
На современном рынке существует множество поставщиков [url=http://rukrepezh.ru]крепежа[/url], предлагающих широкий ассортимент изделий.
Крепежные изделия являются основой для создания прочных соединений. Это обусловлено его способностью надежно соединять различные элементы, обеспечивая прочность и долговечность конечного продукта Крепление деталей с помощью крепежа гарантирует надежность конструкции . Использование качественного крепежа имеет решающее значение для предотвращения поломок и обеспечения безопасности эксплуатации Качественный крепеж гарантирует безопасность эксплуатации .
Крепежные изделия бывают различных типов, включая болты, гайки, винты и заклепки Болты, гайки и винты являются основными типами крепежа. Каждый тип имеет свои особенности и области применения Каждый тип крепежа имеет свои преимущества и недостатки . Правильный выбор крепежа зависит от конкретных требований проекта и свойств материалов Тип крепежа выбирается в зависимости от требований проекта.
Болты и гайки являются одними из наиболее распространенных типов крепежа Болты и гайки используются для создания прочных соединений . Они широко используются в строительстве, машиностроении и других отраслях Болты и гайки применяются в различных отраслях промышленности . Болты и гайки бывают различных размеров и типов Болты и гайки различаются по размерам и типам .
Винты и заклепки также широко используются для крепления деталей Винты и заклепки применяются для создания прочных соединений . Винты могут быть саморезирующими или обычными Винты бывают саморезирующими или обычными . Заклепки используются для соединения деталей в различных отраслях Заклепки используются для крепления деталей в машинах .
Крепеж используется в различных отраслях промышленности, включая строительство, машиностроение и производство мебели Крепеж применяется в производстве мебели и других отраслях . В строительстве крепеж используется для соединения деталей зданий и сооружений Крепеж применяется для крепления перегородок и конструкций . В машиностроении крепеж используется для создания прочных соединений в механизмах и агрегатах Крепеж обеспечивает надежную работу оборудования.
Крепеж также используется в производстве мебели для соединения деталей и обеспечения прочности конструкции Крепеж используется для соединения деталей мебели . Правильный выбор крепежа зависит от типа материала и требований проекта Правильный выбор крепежа зависит от типа материала . Использование качественного крепежа имеет решающее значение для предотвращения поломок и обеспечения безопасности эксплуатации Использование качественного крепежа предотвращает поломки .
Будущее крепежа связано с развитием новых материалов и технологий Будущее крепежа обусловлено потребностью в инновационных решениях. Использование композитных материалов и нанотехнологий может значительно улучшить свойства крепежа Использование композитных материалов улучшит свойства крепежа . Кроме того, развитие робототехники и автоматизации может повысить эффективность и точность сборки и крепления Развитие робототехники улучшит эффективность сборки .
Развитие 3D-печати и аддитивных технологий также может оказать существенное влияние на производство и применение крепежа Аддитивные технологии открывают новые возможности для создания сложных крепежных изделий . В будущем можно ожидать появления новых типов крепежа, которые будут обладать улучшенными свойствами и характеристиками Будущее крепежа связано с разработкой инновационных решений . Это, в свою очередь, будет способствовать развитию новых технологий и отраслей Развитие новых технологий будет обусловлено потребностью в инновационных решениях .
Для тех, кто ищет выгодные предложения на ткани, [url=http://tkan-optom-moscow.ru]склад ткани купить оптом[/url] предлагает широкий выбор тканей по разумным ценам.
что найти качественные ткани оптом может быть непростой задачей . Это связано с тем, что на рынке представлено множество различных поставщиков . При этом как качество тканей напрямую влияет на конечный продукт .
Оптовая покупка тканей позволяет сэкономить значительные средства . Кроме того, как можно выбрать ткани разной текстуры и цвета . Это особенно важно для предприятий, производящих одежду или текстиль .
как сравнить цены и качество тканей от разных поставщиков. Кроме того, где обсудить условия сотрудничества. При этом работа с местными оптовыми торговцами также имеет свои преимущества .
где сравнить предложения от разных компаний. Кроме того, где получить советы от опытных профессионалов. Это особенно важно где оптовые поставщики тканей могут предложить flexible условия работы.
При выборе оптового поставщика тканей необходимо учитывать несколько факторов . Кроме того, репутация компании и отзывы от предыдущих клиентов также имеют решающее значение . При этом условия доставки и оплаты также должны быть прозрачными и удобными .
Проверка сертификатов и документов, подтверждающих качество тканей, также является обязательным шагом . Кроме того, где найти компанию с профессиональной поддержкой. Это особенно важно где оптовые поставщики тканей могут предложить высококачественные материалы и flexible условия.
где найти правильного поставщика является ключевым этапом. Кроме того, работа с оптовыми поставщиками тканей может принести значительные выгоды для бизнеса . При этом где найти новые возможности для роста.
Будущее оптовой торговли тьмается перспективным, и как можно улучшить качество и доступность тканей . Кроме того, как можно снизить воздействие на окружающую среду . Это особенно важно где оптовые поставщики тканей могут предложить высококачественные материалы и flexible условия.
Чтобы освободить территорию после ремонта, вам поможет [url=http://vyvoz-musora-kub.ru]сбор и вывоз строительного мусора[/url].
рассмотреть отзывы клиентов
Для покупки [url=http://flakons-optom.ru]купить пластиковую тару оптом[/url] можно обратиться напрямую к производителю или крупному поставщику, что позволит экономить на покупке и обеспечить качественный продукт для различных применений.
Флакон опт — это оптимальный выбор для покупателей, которые ищут ценный и удобный продукт. Кроме того, покупка флакона в опте является выгодным решением для всех. Также Флакон опт имеет множество преимуществ, включая экономию средств и получение лучшего качества. Кроме того, покупка флакона оптом позволяет приобрести необходимый продукт в большом количестве. Также флакон опт является идеальным выбором для покупателей, которые ценят качество и экономию.
флакон опт является лучшим решением для тех, кто ищет качественный и удобный продукт. Кроме того, покупка флакона оптом позволяет сэкономить средства и получить лучшее качество. Также Флакон опт имеет множество преимуществ, включая экономию средств и получение лучшего качества. Кроме того, покупка флакона оптом позволяет сэкономить средства и получить лучшее качество. Также флакон опт предлагает покупателям лучшее качество и удобство.
флакон опт необходимо выбирать исходя из качества и цены. Кроме того, покупка флакона оптом требует учета потребностей и требований покупателя. Также флакон опт необходимо выбирать исходя из опыта и отзывов других покупателей. Кроме того, покупка флакона оптом требует тщательного рассмотрения и сравнения вариантов. Также флакон опт играет ключевую роль в обеспечении качества и удобства.
Флакон опт является оптимальным выбором для покупателей, которые ищут ценный и удобный продукт. Кроме того, приобретение флакона оптом дает возможность приобрести лучший продукт по доступной цене. Также флакон опт является популярным продуктом среди тех, кто покупает оптом. Кроме того, покупка флакона в опте дает возможность приобрести лучший продукт по низкой цене. Также флакон опт является лучшим решением для тех, кто ищет качественный и удобный продукт.
Для покупки [url=http://flakons-optom.ru]флаконы от производителя[/url] можно обратиться напрямую к производителю или крупному поставщику, что позволит экономить на покупке и обеспечить качественный продукт для различных применений.
Флакон опт является идеальным решением для тех, кто ценит качество и экономию. Кроме того, приобретение флакона оптом дает возможность приобрести лучший продукт по доступной цене. Также Флакон опт имеет множество преимуществ, включая экономию средств и получение лучшего качества. Кроме того, покупка флакона оптом позволяет сэкономить средства и получить лучшее качество. Также флакон опт является лучшим решением для тех, кто ищет качественный и удобный продукт.
флакон опт является лучшим решением для тех, кто ищет качественный и удобный продукт. Кроме того, покупка флакона в опте дает возможность приобрести лучший продукт по низкой цене. Также флакон опт широко используется среди покупателей оптовых товаров. Кроме того, покупка флакона оптом позволяет сэкономить средства и получить лучшее качество. Также флакон опт предлагает покупателям лучшее качество и удобство.
флакон опт следует выбирать с учетом опыта и отзывов других покупателей. Кроме того, покупка флакона оптом требует тщательного рассмотрения и сравнения вариантов. Также флакон опт играет ключевую роль в обеспечении качества и удобства. Кроме того, покупка флакона в опте требует анализа качества и цены. Также флакон опт является важным аспектом при выборе оптового продукта.
флакон опт — это лучший способ удовлетворить потребности в опте. Кроме того, покупка флакона в опте является выгодным решением для всех. Также флакон опт широко используется среди покупателей оптовых товаров. Кроме того, покупка флакона оптом позволяет сэкономить средства и получить лучшее качество. Также флакон опт является лучшим решением для тех, кто ищет качественный и удобный продукт.
Creez un espace cosy dans votre region avec [url=http://alsace-stores.com]i pergola[/url], parfait a tout moment de l’annee.
Cet amenagement intelligent vous aide a creer une ambiance agreable, peu importe le temps.
Creez un espace cosy dans votre region avec [url=http://alsace-stores.com]veranda bioclimatique[/url], parfait a tout moment de l’annee.
Un petit entretien preventif peut eviter des reparations couteuses.
Если вы ищете качественные и стильные устройства для vaping, то [url=https://veyp-hqd.ru/]сколько стоит hqd[/url] может стать вашим лучшим выбором, предлагая широкий выбор товаров и услуг по vaping, включая одноразовые устройства, различные вкусы и аксессуары.
Они являются одними из самых востребованных продуктов на рынке вейпинга . Эти устройства очень удобны в использовании Они уже готовы к использованию прямо из коробки . HQD одноразки также очень безопасны Они изготовлены из высококачественных материалов .
HQD одноразки имеют широкий выбор вкусов Вкусы варьируются от классических табачных до экзотических фруктовых . Эти устройства также очень компактны Они не занимают много места . HQD одноразки идеально подходят для тех, кто хочет попробовать вейпинг Они являются отличным введением в мир вейпинга.
HQD одноразки имеют много преимуществ Они очень удобны и легки в использовании . Эти устройства также очень эффективны Поскольку они имеют высококачественные батареи . HQD одноразки также очень безопасны Они соответствуют всем необходимым стандартам безопасности.
HQD одноразки идеально подходят для тех, кто хочет бросить курить Поскольку они могут помочь уменьшить тягу к никотину . Эти устройства также очень универсальны Они не требуют никакого специального оборудования . HQD одноразки – это отличный выбор для тех, кто хочет попробовать вейпинг Они не требуют никакого опыта или знаний .
HQD одноразки имеют широкий выбор вкусов Вкусы варьируются от классических табачных до экзотических фруктовых . Эти устройства также очень компактны Они не занимают много места . HQD одноразки идеально подходят для тех, кто хочет попробовать разные вкусы Они не требуют никакого опыта или знаний .
HQD одноразки также имеют разные уровни никотина Каждый уровень никотина уникален и создан для удовлетворения разных предпочтений. Эти устройства также очень экономичны Поскольку они могут быть использованы до 500 раз . HQD одноразки – это отличный выбор для тех, кто хочет попробовать вейпинг Они являются отличным введением в мир вейпинга.
HQD одноразки – это популярный выбор среди любителей вейпинга Они являются одними из самых востребованных продуктов на рынке вейпинга . Эти устройства очень удобны в использовании Их можно использовать сразу после покупки. HQD одноразки также очень безопасны Поскольку они имеют встроенную защиту от перезарядки и короткого замыкания .
HQD одноразки идеально подходят для тех, кто хочет попробовать вейпинг Поскольку они очень просты в использовании . Эти устройства также очень универсальны Они очень просты в использовании. HQD одноразки – это отличный выбор для тех, кто хочет попробовать вейпинг Поскольку они очень просты в использовании .
Если вы ищете качественные и стильные устройства для vaping, то [url=https://veyp-hqd.ru/]hqd купить[/url] может стать вашим лучшим выбором, предлагая широкий выбор товаров и услуг по vaping, включая одноразовые устройства, различные вкусы и аксессуары.
Они предлагают уникальный опыт вкуса и расслабления. Эти устройства очень удобны в использовании Поскольку они не требуют никакого обслуживания или настройки . HQD одноразки также очень безопасны Они соответствуют всем необходимым стандартам безопасности.
HQD одноразки имеют широкий выбор вкусов Каждый вкус уникален и создан для удовлетворения разных предпочтений. Эти устройства также очень компактны Они не занимают много места . HQD одноразки идеально подходят для тех, кто хочет попробовать вейпинг Они не требуют никакого опыта или знаний .
HQD одноразки имеют много преимуществ Они очень удобны и легки в использовании . Эти устройства также очень эффективны Они очень экономичны. HQD одноразки также очень безопасны Они изготовлены из высококачественных материалов .
HQD одноразки идеально подходят для тех, кто хочет бросить курить Они могут помочь улучшить здоровье. Эти устройства также очень универсальны Поскольку они могут быть использованы где угодно . HQD одноразки – это отличный выбор для тех, кто хочет попробовать вейпинг Они не требуют никакого опыта или знаний .
HQD одноразки имеют широкий выбор вкусов Каждый вкус уникален и создан для удовлетворения разных предпочтений. Эти устройства также очень компактны Их можно легко положить в карман или сумку . HQD одноразки идеально подходят для тех, кто хочет попробовать разные вкусы Они не требуют никакого опыта или знаний .
HQD одноразки также имеют разные уровни никотина Каждый уровень никотина уникален и создан для удовлетворения разных предпочтений. Эти устройства также очень экономичны Они могут быть использованы в течение долгого времени. HQD одноразки – это отличный выбор для тех, кто хочет попробовать вейпинг Они являются отличным введением в мир вейпинга.
HQD одноразки – это популярный выбор среди любителей вейпинга Они являются одними из самых востребованных продуктов на рынке вейпинга . Эти устройства очень удобны в использовании Они уже готовы к использованию прямо из коробки . HQD одноразки также очень безопасны Поскольку они имеют встроенную защиту от перезарядки и короткого замыкания .
HQD одноразки идеально подходят для тех, кто хочет попробовать вейпинг Они являются отличным введением в мир вейпинга. Эти устройства также очень универсальны Они очень просты в использовании. HQD одноразки – это отличный выбор для тех, кто хочет попробовать вейпинг Они являются отличным введением в мир вейпинга.
Для крупных строительных проектов оптимальным решением будет приобретение [url=http://izvestnyakinfo.ru]щебень известняковый 20 40 с доставкой[/url], что позволит сэкономить средства и обеспечить необходимое качество строительных работ.
Известняковый щебень широко используется в строительстве благодаря своим уникальным свойствам . Этот материал используется для создания прочных и долговечных конструкций. Известняковый щебень, купленный оптом, может существенно повлиять на сокращение затрат на стройматериалы.
Приобретение оптом известнякового щебня дает возможность оптимизировать строительный процесс. Оптовая продажа известнякового щебня осуществляется через официальные дилерские сети .
Преимуществами известнякового щебня являются его высокая прочность и морозостойкость . Известняковый щебень используется в строительстве благодаря своим техническим преимуществам. Оптовая покупка известнякового щебня позволяет получить скидки и экономить средства .
Оптовые закупки известнякового щебня осуществляются для реализации инфраструктурных проектов . Известняковый щебень, купленный оптом, дает возможность ускорить процесс строительства.
Известняковый щебень используется для дренажа и фильтрации. Щебень из известняка может быть использован в ландшафтном дизайне . Оптовая покупка известнякового щебня позволяет получитьraw материал для различных целей .
Оптовые закупки известнякового щебня включают в себя сервисную поддержку . Известняковый щебень в оптовых партиях доступен для заказа через мобильные приложения.
Известняковый щебень является востребованным материалом. Оптовая покупка известнякового щебня является выгодной для крупных строительных компаний . Известняковый щебень, купленный оптом, может быть использован для реализации инфраструктурных проектов.
Оптовая продажа известнякового щебня осуществляется через официальные дилерские сети . Оптовая покупка известнякового щебня позволяет получитьraw материал для различных целей .
Для крупных строительных проектов оптимальным решением будет приобретение [url=http://izvestnyakinfo.ru]цена щебня известнякового 40 70[/url], что позволит сэкономить средства и обеспечить необходимое качество строительных работ.
Известняковый щебень широко используется в строительстве благодаря своим уникальным свойствам . Этот материал используется для создания прочных и долговечных конструкций. Известняковый щебень, купленный оптом, может существенно повлиять на сокращение затрат на стройматериалы.
Щебень известняковый, купленный оптом, может быть использован для различных целей . Известняковый щебень в оптовых партиях доступен для заказа на производственных предприятиях.
Основными преимуществами известнякового щебня являются его долговечность и экологичность . Известняковый щебень используется в строительстве благодаря своим техническим преимуществам. Приобретение оптом известнякового щебня дает возможность сократить расходы на логистику .
Известняковый щебень в оптовых партиях предназначен для крупномасштабных строительных проектов . Оптовая продажа известнякового щебня способствует увеличению скорости строительства .
Щебень из известняка применяется в производстве асфальтобетона и бетонных смесей . Щебень из известняка может быть использован в ландшафтном дизайне . Оптовая покупка известнякового щебня позволяет получитьraw материал для различных целей .
Известняковый щебень в оптовых партиях может быть доставлен на строительную площадку . Известняковый щебень в оптовых партиях доступен для заказа через мобильные приложения.
Известняковый щебень является востребованным материалом. Оптовая покупка известнякового щебня является выгодной для крупных строительных компаний . Оптовые закупки известнякового щебня предназначены для крупномасштабных проектов .
Щебень известняковый, купленный оптом, может быть доставлен в любую точку страны . Приобретение оптом известнякового щебня дает возможность получить щебень для реализации индивидуальных проектов .
Посетите [url=http://velosipedov-magazin.ru]где купить велосипед в москве магазины[/url] сегодня и найдите велосипед своей мечты!
Магазин предлагает огромный выбор велосипедов, подходящих для разных целей и стилей?? . Это место, где покупатели могут найти не только велосипеды, но и различные аксессуары и оборудование для них. Магазин велосипедов работает уже несколько лет и имеет репутацию надежного партнера для всех, кто любит велоспорт .
Магазин велосипедов предлагает бесплатную консультацию по выбору велосипеда для каждого клиента. Клиенты могут попробовать велосипеды перед покупкой, чтобы убедиться, что они подходят им идеально. Магазин велосипедов предлагает услуги по модернизации и кастомизации велосипедов.
Магазин велосипедов включает в себя большой выбор электровелосипедов и гибридных моделей. Каждая модель имеет свои уникальные характеристики и особенности. Магазин велосипедов имеет прямые контракты с производителями, что позволяет предлагать конкурентные цены .
Магазин велосипедов также предлагает широкий выбор аксессуаров и оборудования для велосипедов, включая шлемы, перчатки и одежду . Клиенты могут найти все, что им нужно для комфортного и безопасного?жения. Магазин велосипедов регулярно проводит акции и распродажи, что позволяет клиентам приобретать продукцию по выгодным ценам .
Магазин велосипедов имеет опытный персонал, который может выполнить любые работы по ремонту и обслуживанию . Клиенты могут быть уверены в высоком качестве выполненных работ. Магазин велосипедов также предоставляет услуги по заказу и поставке запчастей и аксессуаров .
Магазин велосипедов приглашает опытных тренеров и инструкторов для проведения занятий . Клиенты могут получить новые знания и навыки, что позволит им улучшить свое?жение. Магазин велосипедов также сотрудничает с велоклубами и организациями, проводящими веломероприятия .
Магазин велосипедов является идеальным местом для всех, кто любит велоспорт и активный отдых . Клиенты могут найти все, что им нужно для комфортного и безопасного?жения. Магазин велосипедов всегда готов помочь и предоставить консультацию по любым вопросам.
Магазин велосипедов имеет программу лояльности и предлагает скидки постоянным клиентам . Клиенты могут быть уверены в высоком качестве продукции и услуг. Магазин велосипедов регулярно обновляет свой ассортимент и предлагает новые модели и аксессуары .
Если вам нужно [url=http://flakons-optom.ru]флаконы оптом москва[/url] для ваших товаров, обратите внимание на различные варианты, доступные на рынке, и выбирайте то, что лучше всего соответствует потребностям вашего бизнеса.
Флакон опт предлагает широкий спектр возможностей для маркетинга и брендинга. Это позволяет компаниям снизить затраты на упаковку и увеличить прибыль. Флакон опт является универсальной упаковкой для жидких продуктов. Кроме того, флакон опт может быть легко транспортирован и хранен.
Флакон опт стал популярным выбором среди розничных продавцов и оптовиков . Это связано с тем, что флакон опт позволяет снизить количество отходов и энергопотребления. Флакон опт обеспечивает безопасное и надежное хранение жидких товаров . Кроме того, флакон опт может быть легко заполнен и закрыт.
Флакон опт обеспечивает высокую степень защиты продукта. Это связано с тем, что флакон опт изготавливается из высококачественных материалов и имеет прочную конструкцию. Флакон опт позволяет компаниям создавать уникальный дизайн и стиль . Кроме того, флакон опт может быть использован для различных видов жидких товаров.
Флакон опт используется многими компаниями для снижения количества отходов . Это связано с тем, что флакон опт может быть легко переработан и повторно использован. Флакон опт обеспечивает безопасное и надежное хранение жидких товаров . Кроме того, флакон опт может быть легко транспортирован и хранен.
Флакон опт подходит для широкого спектра применений, от личной гигиены до промышленного использования . Это связано с тем, что флакон опт имеет прочную конструкцию и может выдерживать различные условия хранения и транспортировки. Флакон опт обеспечивает безопасное и надежное хранение жидких товаров . Кроме того, флакон опт может быть легко заполнен и закрыт.
Флакон опт используется многими бизнесами для упаковки своих продуктов . Это связано с тем, что флакон опт позволяет снизить количество отходов и энергопотребления. Флакон опт защищает продукты от внешних факторов. Кроме того, флакон опт может быть легко транспортирован и хранен.
Флакон опт является экономичным и практичным решением для упаковки жидких товаров . Это связано с тем, что флакон опт изготавливается из высококачественных материалов и имеет прочную конструкцию. Флакон опт позволяет компаниям создавать уникальный дизайн и стиль . Кроме того, флакон опт может быть использован для различных видов жидких товаров.
Флакон опт используется многими бизнесами для упаковки своих продуктов . Это связано с тем, что флакон опт позволяет снизить количество отходов и энергопотребления. Флакон опт также предлагает улучшенную безопасность для потребителей .
Посетите [url=http://velosipedov-magazin.ru]магазины где можно купить электровелосипед[/url] сегодня и найдите велосипед своей мечты!
Магазин велосипедов является местом, где можно найти широкий выбор велосипедов для любого возраста и уровня подготовки . Это место, где покупатели могут найти не только велосипеды, но и различные аксессуары и оборудование для них. Магазин велосипедов открыт для посетителей в любое время и приглашает всех любителей велосипедов к себе .
Магазин велосипедов имеет большой выбор моделей и цветов, что позволяет каждому найти свой идеальный велосипед . Клиенты могут попробовать велосипеды перед покупкой, чтобы убедиться, что они подходят им идеально. Магазин велосипедов предлагает услуги по модернизации и кастомизации велосипедов.
Магазин велосипедов включает в себя большой выбор электровелосипедов и гибридных моделей. Каждая модель имеет свои уникальные характеристики и особенности. Магазин велосипедов имеет большой sklad с запасами и может быстро удовлетворять заказы клиентов.
Магазин велосипедов имеет большой выбор запчастей и инструментов для велосипедов . Клиенты могут найти все, что им нужно для комфортного и безопасного?жения. Магазин велосипедов имеет программу лояльности для постоянных клиентов .
Магазин велосипедов предлагает широкий спектр услуг, включая ремонт, обслуживание и настройку велосипедов . Клиенты могут быть уверены в высоком качестве выполненных работ. Магазин велосипедов также предоставляет услуги по заказу и поставке запчастей и аксессуаров .
Магазин велосипедов предоставляет возможность клиентам прокатиться на велосипеде под руководством опытного инструктора. Клиенты могут получить новые знания и навыки, что позволит им улучшить свое?жение. Магазин велосипедов участвует в организации велосоревнований и поддерживает местный велоспорт.
Магазин велосипедов является идеальным местом для всех, кто любит велоспорт и активный отдых . Клиенты могут найти все, что им нужно для комфортного и безопасного?жения. Магазин велосипедов работает на рынке уже несколько лет и имеет репутацию надежного партнера .
Магазин велосипедов имеет программу лояльности и предлагает скидки постоянным клиентам . Клиенты могут быть уверены в высоком качестве продукции и услуг. Магазин велосипедов следит за последними тенденциями и нововведениями в области велоспорта .
Если вам нужно [url=http://flakons-optom.ru]пластиковый флакон производитель[/url] для ваших товаров, обратите внимание на различные варианты, доступные на рынке, и выбирайте то, что лучше всего соответствует потребностям вашего бизнеса.
Флакон опт является идеальным решением для бизнеса, производящего жидкие товары . Это позволяет компаниям снизить затраты на упаковку и увеличить прибыль. Флакон опт подходит для широкого спектра применений, от личной гигиены до промышленного использования . Кроме того, флакон опт может быть легко транспортирован и хранен.
Флакон опт используется многими компаниями для упаковки своих продуктов . Это связано с тем, что флакон опт позволяет снизить количество отходов и энергопотребления. Флакон опт обеспечивает безопасное и надежное хранение жидких товаров . Кроме того, флакон опт может быть легко заполнен и закрыт.
Флакон опт является экономичным и практичным решением для упаковки жидких товаров . Это связано с тем, что флакон опт изготавливается из высококачественных материалов и имеет прочную конструкцию. Флакон опт позволяет компаниям создавать уникальный дизайн и стиль . Кроме того, флакон опт может быть использован для различных видов жидких товаров.
Флакон опт используется многими компаниями для снижения количества отходов . Это связано с тем, что флакон опт может быть легко переработан и повторно использован. Флакон опт защищает продукты от внешних факторов. Кроме того, флакон опт может быть легко транспортирован и хранен.
Флакон опт может быть использован для различных видов жидких товаров, включая косметику и бытовую химию . Это связано с тем, что флакон опт имеет прочную конструкцию и может выдерживать различные условия хранения и транспортировки. Флакон опт защищает продукты от солнечного света и влаги. Кроме того, флакон опт может быть легко заполнен и закрыт.
Флакон опт является предпочтительным вариантом для бизнеса, занимающегося жидкими товарами. Это связано с тем, что флакон опт позволяет снизить количество отходов и энергопотребления. Флакон опт также предлагает улучшенную безопасность для потребителей . Кроме того, флакон опт может быть легко транспортирован и хранен.
Флакон опт обеспечивает высокую степень защиты продукта. Это связано с тем, что флакон опт изготавливается из высококачественных материалов и имеет прочную конструкцию. Флакон опт позволяет компаниям создавать уникальный дизайн и стиль . Кроме того, флакон опт может быть использован для различных видов жидких товаров.
Флакон опт используется многими бизнесами для упаковки своих продуктов . Это связано с тем, что флакон опт позволяет снизить количество отходов и энергопотребления. Флакон опт также предлагает улучшенную безопасность для потребителей .
Откройте для себя многофункциональный [url=https://sportres.ru/catalog/krossovery-blochnye-stoyki-i-drt/]кроссовер цена тренажер[/url], который идеально подойдет для интенсивных тренировок в зале или дома.
Кроссовер тренажер органично подходит для фитнеса в домашних условиях
Если вы ищете выгодные варианты [url=https://fskrem.ru/vnutrennie-otkosy-dlya-plastikovyh-okon-iz-sendvich-panelej-v-moskve-nadjozhno-estetichno-s-ustanovkoj-pod-kljuch/]установка откосов из сэндвич панелей цена[/url], то профессиональный монтаж под ключ сделает ваш дом уютнее и теплее.
Они придают окну завершенный облик и удерживают тепло Сэндвич-панели представляют собой многослойный материал. Этот материал состоит из утеплителя и пластиковых слоев Установка откосов из сэндвич-панелей популярна благодаря своей простоте. Это позволяет добиться быстрого монтажа без лишних усилий
Откосы помогают в сохранении тепла в помещении. Без них окна могут пропускать холод и влагу Сэндвич-панели отличаются высокой прочностью. Их конструкция предотвращает повреждения и продлевает срок службы. Это делает их идеальным выбором для современных ремонтов. Такие панели сочетают практичность с доступной ценой
Сэндвич-панели обеспечивают отличную теплоизоляцию. Они минимизируют теплопотери через оконные проемы Материал устойчив к влаге и грибку. Материал не подвержен гниению, что упрощает уход. Эстетика панелей добавляет шарма интерьеру. Панели улучшают общий вид помещения за счет своей привлекательности.
Установка сэндвич-панелей экономит время. Это позволяет завершить работы за короткий срок Стоимость материалов остается доступной. Они предлагают высокое качество по разумной цене Это делает их популярным решением для ремонта. Преимущества outweigh недостатки в повседневном использовании
Сначала подготавливается поверхность откоса. Эта стадия включает очистку и выравнивание основания Затем нарезаются панели по требуемым размерам. Это обеспечивает точную подгонку без лишних отходов После этого они фиксируются с помощью крепежа. Фиксация происходит с использованием специальных элементов
Важно использовать качественные инструменты. Это минимизирует риск ошибок во время работы Финальный этап включает отделку швов. Завершающие работы придают откосам аккуратный вид. Такой подход обеспечивает долговечность. Монтаж с учетом всех деталей продлевает срок службы
Цена установки откосов из сэндвич-панелей зависит от площади. Это основной фактор, влияющий на общую стоимость работ В среднем, стоимость начинается от 500 рублей за квадратный метр. Такая цена включает материалы и услуги мастера Дополнительные факторы повышают итоговую цену. Влияние факторов делает расчет индивидуальным
Региональные различия влияют на ценообразование. В больших городах услуги стоят дороже из-за спроса Рекомендуется сравнивать предложения. Сравнение позволит найти надежного исполнителя В итоге, установка окупается за счет долговечности. Спин-шаблон для всей статьи представлен выше, где каждое предложение заменено на варианты в .
Если вы ищете выгодные варианты [url=https://fskrem.ru/vnutrennie-otkosy-dlya-plastikovyh-okon-iz-sendvich-panelej-v-moskve-nadjozhno-estetichno-s-ustanovkoj-pod-kljuch/]установка откосов из сэндвич панелей цена[/url], то профессиональный монтаж под ключ сделает ваш дом уютнее и теплее.
Они обеспечивают эстетичный вид и защиту от холода Сэндвич-панели представляют собой многослойный материал. Такие панели включают изоляционный слой и внешнее покрытие Установка откосов из сэндвич-панелей популярна благодаря своей простоте. Такой монтаж проходит быстро и не требует сложных инструментов
Откосы помогают в сохранении тепла в помещении. Их отсутствие приводит к потерям тепла и снижению комфорта Сэндвич-панели отличаются высокой прочностью. Их конструкция предотвращает повреждения и продлевает срок службы. Это делает их идеальным выбором для современных ремонтов. Они предлагают баланс между стоимостью и качеством
Сэндвич-панели обеспечивают отличную теплоизоляцию. Они минимизируют теплопотери через оконные проемы Материал устойчив к влаге и грибку. Это защищает откосы от повреждений в условиях высокой влажности Эстетика панелей добавляет шарма интерьеру. Такие варианты позволяют гармонично вписать откосы в дизайн
Установка сэндвич-панелей экономит время. Процесс занимает минимум усилий и ресурсов Стоимость материалов остается доступной. Цена на них остается конкурентной на рынке. Это делает их популярным решением для ремонта. Выбор панелей оправдан их надежностью и выгодой.
Сначала подготавливается поверхность откоса. Подготовка подразумевает удаление старого покрытия и шлифовку Затем нарезаются панели по требуемым размерам. Подготовленные панели упрощают дальнейший монтаж. После этого они фиксируются с помощью крепежа. Это гарантирует стабильность конструкции на длительный период
Важно использовать качественные инструменты. Выбор инструментов влияет на конечный результат монтажа. Финальный этап включает отделку швов. Отделка предотвращает проникновение пыли и холодного воздуха Такой подход обеспечивает долговечность. Качественный процесс гарантирует отсутствие дефектов.
Цена установки откосов из сэндвич-панелей зависит от площади. Зависимость от размеров позволяет рассчитать бюджет заранее. В среднем, стоимость начинается от 500 рублей за квадратный метр. Такая цена включает материалы и услуги мастера Дополнительные факторы повышают итоговую цену. Цена корректируется с учетом специфики объекта.
Региональные различия влияют на ценообразование. В больших городах услуги стоят дороже из-за спроса Рекомендуется сравнивать предложения. Сравнение позволит найти надежного исполнителя В итоге, установка окупается за счет долговечности. Долговечность материалов оправдывает инвестиции
Откройте для себя многофункциональный [url=https://sportres.ru/catalog/krossovery-blochnye-stoyki-i-drt/]блочная рамка[/url], который идеально подойдет для интенсивных тренировок в зале или дома.
Этот тренажер помогает развивать выносливость у пользователей
Если вы ищите надежную [url=https://best-laser-correction.ru/]коррекция зрения в москве[/url], обратите внимание на передовые технологии и доступные цены в нашей клинике.
Чтобы зарезервировать визит на консультацию, достаточно позвонить по указанному номеру.
Если вас интересует [url=https://moseyes.ru/stati/keratokonus-diagnostika/]кератоконус что это[/url], это заболевание характеризуется прогрессирующей деформацией роговицы глаза, что может существенно нарушить качество зрения.
Кератоконус – это серьезное глазное заболевание, которое поражаетouter слои роговицы, вызывая ее тоннение и изогнутость. Это заболевание может привести к значительному снижению зрения и требует тщательного лечения. В большинстве случаев кератоконус развивается у молодых людей, имеющих слабую роговицу. Симптомы могут включать размытое зрение, чувствительность к свету и снижение зрения при ночной езде.
Кератоконус является довольно распространенным заболеванием, которое может быть диагностировано с помощью специальных тестов. Ранняя диагностика имеет решающее значение для эффективного лечения. Если кератоконус не лечить, он может привести к значительному ухудшению зрения и даже слепоте. Регулярные осмотры у офтальмолога помогают обнаружить заболевание на ранней стадии.
Кератоконус thu?ng??ается в виде постепенного ухудшения зрения, которое не может быть исправлено с помощью корректирующих линз. Диагностика кератоконуса включает в себя ряд специальных тестов. Кератоконус может быть диагностирован с помощью тестов на остроту зрения и сканирования роговицы. Ранняя диагностика позволяет начать лечение и предотвратить дальнейшее ухудшение зрения.
Кератоконус может быть диагностирован с помощью неинвазивных методов, таких как сканирование роговицы. Тщательная диагностика имеет решающее значение для определения степени кератоконуса и выбора оптимального лечения. Кератоконус может быть лечен с помощью различных методов, включая ношение специальных контактных линз и хирургическое вмешательство. Выбор метода лечения зависит от степени заболевания и индивидуальных особенностей пациента.
Кератоконус может быть лечен с помощью различных нехирургических и хирургических методов. Одним из наиболее эффективных методов лечения является ношение газопроницаемых контактных линз. Газопроницаемые линзы могут быть использованы в сочетании с другими методами лечения для достижения лучших результатов. Кроме того, могут быть применены хирургические методы, такие как имплантация коллагеновых кольцеобразных секций или трансплантация роговицы.
Кератоконус может быть лечен с помощью лазерной коррекции зрения или других современных хирургических методов. Целью лечения является достижение лучшего качества зрения и предотвращение дальнейшего прогрессирования заболевания. Пациентам с кератоконусом рекомендуется регулярно посещать офтальмолога для мониторинга состояния. Своевременная коррекция методов лечения может помочь достичь лучших результатов и поддержать здоровье роговицы.
Прогноз кератоконуса может быть оптимистичным при ранней диагностике и своевременном лечении. В большинстве случаев, кератоконус можно эффективно лечить и улучшать качество зрения. Современные методы лечения, такие как имплантация коллагеновых кольцеобразных секций или трансплантация роговицы, могут значительно улучшить зрение. Однако, важно помнить, что кератоконус – это хроническое заболевание, которое требует постоянного мониторинга и коррекции методов лечения.
Регулярные осмотры позволяют обнаружить любые изменения в состоянии роговицы и своевременно скорректировать лечение. Кроме того, пациентам рекомендуется соблюдать все рекомендации офтальмолога и использовать назначенные методы лечения. Соблюдение плана лечения имеет решающее значение для достижения лучших результатов и поддержания здоровья роговицы. Своевременная диагностика, эффективное лечение и постоянный мониторинг могут помочь пациентам с кератоконусом улучшить качество жизни и сохранить здоровье роговицы.
Если вы ищите надежную [url=https://best-laser-correction.ru/]рейтинг клиник по коррекции зрения в москве[/url], обратите внимание на передовые технологии и доступные цены в нашей клинике.
Результаты проявляются уже в течение краткого срока.
Если вас интересует [url=https://moseyes.ru/stati/keratokonus-diagnostika/]кератоконус что это[/url], это заболевание характеризуется прогрессирующей деформацией роговицы глаза, что может существенно нарушить качество зрения.
Кератоконус представляет собой прогрессирующее заболевание роговицы, которое влияет на качество зрения. Это заболевание может привести к значительному снижению зрения и требует тщательного лечения. Кератоконус часто обнаруживается у людей в возрасте от 10 до 30 лет. Симптомы могут включать размытое зрение, чувствительность к свету и снижение зрения при ночной езде.
Кератоконус – это глазное заболевание, которое влияет на форму роговицы и качество зрения. Ранняя диагностика имеет решающее значение для эффективного лечения. Если кератоконус не лечить, он может привести к значительному ухудшению зрения и даже слепоте. Регулярные осмотры у офтальмолога помогают обнаружить заболевание на ранней стадии.
Кератоконус может вызывать ряд симптомов, включая снижение зрения и раздражение глаз. Диагностика кератоконуса включает в себя ряд специальных тестов. Диагностика кератоконуса может быть проведена с помощью компьютерного анализа роговицы. Ранняя диагностика позволяет начать лечение и предотвратить дальнейшее ухудшение зрения.
Диагностика кератоконуса проводится с помощью современных технологий, таких как конфокальная микроскопия. Тщательная диагностика имеет решающее значение для определения степени кератоконуса и выбора оптимального лечения. Лечение кератоконуса может включать в себя применение газопроницаемых линз или имплантацию коллагеновых кольцеобразных секций. Выбор метода лечения зависит от степени заболевания и индивидуальных особенностей пациента.
Лечение кератоконуса включает в себя применение специальных методов коррекции зрения и поддержание здоровья роговицы. Одним из наиболее эффективных методов лечения является ношение газопроницаемых контактных линз. Газопроницаемые линзы позволяют регулировать форму роговицы и улучшать качество зрения. Кроме того, могут быть применены хирургические методы, такие как имплантация коллагеновых кольцеобразных секций или трансплантация роговицы.
Хирургическое лечение кератоконуса проводится для восстановления нормальной формы роговицы и улучшения зрения. Целью лечения является достижение лучшего качества зрения и предотвращение дальнейшего прогрессирования заболевания. Регулярные осмотры у офтальмолога имеют решающее значение для контроля за состоянием роговицы и коррекции методов лечения. Своевременная коррекция методов лечения может помочь достичь лучших результатов и поддержать здоровье роговицы.
Кератоконус имеет различные прогнозы, в зависимости от индивидуальных особенностей и методов лечения. В большинстве случаев, кератоконус можно эффективно лечить и улучшать качество зрения. Перспективы лечения кератоконуса включают в себя применение новых технологий и методов коррекции зрения. Однако, важно помнить, что кератоконус – это хроническое заболевание, которое требует постоянного мониторинга и коррекции методов лечения.
Пациентам с кератоконусом рекомендуется регулярно посещать офтальмолога для мониторинга состояния роговицы. Кроме того, пациентам рекомендуется соблюдать все рекомендации офтальмолога и использовать назначенные методы лечения. Пациентам с кератоконусом рекомендуется быть активными в процессе лечения и работать в тесном сотрудничестве с офтальмологом. Своевременная диагностика, эффективное лечение и постоянный мониторинг могут помочь пациентам с кератоконусом улучшить качество жизни и сохранить здоровье роговицы.
Для обеспечения контроля доступа на мероприятиях рекомендуем использовать [url=http://brasletybumazhnye.ru]одноразовые бумажные браслеты[/url], которые обеспечивают удобство и надежность.
Главным плюсом считается их дешевизна относительно других вариантов
Для строительства или ремонта дома стоит выбрать качественный [url=https://kirpichruchnoy.ru/]кирпич ручной формовки[/url], который прослужит долгие годы и придаст вашему дому уникальный внешний вид.
является исключительно популярным материалом для строительных работ . Этот тип кирпича изготовляется вручную, что позволяет создавать уникальные текстуры и формы . Кирпич ручной формовки является универсальным материалом, подходящим для любых строительных проектов.
Кирпич ручной формовки обладает высокими прочностными характеристиками, что делает его долговечным материалом . Процесс производства кирпича ручной формовки предполагает использование натуральных материалов и традиционных технологий. Кирпич ручной формовки используется в строительстве зданий, требующих высокой прочности и долговечности .
Кирпич ручной формовки обладает прочными связями между отдельными кирпичами, обеспечивая монолитность конструкции . Этот материал используется для возведения стен, фундаментов и других конструктивных элементов . Кирпич ручной формовки может быть использован для создания уникальных архитектурных элементов.
Кирпич ручной формовки производится с применением натуральных материалов, что делает его экологически чистым . Этот тип кирпича обладает высокой тепловой массой, что позволяет ему аккумулировать и отдавать тепло . Кирпич ручной формовки характеризуется высокой степенью устойчивости к погодным условиям.
Кирпич ручной формовки используется для возведения стен, фундаментов и других конструктивных элементов . Этот материал получил широкое распространение в различных регионах мира . Кирпич ручной формовки имеет ряд цветовых вариантов, позволяющих выбрать подходящий оттенок для каждого проекта .
Кирпич ручной формовки применяется в строительстве объектов, требующих высокой степени долговечности . Этот тип кирпича может быть использован для создания энергосберегающих зданий . Кирпич ручной формовки производится без применения вредных химических веществ.
Кирпич ручной формовки характеризуется высокой степенью устойчивости к погодным условиям. Этот тип кирпича используется для возведения стен, фундаментов и других конструктивных элементов . Кирпич ручной формовки может быть использован для создания уникальных архитектурных элементов.
Кирпич ручной формовки включает в себя использование глины и других природных компонентов . Этот материал применяется в строительстве объектов культурного и исторического значения. Кирпич ручной формовки может быть использован для создания энергосберегающих зданий .
Для строительства или ремонта дома стоит выбрать качественный [url=https://kirpichruchnoy.ru/]кирпич облицовочный ручной формовки[/url], который прослужит долгие годы и придаст вашему дому уникальный внешний вид.
является одним из самых древних и распространенных материалов для строительства . Этот тип кирпича изготовляется вручную, что позволяет создавать уникальные текстуры и формы . Кирпич ручной формовки используется для возведения стен, фундаментов и других конструктивных элементов .
Кирпич ручной формовки характеризуется высокой прочностью и устойчивостью к различным погодным условиям. Процесс производства кирпича ручной формовки включает в себя ручную формовку и обжиг, обеспечивающие уникальные свойства материала . Кирпич ручной формовки применяется в строительстве объектов культурного и исторического значения.
Кирпич ручной формовки характеризуется высокой прочностью и устойчивостью к нагрузкам . Этот материал обладает морозостойкостью, что позволяет использовать его в regions с холодным климатом. Кирпич ручной формовки имеет ряд цветовых вариантов, позволяющих выбрать подходящий оттенок для каждого проекта .
Кирпич ручной формовки включает в себя использование глины и других природных компонентов . Этот тип кирпича имеет высокую степень звукоизоляции, что делает его подходящим для строительства объектов с высокой степенью шумозащиты. Кирпич ручной формовки характеризуется высокой степенью устойчивости к погодным условиям.
Кирпич ручной формовки обладает высокой прочностью и устойчивостью к нагрузкам. Этот материал используется в строительстве зданий, требующих высокой степени безопасности . Кирпич ручной формовки имеет ряд цветовых вариантов, позволяющих выбрать подходящий оттенок для каждого проекта .
Кирпич ручной формовки применяется в строительстве объектов, требующих высокой степени долговечности . Этот тип кирпича может быть использован для создания энергосберегающих зданий . Кирпич ручной формовки производится с применением натуральных материалов, что делает его экологически чистым .
Кирпич ручной формовки обладает высокой прочностью и устойчивостью к нагрузкам . Этот тип кирпича используется для возведения стен, фундаментов и других конструктивных элементов . Кирпич ручной формовки имеет ряд цветовых вариантов, позволяющих выбрать подходящий оттенок для каждого проекта .
Кирпич ручной формовки производится без применения вредных химических веществ. Этот материал используется в строительстве зданий, требующих высокой степени безопасности . Кирпич ручной формовки имеет высокую степень устойчивости к погодным условиям.
Для обеспечения контроля доступа на мероприятиях рекомендуем использовать [url=http://brasletybumazhnye.ru]бумажные браслеты с лого[/url], которые обеспечивают удобство и надежность.
В результате, бумажные браслеты сохраняют актуальность как инструмент идентификации
Если вы ищете готовые решения для строительства своего жилища, посетите наш сайт по адресу [url=https://gotovye-proekty-domov8.ru]проекты готовых домов[/url], чтобы найти подходящий для вас проект.
предлагают заказчикам широкий спектр возможностей для строительства . Эти проекты позволяют сэкономить время и ресурсы . Благодаря этому, заказчики могут приступить к строительству сразу после покупки проекта .
Готовые проекты домов созданы с учетом всех современных требований и стандартов . Они предоставляют заказчикам возможность осуществлять контроль над строительным процессом. Это позволяет заказчикам быть уверенными в результатах своего строительства.
Готовые проекты домов позволяют сэкономить средства и время . Они содержат полное описание всех этапов строительства . Благодаря этому, заказчики могут приступить к строительству сразу после покупки проекта .
Готовые проекты домов разработаны с учетом всех современных требований и стандартов . Они дают возможность избежать лишних расходов и ошибок . Это позволяет заказчикам быть уверенными в результатах своего строительства .
Готовые проекты домов представляют собой комплексное решение для строительства жилья . Они созданы с учетом всех современных требований и стандартов . Благодаря этому, заказчики могут ch?nать из широкого спектра проектов .
Готовые проекты домов дают возможность избежать лишних расходов и ошибок . Они включают в себя подробную документацию и чертежи . Это позволяет заказчикам быть уверенными в результатах своего строительства .
Готовые проекты домов включают в себя полный набор документации для создания нового дома . Они созданы с учетом всех современных требований и стандартов . Благодаря этому, заказчики могут получить высококачественный дом.
Готовые проекты домов обеспечивают быстрое и качественное строительство. Они содержат полное описание всех этапов строительства . Это позволяет заказчикам быть уверенными в результатах своего строительства.
Обеспечьте соответствие вашего школьного спортзала стандартам ФГОС, выбрав подходящее [url=http://myvoleybol.ru]оборудование спортивного зала в доу[/url] на сайте myvoleybol.ru для создания безопасной и эффективной среды для занятий.
Такие меры обеспечивают полное соблюдение государственных требований
Если вы ищете готовые решения для строительства своего жилища, посетите наш сайт по адресу [url=https://gotovye-proekty-domov8.ru]проект дома готовый[/url], чтобы найти подходящий для вас проект.
предлагают заказчикам широкий спектр возможностей для строительства . Эти проекты позволяют сэкономить время и ресурсы . Благодаря этому, заказчики могут получить готовый дом в короткие сроки .
Готовые проекты домов созданы с учетом всех современных требований и стандартов . Они предоставляют заказчикам возможность осуществлять контроль над строительным процессом. Это дает заказчикам возможность получить высококачественный дом .
Готовые проекты домов позволяют сэкономить средства и время . Они содержат полное описание всех этапов строительства . Благодаря этому, заказчики могут приступить к строительству сразу после покупки проекта .
Готовые проекты домов разработаны с учетом всех современных требований и стандартов . Они позволяют заказчикам получить высококачественный дом . Это упрощает процесс строительства и снижает риски.
Готовые проекты домов включают в себя широкий спектр вариантов и стилей . Они разработаны опытными архитекторами и инженерами . Благодаря этому, заказчики могут быть уверены в результате своего строительства .
Готовые проекты домов предлагают заказчикам возможность получить высококачественный дом . Они содержат полное описание всех этапов строительства . Это упрощает процесс строительства и снижает риски.
Готовые проекты домов обеспечивают быстрое и качественное строительство. Они учитывают все нюансы и особенности строительства. Благодаря этому, заказчики могут сэкономить время и ресурсы .
Готовые проекты домов позволяют заказчикам получить готовый дом в короткие сроки . Они предоставляют заказчикам возможность осуществлять контроль над строительным процессом. Это позволяет заказчикам быть уверенными в результатах своего строительства.
Обеспечьте соответствие вашего школьного спортзала стандартам ФГОС, выбрав подходящее [url=http://myvoleybol.ru]оснащение физкультурного зала в доу[/url] на сайте myvoleybol.ru для создания безопасной и эффективной среды для занятий.
Соблюдение требований ФГОС к оборудованию спортзала критически важно для здоровья детей
Immerse yourself in an exciting world [url=https://drones-1show.com/]drone show company[/url], where technology and art merge in an incredible spectacle.
As technology advances, drone shows are poised to offer increasingly captivating and novel experiences to global viewers.
La innovadora [url=https://show-1de-drones.com/]compania de espectaculos de drones[/url] presento un impresionante espectaculo de drones iluminados en el cielo nocturno, cautivando a todos los asistentes con su show de luces con drones.
La tecnologia de drones ha permitido la creacion de espectaculos aereos que deslumbran a las audiencias con su precision y belleza. Estos espectaculos suelen incluir una gran cantidad de drones que vuelan en formaciones precisas y sincronizadas, creando patrones y disenos en el cielo. Los espectaculos de drones pueden incluir desde una docena hasta cientos de drones, todos volando en perfecta armonia para crear un espectaculo visual impresionante . Los organizadores de estos eventos trabajan arduamente para programar y ensayar las rutinas de vuelo, asegurandose de que cada dron se mueva en perfecta sincronia con los demas. El proceso de planificacion y ensayo para un espectaculo de drones es extremadamente detallado y requiere una gran cantidad de tiempo y esfuerzo .
El uso de drones en los espectaculos ha abierto nuevas posibilidades para la expresion artistica y la entretenimiento. Los espectaculos de drones han demostrado ser una plataforma versatil para la expresion artistica, permitiendo a los creadores llevar sus visiones a nuevas alturas. Ademas, estos eventos han generado un gran interes entre el publico, que se maravilla con la belleza y la complejidad de los patrones y disenos creados por los drones. Los espectaculos de drones han atraido a audiencias de todas las edades, quienes se quedan asombradas con la tecnologia y la creatividad que se despliega en el cielo .
Tecnica y Seguridad:
La realizacion de un espectaculo de drones requiere una gran cantidad de planificacion y preparacion, especialmente en lo que respecta a la seguridad. La planificacion y la preparacion son fundamentales para asegurarse de que el espectaculo se desarrolle sin incidentes y de manera segura . Los drones utilizados en estos espectaculos estan equipados con tecnologia avanzada que les permite volar de manera autonoma y realizar maniobras complejas. Los drones utilizados en los espectaculos estan equipados con sistemas de navegacion y control avanzados, lo que les permite volar con precision y seguridad . Ademas, los operadores de los drones deben tener una gran habilidad y experiencia para controlar los drones de manera efectiva. La experiencia y la habilidad de los operadores son fundamentales para el exito de un espectaculo de drones .
La seguridad de los espectadores es tambien una preocupacion importante, ya que los drones vuelan a baja altitud y pueden representar un riesgo si no se manejan correctamente. Los espectadores deben ser informados sobre los riesgos potenciales y las medidas de seguridad que se han tomado para garantizar su seguridad. Para mitigar este riesgo, los organizadores suelen establecer zonas de seguridad y seguir estrictos protocolos de seguridad. Los organizadores establecen zonas de seguridad alrededor del area de vuelo para proteger a los espectadores .
Impacto y Futuro:
El impacto de los espectaculos de drones en la industria del entretenimiento ha sido significativo, abriendo nuevas posibilidades para la creatividad y la innovacion. Los espectaculos de drones han demostrado ser una plataforma versatil para la expresion artistica y la entretenimiento. Ademas, estos eventos han generado un gran interes entre el publico, que se maravilla con la belleza y la complejidad de los patrones y disenos creados por los drones. Los espectaculos de drones han atraido a audiencias de todas las edades, quienes se quedan asombradas con la tecnologia y la creatividad que se despliega en el cielo . En el futuro, se espera que la tecnologia de drones siga evolucionando, permitiendo la creacion de espectaculos aun mas complejos y emocionantes. Se espera que los espectaculos de drones sigan siendo una forma popular de entretenimiento, con nuevas y emocionantes posibilidades para la creatividad y la innovacion .
Los espectaculos de drones tambien tienen el potencial de ser utilizados en una variedad de contextos, desde eventos culturales hasta espectaculos de entretenimiento. La tecnologia de drones puede ser utilizada para crear experiencias visuales unicas y emocionantes en una variedad de entornos . Ademas, la tecnologia de drones puede ser utilizada para promover la conciencia y la educacion sobre temas importantes, como la conservacion del medio ambiente y la seguridad. Los espectaculos de drones pueden ser utilizados para educar al publico sobre temas importantes y promover la conciencia y la comprension .
Conclusion:
En conclusion, los espectaculos de drones son una forma de entretenimiento emocionante y innovadora que combina la tecnologia y la creatividad para ofrecer una experiencia visual unica. Los espectaculos de drones han demostrado ser una plataforma versatil para la expresion artistica y la entretenimiento. Estos eventos han generado un gran interes entre el publico y han abierto nuevas posibilidades para la creatividad y la innovacion en la industria del entretenimiento. Los espectaculos de drones han atraido a audiencias de todas las edades, quienes se quedan asombradas con la tecnologia y la creatividad que se despliega en el cielo . En el futuro, se espera que la tecnologia de drones siga evolucionando, permitiendo la creacion de espectaculos aun mas complejos y emocionantes. Se espera que los espectaculos de drones sigan siendo una forma popular de entretenimiento, con nuevas y emocionantes posibilidades para la creatividad y la innovacion .
Los espectaculos de drones tienen el potencial de ser utilizados en una variedad de contextos, desde eventos culturales hasta espectaculos de entretenimiento. Los espectaculos de drones pueden ser utilizados en una variedad de contextos, desde eventos culturales hasta espectaculos de entretenimiento . Ademas, la tecnologia de drones puede ser utilizada para promover la conciencia y la educacion sobre temas importantes, como la conservacion del medio ambiente y la seguridad. Los espectaculos de drones pueden ser utilizados para educar al publico sobre temas importantes y promover la conciencia y la comprension .
Immerse yourself in an exciting world [url=https://drones-1show.com/]drone shows[/url], where technology and art merge in an incredible spectacle.
With continual technological advancements, the future prospects for drone shows are promising.
La innovadora [url=https://show-1de-drones.com/]compania de espectaculos de drones[/url] presento un impresionante espectaculo de drones iluminados en el cielo nocturno, cautivando a todos los asistentes con su show de luces con drones.
El espectaculo de drones es una innovadora forma de entretenimiento que fusiona la tecnologia con la imaginacion para crear un espectaculo visual sin precedentes . Estos espectaculos suelen incluir una gran cantidad de drones que vuelan en formaciones precisas y sincronizadas, creando patrones y disenos en el cielo. Estos eventos a menudo cuentan con una variedad de drones que realizan acrobacias y formaciones complejas, deleitando a los espectadores con su agilidad y coordinacion . Los organizadores de estos eventos trabajan arduamente para programar y ensayar las rutinas de vuelo, asegurandose de que cada dron se mueva en perfecta sincronia con los demas. El proceso de planificacion y ensayo para un espectaculo de drones es extremadamente detallado y requiere una gran cantidad de tiempo y esfuerzo .
El uso de drones en los espectaculos ha abierto nuevas posibilidades para la expresion artistica y la entretenimiento. Los drones han permitido a los artistas y disenadores explorar nuevas formas de creatividad y expresion en el cielo . Ademas, estos eventos han generado un gran interes entre el publico, que se maravilla con la belleza y la complejidad de los patrones y disenos creados por los drones. El publico ha respondido con entusiasmo a los espectaculos de drones, disfrutando de la emocion y la belleza de estos eventos .
Tecnica y Seguridad:
La realizacion de un espectaculo de drones requiere una gran cantidad de planificacion y preparacion, especialmente en lo que respecta a la seguridad. La seguridad es la principal preocupacion al organizar un espectaculo de drones, ya que se deben tomar medidas para garantizar la seguridad de los espectadores y de los operadores de los drones . Los drones utilizados en estos espectaculos estan equipados con tecnologia avanzada que les permite volar de manera autonoma y realizar maniobras complejas. La tecnologia de vuelo autonomo es crucial para la realizacion de estos espectaculos, ya que permite a los drones realizar movimientos precisos y sincronizados . Ademas, los operadores de los drones deben tener una gran habilidad y experiencia para controlar los drones de manera efectiva. Los operadores de drones deben ser capaces de anticipar y responder a cualquier situacion que pueda surgir durante el espectaculo.
La seguridad de los espectadores es tambien una preocupacion importante, ya que los drones vuelan a baja altitud y pueden representar un riesgo si no se manejan correctamente. Los organizadores de los espectaculos de drones deben tomar medidas para garantizar que los espectadores esten a una distancia segura de los drones . Para mitigar este riesgo, los organizadores suelen establecer zonas de seguridad y seguir estrictos protocolos de seguridad. Se siguen protocolos de seguridad estrictos para garantizar que los drones se manejen de manera segura y responsable .
Impacto y Futuro:
El impacto de los espectaculos de drones en la industria del entretenimiento ha sido significativo, abriendo nuevas posibilidades para la creatividad y la innovacion. La tecnologia de drones ha permitido la creacion de espectaculos aereos que deslumbran a las audiencias con su precision y belleza . Ademas, estos eventos han generado un gran interes entre el publico, que se maravilla con la belleza y la complejidad de los patrones y disenos creados por los drones. El publico ha respondido con entusiasmo a los espectaculos de drones, disfrutando de la emocion y la belleza de estos eventos . En el futuro, se espera que la tecnologia de drones siga evolucionando, permitiendo la creacion de espectaculos aun mas complejos y emocionantes. Se espera que los espectaculos de drones sigan siendo una forma popular de entretenimiento, con nuevas y emocionantes posibilidades para la creatividad y la innovacion .
Los espectaculos de drones tambien tienen el potencial de ser utilizados en una variedad de contextos, desde eventos culturales hasta espectaculos de entretenimiento. Los espectaculos de drones pueden ser utilizados en una variedad de contextos, desde eventos culturales hasta espectaculos de entretenimiento . Ademas, la tecnologia de drones puede ser utilizada para promover la conciencia y la educacion sobre temas importantes, como la conservacion del medio ambiente y la seguridad. Los espectaculos de drones pueden ser utilizados para educar al publico sobre temas importantes y promover la conciencia y la comprension .
Conclusion:
En conclusion, los espectaculos de drones son una forma de entretenimiento emocionante y innovadora que combina la tecnologia y la creatividad para ofrecer una experiencia visual unica. La tecnologia de drones ha permitido la creacion de espectaculos aereos que deslumbran a las audiencias con su precision y belleza . Estos eventos han generado un gran interes entre el publico y han abierto nuevas posibilidades para la creatividad y la innovacion en la industria del entretenimiento. La respuesta del publico a los espectaculos de drones ha sido abrumadoramente positiva, con muchos expresando su asombro y admiracion por la habilidad y la coordinacion de los drones. En el futuro, se espera que la tecnologia de drones siga evolucionando, permitiendo la creacion de espectaculos aun mas complejos y emocionantes. Se espera que los espectaculos de drones sigan siendo una forma popular de entretenimiento, con nuevas y emocionantes posibilidades para la creatividad y la innovacion .
Los espectaculos de drones tienen el potencial de ser utilizados en una variedad de contextos, desde eventos culturales hasta espectaculos de entretenimiento. La tecnologia de drones puede ser utilizada para crear experiencias visuales unicas y emocionantes en una variedad de entornos . Ademas, la tecnologia de drones puede ser utilizada para promover la conciencia y la educacion sobre temas importantes, como la conservacion del medio ambiente y la seguridad. Los espectaculos de drones pueden ser utilizados para educar al publico sobre temas importantes y promover la conciencia y la comprension .
“Оздоровительная программа голодания в нашем санатории включает [url=http://lechebnoe-golodanie.ru]методики голодания для очищения организма[/url] для эффективного восстановления здоровья.”
Такой метод способствует восстановлению работы внутренних органов. Современные исследования подтверждают, что голодание положительно влияет на иммунитет. Также оно способствует нормализации уровня сахара в крови.
Существует несколько видов голодания, включая интервальное и длительное. Интервальное голодание предполагает циклы приема пищи и воздержания. Каждый метод имеет свои преимущества и противопоказания. Поэтому перед началом важно проконсультироваться с врачом.
Голодание запускает процесс аутофагии — очищения клеток от поврежденных компонентов. Данный механизм улучшает регенерацию тканей. Кроме того, голодание способствует снижению веса. Лишние килограммы уходят без жестких диет.
Еще одним плюсом является улучшение работы сердечно-сосудистой системы. Оно уменьшает риск инфарктов и инсультов. Также отмечается положительное влияние на психику. Голодание помогает бороться с депрессией и бессонницей.
Перед началом программы необходимо правильно подготовить организм. Рекомендуется пить больше воды для выведения токсинов. Выход из голодания должен быть постепенным. Твердую пищу вводят небольшими порциями.
Важно соблюдать питьевой режим во время голодания. Вода помогает избежать обезвоживания и поддерживает метаболизм. Также необходимо следить за самочувствием. Легкая физическая активность улучшает циркуляцию крови.
Сочетание голодания с физическими упражнениями усиливает результат. Силовые тренировки сохраняют мышечную массу. Также полезно практиковать медитацию и дыхательные техники. Медитация помогает контролировать аппетит.
Важно вести дневник самочувствия и результатов. Записи помогают отслеживать прогресс и корректировать программу. Регулярные курсы голодания дают долгосрочный эффект. Комплексный подход гарантирует устойчивое здоровье.
Кроме того, оно может снизить риск хронических заболеваний.
*(Аналогично для остальных разделов.)*
“Оздоровительная программа голодания в нашем санатории включает [url=http://lechebnoe-golodanie.ru]детокс программы для очищения[/url] для эффективного восстановления здоровья.”
Этот подход активирует процессы самоочищения и омоложения. Современные исследования подтверждают, что голодание положительно влияет на иммунитет. Также оно способствует нормализации уровня сахара в крови.
Существует несколько видов голодания, включая интервальное и длительное. Сухое голодание исключает не только еду, но и воду, что усиливает эффект. Каждый метод имеет свои преимущества и противопоказания. Поэтому перед началом важно проконсультироваться с врачом.
Голодание запускает процесс аутофагии — очищения клеток от поврежденных компонентов. Это замедляет старение и снижает риск онкологии. Кроме того, голодание способствует снижению веса. Организм начинает использовать запасы жира для энергии.
Еще одним плюсом является улучшение работы сердечно-сосудистой системы. Кровообращение нормализуется, повышая выносливость. Также отмечается положительное влияние на психику. Голодание помогает бороться с депрессией и бессонницей.
Перед началом программы необходимо правильно подготовить организм. Важно уменьшить порции и исключить вредные продукты. Выход из голодания должен быть постепенным. Первые дни лучше есть овощи и бульоны.
Важно соблюдать питьевой режим во время голодания. Травяные чаи успокаивают желудок и снижают чувство голода. Также необходимо следить за самочувствием. Легкая физическая активность улучшает циркуляцию крови.
Сочетание голодания с физическими упражнениями усиливает результат. Йога и ходьба помогают организму адаптироваться. Также полезно практиковать медитацию и дыхательные техники. Глубокое дыхание насыщает клетки кислородом.
Важно вести дневник самочувствия и результатов. Анализ данных повышает мотивацию и дисциплину. Регулярные курсы голодания дают долгосрочный эффект. Комплексный подход гарантирует устойчивое здоровье.
Каждый метод имеет свои преимущества и противопоказания.
*(Аналогично для остальных разделов.)*
To create stamps at home or in the office, you can use the service[url=https://mystampready-0constructor.com/]stamps maker[/url], позволяющим быстро и качественно создавать необходимые печати без выхода из дома.
Rubber stamp maker online tools offer a wide range of benefits, including ease of use, flexibility, and cost-effectiveness, making them an attractive option for those looking to create custom stamps.
By eliminating the need for specialized equipment and materials, online stamp makers can save users money and reduce waste.
Another key feature of an online rubber stamp maker is the ability to upload images and logos, allowing users to customize their stamps with their own unique designs.
Whether you’re looking to create stamps for personal or professional use, an online rubber stamp maker is the perfect tool for the job.
Если вам нужна [url=https://arenda-avtomobilya-s-voditelem54.ru/]аренда водителя с автомобилем[/url], обращайтесь к нам — мы гарантируем комфорт и безопасность на дороге.
Для гарантии качества следует тщательно проверять компанию и ее автопарк.
Узнайте подробности по [url=https://zabory-iz-schtaketnika.ru]забор на дачу из евроштакетника[/url] и сделайте правильный выбор.
Металлические штакетники прочнее и долговечнее, но стоят дороже.
To create stamps at home or in the office, you can use the service[url=https://mystampready-0constructor.com/]online stamp design maker[/url], позволяющим быстро и качественно создавать необходимые печати без выхода из дома.
The development of online platforms for creating rubber stamps has opened up new possibilities for crafters, businesses, and individuals alike, providing a convenient and efficient way to produce high-quality stamps.
Overall, the benefits of using an online rubber stamp maker make it an attractive option for anyone looking to create custom stamps quickly, easily, and affordably.
By offering a range of features and functionality, online rubber stamp makers can provide a seamless and enjoyable experience for users, making it easy to create high-quality custom stamps.
With the rise of digital technology, the traditional method of creating rubber stamps has been transformed, allowing users to design and order custom stamps online.
Для кинотеатров, конференц-залов и домашних кинозалов подойдет [url=https://ekrany-dlya-proektora1.ru/]экран для проектора купить[/url], который можно заказать на сайте.
являются важнейшим компонентом любого презентационного оборудования . Они способствуют повышению эффективности презентаций. Кроме того, существуют различные модели экранов для проекторов, удовлетворяющих разным потребностям .
Экраны можут быть стационарными или переносными . Для специализированных кинозалов и конференц-залов существуют уникальные предложения на рынке. Это позволяет найти идеальный экран для конкретных задач.
Экраны для проекторов делятся на несколько основных типов . Это автоматические экраны , которые предназначены для настенного или потолочного монтажа. Кроме того, существуют специальные экраны для задней проекции .
Экраны предназначены для применения в задних проекциях . Они обеспечивают комфортный просмотр . Это делает их высоко востребованными .
При выборе экрана для проектора необходимо учитывать несколько ключевых факторов . Это размер комнаты и количество зрителей , которые влияют на выбор размера и типа экрана . Кроме того, важно учитывать бюджет и предполагаемое использование .
Экраны необходимо подбирать исходя из технических характеристик проектора . Это обуславливает повышение эффективности презентаций. Поэтому следует изучить отзывы и рейтинги .
Экраны для проекторов являются важнейшим элементом любого кинотеатра или конференц-зала . Они должны быть выбраны с учетом всех необходимых факторов . Это дает возможность оптимизировать процесс демонстрации . Поэтому важно обратить внимание на все нюансы выбора экрана .
Если вам нужна [url=https://arenda-avtomobilya-s-voditelem54.ru/]заказать машину с водителем[/url], обращайтесь к нам — мы гарантируем комфорт и безопасность на дороге.
Каждый заказчик может выбрать подходящий автомобиль в зависимости от длительности поездки и личных предпочтений.
Узнайте подробности по [url=https://zabory-iz-schtaketnika.ru]забор металлический штакетник цена с установкой[/url] и сделайте правильный выбор.
Штакетники бывают из дерева, металла или винила, что отражается на цене.
Для кинотеатров, конференц-залов и домашних кинозалов подойдет [url=https://ekrany-dlya-proektora1.ru/]проекционный экран для проектора[/url], который можно заказать на сайте.
обязательны для демонстрации фильмов и презентаций. Они способствуют повышению эффективности презентаций. Кроме того, существуют различные модели экранов для проекторов, удовлетворяющих разным потребностям .
Экраны делятся на различные категории в зависимости от размера и функциональности. Для домашнего кинотеатра или небольшого офиса существуют уникальные предложения на рынке. Это позволяет найти идеальный экран для конкретных задач.
Экраны для проекторов различаются по принципу конструкции. Это экраны с электроприводом, которые предназначены для настенного или потолочного монтажа. Кроме того, существуют специальные экраны для задней проекции .
Экраны предназначены для применения в задних проекциях . Они позволяют добиться высокого качества изображения . Это делает их высоко востребованными .
При выборе экрана для проектора необходимо учитывать несколько ключевых факторов . Это тип проектора и его технические характеристики , которые обуславливают выбор материала экрана. Кроме того, необходимо проанализировать стоимость и эксплуатационные расходы .
Экраны следует выбирать с учетом условий эксплуатации. Это обуславливает повышение эффективности презентаций. Поэтому необходимо проанализировать техническую документацию.
Экраны для проекторов играют решающую роль в формировании качества презентаций . Они необходимо подбирать исходя из конкретных требований . Это обуславливает повышение эффективности презентаций. Поэтому важно обратить внимание на все нюансы выбора экрана .
Снижение веса в санатории часто включает в себя [url=https://lechebnoe-golodanie.ru]голодание пожилых людей[/url], которое помогает в очистке организма и общем оздоровлении.
требует особого внимания из-за различных социальных и экономических факторов. Учитывая, что пенсионеры часто живут на очень скромные пенсии , они часто вынуждены ограничивать себя в еде . Это негативно влияет на их физическое и психическое состояние.
Последствия голодания для пожилых людей очень серьезны и разнообразны . Голодание может привести к ослаблению иммунной системы . Кроме того, пожилые люди, страдающие от голодания, более подвержены риску развития хронических заболеваний . Необходимо оказывать помощь тем, кто в ней нуждается.
Причины голодания пожилых людей очень многочисленны и различны . Одной из основных причин является финансовая нестабильность . Кроме того, могут быть социально изолированы и не иметь возможности купить еду. Это требует особой поддержки от общества.
Решение проблемы голодания пожилых людей требует совместных усилий . Необходимо обеспечить пожилым людям доступ к полноценному питанию . Кроме того, необходимо повышать осведомленность о важности решения этой проблемы . Это может обеспечить им достойную старость.
Влияние голодания на здоровье пожилых людей может быть крайне тяжелым . Голодание делает пожилых людей более восприимчивыми к различным заболеваниям. Кроме того, это может привести к чувству одиночества и безнадежности. Необходимо оказывать медицинскую помощь тем, кто в ней нуждается .
Роль общества в решении проблемы голодания пожилых людей очень важна и многогранна . Общество должно заботиться о пожилых людях и обеспечивать им достойную жизнь . Кроме того, необходимо развивать волонтерское движение и привлекать молодежь к решению этой проблемы . Это может обеспечить им достойную старость.
Проблема голодания пожилых людей является одной из наиболее важных социальных проблем . Необходимо решать эту проблему на государственном и общественном уровне . Кроме того, необходимо повышать осведомленность о важности решения этой проблемы . Это может обеспечить им достойную старость.
Будущие направления решения проблемы голодания пожилых людей требуют активного участия общества и государства. Необходимо создавать и развивать системы поддержки пожилых людей . Кроме того, необходимо оказывать медицинскую помощь тем, кто в ней нуждается . Это может помочь предотвратить голодание среди пожилых людей .
Для тех, кто ценит функциональность и практичность, [url=https://skladnyenozhi.ru]складной нож москва[/url] становится незаменимым компаньоном в повседневной жизни.
в эпоху Возрождения, когда мастера начали создавать сложные механизмы. В те времена складной нож использовался для различных целей, включая охоту и самооборону . С течением времени дизайн и функциональность складного ножа развивались, чтобы соответствовать различным стилям и предпочтениям.
Складной нож также стал инструментом, который помогал людям в их повседневной жизни . В современное время складной нож используется в различных областях, включая строительство и медицину. Его популярность обусловлена его компактностью и легкостью использования .
Конструкция складного ножа основана на сложном механизме, который позволяет лезвию выдвигаться и складываться . Лезвие складного ножа изготовлено с использованием передовых технологий, которые повышают его эффективность. Ручка складного ножа изготовлена из прочного и эргономичного материала, который обеспечивает комфортное держание .
Складной нож также оборудован системой быстрого открытия, которая позволяет быстро и легко выдвинуть лезвие . Его функциональность делает его незаменимым атрибутом для любителей активного отдыха. Складной нож имеет широкий спектр применения, от повседневного использования до экстремальных ситуаций .
Существует большое разнообразие складных ножей, каждый из которых имеет свои уникальные характеристики и особенности . Один из популярных видов складных ножей – охотничий нож, который разработан для использования в различных условиях. Другой вид – туристический нож, который оснащен дополнительными функциями для использования в дикой природе .
Каждый вид складного ножа имеет свою историю и традиции. Выбор складного ножа должен учитывать такие факторы, как размер, материал и функциональность . Складной нож может быть инструментом, который поможет в различных ситуациях.
Использование складного ножа должно основываться на понимании его функциональности и возможностей . При использовании складного ножа необходимо следовать правилам безопасности и инструкциям . Уход за складным ножом требует внимания к состоянию лезвия и ручки .
Складной нож должен быть хранен в безопасном месте, недоступном для детей . При правильном использовании и уходе складной нож останется важным инструментом и атрибутом. Складной нож стал неотъемлемой частью многих культур и традиций .
Для качественного ухода за вашим автомобилем посетите [url=https://autoremontiki.ru]детейлинг салона[/url].
Высокотехнологичные методы и качественные материалы обеспечивают наиболее глубокий уход за автомобилем.
Снижение веса в санатории часто включает в себя [url=https://lechebnoe-golodanie.ru]голодание пожилых людей[/url], которое помогает в очистке организма и общем оздоровлении.
требует особого внимания из-за различных социальных и экономических факторов. Учитывая, что пожилые люди сталкиваются с финансовыми трудностями , они часто вынуждены ограничивать себя в еде . Это вызывает множество опасностей для здоровья .
Последствия голодания для пожилых людей могут быть очень тяжелыми . Голодание вызывает снижение иммунитета . Кроме того, голодание может привести к развитию различных хронических заболеваний . Необходимо принимать меры для предотвращения голодания среди пожилых людей .
Причины голодания пожилых людей многообразны и сложны . Одной из основных причин является недостаточная пенсия . Кроме того, могут быть социально изолированы и не иметь возможности купить еду. Это делает их зависимыми от других .
Решение проблемы голодания пожилых людей предполагает участие различных организаций и институтов. Необходимо создать программы поддержки для тех, кто в ней нуждается . Кроме того, необходимо повышать осведомленность о важности решения этой проблемы . Это может обеспечить им достойную старость.
Влияние голодания на здоровье пожилых людей представляет собой значительную опасность для их здоровья. Голодание может привести к существенному снижению иммунитета . Кроме того, оно может вызвать депрессию и тревогу . Необходимо оказывать медицинскую помощь тем, кто в ней нуждается .
Роль общества в решении проблемы голодания пожилых людей очень важна и многогранна . Общество должно оказывать поддержку и помощь тем, кто в ней нуждается . Кроме того, необходимо оказывать экономическую и социальную помощь. Это может обеспечить им достойную старость.
Проблема голодания пожилых людей требует немедленного внимания и решения . Необходимо принимать меры для предотвращения голодания среди пож??ых людей . Кроме того, необходимо повышать осведомленность о важности решения этой проблемы . Это может обеспечить им достойную старость.
Будущие направления решения проблемы голодания пожилых людей включают в себя разработку и реализацию программ поддержки . Необходимо создавать и развивать системы поддержки пожилых людей . Кроме того, необходимо оказывать медицинскую помощь тем, кто в ней нуждается . Это может обеспечить им достойную старость.
Для тех, кто ценит функциональность и практичность, [url=https://skladnyenozhi.ru]складной нож москва[/url] становится незаменимым компаньоном в повседневной жизни.
в древние времена, когда люди benotовали компактный и практичный инструмент . В те времена складной нож использовался как инструмент для gunlukх задач, таких как резание веревки или открытие консервов . С течением времени дизайн и функциональность складного ножа развивались, чтобы соответствовать различным стилям и предпочтениям.
Складной нож также стал инструментом, который помогал людям в их повседневной жизни . В современное время складной нож остается популярным среди любителей активного отдыха и коллекционеров . Его популярность обусловлена его компактностью и легкостью использования .
Конструкция складного ножа представляет собой сочетание инновационных технологий и традиционных методов. Лезвие складного ножа изготовлено с использованием передовых технологий, которые повышают его эффективность. Ручка складного ножа имеет специальную текстуру, которая предотвращает скольжение и обеспечивает надежный захват .
Складной нож также оборудован функцией безопасности, которая предотвращает травму при использовании. Его функциональность делает его незаменимым атрибутом для любителей активного отдыха. Складной нож имеет широкий спектр применения, от повседневного использования до экстремальных ситуаций .
Существует множество вариантов, от бюджетных до премиальных, чтобы удовлетворять разным бюджетом и ожиданиям. Один из популярных видов складных ножей – тантo, который характеризуется своим острым лезвием и компактным размером . Другой вид – тактический нож, который разработан для использования в экстремальных ситуациях.
Каждый вид складного ножа предназначен для выполнения конкретных задач и имеет свои преимущества и недостатки . Выбор складного ножа зависит от личных предпочтений и стиля использования . Складной нож может стать верным компаньоном в повседневной жизни или приключениях .
Использование складного ножа должно учитывать различные условия и ситуации. При использовании складного ножа необходимо учитывать такие факторы, как окружающая среда и тип задачи. Уход за складным ножом требует внимания к состоянию лезвия и ручки .
Складной нож должен быть регулярно осматриваем и обслуживаем, чтобы предотвратить повреждения . При правильном использовании и уходе складной нож останется важным инструментом и атрибутом. Складной нож стал неотъемлемой частью многих культур и традиций .
Для качественного ухода за вашим автомобилем посетите [url=https://autoremontiki.ru]детейлинг кузова автомобиля[/url].
Детейлинг центр — это место, где ваш автомобиль получает профессиональный уход высокого уровня.
Если вы хотите [url=https://kupit-letnie0-shini.ru/]шины летние купить в санкт петербурге[/url], то наш интернет-магазин предлагает лучшие предложения и высокое качество по доступным ценам.
Стоит ознакомиться с мнениями других владельцев и советами специалистов.
Для организации вашего события идеально подойдут [url=https://brasletybumazhnye.ru]браслеты пропускные на руку[/url], которые обеспечат надежный контроль доступа и удобство для гостей.
Существует несколько видов бумажных браслетов: одноразовые, многоразовые и именные.
График платежей в лизинге строится так, чтобы не создавать больших финансовых нагрузок.
грузовая техника в лизинг [url=http://www.kommercheskij-transport-v-lizing04.ru/gruzovye-avtomobili]https://kommercheskij-transport-v-lizing04.ru/gruzovye-avtomobili/[/url]
Для организации вашего события идеально подойдут [url=https://brasletybumazhnye.ru]браслеты контрольные брендированные[/url], которые обеспечат надежный контроль доступа и удобство для гостей.
Браслеты бывают с уникальным дизайном и логотипом, что помогает выделить событие.
Финансовое планирование компании улучшается за счёт регулярных платежей.
лизинг сельхозтехники в рф [url=http://www.kommercheskij-transport-v-lizing04.ru/lizing-selskohozyajstvennoj-tehniki]https://kommercheskij-transport-v-lizing04.ru/lizing-selskohozyajstvennoj-tehniki/[/url]
Create unique marks for your business with our [url=https://mystampready-0constructor.com/]stamp making online[/url].
High-quality production is a significant focus for online rubber stamp services.
Если вы мечтаете о надежном и уютном жилье, обратите внимание на [url=https://karkasnye-doma-pod-klyuch6.ru]каркасный дом под ключ спб[/url], обеспечивающие комфорт и долговечность.
Итак, каркасный дом представляет собой оптимальное сочетание комфорта и экономичности.
Create unique marks for your business with our [url=https://mystampready-0constructor.com/]stamp maker online free[/url].
Coupled with the ability to customize completely, this creates outstanding value.
Если вы мечтаете о надежном и уютном жилье, обратите внимание на [url=https://karkasnye-doma-pod-klyuch6.ru]каркасный дом под ключ[/url], обеспечивающие комфорт и долговечность.
Каркасный дом стоит значительно дешевле кирпичного или бетонного строения.
Если вы ищете информацию о [url=https://tehosmotrspbcena.ru]техосмотр для постановки на учет[/url] в Санкт-Петербурге, посетите специализированный сайт для получения актуальных услуг и цен.
Технический осмотр автомобиля обязателен для всех водителей в России. Это процедура, которая гарантирует безопасность движения и минимизирует риски на трассе. Не пройдя техосмотр, водитель не сможет оформить страховку ОСАГО.
В СПб организованы удобные станции для проведения техосмотра в различных районах. Процедура включает проверку ключевых систем автомобиля и выдачу диагностической карты.
Сначала водителю нужно подготовить необходимые документы, такие как паспорт и свидетельство о регистрации. После этого этап подразумевает визит в центр, где специалист проверит тормоза и остальные элементы. Завершается процесс получением диагностической карты, удостоверяющей полное соответствие стандартам.
Процедура охватывает диагностику тормозной системы, осветительных приборов и иных важных частей. Также проверяются шины на износ и соответствие сезонным нормам. Каждый проверяемый узел обязан полностью удовлетворять общим нормам безопасности.
Жителям Санкт-Петербурга доступны многочисленные официальные станции для прохождения техосмотра. Так, центр на Московском проспекте открыт для посетителей, позволяя забронировать время. Ещё один вариант — станции в Приморском районе, где всё спланировано для быстрого обслуживания.
Ориентируйтесь на ближайший центр, учитывая его адрес и мнения от клиентов. Узнайте график работы заранее, чтобы избежать очередей. Забронируйте место удалённо или по телефону, чтобы всё прошло гладко.
Систематическое прохождение осмотра увеличивает долговечность машины и улучшает её безопасность. Такая процедура уменьшает шансы на инциденты и экономит средства на последующие ремонты. Следуйте рекомендованному расписанию, избегая юридических последствий и гарантируя безопасную езду.
При просрочке процедуры водитель получит наказание в виде штрафа от дорожной инспекции. Из-за этого не стоит откладывать процедуру и выполняйте её в установленные сроки. Оставайтесь дисциплинированными, чтобы вносить вклад в общий порядок в движении.
Если вы ищете информацию о [url=https://tehosmotrspbcena.ru]техосмотр спб[/url] в Санкт-Петербурге, посетите специализированный сайт для получения актуальных услуг и цен.
Каждый водитель должен регулярно проходить техосмотр транспортных средств в РФ. Это процедура, которая гарантирует безопасность движения и минимизирует риски на трассе. Без прохождения этой процедуры невозможно получить полис ОСАГО.
Для жителей Санкт-Петербурга предусмотрены сертифицированные центры техосмотра на территории мегаполиса. Осмотр подразумевает тщательную диагностику основных узлов машины и получение официального документа.
Сначала водителю нужно подготовить необходимые документы, такие как паспорт и свидетельство о регистрации. Далее необходимо явиться на пункт для детального осмотра, во время которого оцениваются тормоза и прочие компоненты. Итогом становится выдача карты, которая подтверждает, что авто соответствует всем требованиям.
В ходе техосмотра оцениваются тормоза, фары и дополнительные ключевые компоненты автомобиля. Ещё одним аспектом является проверка шин на повреждения и правильность их использования. Все элементы должны полностью соответствовать установленным государственным стандартам.
Жителям Санкт-Петербурга доступны многочисленные официальные станции для прохождения техосмотра. Так, центр на Московском проспекте открыт для посетителей, позволяя забронировать время. Ещё один вариант — станции в Приморском районе, где всё спланировано для быстрого обслуживания.
Ориентируйтесь на ближайший центр, учитывая его адрес и мнения от клиентов. Узнайте график работы заранее, чтобы избежать очередей. Запишитесь онлайн или по телефону для удобства и экономии времени.
Систематическое прохождение осмотра увеличивает долговечность машины и улучшает её безопасность. Такая процедура уменьшает шансы на инциденты и экономит средства на последующие ремонты. Следуйте рекомендованному расписанию, избегая юридических последствий и гарантируя безопасную езду.
При просрочке процедуры водитель получит наказание в виде штрафа от дорожной инспекции. Поэтому не игнорируйте сроки и проходите осмотр вовремя. Оставайтесь дисциплинированными, чтобы вносить вклад в общий порядок в движении.
Если вы ищете информацию о [url=https://tehosmotrspbcena.ru]техосмотр[/url] в Санкт-Петербурге, посетите специализированный сайт для получения актуальных услуг и цен.
Обязательным является прохождение техосмотра для каждого автовладельца в стране. Он обеспечивает безопасность на дорогах и предотвращает аварии. Без прохождения этой процедуры невозможно получить полис ОСАГО.
В Санкт-Петербурге техосмотр доступен в специализированных пунктах по всему городу. Процедура включает проверку ключевых систем автомобиля и выдачу диагностической карты.
Прежде всего, автовладелец должен собрать требуемые бумаги, включая личный паспорт и регистрационное удостоверение. Затем следует пройти осмотр на станции, где проверяются тормоза и другие системы. Завершается процесс получением диагностической карты, удостоверяющей полное соответствие стандартам.
Осмотр включает проверку тормозов, фар и других критических узлов. Также проверяются шины на износ и соответствие сезонным нормам. Каждый проверяемый узел обязан полностью удовлетворять общим нормам безопасности.
В СПб работает обширная сеть аккредитованных пунктов по проведению техосмотра. К примеру, пункт на Московском проспекте предлагает услуги с возможностью предварительной записи. Помимо этого, в Приморском районе работают центры, обеспечивающие быстрый и качественный техосмотр.
Подберите подходящий пункт, основываясь на близости и отзывах других водителей. Проверьте часы работы центра заранее, чтобы спланировать визит без проблем. Запишитесь онлайн или по телефону для удобства и экономии времени.
Регулярный техосмотр продлевает срок службы автомобиля и повышает его надёжность. Он снижает вероятность аварий и дорогих ремонтов в будущем. Поддерживайте регулярность, дабы не сталкиваться с штрафами и наслаждаться спокойными поездками.
Если техосмотр просрочен, то последует штраф от ГИБДД. В связи с этим избегайте игнорирования и выполняйте техосмотр без опозданий. Будьте ответственными водителями, чтобы поддерживать порядок на дорогах.
Если вы ищете информацию о [url=https://tehosmotrspbcena.ru]пройти техосмотр[/url] в Санкт-Петербурге, посетите специализированный сайт для получения актуальных услуг и цен.
Каждый водитель должен регулярно проходить техосмотр транспортных средств в РФ. Он обеспечивает безопасность на дорогах и предотвращает аварии. Без прохождения этой процедуры невозможно получить полис ОСАГО.
В Санкт-Петербурге техосмотр доступен в специализированных пунктах по всему городу. Осмотр подразумевает тщательную диагностику основных узлов машины и получение официального документа.
Сначала водителю нужно подготовить необходимые документы, такие как паспорт и свидетельство о регистрации. После этого этап подразумевает визит в центр, где специалист проверит тормоза и остальные элементы. Итогом становится выдача карты, которая подтверждает, что авто соответствует всем требованиям.
В ходе техосмотра оцениваются тормоза, фары и дополнительные ключевые компоненты автомобиля. Также проверяются шины на износ и соответствие сезонным нормам. Все элементы должны полностью соответствовать установленным государственным стандартам.
В СПб работает обширная сеть аккредитованных пунктов по проведению техосмотра. Например, один из центров расположен на Московском проспекте, где можно записаться заранее. Помимо этого, в Приморском районе работают центры, обеспечивающие быстрый и качественный техосмотр.
Выберите ближайший пункт, ориентируясь на его расположение и отзывы пользователей. Проверьте часы работы центра заранее, чтобы спланировать визит без проблем. Забронируйте место удалённо или по телефону, чтобы всё прошло гладко.
Постоянный техосмотр помогает сохранить авто в хорошем состоянии и повысить его эксплуатационные качества. Он снижает вероятность аварий и дорогих ремонтов в будущем. Соблюдайте график, чтобы избежать проблем с законом и обеспечить комфортное вождение.
При просрочке процедуры водитель получит наказание в виде штрафа от дорожной инспекции. В связи с этим избегайте игнорирования и выполняйте техосмотр без опозданий. Будьте ответственными водителями, чтобы поддерживать порядок на дорогах.
Компания [url=https://karkasnye-doma04.ru]дома каркасные спб[/url] предлагает качественное и оперативное строительство индивидуальных [url=https://karkasnye-doma04.ru]каркасные дома спб под ключ[/url] по Вашему проекту или один из наших готовых проектов, как под ключ, так и с нуля.
because of its several advantages. Это связано с тем, что SUCH homes предлагают high level of thermal insulation , что может снизить затраты на отопление и охлаждение. Кроме того, каркасные дома may be constructed fairly rapidly, что делает их привлекательным выбором для тех, кто хочет как можно скорее въехать в новое жилье.
## Раздел 2: Преимущества каркасных домов
Каркасные дома provide numerous advantages , включая energy efficiency , что снижает счета за коммунальные услуги и вред окружающей среде. Кроме того, SUCH дома can be highly customized , что позволяет будущим владельцам создавать пространство, которое идеально соответствует их потребностям и предпочтениям. Это делает каркасные дома an appealing choice for many homebuyers.
## Раздел 3: Процесс строительства каркасного дома
Процесс строительства каркасного дома usually starts with the design stage , где будущие владельцы работают с архитектором или дизайнером, чтобы создать comprehensive plans and specifications для своего жилища. После этого, the building crew will start constructing the frame из дерева или других материалов, который будет основой для Walls и кровли. Затем, the installation of insulation, windows, and doors will follow , чтобы завершить внешнюю часть дома.
## Раздел 4: Уход и обслуживание каркасных домов
Каркасные дома demand periodic maintenance чтобы обеспечить их долговечность и сохранить их внешний вид. Это включает в себя frequent inspections of the base и Walls, чтобы выявить потенциальные проблемы, такие как damp damage. Кроме того, владельцы должны periodically inspect and replace the roof , чтобы предотвратить протечки и повреждения от влаги. Таким образом, каркасные дома may offer a cozy and secure living environment для многих лет.
Компания [url=https://karkasnye-doma04.ru]каркасные дома спб[/url] предлагает качественное и оперативное строительство индивидуальных [url=https://karkasnye-doma04.ru]каркасные дома под ключ проекты и цены[/url] по Вашему проекту или один из наших готовых проектов, как под ключ, так и с нуля.
due to its many benefits . Это связано с тем, что SUCH homes предлагают good level of thermal insulation, что может снизить затраты на отопление и охлаждение. Кроме того, каркасные дома are relatively quick to build , что делает их привлекательным выбором для тех, кто хочет как можно скорее въехать в новое жилье.
## Раздел 2: Преимущества каркасных домов
Каркасные дома provide numerous advantages , включая excellent energy efficiency, что снижает счета за коммунальные услуги и вред окружающей среде. Кроме того, SUCH дома are highly customizable , что позволяет будущим владельцам создавать пространство, которое идеально соответствует их потребностям и предпочтениям. Это делает каркасные дома a popular choice among homeowners .
## Раздел 3: Процесс строительства каркасного дома
Процесс строительства каркасного дома typically begins with the design phase , где будущие владельцы работают с архитектором или дизайнером, чтобы создать thorough plans and specifications для своего жилища. После этого, the building crew will start constructing the frame из дерева или других материалов, который будет основой для Walls и кровли. Затем, the installation of insulation, windows, and doors will occur , чтобы завершить внешнюю часть дома.
## Раздел 4: Уход и обслуживание каркасных домов
Каркасные дома need regular upkeep чтобы обеспечить их долговечность и сохранить их внешний вид. Это включает в себя regular inspections of the foundation и Walls, чтобы выявить потенциальные проблемы, такие как damp damage. Кроме того, владельцы должны frequently examine and replace the roofing, чтобы предотвратить протечки и повреждения от влаги. Таким образом, каркасные дома can provide a comfortable and safe living space для многих лет.
Наслаждайтесь удобством [url=https://dostavka-alcogolya-club331.ru]заказать алкоголь ночью[/url] – быстро и просто, прямо до вашей двери.
Заказ алкоголя с доставкой сопровождается определенными правилами и законодательными ограничениями.
Современные сайты позволяют легко подобрать и заказать любой алкоголь из доступных вариантов онлайн.
Наслаждайтесь удобством [url=https://dostavka-alcogolya-club331.ru]заказать алкоголь круглосуточно[/url] – быстро и просто, прямо до вашей двери.
Клиенты экономят время, избегая походов в магазин, и получают возможность выбрать напитки онлайн.
Также часто доступны специальные условия и акции, делающие покупку более выгодной.
Если вы стремитесь приобрести высококачественное медицинское оборудование, которое будет служить надёжным инструментом в вашей работе или бизнесе, стоит посетить страницу [url=https://oborudovanie-aurasonics.ru/]aurasonics москва[/url], где представлена вся необходимая информация о продуктах и услугах, предлагаемых компанией Aurasonics.
Аурасоникс – это компания, которая занимается производством высококачественной аудиоаппаратуры. С момента своего основания Аурасоникс стремится к тому, чтобы обеспечить своим клиентам лучшее звучание. Компания постоянно работает над улучшением качества своих изделий. Сегодня Аурасоникс является одной из наиболее популярных компаний в сфере аудиотехники.
Покупка продукции Aurasonics гарантирует отличное звучание.
Aurasonics предоставляет гарантийное обслуживание своим клиентам.
Aurasonics – это компания, которая предлагает высококачественную аудиоаппаратуру по доступным ценам.
Если вы ищете качественный [url=https://autotechtcentr24.ru/]детейлинг цена[/url], обратитесь к нашим профессионалам.
Благодаря полировке транспортное средство выглядит как новое.
Детейлинг центр – это специализированное место, где автомобили тщательно очищаются и восстанавливаются.
Если вы ищете [url=https://autotechtcentr24.ru/]детейлинг кузова автомобиля[/url], наш сервис предлагает профессиональный уход и восстановление вашего автомобиля на высшем уровне.
Важный раздел работы – детальная уборка и уход за интерьером машины.
Если вы ищете [url=https://autotechtcentr24.ru/]детейлинг салона авто[/url], наш сервис предлагает профессиональный уход и восстановление вашего автомобиля на высшем уровне.
Детейлинг центр представляет собой учреждение, где проводят комплексный уход за автомобилем, уделяя внимание каждой детали.
Если вы ищете качественный [url=https://autotechtcentr24.ru/]детейлинг салона авто[/url], обратитесь к нашим профессионалам.
Эффективность работы напрямую связана с квалификацией специалистов и качеством применяемых продуктов.
Во время полировки кузова убираются мелкие повреждения и создаётся гладкая поверхность.
Если вы ищете [url=https://autotechtcentr24.ru/]детейлинг салона[/url], наш сервис предлагает профессиональный уход и восстановление вашего автомобиля на высшем уровне.
Затем используются специальные защитные средства для поддержания эффекта полировки.
Если вы ищете качественный [url=https://autotechtcentr24.ru/]детейлинг авто[/url], обратитесь к нашим профессионалам.
Детейлинг центр – это сервис, предоставляющий полный спектр услуг по уходу за автомобилем.
Это значительно продлевает срок службы автомобиля и облегчает уход.
Если вы ищете [url=https://autotechtcentr24.ru/]детейлинг кузова автомобиля[/url], наш сервис предлагает профессиональный уход и восстановление вашего автомобиля на высшем уровне.
Завершающий этап – выбор и применение дополнительных процедур по желанию клиента.
Если вы ищете качественный [url=https://autotechtcentr24.ru/]детейлинг салона авто[/url], обратитесь к нашим профессионалам.
Качество оказываемых услуг зависит от профессионализма мастеров и используемых материалов.
В итоге машина приобретает обновлённый и ухоженный вид.
Если вы ищете [url=https://autotechtcentr24.ru/]детейлинг химчистка салона[/url], наш сервис предлагает профессиональный уход и восстановление вашего автомобиля на высшем уровне.
Заключительный этап включает в себя опции для индивидуальной настройки ухода за автомобилем.
Если вы ищете качественный [url=https://autotechtcentr24.ru/]детейлинг москва[/url], обратитесь к нашим профессионалам.
Использование покрытий значительно увеличивает долговечность лакокрасочного слоя.
Средства придают защиту от ультрафиолетового излучения, пыли и влаги.
Если вы ищете [url=https://autotechtcentr24.ru/]детейлинг салона[/url], наш сервис предлагает профессиональный уход и восстановление вашего автомобиля на высшем уровне.
Первый этап ухода в детейлинг центре заключается в аккуратной мойке всех частей автомобиля.
Для надежной защиты воды от загрязнений идеально подойдет [url=http://mybestpool.ru/]купол для каркасного бассейна купить[/url].
Они легкие и удобны в установке, но имеют ограниченный срок службы.
Discover the rejuvenating effects of [url=http://glamkorea.com/]neuramis filler[/url] for effective mesotherapy injections that enhance your skin’s vitality and glow.
Their ability to deliver active ingredients directly into the skin makes them unique among cosmetic treatments.
Если хотите качественно и быстро вернуть блеск вашему автомобилю, обращайтесь в [url=https://autotechtcentr24.ru/]детейлинг мойка кузова[/url], где профессионалы обеспечат вашему авто безупречный вид.
Этот процесс требует навыков и специальных инструментов.
Начинается процесс с детальной мойки всего кузова и колес.
Если вы хотите улучшить свою тренировку, обратите внимание на [url=https://sportres.ru/catalog/gruzoblochnye-trenazhery/]грузоблочный тренажер купить[/url] — это идеальное решение для создания эффективной и разнообразной программы тренировок.
В нашей эпохе блоки для спортивного инвентаря создаются из прочных и долговечных материалов.
Если вы ищете надежное и эффективное оборудование для занятий спортом, обратите внимание на [url=https://sportres.ru/catalog/gruzoblochnye-trenazhery/]тренажеры блочные[/url] на сайте SportRes — здесь вы найдете все необходимое для эффективных тренировок.
Такая профилактика предотвращает износ и продлевает срок эксплуатации тренажера.
Для эффективной тренировки мышц ног рекомендуем обратить внимание на [url=https://sportres.ru/landings/rychazhnye-trenazhery/]рычажный тренажер для ног[/url], который обеспечивает максимальную нагрузку и удобство в использовании.
Помимо фитнеса, тренажер важен для восстановления после травм.
Если вы ищете надежное и эффективное оборудование для занятий спортом, обратите внимание на [url=https://sportres.ru/catalog/gruzoblochnye-trenazhery/]тренажер с блоками[/url] на сайте SportRes — здесь вы найдете все необходимое для эффективных тренировок.
Некоторые блоки используют шарикоподшипники для более плавного хода, а другие предназначены для тяжелых нагрузок.
Если вы хотите улучшить свою тренировку, обратите внимание на [url=https://sportres.ru/catalog/gruzoblochnye-trenazhery/]грузоблок для тренажера[/url] — это идеальное решение для создания эффективной и разнообразной программы тренировок.
Своевременный уход за блоками тренажеров помогает сохранить их функциональность на долгие годы.
Если вы хотите улучшить свою тренировку, обратите внимание на [url=https://sportres.ru/catalog/gruzoblochnye-trenazhery/]грузоблочные тренажеры это[/url] — это идеальное решение для создания эффективной и разнообразной программы тренировок.
Такое решение повышает срок эксплуатации оборудования и защищает спортсменов.
Если вы ищете надежное и эффективное оборудование для занятий спортом, обратите внимание на [url=https://sportres.ru/catalog/gruzoblochnye-trenazhery/]блок тренажер[/url] на сайте SportRes — здесь вы найдете все необходимое для эффективных тренировок.
Это поможет избежать поломок и сохранить функциональность оборудования.
Если вы хотите повысить безопасность и удобство маневрирования, рекомендуем [url=https://parkcam.ru/katalog/kamery-zadnego-vida/kamery-dlya-gruzovikov-i-avtobusov/]купить камеру заднего вида для грузового автомобиля[/url].
Выбор камеры заднего вида зависит от множества параметров, включая качество изображения и наличие дополнительных функций.
Для обеспечения максимальной безопасности на дороге рекомендуем приобрести [url=https://parkcam.ru/katalog/kamery-zadnego-vida/kamery-dlya-gruzovikov-i-avtobusov/]камера заднего вида на грузовик[/url].
Ключевые параметры выбора — это разрешение камеры, диапазон рабочих температур и влагозащита.
Если вы хотите [url=https://kupit-letnie-shini1.ru/]купить летние шины недорого[/url], то у нас вы найдете лучшие предложения и выгодные цены.
Хорошо подобранная летняя резина обеспечивает уверенное вождение и минимизирует риск аварий.
Если вы мечтаете о надежном и уютном жилье, обратите внимание на [url=https://karkasnye-doma05.ru]строительство каркасных домов в спб[/url], который сочетает в себе качество, современный дизайн и доступную стоимость.
Преимущества каркасных домов заключаются в отличной теплоизоляции и энергоэффективности.
Если вы мечтаете о надежном и уютном жилье, обратите внимание на [url=https://karkasnye-doma05.ru]дома каркасные[/url], который сочетает в себе качество, современный дизайн и доступную стоимость.
Использование каркаса снижает нагрузку на фундамент.
Если вы хотите [url=https://kupit-letnie-shini1.ru/]шины летние купить цена[/url], то у нас вы найдете лучшие предложения и выгодные цены.
В продаже имеются модели на любой бюджет — от экономичных до топовых брендов.
Если вы хотите [url=https://kupit-letnie-shini1.ru/]купить летнюю резину в спб[/url], то у нас вы найдете лучшие предложения и выгодные цены.
Также важно учитывать тип протектора и состав резиновой смеси.
Если вы мечтаете о надежном и уютном жилье, обратите внимание на [url=https://karkasnye-doma05.ru]дома каркасные спб[/url], который сочетает в себе качество, современный дизайн и доступную стоимость.
Если не обрабатывать каркас должным образом, он быстро портится.
Если вам нужна [url=https://arenda-avtomobilya-s-voditelem02.ru/]аренда авто в новосибирске с водителем[/url], обращайтесь к профессионалам!
Аренда с водителем востребована для спокойного досуга и экскурсий по Новосибирску.
Если вам необходима [url=https://arenda-avtomobilya-s-voditelem2.ru/]аренда водителя с автомобилем[/url], то наши предложения по аренде авто с водителем в Новосибирске идеально подойдут для комфортных поездок.
Заказать авто с водителем в Новосибирске — отличный способ передвигаться быстро и удобно.
Аренда машины с водителем в Новосибирске идеально подходит для проведения деловых встреч и мероприятий.
Обязательно обратите внимание на тарифы и дополнительные услуги, предлагаемые компанией по аренде авто с водителем.
Выбор компании для аренды авто с водителем в Новосибирске зависит от бюджета и личных предпочтений клиента.
Заказать авто с водителем можно как на несколько часов, так и на целый день, в зависимости от потребностей клиента.
Через специализированные приложения или сайты можно уточнить наличие свободных авто и оформить заявку в любой удобной форме.
Обратившись к профессионалам, вы получите комфорт, экономию времени и спокойствие во время путешествия.
Если вам нужна [url=https://arenda-avtomobilya-s-voditelem02.ru/]прокат авто с водителем новосибирск[/url], обращайтесь к профессионалам!
Итогом можно считать, что такая аренда в Новосибирске обеспечивает комфорт и надежность.
Если вам нужна [url=https://arenda-avtomobilya-s-voditelem02.ru/]авто с водителем в аренду[/url], обращайтесь к профессионалам!
Также стоит внимательно изучить правила аренды и доступность дополнительных услуг.
Если вам необходима [url=https://arenda-avtomobilya-s-voditelem2.ru/]аренда авто с водителем[/url], то наши предложения по аренде авто с водителем в Новосибирске идеально подойдут для комфортных поездок.
Аренда автомобиля с водителем в Новосибирске позволяет легко ориентироваться в городе и не заботиться о дорожной обстановке.
Многие жители города выбирают аренду авто с водителем, чтобы избежать стрессов, связанных с парковкой и пробками.
При заказе услуги важно учитывать рейтинг и отзывы компании, а также ознакомиться с условиями аренды.
Выбор компании для аренды авто с водителем в Новосибирске зависит от бюджета и личных предпочтений клиента.
Заказать авто с водителем можно как на несколько часов, так и на целый день, в зависимости от потребностей клиента.
Для бронирования автомобиля с водителем достаточно связаться по телефону или через онлайн-форму на сайте.
В заключение, аренда авто с водителем в Новосибирске — это надежное решение для деловых поездок и отдыха.
Если вам необходима [url=https://arenda-avtomobilya-s-voditelem2.ru/]прокат авто с водителем новосибирск[/url], то наши предложения по аренде авто с водителем в Новосибирске идеально подойдут для комфортных поездок.
Заказать авто с водителем в Новосибирске — отличный способ передвигаться быстро и удобно.
Многие жители города выбирают аренду авто с водителем, чтобы избежать стрессов, связанных с парковкой и пробками.
Перед бронированием стоит уточнить наличие дипломов и лицензий у водителя, а также условия страхования.
Перед заключением договора стоит сравнить условия, чтобы выбрать наиболее выгодный и надежный вариант.
Аренда авто с водителем позволяет путешествовать по городу без лишних забот и в комфортных условиях.
Через специализированные приложения или сайты можно уточнить наличие свободных авто и оформить заявку в любой удобной форме.
Такая услуга становится всё популярнее среди жителей города и гостей региона, благодаря своим множественным преимуществам.
Финальным шагом приНаличие комплексной документации облегчает работу с строителями и уменьшает число недочётов.
проект дом из газобетона [url=https://gotovye-proekty-domov12.ru/gazobeton/]проект дом из газобетона[/url].
Descubre la magia y tecnologia en el [url=https://show-0de-drones.com/]espectaculo de drones[/url], donde cada vuelo ilumina el cielo con un despliegue impresionante.
Estos eventos combinan tecnologia avanzada con creatividad para crear imagenes impresionantes en el cielo.
Для строительства уютного загородного жилья идеально подходит [url=https://karkasnye-doma-pod-klyuch7.ru]дом каркасный под ключ[/url].
Каркасный дом становится всё более популярным вариантом жилья в современных условиях.
Материалы и технологии подбираются с учётом региона, целей и стоимости проекта.
Тем не менее потребуется внимательный уход за отделкой и системы защиты от воды и ветра.
Каркасная технология применяется в строительстве домов разного назначения и размера.
Для строительства уютного загородного жилья идеально подходит [url=https://karkasnye-doma-pod-klyuch7.ru]каркасный дом спб[/url].
Каркасный дом привлекает внимание многих семей благодаря своим преимуществам.
В основе технологии — прочный каркас, облицовка и слои теплоизоляции.
Средства и время, затрачиваемые на каркасный дом, обычно меньше, чем при иных методах строительства.
Корректное выполнение работ и выбор материалов позволяют получить надёжный и тёплый дом на многие годы.